Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 2 by Yvaine Wei and Version 1 by Alexandru Martian.
Drones are small and low-cost unmanned aerial vehicles (UAVs). With the decrease in the cost and size of drones in recent years, their number has also increased exponentially. As such, the concerns regarding security aspects that are raised by their presence are also becoming more serious.
- drone
- UAV
- RF methods
- detection system
- defense system
1. Introduction
Technical innovations continue to manifest at an ever-increasing speed, causing fast and drastic changes to modern society. These changes, driven by the possibilities offered by new technologies, affect citizens, governments, and all public and private industry sectors.
As a result, the development of small, low-cost unmanned aerial vehicles (UAVs), commonly known as drones, has resulted in an ever-increasing number of these devices being utilized in a variety of applications [1]. UAVs have introduced new participants in aviation, quickly evolving beyond their military origin to become powerful business tools [2,3][2][3].
Applications of UAVs range from recreation to commercial and military applications, including enjoyment, hobbies, games with drones, homemade entertainment videos, recreational movies [4[4][5][6],5,6], low altitude flying base stations [7], and the operation of UAVs for military purposes [8,9,10,11,12,13][8][9][10][11][12][13].
2. The Necessity of Drone Detection and Defense Systems: Incidents and Regulations
The drone industry’s rapid rise has outpaced the rules for safe and secure drone operation, making them a symbol of illegal and destructive terror and crimes [15][14]. Drones have gained attention as a threat to safety and security since their entrance into civilian technology, which has fueled the development of anti-drone (or counter-drone) technologies. Anti-drone systems are designed to protect against drone accidents or terrorism, but they will need to evolve in order to deal with future drone flight systems [16][15]. UAVs have been used in a variety of military actions. Non-military UAVs have been accused of endangering airplanes, as well as persons and property on the ground. Due to the potential of an ingested drone to quickly damage an aircraft engine [17][16], safety concerns have been raised. Multiple near-misses and verified collisions have occurred involving hobbyist UAV pilots operating when violating the aviation safety standards [18][17].3. Drone Detection and Defense Systems: Classification, Sensors, Countermeasures
3.1. Classification of Drone Detection and Defense Systems
Firstly, it is necessary to classify drone detection and defense systems (DDDSs) in order to understand their capabilities, as it is summarized in Table 31.
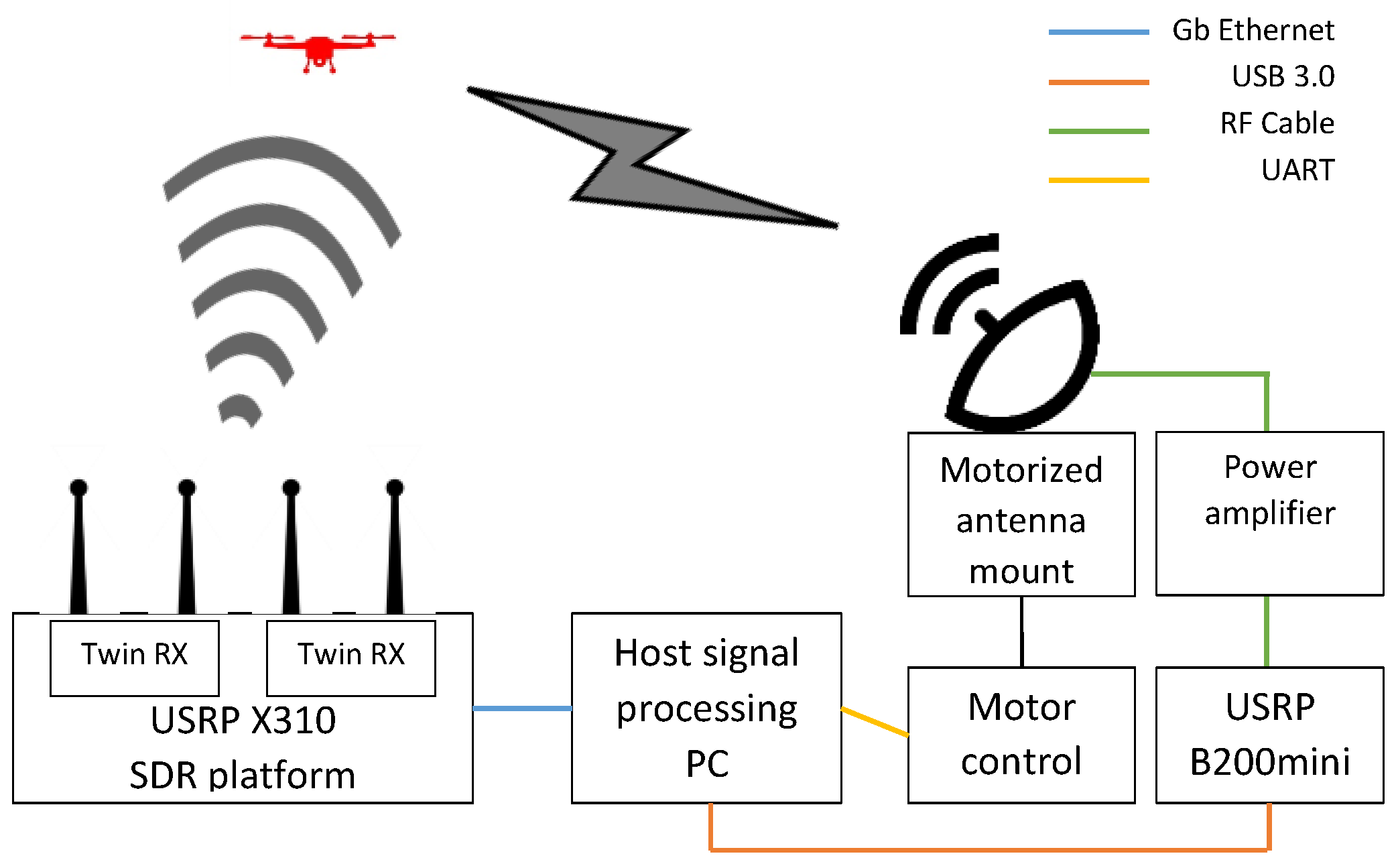
Table 31.
Classification of DDDSs.
| Category | Definition | |||
|---|---|---|---|---|
| Ground-based: fixed | Systems designed for usage in fixed locations [33][18] | |||
| 22 | ] | Ground-based: mobile | ||
| Acoustic |
|
|
[36,37,38,39,40,41,42,43,44,45,46,[47,48,23][24][25][26][2749,50,51,52,53][21][][28][29][30][31][32][33][34][35][36][37][38] | |
| Systems designed to be installed on automobiles and operated while they are in motion | [33][18] | |||
| Imaging |
|
Hand-held | Systems designed to be operated by a single person using their hands; the majority of these systems resemble rifles [34][19] | |
| UAV-based | Systems designed to be mounted on unmanned aerial vehicles (UAVs) [34][19] | |||
| UAV-swarm-based | Systems designed to use multiple drones [35][20] |
3.2. Classification of Detection Sensors
All of the types of sensors that are currently used in DDDS present specific advantages and limitations and, as a direct consequence, such a system must incorporate more sensors of different types in order to achieve a higher detection rate [33][18]. The different pros and cons for each category are summarized in Table 52.Table 52.
Pros and cons of sensors used in DDDSs.
| Type | Pros | Cons | References |
|---|---|---|---|
|
|
[54,55,56,57,68,69,70,71,72][39][40][41][58,42][59,43][60,44][61,45][62,46][63,47][64,4865,[49][5066,]67,][51][52][53][54][55][56][57] | |
| Radar |
|
|
[73,74,75,76,77,[78,79,5980,81,][60][61][62][63][64][6582,][83,6684,85,]86,87,[88,67][68][69][70][71][72 |
| 113 | ] | [ | 88][89][90][91][92][93][94][95][96][97][98] |
4. Drone Detection and Defense Systems Based on RF Methods
One of the most used methods for drone detection is the identification of the RF signals that are exchanged by the drones with another entity (ground station/operator). Moreover, the annihilation of the detected drones can also be obtained by RF methods, by means of transmitting strong enough jamming signals that can interrupt the communication between the drone and its operator. Usually, drones operate on different frequencies, but most commercial drones operate in Industrial, Scientific, and Medical (ISM) frequency bands of 433 MHz and 2.4/5.8 GHz. The simple power detection in these bands will not work due to the presence of other legitimate users in the same geographical area. Therefore, most of the modern RF detection systems provide the detection and identification of the special and unique signals that are generated by the UAV or the data protocols implemented in a UAV. There are two main functions that are necessary for the detection of the drones, as follows: The identification of the presence of the drones by scanning the frequency spectrum and localization of the drones. The annihilation function, which is necessary in order to allow the defense against the detected drones, can be performed by means of RF jamming, in order to interrupt the communication between the drones and their operators. Table 73 summarizes the main elements regarding the implementation of such systems.Table 73.
RF-based drone detection and defense systems.
| References | Implemented Functions | Methods | SDR Platform Used (Including Manufacturer, City and Country) | |||
|---|---|---|---|---|---|---|
| [152][99] | Identification Localization |
RF fingerprinting (SFS, WEE, PSE) AoA (MUSIC, RAP MUSIC) |
USRP-X310 (Ettus Research, Santa Clara, CA, USA) | |||
| [153][100] | Identification | RF fingerprinting (DRNN) | USRP-X310 (Ettus Research, Santa Clara, CA, USA) | |||
| [154][101] | 89 | , | 90,91,92,93,94,]95,96,97,98,[7399,][74100,]101,102][58][75][76][77][ | Identification78][79][80][81][82][83][ | RF fingerprinting (CNN)84][85][86][87] | |
| USRP-X310 (Ettus Research, Santa Clara, CA, USA) | Radio Frequency (RF) | |||||
| [155][102] |
|
|
[103,104,105,106,107,108,109,110,111, | Identification112 | RF fingerprinting (KNN), | USRP-B210 (Ettus Research, Santa Clara, CA, USA) |
| [156][103] | Identification | RF fingerprinting (KNN, XGBoost) | - | |||
| [157][104] | Identification | RF fingerprinting (Wi-Fi) | - | |||
| [158][105] | Identification | RF fingerprinting | LimeSDR (Lime Microsystems, Guilford, UK)(customized) | |||
| [159][106] | Identification | RF fingerprinting | - | |||
| [160][107] | Localization | Received-signal strength (RSS) | USRP N210 (Ettus Research, Santa Clara, CA, USA) | |||
| [161][108] | Localization | RSS | AD-FMCOMMS5-EBZ Evaluation Board (Analog Devices, Wilmington, DC, USA) | |||
| [162,[163,109164]][110][111] | Annihilation | RF jamming | BladeRF (Nuand, San Francisco, CA, USA) | |||
| [165][112] | Annihilation | RF jamming | Great Scott Gadgets HackRF One |
5. Challenges and Future Perspectives for Drone Detection and Defense Systems
One of the challenges that is faced when implementing a DDDS is the ability to identify and, in a further step, to annihilate not only one, but several different target drones. In recent years, many applications have used multiple drones [166][113], therefore, such a feature becomes an important characteristic for a DDDS. Depending on the sensors that are used in the system, the possibility of detecting several target drones may or may not exist. A few examples of systems that include such a feature exist in the literature. In [167[114][115],168], algorithms are developed in order to allow multi-UAV detection using video streams. In [169][116], an RF-based deep learning (DL) algorithm is proposed for performing multiple drone detection. The possibility of a simultaneous annihilation of several drones is an even more challenging task. Electromagnetic pulses (EMP) have been proposed as a possible solution for defense against drone swarms [170][117]. RF jamming performed using antenna arrays could also generate, by means of signal processing methods (beamforming), multiple beams that could be targeted towards multiple target drones. Another challenge that a DDDS would have to face, especially if the area in which the system is installed is a residential area, and there are several households in the close neighborhood, is to avoid interference or damage to nearby equipment (in the case of RF jamming and EMP) and to respect the privacy of the nearby neighbors (in the case of imaging sensors). In the case of RF jamming, this could be solved if the antennas that are used or the beams, in the case of using a beamforming approach, are very directive and targeted directly towards the target drone(s).6. DronEnd Detection and Defense System
The goal of the DronEnd ground defense system is to secure a certain area against the unauthorized presence of drones. In order to achieve this goal, the DronEnd system scans the RF spectrum in order to detect the presence of the drones in the supervised area, identifies the location of the drone by means of AoA algorithms, and annihilates the drone by using RF jamming methods. The block diagram of the implemented DronEnd ground defense system is presented in Figure 21.

Figure 1. Block diagram of the DronEnd ground defense system.
Figure 2. Block diagram of the DronEnd ground defense system.
6.1. Detecting the Presence of the Drone Using Spectrum Sensing Algorithms
A first step required for detecting the presence of a drone in the case of RF-based drone defense systems is to monitor the radio spectrum through a spectrum sensing process in order to identify the signals that are transmitted by the drone. For the implementation of the spectrum sensing process in the DronEnd system, spectrum sensing algorithms based on the energy detection method have been used. Algorithms, such as 3EED [174][118] and 3EED with an adaptive threshold [175][119], that were previously developed, provide improved performance compared to the classical energy detection (CED) [176][120] algorithm and were used to identify the presence of the drones in the monitored area. The above-mentioned algorithms were implemented on SDR platforms from the USRP family (USRP X310 (Ettus Research, Santa Clara, CA, USA) [177][121] equipped with Twin-RX RF Daugterboards (Ettus Research, Santa Clara, CA, USA) [178][122], 10–6000 MHz frequency range).6.2. Localization of the Drone Using AoA Algorithms
Once the frequency that is used by the drone to communicate has been identified, a second necessary step is to obtain information about the position of the drone. This step was performed using AoA algorithms for detecting the angle of incidence of the detected RF signal. Such algorithms exploit the phase difference of the signals that are received from the drone using a multi-antenna system. The SDR platform that was used as the hardware for providing the RF receive front-end was the USRP X310 [177][121], on which two Twin-RX RF modules [178][122] were mounted (covered frequency range of 10–6000 MHz, instantaneous bandwidth 80 MHz).6.3. Annihilation of the Drone Using RF Jamming
A final step is to transmit a jamming signal to the identified target drone in order to disrupt the communication between the drone and its operator. As the jamming signal should only be transmitted in the direction of the target drone, in order to avoid interference with other equipment in the area, a directional antenna was used for the jamming operation.6.4. Conclusion
To conclude, the main novel elements that are introduced by the DronEnd system, when compared to other drone detection and defense systems based on RF methods, can be summarized as follows:-
Incorporates all of the three functions (identification, localization, and annihilation) that are necessary for a drone detection and defense system in an integrated and scalable platform, which can be reconfigured depending on the requirements of different use cases;
-
Includes an agile and accurate identification subsystem, based on improved spectrum sensing algorithms, which performs a real-time identification of the signals that are transmitted by the drone and, moreover, allows a dynamic tracking of the signal transmitted by the drone, even when the transmit frequency is changed;
-
Annihilates the detected drone by means of jamming, avoiding at the same time significant interference with nearby devices, as a directional antenna, targeted directly towards the target drone using a motorized antenna mount, is used.
References
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless Communications with Unmanned Aerial Vehicles: Opportunities and Challenges. IEEE Commun. Mag. 2016, 54, 36–42.
- World Economic Forum. Drones and Tomorrow’s Airspace. 2020. Available online: https://www.weforum.org/communities/drones-and-tomorrow-s-airspace (accessed on 13 January 2022).
- Scott, G.; Smith, T. Disruptive Technology: What Is Disruptive Technology? Investopedia 2020. Available online: https://www.investopedia.com/terms/d/disruptive-technology.asp/ (accessed on 13 January 2022).
- Germen, M. Alternative cityscape visualisation: Drone shooting as a new dimension in urban photography. In Proceedings of the Electronic Visualisation and the Arts (EVA), London, UK, 12–14 July 2016; pp. 150–157.
- Kaufmann, E.; Gehrig, M.; Foehn, P.; Ranftl, R.; Dosovitskiy, A.; Koltun, V.; Scaramuzza, D. Beauty and the beast: Optimal methods meet learning for drone racing. In Proceedings of the IEEE International Conference on Robotics and Automation, Montreal, QC, Canada, 20–24 May 2019; pp. 690–696.
- Kaufmann, E.; Loquercio, A.; Ranftl, R.; Dosovitskiy, A.; Koltun, V.; Scaramuzza, D. Deep drone racing: Learning agile flight in dynamic environments. In Proceedings of the Conference on Robot Learning (CoRL), Zürich, Switzerland, 29–31 October 2018; pp. 133–145.
- Ahmad, A.; Cheema, A.A.; Finlay, D. A survey of radio propagation channel modelling for low altitude flying base stations. Comput. Netw. 2020, 171, 107122.
- Tozer, T.; Grace, D.; Thompson, J.; Baynham, P. UAVs and HAPspotential convergence for military communications. In Proceedings of the IEEE Colloquium on Military Satellite Communications, London, UK, 6 June 2000; pp. 10-1–10-6.
- Schneiderman, R. Unmanned drones are flying high in the military/aerospace sector. IEEE Signal Process. Mag. 2012, 29, 8–11.
- Chen, J.Y.C. UAV-guided navigation for ground robot tele-operation in a military reconnaissance environment. Ergonomics 2010, 53, 940–950.
- Coffey, T.; Montgomery, J.A. The emergence of mini UAVs for military applications. Def. Horiz. 2002, 22, 1.
- Quigley, M.; Goodrich, M.A.; Griffiths, S.; Eldredge, A.; Beard, R.W. Target acquisition, localization, and surveillance using a fixed-wing mini-UAV and gimbaled camera. In Proceedings of the IEEE International Conference on Robotics and Automation, Barcelona, Spain, 18–22 April 2005; pp. 2600–2605.
- Iscold, P.; Pereira, G.A.S.; Torres, L.A.B. Development of a hand launched small UAV for ground reconnaissance. IEEE Trans. Aerosp. Electron. Syst. 2010, 46, 335348.
- Butt, A.; Shah, S.I.A.; Zaheer, Q. Weapon launch system design of anti-terrorist UAV. In Proceedings of the International Conference on Engineering Technology (ICEET), Lahore, Pakistan, 21–22 February 2019; pp. 1–8.
- EY India. What’s the Right Strategy to Counter Rogue Drones? Available online: https://www.ey.com/en_in/emergingtechnologies/whats-the-right-strategy-to-counter-rogue-drones (accessed on 12 January 2022).
- Ritchie, M.; Fioranelli, F.; Borrion, H. Micro UAV crime prevention: Can we help princess Leia? In Crime Prevention 21st Century; Springer: New York, NY, USA, 2017; pp. 359–376.
- Van Voorst, B.R. Counter Drone System. U.S. Patent 15,443,143, 14 September 2017.
- Markarian, G.; Staniforth, A. Countermeasures for Aerial Drones; ARTECH HOUSE: Norwood, MA, USA, 2021; ISBN 13: 978-1-63081-801-2.
- Michel, A.H. Counter-Drones Systems, 2nd ed.; Report from the Center of the Study of the Drone at Bard College: Annandale-On-Hudson, NY, USA, 2019; Available online: https://dronecenter.bard.edu/files/2018/02/CSD-Counter-Drone-Systems-Report.pdf (accessed on 13 January 2022).
- Brust, M.R.; Danoy, G.; Stolfi, D.H.; Pascal, B. Swarm-based counter UAV defense system. Discov Internet Things 2021, 1, 2.
- Alsok. 2020. Available online: https://www.alsok.co.jp/en/ (accessed on 12 January 2022).
- Ottoy, G.; de Strycker, L. An improved 2D triangulation algorithm for use with linear arrays. IEEE Sens. J. 2016, 16, 8238–8243.
- Shi, Z.; Chang, X.; Yang, C.; Wu, Z.; Wu, J. An Acoustic-Based Surveillance System for Amateur Drones Detection and Localization. IEEE Trans. Veh. Technol. 2020, 69, 2731–2739.
- Mezei, J.; Fiaska, V.; Molnar, A. Drone sound detection. In Proceedings of the 16th IEEE International Symposium on Computational Intelligence and Informatics (CINTI), Budapest, Hungary, 19–21 November 2015; pp. 333–338.
- Hilal, A.A.; Mismar, T. Drone Positioning System Based on Sound Signals Detection for Tracking and Photography. In Proceedings of the 11th IEEE Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 4–7 November 2020; pp. 8–11.
- Kim, J.; Kim, D. Neural network based real-time UAV detection and analysis by sound. J. Adv. Inf. Technol. Converg. 2018, 8, 43–52.
- Busset, J.; Perrodin, F.; Wellig, P.; Ott, B.; Heutschi, K.; Rühl, T.; Nussbaumer, T. Detection and tracking of drones using advanced acoustic cameras. Unmanned/Unattended Sens. Sens. Netw. XI Adv. Free. Space Opt. Commun. Tech. Appl. 2015, 9647, 96470F.
- Christnacher, F.; Hengy, S.; Laurenzis, M.; Matwyschuk, A.; Naz, P.; Schertzer, S.; Schmitt, G. Optical and acoustical UAV detection. Electro-Opt. Remote Sens. X 2016, 9988, 99880B.
- Seo, Y.; Jang, B.; Im, S. Drone detection using convolutional neural networks with acoustic STFT features. In Proceedings of the 15th IEEE International Conference on Advanced Video and Signals-based Surveillance (AVSS), Auckland, New Zealand, 27–30 November 2018; pp. 1–6.
- Bernardini, A.; Mangiatordi, F.; Pallotti, E.; Capodiferro, L. Drone detection by acoustic signature identication. Electron. Imaging 2017, 2017, 60–64.
- Hauzenberger, L.; Ohlsson, E.H. Drone Detection Using Audio Analysis. Master’s Thesis, Department of Electrical and Information Technology, Faculty of Engineering, LTH, Lund University, Lund, Sweden, 2015.
- Harvey, B.; O’Young, S. Acoustic detection of a xed-wing UAV. Drones 2018, 2, 4.
- Yang, C.; Wu, Z.; Chang, X.; Shi, X.; Wo, J.; Shi, Z. DOA Estimation Using Amateur Drones Harmonic Acoustic Signals. In Proceedings of the 2018 IEEE 10th Sensor Array and Multichannel Signal Processing Workshop (SAM), Sheffield, South Yorkshire, 8–11 July 2018; pp. 587–591.
- Kim, J.; Park, C.; Ahn, J.; Ko, Y.; Park, J.; Gallagher, J.C. Real-time UAV sound detection and analysis system. In Proceedings of the 2017 IEEE Sensors Applications Symposium (SAS), Glassboro, NJ, USA, 13–15 March 2017; pp. 1–5.
- Siriphun, N.; Kashihara, S.; Fall, D.; Khurat, A. Distinguishing Drone Types Based on Acoustic Wave by IoT Device. In Proceedings of the 2018 22nd International Computer Science and Engineering Conference (ICSEC), Chiang Mai, Thailand, 21–24 November 2018; pp. 1–4.
- Droneshield. Dronesentry. 2020. Available online: https://www.droneshield.com/sentry (accessed on 13 January 2022).
- Chang, X.; Yang, C.; Wu, J.; Shi, X.; Shi, Z. A surveillance system for drone localization and tracking using acoustic arrays. In Proceedings of the IEEE 10th Sensor Array Multichannel Signal Process Workshop (SAM), Sheffield, UK, 8–11 July 2018; pp. 573–577.
- Al-Emadi, S.; Al-Ali, A.; Mohammad, A.; Al-Ali, A. Audio based drone detection and identication using deep learning. In Proceedings of the 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 459–464.
- Opromolla, R.; Fasano, G.; Accardo, D. A vision-based approach to UAV detection and tracking in cooperative applications. Sensors 2018, 18, 3391.
- Rozantsev, A.; Lepetit, V.; Fua, P. Detecting flying objects using a single moving camera. IEEE Trans. Pattern Anal. Mach. Intell. 2017, 39, 879–892.
- Park, J.; Kim, D.H.; Shin, Y.S.; Lee, S. A comparison of convolutional object detectors for real-time drone tracking using a PTZ camera. In Proceedings of the 2017 17th International Conference on Control, Automation and Systems (ICCAS), Jeju, Korea, 18–21 October 2017; pp. 696–699.
- Nalamati, M.; Kapoor, A.; Saqib, M.; Sharma, N.; Blumenstein, M. Drone Detection in Long-Range Surveillance Videos. In Proceedings of the 2019 16th IEEE International Conference on Advanced Video and Signal Based Surveillance (AVSS), Taipei, Taiwan, 18–21 September 2019; pp. 1–6.
- Müller, T. Robust drone detection for day/night counter-UAV with static VIS and SWIR cameras. Proc. SPIE 2017, 10190, 302–313.
- Magoulianitis, V.; Ataloglou, D.; Dimou, A.; Zarpalas, D.; Daras, P. Does deep super-resolution enhance UAV detection. In Proceedings of the 2019 16th IEEE International Conference on Advanced Video and Signal Based Surveillance (AVSS), Taipei, Taiwan, 18–21 September 2019; pp. 1–6.
- Birch, G.C.; Woo, B.L. Counter Unmanned Aerial Systems Testing: Evaluation of VIS SWIR MWIR and LWIR Passive Imagers; SNL-NM: Albuquerque, NM, USA, 2017; Tech. Rep.; SAND2017-0921 650791.
- Chen, H.; Wang, Z.; Zhang, L. Collaborative spectrum sensing for illegal drone detection: A deep learning-based image classification perspective. China Commun. 2020, 17, 81–92.
- Ringwald, T.; Sommer, L.; Schumann, A.; Beyerer, J.; Stiefelhagen, R. UAV-Net: A fast aerial vehicle detector for mobile platforms. In Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition, CVPR Workshops, Long Beach, CA, USA, 14–19 June 2019; pp. 1–9.
- Craye, C.; Ardjoune, S. Spatio-temporal semantic segmentation for drone detection. In Proceedings of the 16th IEEE International Conference on Advanced Video and Signal Based Surveillance (AVSS), Taipei, Taiwan, 18–21 September 2019; pp. 1–5.
- Sapkota, K.R.; Roelofsen, S.; Rozantsev, A.; Lepetit, V.; Gillet, D.; Fua, P.; Martinoli, A. Vision-based unmanned aerial vehicle detection and tracking for sense and avoid systems. In Proceedings of the 2016 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS 2016), Daejeon, Korea, 9–14 October 2016; pp. 1556–1561.
- Aker, C.; Kalkan, S. Using deep networks for drone detection. In Proceedings of the 14th IEEE International Conference on Advanced Video and Signal based Surveillance (AVSS 2017), Lecce, Italy, 29 August–1 September 2017; pp. 1–6.
- Zhu, P.; Wen, L.; Du, D.; Bian, X.; Ling, H.; Hu, Q.; Nie, Q.; Cheng, H.; Liu, C.; Chenfeng, L.; et al. VisDrone-DET2018: The vision meets drone object detection in image challenge results. In Proceedings of the 15th European Conference, Munich, Germany, 8–14 September 2018; pp. 1–30.
- Schumann, A.; Sommer, L.; Klatte, J.; Schuchert, T.; Beyerer, J. Deep cross-domain ying object classication for robust UAV detection. In Proceedings of the 14th IEEE International Conference on Advanced Video and Signal based Surveillance (AVSS 2017), Lecce, Italy, 29 August–1 September 2017; pp. 1–6.
- Wang, L.; Ai, J.; Zhang, L.; Xing, Z. Design of airport obstacle free zone monitoring UAV system based on computer vision. Sensors 2020, 20, 2475.
- Saqib, M.; Khan, S.D.; Sharma, N.; Blumenstein, M. A study on detecting drones using deep convolutional neural networks. In Proceedings of the 14th IEEE Int. Conf. Adv. Video Signal Based Surveill. (AVSS), Lecce, Italy, 29 August–1 September 2017; pp. 1–5.
- Cigla, C.; Thakker, R.; Matthies, L. Onboard stereo vision for drone pursuit or sense and avoid. In Proceedings of the 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition Workshops (CVPRW), Salt Lake City, UT, USA, 18–22 June 2018; pp. 738–746.
- Crivellaro, A.; Rad, M.; Verdie, Y.; Yi, K.M.; Fua, P.; Lepetit, V. A novel representation of parts for accurate 3D object detection and tracking in monocular images. In Proceedings of the IEEE International Conference on Computer Vision (ICCV), Santiago, Chile, 7–13 December 2015; pp. 4391–4399.
- Liu, H.; Qu, F.; Liu, Y.; Zhao, W.; Chen, Y. A drone detection with aircraft classication based on a camera array. In Proceedings of the 4th International Conference on Structure, Processing and Properties of Materials (SPPM 2018), Dhaka, Bangladesh, 1–3 March 2018; Volume 322. no. 5, Art. no. 052005.
- Wellig, P.; Speirs, P.; Schupbach, C.; Oeschlin, R.; Renker, M.; Boeniger, U.; Pratisto, H. Radar Systems and Challenges for C-UAV. In Proceedings of the 19th International Radar Symposium IRS 2018, Bonn, Germany, 20–22 June 2018.
- Torvik, B.; Olsen, K.E.; Griffiths, H. Classification of birds and UAVs based on radar polarimetry. IEEE Geosci. Remote Sens. Lett. 2016, 13, 13051309.
- Ren, J.; Jiang, X. Regularized 2-D complex-log spectral analysis and subspace reliability analysis of micro-Doppler signature for UAV detection. Pattern Recognit. 2017, 69, 225–237.
- Kim, B.K.; Kang, H.-S.; Park, S.-O. Drone classication using convolutional neural networks with merged Doppler images. IEEE Geosci. Remote Sens. Lett. 2017, 14, 38–42.
- Mahafza, B.R. Radar Systems Analysis and Design Using MATLAB; CRC Press: Boca Raton, FL, USA, 2013.
- Li, C.J.; Ling, H. An investigation on the radar signatures of small consumer drones. IEEE Antennas Wirel. Propag. Lett. 2017, 16, 649–652.
- Shin, D.-H.; Jung, D.-H.; Kim, D.-C.; Ham, J.-W.; Park, S.-O. A distributed FMCW radar system based on fiber-optic links for small drone detection. IEEE Trans. Instrum. Meas. 2017, 66, 340–347.
- Mizushima, T.; Nakamura, R.; Hadama, H. Reection characteristics of ultra-wideband radar echoes from various drones in flight. In Proceedings of the IEEE Topical Conference on Wireless Sensors and Sensor Networks (WiSNeT), San Antonio, TX, USA, 17–20 January 2020.
- Torvik, B.; Knapskog, A.; Lie-Svendsen, O.; Olsen, K.E.; Griffiths, H.D. Amplitude modulation on echoes from large birds. In Proceedings of the 11th European Radar Conference, Rome, Italy, 8–10 October 2014; pp. 177–180.
- Guay, R.; Drolet, G.; Bray, J.R. Measurement and modelling of the dynamic radar cross-section of an unmanned aerial vehicle. IET Radar Sonar Navigat. 2017, 11, 1155–1160.
- Stateczny, A.; Lubczonek, J. FMCW radar implementation in river information services in poland. In Proceedings of the 16th International Radar Symposium (IRS), Dresden, Germany, 24–26 June 2015; pp. 852–857.
- Farlik, J.; Kratky, M.; Casar, J.; Stary, V. Multispectral detection of commercial unmanned aerial vehicles. Sensors 2019, 19, 1517.
- Eriksson, N. Conceptual Study of a Future Drone Detection System-Countering a Threat Posed by a Disruptive Technology. Master’s Thesis, Chalmers University Technology, Gothenburg, Sweden, 2018.
- Chen, V.C. The Micro-Doppler Effect in Radar; Artech House: Boston, MA, USA, 2019.
- Kim, B.K.; Kang, H.-S.; Park, S.-O. Experimental analysis of small drone polarimetry based on micro-Doppler signature. IEEE Geosci. Remote Sens. Lett. 2017, 14, 1670–1674.
- Fang, G.; Yi, J.; Wan, X.; Liu, Y.; Ke, H. Experimental research of multistatic passive radar with a single antenna for drone detection. IEEE Access 2018, 6, 33542–33551.
- Colorado, J.; Perez, M.; Mondragon, I.; Mendez, D.; Parra, C.; Devia, C.; Martinez-Moritz, J.; Neira, L. An integrated aerial system for landmine detection: SDR-based ground penetrating radar onboard an autonomous drone. Adv. Robot. 2017, 31, 791–808.
- Rahman, S.; Robertson, D.A. Millimeter-wave micro-Doppler measurements of small UAVs. Proc. SPIE 2017, 10188, 101880T.
- Drozdowicz, J.; Wielgo, M.; Samczynski, P.; Kulpa, K.; Krzonkalla, J.; Mordzonek, M.; Bryl, M.; Jakielaszek, Z. 35 GHz FMCW drone detection system. In Proceedings of the 17th International Radar Symposium (IRS 2016), Krakow, Poland, 10–12 May 2016; pp. 1–4.
- Fontana, R.J.; Richley, E.A.; Marzullo, A.J.; Beard, L.C.; Mulloy, R.W.T.; Knight, E.J. An ultra wideband radar for micro air vehicle applications. In Proceedings of the 2002 IEEE Conference on Ultra Wideband Systems and Technologies (IEEE Cat. No.02EX580), Baltimore, MD, USA, 21–23 May 2002; pp. 187–191.
- Liu, Y.; Wan, X.; Tang, H.; Yi, J.; Cheng, Y.; Zhang, X. Digital television based passive bistatic radar system for drone detection. In Proceedings of the IEEE Radar Conference (RadarConf), 8–12 May 2017; pp. 1493–1497.
- Aldowesh, A.; BinKhamis, T.; Alnuaim, T.; Alzogaiby, A. Low Power Digital Array Radar for Drone Detection and Micro-Doppler Classification. In Proceedings of the 2019 Signal Processing Symposium (SPSympo), Krakow, Polan, 17–19 September 2019; pp. 203–206.
- Jian, M.; Lu, Z.; Chen, V.C. Drone detection and tracking based on phase-interferometric Doppler radar. In Proceedings of the 2018 IEEE Radar Conference (RadarConf18), Oklahoma City, OK, USA, 23–27 April 2018; pp. 1146–1149.
- Semkin, V.; Yin, M.; Hu, Y.; Mezzavilla, M.; Rangan, S. Drone Detection and Classification Based on Radar Cross Section Signatures. In Proceedings of the 2020 International Symposium on Antennas and Propagation (ISAP), Osaka, Japan, 25–28 January 2021; pp. 223–224.
- Jarabo-Amores, M.P.; Mata-Moya, D.; Hoyo, P.J.G.; Bárcena-Humanes, J.; Rosado-Sanz, J.; Rey-Maestre, N.; Rosa-Zurera, M. Drone detection feasibility with passive radars. In Proceedings of the 15th European Radar Conference (EuRAD), Madrid, Spain, 26–28 September 2018; pp. 313–316.
- Robin Radar Systems. Elvira. 2020. Available online: https://www.robinradar.com/elvira-anti-drone-system (accessed on 13 January 2022).
- Björklund, S. Target Detection and Classification of Small Drones by Boosting on Radar Micro-Doppler. In Proceedings of the 2018 15th European Radar Conference (EuRAD), Madrid, Spain, 26–28 September 2018; pp. 182–185.
- Güvenç, I.; Ozdemir, O.; Yapici, Y.; Mehrpouyan, H.; Matolak, D. Detection, localization, and tracking of unauthorized UAS and jammers. In Proceedings of the 2017 IEEE/AIAA 36th Digital Avionics Systems Conference (DASC), St. Petersburg, FL, USA, 17–21 September2017; pp. 1–10.
- Balleri, A. Measurements of the Radar Cross Section of a nano-drone at K-band. In Proceedings of the 2021 IEEE 8th International Workshop on Metrology for AeroSpace (MetroAeroSpace), Naples, Italy, 23–25 June 2021; pp. 283–287.
- Al-Nuaim, T.; Alam, M.; Aldowesh, A. Low-Cost Implementation of a Multiple-Input Multiple-Output Radar Prototype for Drone Detection. In Proceedings of the 2019 International Symposium ELMAR, Zadar, Croatia, 23–25 September 2019; pp. 183–186.
- CRFS. Drone Detection: Myths and Reality. 2018. Available online: https://www.crfs.com/blog/drone-detection-myths-and-reality/ (accessed on 13 January 2022).
- Shi, X.; Yang, C.; Xie, W.; Liang, C.; Shi, Z.; Chen, J. Anti-drone system with multiple surveillance technologies: Architecture, implementation, and challenges. IEEE Commun. Mag. 2018, 56, 68–74.
- Ezuma, M.; Erden, F.; Anjinappa, C.K.; Ozdemir, O.; Guvenc, I. Micro-UAV detection and classication from RF fingerprints using machine learning techniques. In Proceedings of the 2019 IEEE Aerospace Conference, Big Sky, MT, USA, 2–9 March 2019; pp. 1–13.
- CRFS. DroneDefense. 2020. Available online: https://pages.crfs.com/hubfs/CR-002800-GD-2-DroneDefense%20Brochure.pdf (accessed on 12 January 2022).
- Allahham, M.S.; Khattab, T.; Mohamed, A. Deep learning for RFbased drone detection and identication: A multi-channel 1-D convolutional neural networks approach. In Proceedings of the 2020 IEEE International Conference on Information Technology (ICIoT), Doha, Qatar, 2–5 February 2020; pp. 112–117.
- Al-Sa’d, M.F.; Al-Ali, A.; Mohamed, A.; Khattab, T.; Erbad, A. RF based drone detection and identication using deep learning approaches: An initiative towards a large open source drone database. Future Gener. Comput. Syst. 2019, 100, 86–97.
- Nguyen, P.; Truong, H.; Ravindranathan, M.; Nguyen, A.; Han, R.; Vu, T. Matthan: Drone presence detection by identifying physical signatures in the drone’s RF communication. In Proceedings of the 15th ACM International Conference on Mobile Systems, Applications, and Services, Niagara Falls, NY, USA, 19–23 June 2017; pp. 211–224.
- Rodhe and Schwarz. R&S Ardonis. 2020. Available online: https://scdn.rohde-schwarz.com/ur/pws/dl_downloads/dl_common_library/dl_brochures_and_datasheets/pdf_1/ARDRONIS_bro_en_5214-7035-12_v0600.pdf (accessed on 13 January 2022).
- Nguyen, P.; Ravindranatha, M.; Nguyen, A.; Han, R.; Vu, T. Investigating cost-effective RF-based detection of drones. In Proceedings of the 2nd Workshop on Micro Aerial Vehicle Networks, Systems, and Applications for Civilian Use, Singapore, 26 June 2016; pp. 17–22.
- DeDrone. RF-300 Data Sheet. 2020. Available online: https://assets.website-files.com/58fa92311759990d60953cd2/5d1e14bc96a76a015d193225_dedrone-rf-300-data-sheet-en.pdf (accessed on 13 January 2022).
- Medaiyese, O.O.; Syed, A.; Lauf, A.P. Machine Learning Framework for RF-Based Drone Detection and Identication System. arXiv 2020, arXiv:2003.02656. Available online: http://arxiv.org/abs/2003.02656 (accessed on 13 January 2022).
- Nie, W.; Han, Z.; Li, Y.; He, W.; Xie, L.; Yang, X.; Zhou, M. UAV Detection and Localization Based on Multi-dimensional Signal Features. IEEE Sens. J. 2021.
- Basak, S.; Rajendran, S.; Pollin, S.; Scheers, B. Drone classification from RF fingerprints using deep residual nets. In Proceedings of the 2021 International Conference on COMmunication Systems & NETworkS (COMSNETS), Bengaluru, India, 5–9 January 2021; pp. 548–555.
- Ezuma, M.; Erden, F.; Anjinappa, C.K.; Ozdemir, O.; Guvenc, I. Detection and Classification of UAVs Using RF Fingerprints in the Presence of Wi-Fi and Bluetooth Interference. IEEE Open J. Commun. Soc. 2020, 1, 60–76.
- Xu, C.; Chen, B.; Liu, Y.; He, F.; Song, H. RF Fingerprint Measurement for Detecting Multiple Amateur Drones Based on STFT and Feature Reduction. In Proceedings of the 2020 Integrated Communications Navigation and Surveillance Conference (ICNS), Virtual Conference, 8–10 September 2020; pp. 4G1-1–4G1-7.
- Nemer, I.; Sheltami, T.; Ahmad, I.; Yasar, A.U.-H.; Abdeen, M.A.R. RF-Based UAV Detection and Identification Using Hierarchical Learning Approach. Sensors 2021, 21, 1947.
- Bisio, I.; Garibotto, C.; Lavagetto, F.; Sciarrone, A.; Zappatore, S. Blind Detection: Advanced Techniques for WiFi-Based Drone Surveillance. IEEE Trans. Veh. Technol. 2019, 68, 938–946.
- Flak, P. Drone Detection Sensor with Continuous 2.4 GHz ISM Band Coverage Based on Cost-Effective SDR Platform. IEEE Access 2021, 9, 114574–114586.
- Kaplan, B.; Kahraman, İ.; Görçin, A.; Çırpan, H.A.; Ekti, A.R. Measurement based FHSS–type Drone Controller Detection at 2.4GHz: An STFT Approach. In Proceedings of the 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Online, 18 November–16 December 2020; pp. 1–6.
- IGelman, S.; Loftus, J.P.; Hassan, A.A. Adversary UAV Localization with Software Defined Radio; Worcester Polytechnic Institute: Worcester, MA, USA, 2019; Tech. Rep.; E-project-041719-144214.
- Miranda, R.K.; Ando, D.A.; da Costa, J.P.C.L.; de Oliveira, M.T. Enhanced Direction of Arrival Estimation via Received Signal Strength of Directional Antennas. In Proceedings of the 2018 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), Louisville, KY, USA, 6–8 December 2018; pp. 162–167.
- Brito, A.; Sebastião, P.; Souto, N. Jamming for Unauthorized UAV Operations-Communications Link. In Proceedings of the 2019 International Young Engineers Forum (YEF-ECE), Costa da Caparica, Portugal, 10 May, 2019; pp. 94–98.
- Ferreira, R.; Gaspar, J.; Souto, N.; Sebastião, P. Effective GPS Jamming Techniques for UAVs Using Low-Cost SDR Platforms. In Proceedings of the 2018 Global Wireless Summit (GWS), Chiang Rai, Thailand, 25–28 November 2018; pp. 27–32.
- Pärlin, K.; Alam, M.M.; le Moullec, Y. Jamming of UAV remote control systems using software defined radio. In Proceedings of the 2018 International Conference on Military Communications and Information Systems (ICMCIS), Warsaw, Poland, 22–23 May 2018; pp. 1–6.
- Fang, L.; Wang, X.H.; Zhou, H.L.; Zhang, K. Design of Portable Jammer for UAV Based on SDR. In Proceedings of the 2018 International Conference on Microwave and Millimeter Wave Technology (ICMMT), Chengdu, China, 7–11 May 2018; pp. 1–3.
- Skorobogatov, G.; Barrado, C.; Salamí, E. Multiple UAV systems: A survey. Unmanned Syst. 2020, 8, 149–169.
- Yavariabdi, A.; Kusetogullari, H.; Celik, T.; Cicek, H. FastUAV-NET: A Multi-UAV Detection Algorithm for Embedded Platforms. Electronics 2021, 10, 724.
- Li, J.; Ye, D.H.; Chung, T.; Kolsch, M.; Wachs, J.; Bouman, C. Multi-target detection and tracking from a single camera in Unmanned Aerial Vehicles (UAVs). In Proceedings of the 2016 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Daejon, Korea, 9–14 October 2016; pp. 4992–4997.
- Sazdić-Jotić, B.; Pokrajac, I.; Bajčetić, J.; Bondžulić, B.; Obradović, D. Single and multiple drones detection and identification using RF based deep learning algorithm. Expert Syst. Appl. 2022, 187, 115928.
- The Most Promising Defense against Militarized Drone Swarms. Available online: https://mindmatters.ai/2021/06/the-most-promising-defense-against-militarized-drone-swarms/ (accessed on 13 January 2022).
- Vladeanu, C.; Nastase, C.; Martian, A. Energy Detection Algorithm for Spectrum Sensing Using Three Consecutive Sensing Events. IEEE Wirel. Commun. Lett. 2016, 5, 284–287.
- Martian, A.; Al Sammarraie, M.J.A.; Vlădeanu, C.; Popescu, D.C. Three-Event Energy Detection with Adaptive Threshold for Spectrum Sensing in Cognitive Radio Systems. Sensors 2020, 20, 3614.
- Urkowitz, H. Energy Detection of Unknown Deterministic Signals. Proc. IEEE 1967, 55, 523–531.
- Ettus Research USRP X310. Available online: https://www.ettus.com/all-products/x310-kit/ (accessed on 12 January 2022).
- Ettus Research Twin-RX RF Daughterboard. Available online: https://www.ettus.com/all-products/twinrx/ (accessed on 12 January 2022).
More
