Unmanned aerial vehicles (UAVs), or drones, have made them able to communicate and collaborate, forming flying ad hoc networks (FANETs). FANETs are becoming popular in many application domains, including precision agriculture, goods delivery, construction, environment and climate monitoring, and military surveillance. These interesting new avenues for the use of UAVs are motivating researchers to rethink the existing research on FANETs.
- unmanned aerial vehicles
- UAVs
- drones
- flying ad hoc network
- cloud-based UAV systems
1. Introduction
2. UAV Classification
There are different types of UAV classifications in the literature. As shown in Figure 1, in this SLR, a comprehensive UAV classification is provided based on different factors such as UAV size and weight, altitude, range, application, flying mechanism, ownership, airspace class, level of control autonomy, and engine type [21], all of which are shown in Figure 1. Size is often a major factor in deciding which UAV is appropriate for a mission. As shown in Figure 1, box A, UAVs can be classified into Very small sizes with very light weight, such as Micro Aerial Vehicles (mUAVs) and Nano Aerial Vehicles (NAVs), Small sizes such as Mini-UAVs, and Medium and Large UAVs that are heavy or super heavy [22]. The classification of UAVs based on weight, endurance, and altitude is provided in Figure 1, boxes B, C, and D, respectively.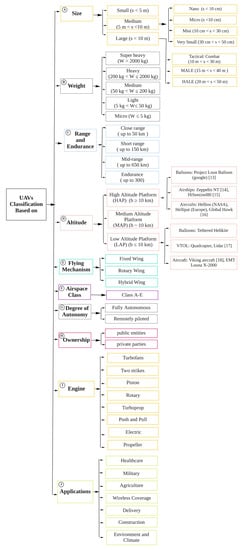
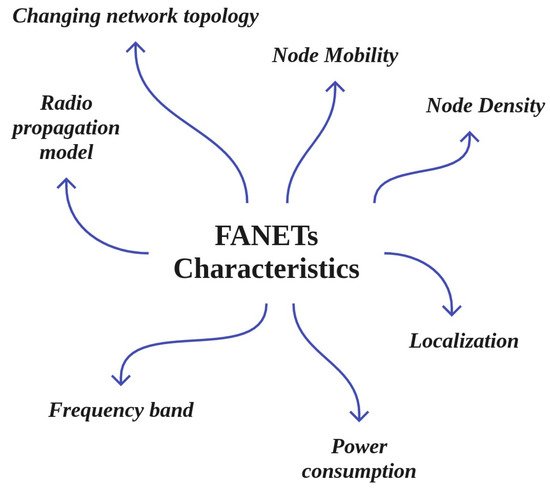
3. Main Characteristics of FANETs
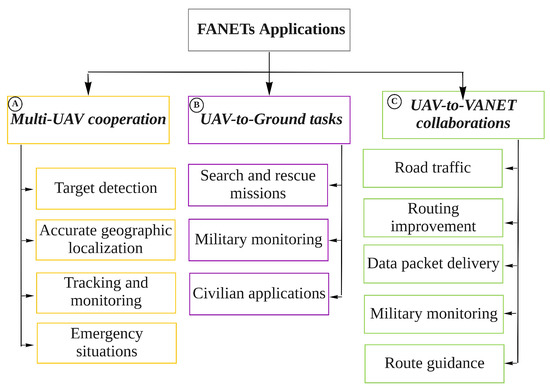
4. Main Applications of FANETs
-
Multi-UAV cooperation: Figure 34, box A shows the following applications, which can be categorized as multi-UAV cooperation:
- –
- –
-
Tracking and monitoring in disaster situations: UAVs can help to assess the direction in which a flood is moving, then predict what buildings are exposed to damage. Similarly, they can be used for rescue operations in the aftermath of earthquakes, identifying collapsed population-dense buildings such as hospitals and schools so that these areas are given a higher priority in rescue operations [30][31][76,77].
- –
-
Emergency situations: UAVs are used in the construction industry to check safety and to monitor the progress of construction and buildings. UAVs can be used to provide temporary wireless coverage in cellular networks during emergencies when the ground base stations are out of service, as well as in many other emergency scenarios [32][33][33,54].
6. UAV Mobility Models
Typical mobility models used in FANETs include pure randomized mobility models (the random way (RW), random waypoint (RWP), random direct ion (RD), and Manhattan grid (MG) models), time-dependent mobility models (the Gauss Markov (GM), boundless simulation area (BSA), and smooth turn (ST) models), path-based mobility models (the semi-random circular movement mobility model (STCM), and paparazzi (PPRZM) models), group mobility models (the reference point froup (RPGM), exponential correlated (ECR), column (CLMN), nomadic community (NC), pursue (PRS), and particle swarm (PS) models), and topology control mobility models (the pheromone base (PB), distributed pheromone repel (DPR)-based, mission plan-based (MBP), and self-deployable point coverage (SDPC) models) [24][35][44][57][66,73,79,88]. The chosen model relies on the network to keep the entire system working as a unity. There are several parameters, including the altitude, path and directing of flying, and atmospheric conditions, all of which impact UAV mobility. In addition to these parameters, other important aspects should be considered when select a mobility model for UAVs in different scenarios. These aspects include avoidance of connections that control the distance between UAVs, controlling sudden changes in the UAVs’ direction, and the safety standards and deployment that need to be considered in order to prevent collisions between UAVs [56][100].7. Integration of Technologies with the UAV-Networked Systems
-
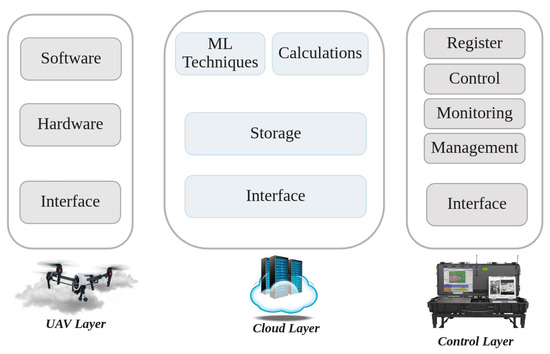
UAV Layer: As shown inFigure 7, in the UAV layer (i.e., the physical layer), UAVs that are connected with the IoT cloud using short- and long-range wireless technologies can perform different tasks, ranging from traffic monitoring to delivery. The cloud layer sends control information and signals about the traffic situation to the UAV layer to guide responses based on the desired GBS in the control layer. In the UAV layer, multiple network components such as drone-to-target (D2T) and drone-to-drone (D2D) are attached [20][68].8, in the UAV layer (i.e., the physical layer), UAVs that are connected with the IoT cloud using short- and long-range wireless technologies can perform different tasks, ranging from traffic monitoring to delivery. The cloud layer sends control information and signals about the traffic situation to the UAV layer to guide responses based on the desired GBS in the control layer. In the UAV layer, multiple network components such as drone-to-target (D2T) and drone-to-drone (D2D) are attached [20,118].
-
Cloud Layer: The cloud layer, which is the heart of CBUMS, transfers the data between the UAV and control layers. As can be seen inFigure 7, the storage, computation, ML techniques, and interface are the main components of the cloud layer [20][68].8, the storage, computation, ML techniques, and interface are the main components of the cloud layer [20,118].Storage:The cloud layer captures streams of data about the location, environment, and UAV mission information, storing the captured data in a regular SQL database or NoSQL database based on the application’s requirements.Calculations and ML techniques:Several computation algorithms, such as map/reduce, data analytics, image processing, ML techniques (including supervised and unsupervised learning algorithms), RL and DRL-based algorithms, and FL-based techniques are executed in the cloud to improve the system performance and fix existing open issues.Interface:The interface contains web and network services that make connections between control and UAV layers. Interfaces in the cloud layer take advantage of various communication protocols, including wireless personal area networks (WPAN), wireless local area networks (WLAN), low-power wide-area networks (LPWAN), and cellular networks. In applications that require UAVs to directly communicate with the central station, a WiFi transmission system is used. However, long-term evolution (LTE) and long-range area networks (LPWAN) provide lower-latency communication systems than WIFi.
-
Control Layer: AsFigure 7 shows, the control layer includes GCSs that remotely register, control, manage, and monitor UAVs from a location close to or inside the flying field. The GCS contains application software that receives collected data from UAVs and sends control signals to them. The users can monitor UAVs, set task parameters, and modify them through the data analysis implemented by the cloud based on the application software [20][68].8 shows, the control layer includes GCSs that remotely register, control, manage, and monitor UAVs from a location close to or inside the flying field. The GCS contains application software that receives collected data from UAVs and sends control signals to them. The users can monitor UAVs, set task parameters, and modify them through the data analysis implemented by the cloud based on the application software [20,118].
- UAV-to-Ground tasks:
- Figure
- 34, box B shows the following applications for UAV-to-ground cooperation:
- –
- –
-
Search and rescue missions: UAVs play a vital role in search and rescue missions (SAR). FANETs are considered an immense advantage in guaranteeing public safety, performing SAR missions, and managing man-made or natural disasters such as floods, earthquakes, forest fires, tsunamis, terrorist attacks, and checking the safety of critical infrastructure such as power and water utilities. It is important to provide communications coverage in such situations. In situations when public communications networks are disrupted, UAVs can provide timely disaster warnings and help to speed up rescue and recovery operations. UAVs can carry medical equipment to inaccessible regions. They can make SAR operation much faster in situations such as avalanches, wildfires, searching for missing persons, and more.
-
UAV-to-VANET collaborations between UAVs and vehicles: As shown in Figure 34, box C, the following applications involve cooperation between UAVs and vehicles:
- –
-
Roadway traffic monitoring: FANETs can be employed instead of intensive labour and complex observational infrastructure to carry out road traffic monitoring. In roadway traffic monitoring, UAVs are able to detect traffic crashes and then report these incidents easily. Using UAVs is much faster than using the incident commander’s vehicle. In addition, UAVs can be used to provide road safety by capturing real-time videos from various security scenarios and situations in road networks [35][79].
- –
-
Data packet delivery: Data delivery to mobile ad hoc nodes is a challenging task, as it is difficult to find a reliable forwarding path to ensure that data is delivered from one user to another. In this respect, UAVs are widely used as airborne communication relays to deliver data collected by ground devices to distant control centres. In other words, UAVs deliver packet data based on the load-carry-and-delivery (LCAD) paradigm, in which data is loaded from the source node and forwarded to the destination node utilizing multiple UAVs [36][37][80,81].
- –
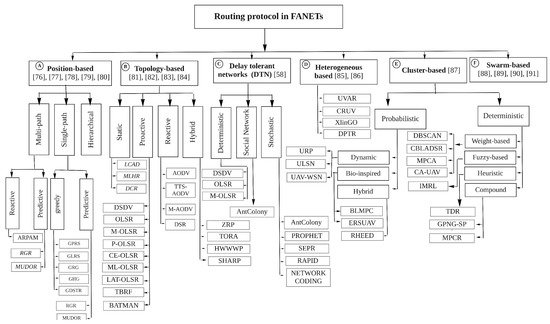
5. FANET Routing Protocols
- Augmented reality (AR) and Virtual Reality (VR) technologies (
- Figure
- 5
- 6
- , box A): VR, which is shown in Figure 56, box A, has been integrated with UAV-networked systems for greater integration of the virtual and real worlds. Such integration can create a virtual environments for multiple purposes, including marketing, agriculture, entertainment, education, and more, by taking over people’s vision and making them feel as if they are somewhere else. AR is considered a variation of VR; VR technology, there is an essential need for 3D data on a large scale. In this regard, UAVs that can freely fly in the sky are excellent tools for collecting 3D data. Several studies have investigated the use of VR technology and UAV networks [5][6][7][8][9][5,6,7,8,9].
-
IoT-enabled UAV communication system (Figure 56, box B): The integration of UAVs with IoT is called the Internet of Flying Things (IoFT) [10][11][10,11] or Internet of Drone Things (IoDT) [12]. IoFT or IoDT represents a new research topic related to IoT, cellular networks, cloud, fog, and edge computing, big data, intelligent computer vision, and security techniques. IoFT or IoDT can efficiently support different applications in various fields ranging from disaster management to smart industry, providing high connectivity, scalability, flexibility, and availability.
-
Integration with Cloud Computing (Figure 56, box C): As shown in Figure 56, box C, cloud computing has been integrated with FANETs; known as cloud-based UAV or flying cloud computing, this can improve and increase storage, network bandwidth, and processing. Such an integrated system includes three main layers: a UAV layer, a cloud server layer, and a ground control system (GCS)/client layer. The UAV layer collects sensor data such as pressure, temperature, etc., while flying and transmits the collected data to the cloud for storage and processing using 3G/4G/5G cellular communication devices or other technologies such as WiMAX, WiFi, etc. The communication layer is responsible for providing wireless connectivity for the UAVs and GCS any time and anywhere without any limitations on communication range. The last layer contains the cloud servers that store and process different types of data, such as geographical location parameters, environment variables, sensor data, images, etc., received from the UAVs to detect various events [10][58][59][60][10,109,110,111].
-
Flying Edge Computing (Figure 56, box D): Edge computing allows data storage and computing closer to the sources of data. Edge computing has been integrated with FANET (flying edge computing) to mitigate the hardware limitations of UAVs and improve the performance of UAV networks [13]. Flying edge computing is employed to support real-time IoT applications such as video streaming surveillance, VR and AR, and smart transportation [61][112]. In flying edge computing, UAVs are associated with edge IoT devices such as GBSs to offload and migrate part of the data computation to the edge layer; the other parts of computation tasks are locally managed by the UAVs [62][113] without the intervention of the cloud [63][114]. Integrating UAVs with edge computing provides low latency and response time for different IoT real-time applications. However, certain applications require storage and computing of voluminous data such as video streams. The local resources of edge IoT devices cannot efficiently support such cases. Therefore, flying fog computing can be expanded to the core network to provide low latency for storage and processing of huge amounts of UAV data [10].
-
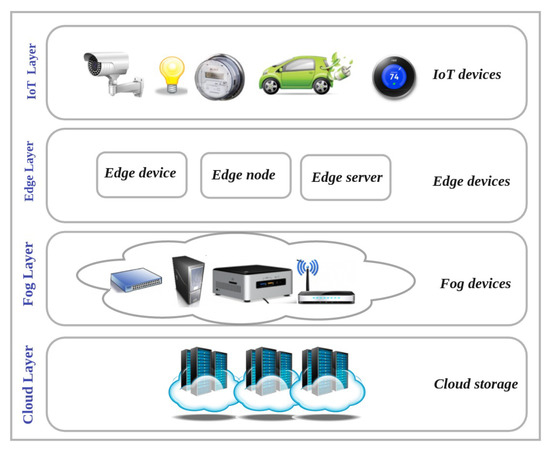
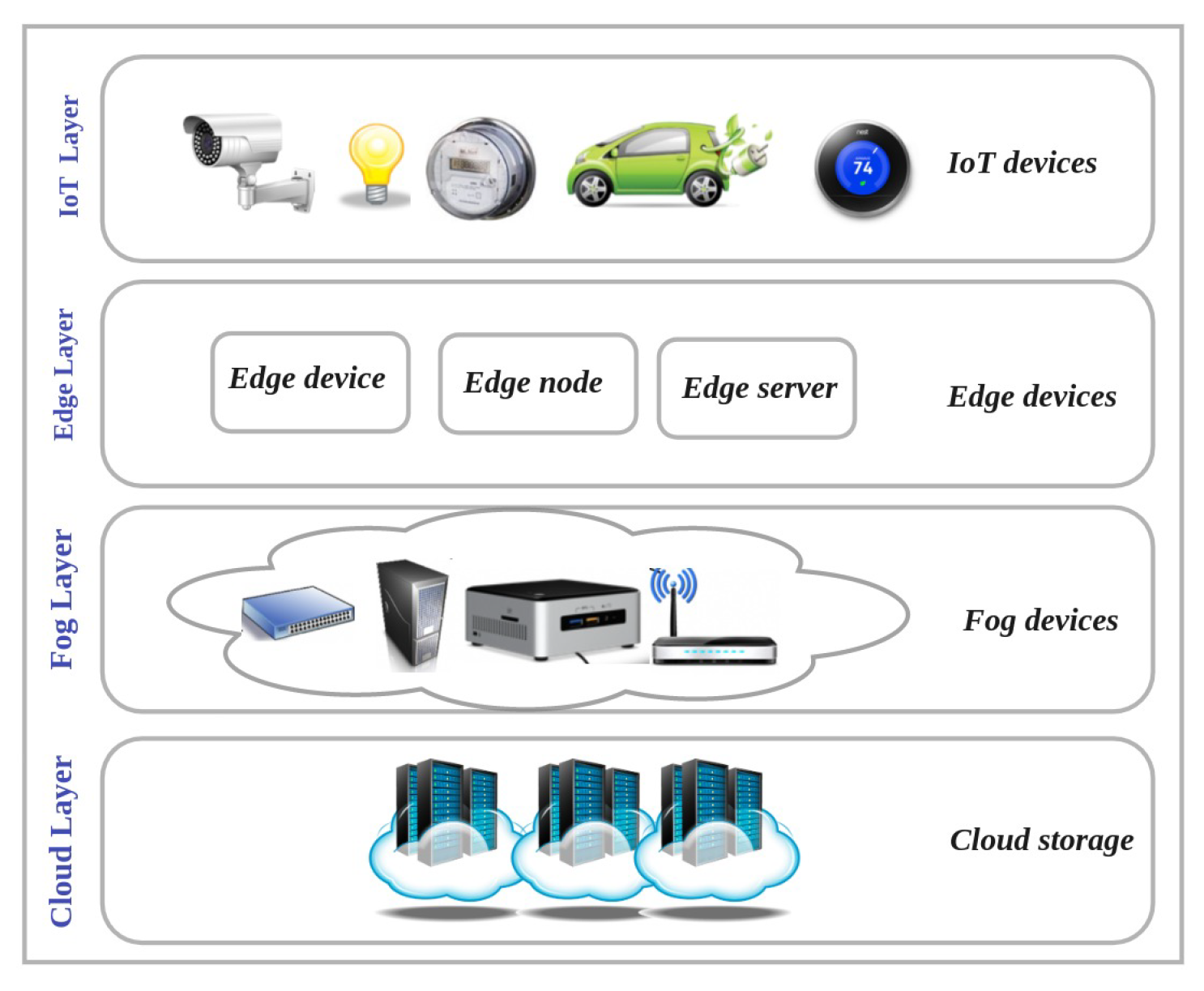
Flying Fog Computing (Figure 56, box E): Flying fog computing, which is located at the edge of the network, provides an intermediate level between the cloud and UAV layers. The fog layer communicates with the UAV layer through wireless connection and the cloud layer using the internet. The integration of fog computing and UAVs provides low latency for real-time UAV-assisted IoT applications along with high capacity in terms of computing and storage. Although the flying fog computing paradigm provides enough computing power for IoT nodes, a major issue involves the integration of the UAVs in the edge computing layer with the cloud computing layer [10][14][15][10,14,15]. Figure 67 shows the cloud, fog, edge, and IoT layers.
-
Integrating UAVs into cellular networks (Figure 56, box F): Agile UAVs are a special class of lightweight fixed-wing UAVs with small control surfaces [64][115]; they can be used as flying base stations, mobile relays, users, sensors, network controllers, and even as a scheduler in a cellular network [16], providing high reliability and low latency in communications. In UAV-based cellular networks, UAVs are mostly equipped with small BSs to provide temporary required communication links and cover the hard-to-reach regions. These flying BSs are more adaptive, flexible, and cost-effective than conventional towers or pole-mounted or rooftop BSs [17]. However, cellular networks have limitations in terms of supporting UAV communications. For example, optimally deploying UAVs is one of the most challenging issues in this context [18][19][18,19]. Therefore, new communication technologies such as 5G and 6G that support aerial and satellite communication are needed to manage UAV traffic in very dense air traffic scenarios [31][65][66][67][77,103,116,117]. There are challenges with integrating 5G and 6G with FANETs, which can suffer from issues and is a very complex task with many technical issues which need to be addressed [24][66].
- Position-based (
- Figure
- 4
- 5
- , box A):
- In these protocols, the geographic information of the nodes is known from GPS, and the positions of the sender and receiver are determined in advance using
- reactive
- , predictive, greedy [40][84], and hierarchical [41][42][43][85,86,87] methods, as shown in Figure 45, box A. The position-based hop by hop protocols usually dynamically select relay nodes. The packets are broadcast blindly by the node, and the selection of the relay is postponed until the neighbours of the node receive the packets. After the neighbours receive the packets, they calculate the dynamic forwarding delay (DFD) values according to their local position information in a distributed manner and then forward the packets to the destination greedily. The nodes closest to the destination then acquire the minimum DFD value and become the next forwarder [44][88].
-
Topology-based (Figure 45, box B): In topology-based hop by hop routing protocols, the senders forward packets through an optimal path using the network’s topology information along with link- state information such as IP address [45][89]. As shown in to Figure 45, box B, these can be classified as static [46][90], proactive [47][91], reactive [48][92], and Hybrid.
-
Delay-tolerant networks (DTNs) (Figure 45, box C): In DTNs, the mobile nodes are intermittently and unstably connected. As the mobile nodes experience high latency and low data rates, new routing protocols are needed to address the DTN characteristics [24][66]. The three main DTN-based routing protocols studied for FANETs are deterministic, social network, and stochastic [24][66], which are depicted in Figure 45, box C.
-
Heterogeneous (Figure 45, box D): FANETs interact with various ground networks, such as VANETs, MANETs, or fixed nodes, in which heterogeneous routing protocols are required for exchanging data between moving users. Routing protocols with heterogeneous techniques can support both mobile and fixed nodes in FANETs [49][93]. This technique can provide sub-network assistance coverage for both nodes on the ground and UAVs, network extension, and more [50][94]. The classification of heterogeneous routing protocols is shown in Figure 45, box D.
-
Cluster-based (Figure 45, box E): In the clustering technique, nodes with similar characteristics and features are combined to form clusters. There is a cluster head in each cluster that carries out communication processing [51][95]. As shown in Figure 45, box E, cluster-based routing protocols in FANETs can be classified into two main categories, namely, probabilistic and deterministic. A full classification of cluster-based routing protocols in FANETs is shown in Figure 45, box E.
8. Main Components of Cloud-Based UAV Managing Systems (CBUMS)
9. Simulation Tools
Evaluating the performance of UAV-based communication networks in the real world is a difficult task that requires a remarkable amount of time and resources. Frequent topology changes and the high degree of mobility of the UAVs in FANETs make the practical evaluation of UAV performance a challenging, costly, and time-consuming task. In addition, due to regulations around using UAVs in most countries, certain types of cyber-attack resistance evaluation tests for UAV networks are not allowed [2]. Therefore, many flexible simulation tools, frameworks, emulators, and testbeds have been developed to make it possible to create, implement, test, and evaluate schemes virtually without requiring real-world implementation. The available FANET performances analysis tools include
AVENS, CUSCUS, Simbeeotic, UAVSim, UTSim, FANETSim, Netsim, OMNeT++, NS2,NS3, OPNET, ROS-NetSim, MATLAB, TOSSIM, QualNet, GloMoSim, YANS, ONE, SSFNet, FlynetSim, J-Sim, BonnMotion, GAZEBO, AirSim, RoboNetSim, Mininet-Wifi
, and
SUMO, each of which supports different mobility models, operating system, and programming languages [69][70][71][72].
, each of which supports different mobility models, operating system, and programming languages [119,120,121,122].
