Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Subjects:
Engineering, Electrical & Electronic
|
Computer Science, Cybernetics
|
Engineering, Manufacturing
As the global supply chain grows more intricate and the prevalence of counterfeit components surges, it becomes paramount to verify the authenticity of electrical chips. The infiltration of counterfeit components, potentially finding their way into electronic equipment, raises concerns as workers contend with mounting client demands. Microelectronics are vital to the healthcare and defense industries, making them vulnerable to counterfeit products.
- counterfeit
- detection
- trust
- microelectronics
- security
1. Introduction
Cybersecurity plays a pivotal and indispensable role in today’s technological landscape. Yet, cybercriminal tactics continue to evolve, making their identification increasingly challenging. Phishing, IoT hacks, and ransomware have resulted in substantial losses in the tech industry. Thus, hardware security, which protects electronic gear throughout production, has grown in popularity. Hardware security, akin to other security domains, strives to shield hardware from threats that could compromise or obliterate it [1]. Ensuring ‘Assurance’ and ‘Trust’ in the context of securing hardware systems translates to the confidence that electronic equipment will perform as intended, free from the peril of compromised components [2].
As the global supply chain grows more intricate and the prevalence of counterfeit components surges, it becomes paramount to verify the authenticity of electrical chips. The infiltration of counterfeit components, potentially finding their way into electronic equipment, raises concerns as workers contend with mounting client demands [3]. National security, economic stability, and individual privacy hang in the balance when hardware systems lack adequate security. Reports from the Department of Defense reveal that over a million components in military aviation and combat missiles have been identified as counterfeit [4,5].
During the first Iraq War in 1991, fighter planes were disabled by a secret activation code embedded in the hardware [6]. Experts believe that the presence of a wicked electrical circuit that was remotely programmable and triggerable played a part in aiding such a catastrophic catastrophe. The Semiconductor Industry Association (SIA) says that annual losses to manufacturers owing to counterfeits total USD 7.5 billion [7], amounting to around 11,000 job losses in the United States [8]. Other sources assert even higher losses, estimating annual sales losses of around USD 100 billion to counterfeiting [9,10].
To combat this menace, cutting-edge strategies for detecting and preventing counterfeits from infiltrating the market are of paramount importance [11]. Figure 1 illustrates the alarming increase in reported counterfeit components between 2021 and 2022, a period during which worldwide semiconductor sales remained relatively stable.
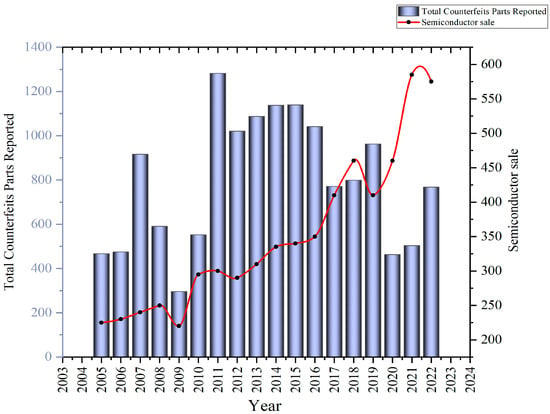
Figure 1. Reported counterfeits increased significantly between 2021 and 2022 [12].
2. Counterfeit Attack Modes
As depicted in Figure 3, counterfeit integrated circuits (ICs) are primarily susceptible to four categories of attack mechanisms: software, hardware, network, and information security.
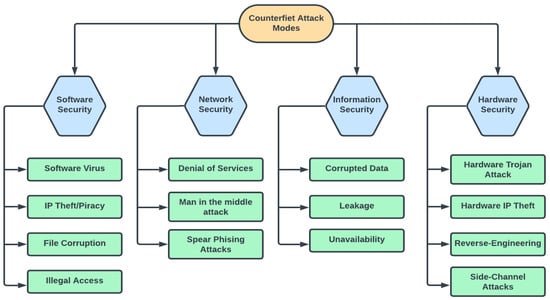
Figure 3. Chart showing counterfeit attack modes and the potential consequences of such attacks.
2.1. Software Security
As the significance of software security continues to escalate, the role of trusted microelectronics in fortifying software applications and ensuring their stability has gained paramount importance. Software security revolves around the safeguarding of software applications against vulnerabilities and attacks that could be exploited by counterfeit integrated circuits (ICs). Counterfeit ICs provide malicious actors with the means to inject malicious code, circumvent security protocols, or manipulate the functionality of software applications. They can also facilitate software-based side-channel attacks and privilege escalation, thereby granting unauthorized access to sensitive data or system resources.
Notably, the Plundervolt attack, elucidated by [13], exploits the dynamic frequency and voltage scaling features of modern CPUs, specifically targeting Intel SGX enclave operations. By manipulating the processor’s voltage, attackers can induce known faults in the processor package, compromising security. This vulnerability can lead to the compromise of cryptographic keys and the introduction of memory-safety vulnerabilities. The repercussions, as outlined in [14], encompass unauthorized access to private data, system instability, software performance degradation, and reduced overall system security.
Furthermore, speculative execution, a form of software security attack that occurs when the CPU speculatively executes tasks it anticipates needing in the future without explicit instruction [15], introduces potential risks. This approach eliminates the need to await the completion of previous commands before executing new ones, thereby enhancing speed by reducing latency and increasing parallelism [16]. However, speculative execution can inadvertently execute potentially harmful programs, raising security concerns.
To enhance software security and instill trust, Physically Unclonable Functions (PUFs) have been proposed. PUFs are employed to generate unique and unpredictable cryptographic keys for authentication and encryption, constituting robust hardware-based security mechanisms. Notable PUF projects include the Arbiter PUF, which leverages differing data-line delays [17], the Ring Oscillator PUF, which relies on variations in the frequencies of two-ring oscillators [18], the SRAM PUF, exploiting idiosyncrasies in SRAM-cell startup behavior [19], and the Memristor PUF, capitalizing on the resistance-changing properties of memristive devices [20]. It is worth noting that PUFs have faced attacks, as elucidated in [21], where modeling attacks seek to emulate a PUF’s behavior through mathematical modeling. These attacks have been successfully executed with the aid of machine learning tools such as Support Vector Machines (SVMs) and neural networks.
2.2. Hardware Security
The embedding of Hardware Trojans, backdoors, and other malicious circuits within counterfeit integrated circuits (ICs) poses a significant threat, endangering the security, confidentiality, and availability of electronic systems [22]. This underscores the critical need for rigorous hardware security measures, including supply chain oversight, secure manufacturing processes, and state-of-the-art counterfeit detection technologies, to forestall unauthorized access [23], data breaches [24], or system malfunctions [25].
Hardware security presents multifaceted challenges, encompassing vulnerabilities to a range of attacks (e.g., side-channel or Trojan attacks) at various layers (e.g., chip or PCB), further complicating the landscape of hardware security. Concurrently, hardware trust concerns stem from interactions with untrustworthy third parties at any stage of a device’s production and distribution, spanning from IP or CAD tool providers to manufacturing facilities and warehouses.
Among common hardware security breaches, Reverse Engineering Attacks, which aim to pilfer a device’s intellectual property and design details for illicit purposes such as duplication or counterfeiting, are prominent [26]. These attacks can be executed through methods like deprocessing, optical imaging, and circuit extraction [27]. In contrast, fault injection attacks intentionally induce system malfunctions to gain access to or control over the targeted system [28], employing tools such as lasers, electromagnetic pulses, or temperature-dependent fault injections [29].
Side-channel attacks focus on unintentional data leakage from a device’s physical implementation, encompassing aspects like power consumption, electromagnetic radiation, or timing data [30]. Techniques such as differential power analysis, simple power analysis, and correlation power analysis are employed to infer device behaviors and potentially extract sensitive information, such as encryption keys, from power consumption patterns [31].
Furthermore, Hardware Trojans represent malevolent hardware additions introduced during product assembly, serving as latent security or functionality vulnerabilities that can be activated at a later stage [32].
2.3. Network Security
Network attacks often manifest in the deployment of counterfeit network interface controllers or routers, potentially leading to the theft of sensitive information, service disruptions, or the illicit takeover of networked devices via unauthorized remote access [33].
In safeguarding critical infrastructure, the Internet of Things (IoT), and cloud-based services, trusted microelectronics play a central role [34]. These components are instrumental in ensuring the privacy, integrity, and authenticity of stored data [18], commonly relying on cryptographic primitives and secure key storage.
One particular area of scrutiny is spear-phishing, an exceptionally targeted and sophisticated form of phishing attack that surpasses conventional phishing attempts in terms of complexity and personalization. This issue is explored extensively in a research paper authored by a single individual [35]. The paper underscores the urgency for enterprises to proactively counter the escalating threat of spear-phishing. To fortify themselves against sophisticated cyberattacks, businesses are advised to prioritize user education, implement robust security measures, and maintain a comprehensive and up-to-date incident response plan.
2.4. Information Security
In addition to bypassing security measures to gain unauthorized access to sensitive data, counterfeit cryptographic integrated circuits also have the potential to disrupt encryption or authentication methods. The advent of social media and cloud computing has necessitated a heavy investment by businesses in information security in order to safeguard data. The Federal Communications Commission offers tips to businesses for cybersecurity [36]. The CIA Triad, comprising of Confidentiality, Integrity, and Availability, serves as a fundamental framework within the field of information security. An all-encompassing information security strategy encompasses policies and security controls that effectively mitigate risks to these three essential components.
The CIA triad serves as a comprehensive framework for overseeing information security and is also valuable for effectively managing research products and data.
This entry is adapted from the peer-reviewed paper 10.3390/electronics12224618
This entry is offline, you can click here to edit this entry!
