Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Subjects:
Engineering, Electrical & Electronic
Seeking to meet the need for the integration of new sources of energy, the entry and integration of new technologies into the grid, global concerns about the environment, diversification of the energy matrix, and the growing consumption of energy, the electrical system is in the process of modernizing its operation, planning, maintenance, communication, management, and control. Therefore, the power system is gradually transforming into SGs, and consequently, the vulnerabilities of this new system become the target of cyberattacks.
- cybersecurity
- cyber–physical systems
- cyberattack
- monitoring
- control
- protection
- defense strategies
- future trends
- power systems
1. Introduction
Technological advances in industries drive the emergence of cyber–physical systems [82,83]. Figure 1 illustrates the CPS system in a block diagram. This type of system integrates the physical aspects of a process and digital technology [84,85]. In addition, using computational concepts, the CPS can act and expand the components on the shop floor, being an important factor in the technology development [84]. The CPS develops a leading role in the development of the industrial Internet of Things (IIoT) and Industry 4.0 [86]. This evolution in the industry provides better access to the information provided by sensors and, consequently, impacts the generation of a high number of data continuously, the so-called big data [87]. In this way, the CPS provides a precise and real-time operation [82,86,88]. Currently, the CPS is the object of study in the literature, since it impacts the economy, environment, and people’s daily lives. In this context, the work developed in [89] presents a review of the literature on CPS applications in 10 research fields: agriculture, education, energy management, environmental monitoring, medical devices and systems, process control, security, smart city and smart home, smart manufacturing, and transportation systems.
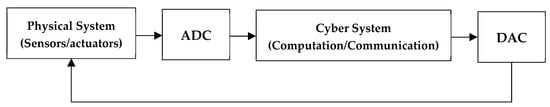
Figure 1. Block diagram of a cyber–physical system.
The following sections display the architecture layers and basic components of a CPS.
2. Cyber–Physical System Layers
The architecture of a CPS is divided into three main typical layers: perception layer, transport layer, and the application layer. Figure 2 illustrates the architecture of a CPS from the layers’ point of view. In the following, the characteristics of each layer are presented and discussed.
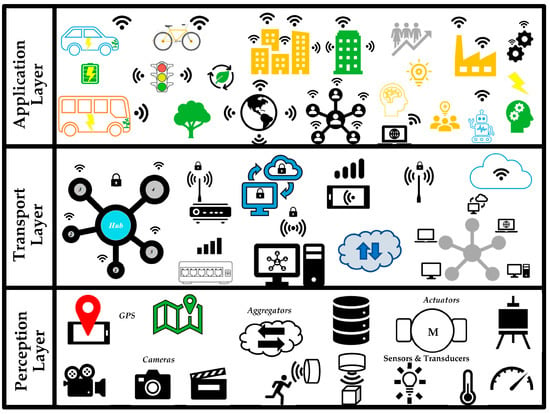
Figure 2. Cyber–physical system layers’ representation.
1.1.1. Perception Layer
The first layer of the CPS architecture is called the perception layer. This layer holds all the equipment that will interpret the physical phenomena and transform them into electrical signals and, subsequently, into information. Some equipment of this first layer is aggregators, actuators, sensors, transducers, Global Position System (GPS), cameras, “Radio-Frequency Identification” (RFID) tags, lasers, and any other intelligent equipment of the so-called “factory floor” [86,90]. This layer aims to collect real-time process information to perform planning, monitoring, and control of the physical system. Due to these factors, in the literature, this layer is also known as the “sensing layer” and “recognition layer” [56,90].
1.1.2. Transport Layer
The second layer of the CPS architecture is called the transport layer. This is the intermediate layer between perception layer and application layer, thus being responsible for the communication of data between the layers. This seamless communication is accomplished through wired or Wi-Fi Internet networks, Bluetooth technology, Infrared (IR), 4G and 5G, Zigbee, and Internet protocols, among other technologies that aid communication. In addition, this layer is responsible for routing and transporting data through routers, switches, hubs, gateways, and clouds. In the literature, the intermediate layer is also known as the transmission layer or network layer [56,90].
1.1.3. Application Layer
The last and most interactive layer of the CPS architecture is called the application layer. The role of this layer is to receive information from the transport layer, analyze it and send appropriate command signals to the devices located in the perception layer to act in the physical process. The application layer uses intelligent decision-making algorithms to analyze the information received and, consequently, make the most appropriate control decision for the proper functioning of the physical system [91]. In addition, system monitoring is performed in this layer, seeking to map the behavior of the physical system to assist in the decision-making process. Furthermore, the application layer can save previous decision-making from obtaining operational improvements and future feedback [86,90].
2. Cyber–Physical System Components
The components that make up a CPS are divided into three groups:
- (i).
-
Physical components;
- (ii).
-
Detection components,
- (iii).
-
Control and communication components.
2.1. Physical Components
The physical components of a CPS are sets of equipment that enable the operation of the physical process. The major components of a Cyber–physical Power System (CPPS) are the power generators, transformers, switchgear, transmission line, circuit breakers, motors, cylinders, and numerous other loads that describe the power system [92].
2.2. Detection Components
The sensing components are devices that are physically connected to the physical system and are responsible for observing and extracting information from the process. This unit highlights three types: sensors, aggregators, and actuators.
-
Sensors
These devices are in the perception layer and are connected directly to the physical system components. The sensors are responsible for interpreting the physical phenomenon and transforming it into a signal that can be interpreted. In addition, they have the function of collecting the information from the physical system and through the aggregators sending it to the transport layer [86,93].
-
Aggregators
These are devices that are mostly located in the transport layer and responsible for processing the data received by the sensors. It works as a “bridge” that transports the data obtained by the sensors, from the perception layer to the transport layer. Online data aggregators are found in routers, switches, gateways, and other devices performing this transport function [86,93].
-
Actuators
These are devices located in the application layer. Actuators receive a message indicating their operation based on data processing and decision-making from the aggregators. In addition, they are responsible for modifying system parameters so that the process operates properly. Actuators receive messages in the form of electrical signals and hydraulic or pneumatic energy and generate physical actions as responses [86,93]. Motors, valves, and cylinders are examples of actuators.
2.3. Control and Communication Components
The control and communication components of a CPS are devices responsible for monitoring and managing the physical system. In addition, they seek to control the process to achieve z satisfactory performance, reliability, and security. Therefore, control devices are fundamental for the robustness of the system. In this perspective, Programmable Logic Controllers (PLCs), Distributed Control Systems (DCSs), and Remote Terminal Units (RTUs) are elements that stand out to control, and the Supervisory Control and Data Acquisition (SCADA) and Phasor Measurement Unit (PMU) perform the data acquisition in a CPS system. The following sections detailed describe these components.
-
Programmable Logic Controllers (PLCs)
PLCs are digital computers that, through user programming, can automate and control modern industrial processes. Initially, these devices were developed to replace industrial relay panels and emulate the behavior of electrical diagrams. Besides that, this device presents characteristics that facilitate fault diagnosis, good flexibility, resistance to vibrations, immunity to electrical noise, support algorithms and loops, easy programming, low cost, robustness, and good reliability, among other important aspects [86,94]. The basic building blocks that make up the PLC hardware are a rack, a power supply, a programming unit, input and output (I/O) modules, and the central processing unit (CPU) [95]. Thus, the PLC is used for various industrial control and automation applications, from simple to more complex systems [95].
-
Distributed Control Systems (DCSs)
Centralized control for large and complex systems may present a different efficiency, reliability, controllability, flexibility, and robustness as communication failures [96]. From this perspective, physical system processes are divided into subsystems and locally controlled through industrial computers, thus allowing the distribution of control and greater flexibility in operator action [86,96]. In addition, monitoring can be performed through supervisory systems that provide online and remote control. In this way, DCSs have reduced implementation costs while increasing the reliability and robustness of the system [86].
-
Remote Terminal Units (RTUs)
RTUs are electronic devices that extract the signal samples, investigate, and identify possible failures and then restore the data in a distribution system [97]. In comparison with PLC, the RTU does not perform well in algorithms and control loops, as well it presents low immunity to vibrations and noise [86]. Its main application is focused on geographical telemetry systems, being used to extract information from the system, send/receive messages, and perform control actions in a SCADA system [98], while presenting some processing capacity due to its microprocessor unit [86]. In addition, some RTUs can also control numerous systems that are connected to the control room [99].
-
Supervisory Control and Data Acquisition (SCADA)
These systems use software to collect, measure, monitor, process, and control the data and equipment in a CPS [100]. The SCADA system extracts and processes the data generated by the PLCs and RTUs [101]. The typical SCADA system architecture features a “Human–Machine Interface” (HMI), hardware, software, RTU, central supervisor, database, measurement devices, and process actuation [100,102]. These systems’ communication networks can be based on Internet protocols, providing benefits in monitoring, planning, management, and control of the CPS. However, this can also bring some harm, such as a higher number of cyberattacks on the vulnerabilities of the SCADA system [103].
-
Phasor Measurement Unit (PMU)
PMU technology is used in power systems to measure a “quantity” called a phasor. The phasor is a graphical representation of the magnitude and phase angle of an alternating current electrical quantity at a specific time. In this way, it aims to improve the precision of the visualization of electrical quantities at all points of the network and, therefore, facilitate the diagnosis of possible failures in the system [104,105]. Using GPS for the time-stamping of samples, PMUs can measure the frequency and the rate of change of the frequency of electrical signals. For this reason, they are also known as synchrophasors [106]. Systems with PMUs have a higher update rate and accuracy of around 1 µs compared to SCADA systems [107,108]. From this perspective, using data acquisition with PMU technology provides real-time measurement, analysis, and control of system dynamics that cannot be achieved using a traditional SCADA system.
3. Cyber–Physical System Vulnerabilities
The current integration between people and machines controlled remotely in real-time by Internet networks, data processing, and new computer and information technologies provide benefits regarding the efficiency and performance of the control system in industries and in the automation of processes. In counterpart, this system presents new evils concerning the cybersecurity of information on physical devices, communication, monitoring, operation, and control of the cyber–physical system.
From this perspective, the cyber–physical system presents new weaknesses in its operation that are known as cyber, physical, and cyber–physical vulnerabilities. The cyber vulnerability relates to the network system, communications, smart devices, remote access, and unintentional failure of employees and vendors [109]. The physical vulnerability is related to physical attacks on the devices that make up the infrastructure of the cyber–physical system, such as the sensors, transducers, actuators, motors, cylinders, pumps, valves, transmission line cables, and distribution and transmission transformer towers, among other physical devices that make up an industrial system [109]. Finally, there is the cyber–physical vulnerability which represents a new type of vulnerability that is concerned with the weaknesses and damage presented by the junction of cyber and physical devices and components of the critical infrastructure of an industrial cyber–physical system [109].
Modern systems of monitoring, control, and industrial management are performed by SCADA systems or other industrial control systems that use as a primary element a set of systems with PLCs [110,111]. PLCs, through their inputs, are responsible for receiving and processing the data received by sensors and transducers connected to the industrial process, and through a programming logic and signal issued, they can determine how the actuators, motors, frequency inverters, relays, transformers, and other final control elements will work in the industrial process [110]. From this perspective, the PLC integration with new Internet technologies makes it a target of cyberattacks on its communication network, such as Stuxnet [111], Triton, and Black Energy [112], and consequently, such devices present a vulnerability in cybersecurity and are part of the critical infrastructure of the industrial control system of a CPS.
PLCs are connected to and integrated into the Internet of Things; therefore, they are vulnerable to malicious threats in their control logic. This type of attack is called control logic injection, and it aims to cause failures and disruptions in the processes controlled by PLCs. In this perspective, the author of [112] presents recent work on control logic injection attacks and points out the recommendations and current challenges in the security and protection of information in PLC-controlled systems. Besides the control logic injection attack, there is the denial-of-service attack, wherein a large number of malicious packets are sent and transmitted that exploit the possible security vulnerabilities of a PLC system [113]. Thus, the author of [113] discusses a methodology capable of detecting anomalies based on monitoring the behavior of the CPU of a PLC in a water tank control system.
Cybersecurity in management and control systems with PLCs is important to maintain the availability, integrity, and confidentiality of process data and ensure proper and resilient operation of the industrial system. Thus, the author of [114] presents a study that points out the challenges in information security and discusses the security of communication protocols in Industry 4.0 systems that use PLCs and SCADA. The author of [111] takes a different approach than the conventional one, considering the communication network between engineering stations and PLCs as an object of study and analysis of cybersecurity.
This entry is adapted from the peer-reviewed paper 10.3390/en16124556
This entry is offline, you can click here to edit this entry!
