You're using an outdated browser. Please upgrade to a modern browser for the best experience.
Please note this is a comparison between Version 1 by SONAIN JAMIL and Version 2 by Sirius Huang.
As a result of the advancement in the fourth industrial revolution and communication technology, the use of digital twins (DT) and federated learning (FL) in the industrial Internet of Things (IIoT), the Internet of Vehicles (IoV), and the Internet of Drones (IoD) is increasing. DT provides a virtual simulation of the networks, whereas FL involves collaborative learning and enhances the privacy and security of the network. The application of DT and FL has been proven to be efficient in increasing the performance of the IIoT, IoV, and IoD.
- digital twins
- Internet of Vehicles
- federated learning
- Internet of Drones
- Industry 4.0
- cyber–physical system
- next generation networks
- industrial Internet of Things
1. Introduction
The fourth industrial revolution revolutionized the Internet of Things (IoT). This age of the industrial revolution is also called the connected age [1]. The industrial revolution started in 1780 with the introduction of the mechanization age. In 1870, the second revolution, named the electrification age, was introduced. As a result of the advancement in technology, Industry 3.0, also known as the automated age, was adopted in 1970. However, with the introduction of IoT, Industry 4.0, also called the connected age, was fully utilized. Because of increased interconnection and smart automation, Industry 4.0 envisions a fast change in technology, industries, and social patterns and processes [2]. Industry 4.0, in essence, is the trend toward automation and data sharing in manufacturing technologies and processes such as cognitive computing [3], cyber–physical systems (CPSs) [4], the industrial Internet of Things (IIoT) [5], cloud computing [6], indoor factories [7], IoT, and artificial intelligence (AI). Figure 1 shows the evolution of the industrial revolution.
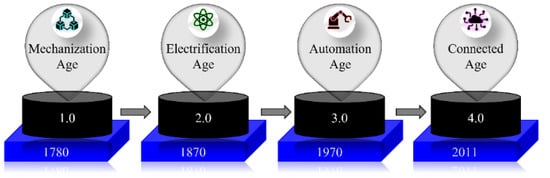
Figure 1. Industrial revolution from Industry 1.0 to Industry 4.0.
Industry 4.0 uses technologies such as DT and FL. DT is the digital processing and evaluation of an industry, smart city, or network. Intelligent manufacturing is composed of six layers; the zero layer is called the manufactory area; the first layer is known as the manufactory building; the second layer is infrastructure; the third layer is operations the fourth layer is the smart manufactory; and the fifth layer is DT [8]. All these layers are shown in Figure 2.
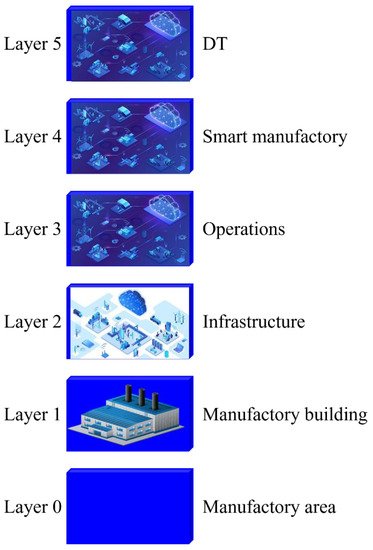
Figure 2. Different layers of intelligent manufacturing having DT. Simulations and DT are two different things.
1.1. Simulations
Across industries, simulations are used to test goods, systems, processes, and concepts. Simulations are generally digital models created with computer-aided design software tools and are frequently utilized during the design phase. These models can be constructed in 2D or 3D to depict different aspects of a process or product, but they can also be created with mathematical principles rather than computer-based representations. To analyze results, the simulation introduces and tests many factors in the digital world or interface.
1.2. Digital Twins (DT)
A virtual representation that is constructed to accurately mirror an existing physical thing is referred to as a DT. The physical thing is outfitted with sensors that generate data regarding many elements of the device’s performance, such as on a wind turbine. This information is subsequently sent to a processing system and applied to the digital model. This DT may then be used to run simulations, analyze current performance, and create prospective enhancements that can be transferred back to the real asset. A DT for non-physical processes and systems may also be developed, replicating the underlying process or system, and allowing simulations to be undertaken using real-time data.
DT data is often obtained via Internet of Things (IoT)-connected devices, enabling the gathering of high-level information that can subsequently be merged into the virtual model.
A DT is essentially a virtual environment in which ideas may be explored with little constraints. With an IoT platform, the model transforms into an integrated, closed-loop twin that can be utilized to inform and drive company strategy.
1.3. Differences between Simulations and DT
Although both simulations and DT employ digital models to imitate items and processes, they have some fundamental distinctions. The most noticeable is that a DT generates a virtual environment capable of studying several simulations, supported by real-time data and a two-way communication flow between the twin and the sensors that gather this data. This improves the accuracy of predictive analytical models, allowing for better management and monitoring of products, regulations, and processes. A comparison of simulations and DT is presented in Table 1.
Table 1. Comparison of simulations and DT.
| Simulations | DT | |
|---|---|---|
| Data elements and interactions | Static | Active |
| Simulation basis | Potential parameters input for testing | Real-world feedback from a specific product/process |
| Scope | Narrow—primarily design | Wide—cross-business |
1.4. Federated Learning (FL)
FL is defined as collaborative ML without centralized training data. In FL, the shared prediction model learns collaboratively and keeps all training data on the local devices, without storing all the information on a single server. FL provides several advantages, such as smarter models, low latency, less power consumption, and privacy preservation. FL is a new technology that enables phones to learn from other devices while keeping data private and secure. It works as follows. First, the phone downloads a generic ML model. Then, the phone personalizes and improves its model, and computes a summary of the changes. Thousands of summaries are anonymously combined when phones are plugged in at night. This provides a global improvement to the model, enabling it to work better for all users. Thus, users benefit from having a smarter phone, and their data remain in users’ hands [8]. Figure 3 demonstrates FL.
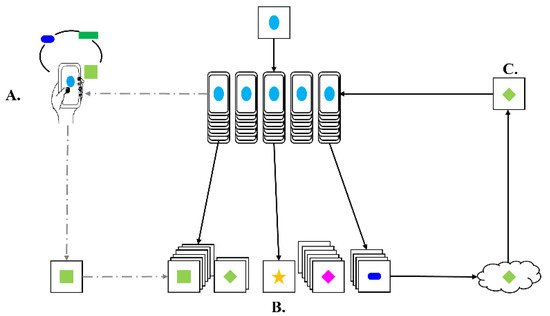
Figure 3. Smart phone personalizes the model locally, based on usage (A). Many users’ updates are aggregated (B) to form a consensus change (C) to the shared model, after which the procedure is repeated.
1.5. IIoT
The industrial Internet of Things (IIoT), Internet of Vehicles (IoV), and Internet of Drones (IoD) are three important technologies of next generation networks (NGNs). IIoT is referred to as the industry of the future. IIoT refers to interconnected instruments, devices, and sensors networked with industrial applications on computers, such as for production and energy management. This connectivity enables data gathering, sharing, and analysis, possibly promoting productivity and efficiency increases and other economic benefits [9]. The IIoT is a development of a distributed control system (DCS) [10] that enables more automation by refining and optimizing process controls utilizing cloud computing.
1.6. IoV
IoV is a network of vehicles and allows the utilization of data generated by linked automobiles and Vehicular Ad Hoc Networks (VANETs). IoV is a decentralized network of vehicles outfitted with sensors, software, and technologies linking and exchanging data over the Internet following agreed-upon standards [11][12][11,12]. IoV emerged from Vehicular Ad Hoc Networks [13] (“VANET,” a type of mobile ad hoc network used for communication between automobiles and roadside equipment), and is predicted to grow into an “Internet of autonomous vehicles” in the future. The IoV is predicted to be one of the facilitators of autonomous, connected, shared, and electric (ACES) Future Mobility [14]. Figure 4 shows an illustration of the IoV.
Figure 4. Illustration of the IoV.
1.7. Internet of Drones (IoD)
The IoD is defined as an infrastructure that aims to offer control and access to drones and users over the Internet. Drones are quickly becoming commonplace commodities, allowing each user to fly many missions in regulated airspace. The IoD is a layered network control architecture developed primarily to coordinate the access of unmanned aerial vehicles (UAVs) to regulated airspace and deliver navigation services between nodes [15]. The IoD offers general services for various drone applications, including package delivery, traffic monitoring, and search and rescue [16][17][18][16,17,18]. Figure 5 illustrates the IoD.
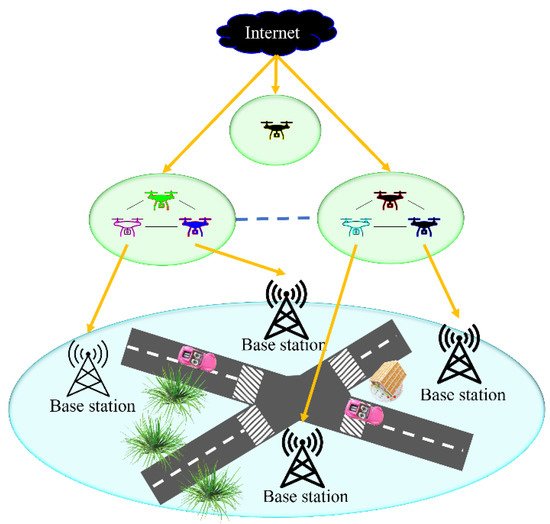
Figure 5. Illustration of IoD.
2. Use of DT and FL
This section explains the use of DT and FL for the IIoT, IoV, and IoD in the following subsections.
2.1. IIoT
DT is widely used in IIoT systems. Malakuti et al. elaborated on the definition of DT and the role of DT in IIoT systems. The authors also analyzed the decisions made by software architects regarding the architecture [19][46]. Similarly, the authors of [20][47] focused on the interoperability of DT for IIoT systems. The results showed that DT simulation of the development of the 3GPP for ultra-reliable low latency (URLLC) reduces the delay and increases reliability [21][48].
In [22][49], the authors proposed a DT model for basalt fiber production. They illustrated the smart digitization of the fiber industry using IIoT. Thomas et al. developed an artificial intelligence (AI) and extended reality (XR)-based DT for the management of complex systems. They also presented the advantages of using AI and XR for DT’s improved training and performance [23][50].
FL is also widely used for several purposes in IIoT networks. Zhang et al. demonstrated the data management by using a deep reinforcement learning (DRL)-based FL algorithm. The algorithm achieved 97% accuracy for the data management of the IIoT network [24][51]. Rahman et al. highlighted the importance of using FL to ensure the fairness and trustworthiness of the IIoT network [25][52].
Ferrag et al. presented a realistic dataset for cyber security. The dataset can be used for training FL models [26][53]. Jia et al. presented a blockchain-enabled FL scheme for protecting the data using differential privacy and homomorphic encryption [27][54].
Lakhan et al. presented deadline, latency, and energy-efficient strategies and a BEFC scheme to ensure blockchain hashing and validation [28][55]. Makkar et al. proposed SecureIIoT, an FL approach to avoid data breaches [29][56]. Similarly, the researchers demonstrated an FL and blockchain-enabled defensive transmission model and achieved 98% accuracy [30][57].
Vy et al. demonstrated federated transfer learning (FTL) for low computing power IIoT gadgets and achieved an accuracy of more than 70% for the KDD99 dataset [31][58]. In [32][33][59,60], the authors highlighted the use of FL for intrusion detection in context-aware IIoT networks and software-defined network (SDN)-enabled IIoT, respectively.
The researchers presented an FL-based cyber-threat hunting model for IIoT networks based on blockchain technology [34][61]. Chen et al. proposed a communication effective federated edge learning (FEL) algorithm for new radios in unlicensed spectrum (NRU)-based IIoT networks [35][62].
K et al. proposed a novel algorithm based on FTL for the authentication and privacy preservation of the IIoT network [36][63]. Table 23 presents the summary of the use of DT and FL in IIoT.
Table 23. Summary of the use of DT and FL in IIoT.
| Ref. | Year | Objective | FL | DT | Achievements |
|---|---|---|---|---|---|
| [19][46] | 2018 | Architectural aspects | No | Yes | Elaborate the role of DT in IIoT systems |
| [20][47] | 2020 | Interoperability | No | Yes | A flexible solution for the interoperability of the DTs in IIoT |
| [21][48] | 2020 | Wireless technology and protocols | No | Yes | Development of 3GPP for URLLC in minimizing delay and enhance reliability |
| [22][49] |
42][69]. Similarly, the researchers proposed a FL-based model for the improved TCP performance of the IoV network over WiFi [43][70].
Chai et al. proposed a blockchain-enabled FL algorithm for improved knowledge sharing in IoV networks [44][71]. Moreover, the authors proposed a novel FL model for efficient license plate recognition in 5G-enabled IoV [45][72].
Zhou et al. proposed a dual-layer FL and heterogeneous model aggregation for the efficient communication and privacy preservation of 6G-enabled IoV [46][73]. Kong et al. demonstrated FL-based cooperative positioning in the IoV network for autonomous driving and collision avoidance [47][74]. Wang et al. used FL for efficient resource management in the IoV network [48][75]. Table 34 shows a summary of the use of DT and FL in IoV networks.
Table 34. Summary of the use of DT and FL in IoV.
| Ref. | Year | Objective | FL | DT | Achievements |
|---|---|---|---|---|---|
| [37][64] | 2021 | Traffic data predication | No | Yes | DT to predict the traffic data of the IoV and achieved quick response and improved accuracy |
| [38][65] | 2021 | Resource allocation | No | Yes | DT for the dynamic resource allocation in the aerial-assisted IoV |
| [39][66] | 2019 | Time series behavior modeling | No | Yes | DT model for the evaluation and validation of charging recommendation design |
| 2021 | Fiber production | No | Yes | A DT for the digitization of fiber industry using IIoT | |
| [40][67] | 2021 | Resource sharing | No | Yes |
Smart entities, such as smart automobiles having the ability to detect and act, are common in the modern day. During their operational period, these entities can collect a large amount of data, which can then be used to improve the well-being of inhabitants. However, these data are extremely sensitive, prompting concerns about privacy. Furthermore, network constraints, bandwidth use, and other factors may exacerbate the situation. FL, IoD, and dew computing (DC) are transformative technologies that may be used to address the aforementioned issues. Using IoD, a FL-based computing paradigm was implemented over DC to analyze road-related data in order to improve the efficiency of applications, such as for identifying parking places [50][77].
Similarly, Islam et al. used FL and IoD to create a blockchain-based data accumulation scheme. This scheme enhanced the security of IoD against cyber threats [51][78]. Zhang et al. investigated a robust semi-supervised learning-based FL scheme in IoD for automatic image recognition. The approach improved the privacy of the image data in the IoD [52][79]. Table 45 presents the summary of the use of FL in IoD.
Table 45. Summary of the use of FL in IoD.
| Ref. | Publication Year | Objective | FL | DT | Achievements | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [49][76] | 2021 | Power control | Yes | No | Improved security, better QoS | |||||||
| [50][77] | 2021 | Roadside computing | Yes | No | Improved efficiency | |||||||
| [51][78] | 2022 | Blockchain integrated data accumulation | Yes | No | Higher security against cyber threats, improved privacy | |||||||
| [52][79] | 2022 | Automatic image recognition | Yes | No | DT for the remote resource sharing in IoV and applied consortium blockchain to track and secure resource sharing | Better image recognition, enhanced privacy | [23][50] | [412020 | ][68Complex systems management | ]No | Yes | AI and XR-enabled DT development for the management of complex systems |
| [24][51] | 2021 | Data management | Yes | No | FL algorithm with DRL for data management achieving 97% accuracy | |||||||
| 2021 | Resource allocation | No | Yes | DT for the resource allocation in air assisted-IoV and achieved improved energy efficiency | [25][52] | 2021 | TrustFed | Yes | No | Blockchain-enabled TrustFed framework to ensure fairness and trustworthiness | ||
| [26][53] | 2022 | Cyber security dataset | ||||||||||
| [42][69] | 2020 | Data sharing | Yes | No | Asynchronous FL-based approach for efficient and secure data sharing | |||||||
| [43][70] | 2020 | TCP performance improvement | Yes | No | FL-based model for the improved TCP performance over WiFi in an IoV network | Yes | No | Provides a realistic dataset for the cyber security of IoT and IIoT. Dataset can be used for the training of FL models | ||||
| [44][71] | 2020 | Knowledge sharing | Yes | No | Improved knowledge sharing in the IoV-based blockchain-empowered FL algorithm | [27][54] | 2021 | Data protection | Yes | No | ||
| [45][72 | Blockchain enabled FL scheme for the protection of the data using differential privacy and homomorphic encryption | |||||||||||
| ] | 2021 | License plate recognition | Yes | No | Improved license plate recognition system based on FL for the 5G-enabled IoV | [28][55] | 2022 | |||||
| [46] | Multi-objective modeling and blockchain enabled system | [ | Yes | No | Deadline, latency, and energy-efficient strategies, and a BEFC scheme to ensure blockchain hashing and validation | |||||||
| 73] | 2021 | Accurate learning and privacy preservation | Yes | No | [29][56] | 2022 | Data breach protection | Yes | No | FL-based framework (SecureIIoT) to protect IIoT networks from data breach | ||
| Dual-layer FL and heterogeneous model aggregation for the efficient communication and privacy preservation of 6G-enabled IoV | ||||||||||||
| [47][74] | 2021 | Cooperative positioning | Yes | No | FL-based cooperative positioning in an IoV network for autonomous driving and collision avoidance | [30][57] | 2021 | |||||
| [48][75] | Defensive transmission model | Yes | 2021 | Joint resource management | YesNo | FL and blockchain-enabled model for defensive transmission, and achieved 98% accuracy | ||||||
| No | Efficient resource management based on the FL in an IoV network | [31][58] | 2021 | FTL for low computing power IIoT devices | Yes | No | FTL for low computing power IIoT gadgets and achieved accuracy of more than 70% for the KDD99 dataset | |||||
| [32][59] | 2021 | Intrusion detection | Yes | No | FL-based intrusion detection system for IIoT networks with improved efficiency | |||||||
| [33][60] | 2021 | Intrusion detection | Yes | No | FL-based intrusion detection in SDN-enabled IIoT networks | |||||||
| [34][61] | 2022 | Cyber threat hunting | Yes | No | FL-based cyber-threat hunting model for IIoT networks based on the blockchain technology | |||||||
| [35][62] | 2021 | Communication-effective FEL in NRU | Yes | No | Communication-effective FEL algorithm NRU-based IIoT networks | |||||||
| [36][63] | 2021 | Authentication and privacy preservation | Yes | No | Novel algorithm based on FTL for the authentication and privacy preservation of the IIoT network |
2.2. IoV
DT and FL are also widely used in IoV for resource allocation, resource sharing, traffic prediction, etc. Hu et al. proposed a DT model to predict traffic data in an IoV network and improve accuracy and response time [37][64]. Similarly, the authors investigated DT for the dynamic resource allocation in an aerial-assisted IoV network [38][65].
Zhang et al. presented a DT model to evaluate and validate the charging recommendation design [39][66]. Tan et al. designed DT for remote resource sharing in IoV and applied a consortium blockchain to track and secure resource sharing [40][67]. Wang et al. proposed a DT model for efficient and quick resource sharing in an unmanned aerial vehicle (UAV)-based IoV network [41][68].
Several articles used FL in the IoV. Lu et al. presented an asynchronous FL approach to implement secure and effective data sharing in IoV networks [
2.3. IoD
The IoD is a network of drones. The use of FL, which is also known as collaborative learning, has proven to be very effective in the deployment of IoD. ML is used to supply numerous services in fog-affected IoDs, where vast amounts of training data are gathered by drones and evaluated in the nodes experiencing fog. Aggregating all data in these nodes may result in massive network traffic and data privacy leaks from drones. FL is therefore suggested to protect drone data privacy by performing local training in drones and communicating training model parameters to the fog-bound nodes without uploading raw drone data. However, ground eavesdroppers can still access private drones by eavesdropping and analyzing uploaded parameters during the FL training process. Yao et al. examined the power regulation of all drones to optimize the FL system security rate while considering drone battery capacities and quality of service (QoS) requirements (i.e., FL training time)
