As digital instrumentation in Nuclear Power Plants (NPPs) is becoming increasingly complex, both attack vectors and defensive strategies are evolving based on new technologies and vulnerabilities. Continued efforts have been made to develop a variety of measures for the cyber defense of these infrastructures, which often consist in adapting security measures previously developed for other critical infrastructure sectors according to the requirements of NPPs. That being said, due to the very recent development of these solutions, there is a lack of agreement or standardization when it comes to their adoption at an industrial level.
To better understand the state of the art in NPP Cyber-Security (CS) measures, in this work, we conduct a Systematic Literature Review (SLR) to identify scientific papers discussing CS frameworks, standards, guidelines, best practices, and any additional CS protection measures for NPPs.
From our literature analysis, it was evidenced that protecting the digital space in NPPs involves three main steps: (i) identification of critical digital assets; (ii) risk assessment and threat analysis; (iii) establishment of measures for NPP protection based on the defense-in-depth model.
To ensure the CS protection of these infrastructures, a holistic defense-in-depth approach is suggested in order to avoid excessive granularity and lack of compatibility between different layers of protection. Additional research is needed to ensure that such a model is developed effectively and that it is based on the interdependencies of all security requirements of NPPs.
- cyber-security
- critical infrastructure
- nuclear power plant
1. Introduction
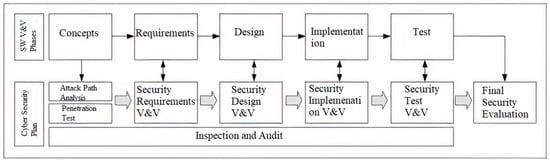
2. Critical Digital Assets in Nuclear Power Plants
3. Risk Assessment and Threat Analysis for NPPs
- –
-
Lack of assessment methods for computer security conditions and identification of security vulnerabilities;
- –
-
Lack of assessment methods for computer risks and threats;
- –
-
The development stage does not consider computer security issues;
- –
-
Lack of consideration for aspects of training and attestation of personnel concerning computer security.The authors of [15][50] suggested classifying attacks by their format/character:
- –
-
Information-gathering attacks;
- –
-
Active attacks to disable or compromise the proper functioning of one or several computers or other devices critical to a facility’s safety or security;
- –
-
Concurrent modes of attack.The authors of [16][23] argued that the vulnerability assessment methodologies proposed by the US Nuclear Regulatory Commission (NRC) require several key additions and changes to increase their efficacy. Some of the changes suggested by the authors include conducting and storing a comprehensive inventory of digital systems and components, conducting more penetration testing, using vulnerability databases and analysis software, and improved use of vulnerability assessment methods.The authors of [14][19] suggested categorizing threats to NPPs into cyber threats at the stage of development of I&C systems and cyber threats at the stage of operation of I&C systems at NPPs. Additionally, these threats could also be sub-divided based on whether they are internal or external.To identify possible risks and overcome the gaps found in the current regulatory frameworks, many vulnerability assessment methodologies have been proposed in the literature. A potential security risk analysis of NPPs should include probability of attack by the adversary, attack purpose, and attack ability [17][42].To evaluate CS risk in accordance with regulatory guides such as RG 5.71, the authors of [18][28] proposed a CS risk model using a Bayesian Network (BN) for a Reactor Protection System (RPS) of a nuclear reactor, as well as a methodology for applying analytical results from a BN model to an event tree model. The model was developed to overcome the limitations of previously used fault trees as a Probabilistic Safety Assessment (PSA) method.Another risk assessment framework was proposed by [19][24]. The framework proposed by these authors evaluates risk by defining the difficulty and consequences of a cyber attack, basing assessment methods on Bayesian belief networks and probabilistic safety assessment methods. The authors demonstrated the feasibility of the proposed framework by quantitatively evaluating several cyber attack scenarios based on the developed models for difficulty and consequences as a case study. Finally, the authors suggested that the framework may be used for risk-informed regulation of cyber attack scenarios and CDAs with quantitative goals, as well as risk-informed CS strategies and related evaluation efficiencies.According to RG 5.71, periodic checking of the I&C systems should be conducted to identify any possible CS vulnerabilities. For this reason, CS vulnerability checking systems, such as the one proposed by [20][31], should be used to reduce the impact of vulnerabilities, as well as to ensure compliance with the automatic check regulatory guidelines. A fundamental requirement of these scanning tools is that they should not generate excessively high network traffic or overhead on the objects to be scanned.The work by [21][45] determined the levels of CS protection for the subsystems and equipment of a digital I&C system of an NPP. These levels were determined using the CS defense-in-depth model, an example of which is shown in Figure 1. The authors tried to identify the potential CS risk factors, namely, assets, threats, and vulnerabilities. The proposed risk analysis was then carried out each of the identified levels.
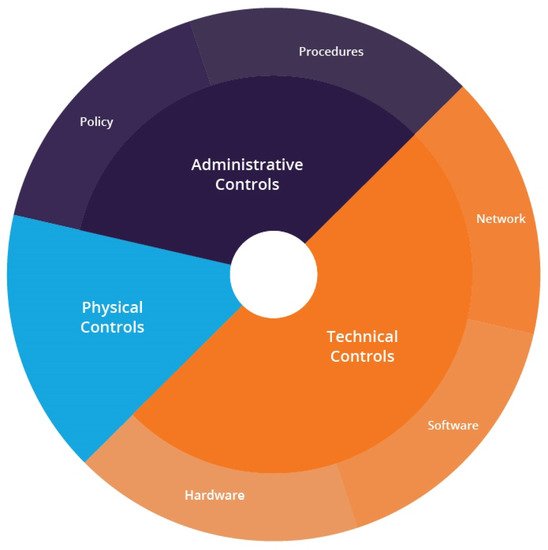 Figure 1. Example of the layered security architecture of the defense-in-depth model.The authors of [12][41] proposed an importance analysis method for cyber attacks against an NPP using the Probabilistic Safety Assessment (PSA) method. The authors started by identifying possible cyber attacks with failure modes. The authors demonstrated the proposed PSA method with two case studies. In the case studies, the risks of two cyber attack scenarios were quantitatively evaluated with two risk metrics: Core Damage Frequency (CDF) and Conditional Core Damage Probability (CCDP). The authors concluded that by identifying significant CDAs and classifying cyber attacks using quantifiable measures, it should be possible to develop a defense strategy against cyber attacks on NPPs that is both reliable and efficient.The authors of [22][51] presented a qualitative methodology for CS assessment that is appropriate for nuclear I&C systems. The authors conducted an assessment based on a questionnaire comprising 162 questions divided into five categories. An evaluation of the questionnaires was then conducted by weighting each response depending on whether the results showed the overall CS status for each category, and they conducted an evaluation of the system as a whole. The authors suggested that this methodology could serve as a CS index at an initial phase of the system development for the CS assessment of nuclear I&C systems. Nonetheless, further research needs to be conducted to assign detailed CS countermeasures in each category.Possible attacks may also be categorized into taxonomies to facilitate both their identification and preventive action planning. The authors of [7] highlighted that it is difficult to study cyber attack taxonomies for NPPs considering the characteristics of ICSs and the inadequacy of research compared to such issues in information technology. The authors suggested a template for a cyber attack taxonomy based on the characteristics of NPPs, exemplified a specific cyber attack case in the template, and proposed a systematic countermeasure selection strategy by matching the countermeasures with CDAs and security control in RG 5.71. The taxonomy included the attack procedure, attack vector, attack consequence, vulnerability, and countermeasure selection.The authors of [23][34] noted the importance of correctly classifying cyber attacks and distinguishing them from fault-induced safety events. For this purpose, the authors developed an event classifier to classify abnormal events in NPPs as either fault-induced safety events or cyber attacks. While the classifier was proven to be successful in distinguishing different types of abnormal events, more work is needed to enable the classification of combinations of safety events and cyber attacks.The authors of [24][20] proposed a Monte-Carlo-based exploration framework for generating cyber attack scenarios in Cyber–Physical Systems (CPSs). The method takes into account various failure modes of attacked components of the CPSs and outputs the possible effects of the cyber threats on the system. According to their analysis, actuators are the most vulnerable CPS components, as their failures may lead to the loss of system functionality and integrity.The authors of [25][22] proposed a method for calculating the degree of risk to a nuclear reactor’s systems based on multiple factors for the purpose of safety. The authors presented a security threat mapping table, which was used to define and specify security problems. An important observation noted by the authors is that to create security profiles, environmental elements, security assumptions, and the organization’s security policy must be analyzed. The model developed by the authors has already been implemented in reactor protection systems that are operating in the Republic of Korea. Nonetheless, additional research on I&CS protection profiles and security functions is suggested.A possible way to study attack vectors is by simulating threat scenarios both theoretically and with the aid of simulation platforms. The authors of [26][32] presented three threat scenarios related to the Electric Power Systems (EPSs) of NPPs. This type of modeling is believed by the authors to be a useful input for security analysis and closed-loop virtual validation via simulation and Fault Tree Analysis (FTA).Another effective way of understanding threats to NPPs is by modeling attack scenarios or attack graphs; this can be done by either taking the security-related details of the NPP system into consideration or not [27][25].The authors of [28][21] described methods of defining attack vectors in NPP systems. Additionally, techniques for reviewing and selecting requirements in RG 5.71 were also described. Finally, methods of integrating the results of the previous techniques to identify possible technical security controls to counter respective attack vectors were also described. To conduct the attack vector analysis process, analysis of the system architecture and of attack vectors, modeling of the target system, assignment of the security level of its CDAs, and investigation of the known vulnerabilities of these CDAs are all suggested.The authors acknowledged that further studies are needed to research the details of the practices of those control requirements and to develop security devices and technologies best fitted to NPP I&C systems.Study of attack procedures, vectors, and consequences should not be conducted only on a theoretical basis, but should be supported by real-life occurrences. An example of such a study is the analysis of the cyber terror attacks against NPPs that occurred in South Korea conducted by [29][27]. This type of analysis aids in understanding the factors motivating the attackers, and also gives a concrete outlook of the consequences of successful attacks on these critical systems.Another study that used historical incident analysis as a basis for developing a quantitative CS assessment method was discussed in [30][52]. The authors proposed organizing initiating threats and their bounding groups for NPPs to determine threats based on actual industrial incidents. It was also suggested to apply the same criteria to Probabilistic Safety Assessments (PSAs) in order to describe scenarios and models of NPP cyber risk. Nonetheless, the authors argued that the quantification of the probability of each scenario should also be conducted in order to understand the likelihood of each attack.
Figure 1. Example of the layered security architecture of the defense-in-depth model.The authors of [12][41] proposed an importance analysis method for cyber attacks against an NPP using the Probabilistic Safety Assessment (PSA) method. The authors started by identifying possible cyber attacks with failure modes. The authors demonstrated the proposed PSA method with two case studies. In the case studies, the risks of two cyber attack scenarios were quantitatively evaluated with two risk metrics: Core Damage Frequency (CDF) and Conditional Core Damage Probability (CCDP). The authors concluded that by identifying significant CDAs and classifying cyber attacks using quantifiable measures, it should be possible to develop a defense strategy against cyber attacks on NPPs that is both reliable and efficient.The authors of [22][51] presented a qualitative methodology for CS assessment that is appropriate for nuclear I&C systems. The authors conducted an assessment based on a questionnaire comprising 162 questions divided into five categories. An evaluation of the questionnaires was then conducted by weighting each response depending on whether the results showed the overall CS status for each category, and they conducted an evaluation of the system as a whole. The authors suggested that this methodology could serve as a CS index at an initial phase of the system development for the CS assessment of nuclear I&C systems. Nonetheless, further research needs to be conducted to assign detailed CS countermeasures in each category.Possible attacks may also be categorized into taxonomies to facilitate both their identification and preventive action planning. The authors of [7] highlighted that it is difficult to study cyber attack taxonomies for NPPs considering the characteristics of ICSs and the inadequacy of research compared to such issues in information technology. The authors suggested a template for a cyber attack taxonomy based on the characteristics of NPPs, exemplified a specific cyber attack case in the template, and proposed a systematic countermeasure selection strategy by matching the countermeasures with CDAs and security control in RG 5.71. The taxonomy included the attack procedure, attack vector, attack consequence, vulnerability, and countermeasure selection.The authors of [23][34] noted the importance of correctly classifying cyber attacks and distinguishing them from fault-induced safety events. For this purpose, the authors developed an event classifier to classify abnormal events in NPPs as either fault-induced safety events or cyber attacks. While the classifier was proven to be successful in distinguishing different types of abnormal events, more work is needed to enable the classification of combinations of safety events and cyber attacks.The authors of [24][20] proposed a Monte-Carlo-based exploration framework for generating cyber attack scenarios in Cyber–Physical Systems (CPSs). The method takes into account various failure modes of attacked components of the CPSs and outputs the possible effects of the cyber threats on the system. According to their analysis, actuators are the most vulnerable CPS components, as their failures may lead to the loss of system functionality and integrity.The authors of [25][22] proposed a method for calculating the degree of risk to a nuclear reactor’s systems based on multiple factors for the purpose of safety. The authors presented a security threat mapping table, which was used to define and specify security problems. An important observation noted by the authors is that to create security profiles, environmental elements, security assumptions, and the organization’s security policy must be analyzed. The model developed by the authors has already been implemented in reactor protection systems that are operating in the Republic of Korea. Nonetheless, additional research on I&CS protection profiles and security functions is suggested.A possible way to study attack vectors is by simulating threat scenarios both theoretically and with the aid of simulation platforms. The authors of [26][32] presented three threat scenarios related to the Electric Power Systems (EPSs) of NPPs. This type of modeling is believed by the authors to be a useful input for security analysis and closed-loop virtual validation via simulation and Fault Tree Analysis (FTA).Another effective way of understanding threats to NPPs is by modeling attack scenarios or attack graphs; this can be done by either taking the security-related details of the NPP system into consideration or not [27][25].The authors of [28][21] described methods of defining attack vectors in NPP systems. Additionally, techniques for reviewing and selecting requirements in RG 5.71 were also described. Finally, methods of integrating the results of the previous techniques to identify possible technical security controls to counter respective attack vectors were also described. To conduct the attack vector analysis process, analysis of the system architecture and of attack vectors, modeling of the target system, assignment of the security level of its CDAs, and investigation of the known vulnerabilities of these CDAs are all suggested.The authors acknowledged that further studies are needed to research the details of the practices of those control requirements and to develop security devices and technologies best fitted to NPP I&C systems.Study of attack procedures, vectors, and consequences should not be conducted only on a theoretical basis, but should be supported by real-life occurrences. An example of such a study is the analysis of the cyber terror attacks against NPPs that occurred in South Korea conducted by [29][27]. This type of analysis aids in understanding the factors motivating the attackers, and also gives a concrete outlook of the consequences of successful attacks on these critical systems.Another study that used historical incident analysis as a basis for developing a quantitative CS assessment method was discussed in [30][52]. The authors proposed organizing initiating threats and their bounding groups for NPPs to determine threats based on actual industrial incidents. It was also suggested to apply the same criteria to Probabilistic Safety Assessments (PSAs) in order to describe scenarios and models of NPP cyber risk. Nonetheless, the authors argued that the quantification of the probability of each scenario should also be conducted in order to understand the likelihood of each attack.4. Measures for NPP Protection
After obtaining an understanding of the threats and vulnerabilities that afflict the digital systems of NPPs, it is necessary to establish measures to protect them from computer threats and techniques for the mitigation of cyber attacks. As indicated by [31][30], the cyber/physical security of NPPs may require the management of different levels/layers of protection in accordance with the standard set by RG 5.71. According to [14][19], standards of minimum acceptable risks are challenging to develop due to the constant progress and modernization of information technology and digital systems, in addition to the new threats and tools that are constantly being developed. For the same reason, standardized measures for protection from or mitigation of cyber attacks are just as arduous to define.In the series of documents published by the International Atomic Energy Agency (IAEA) [15][50], it was suggested that the basic principle to follow to protect against computer threats is the use of the defense-in-depth model. This model is based on the idea of using multiple layers of often independent protection measures to guarantee multi-level protection without single points of failure.The authors of [14][19] described an action list of activities to conduct during the development, implementation, maintenance, and improvement of computer security in NPPs in accordance with the procedures defined in the international standards and regulatory guides.Approaches to CS threat prevention, detection, and response of (IT) systems that have proven to be successful have also been suggested to be used for I&C systems of NPPs. Naturally, differences in real-time operational requirements, distinct communication protocols, and requirements for continuous availability of the systems need to be considered when adapting these approaches for I&C systems in NPPs.The authors of [32][49] proposed specific approaches to implementing a framework for prevention, detection, and response for I&C systems. For prevention, the authors suggested monitoring and auditing I&C systems to meet the real-time requirements. For detection, an intrusion detection approach based on physical data was proposed in order to deal with the distinct communication protocols. Finally, for response, the intrusion-tolerant control was proposed to maintain continuous availability. According to the authors, this overall solution, when combined with a safety design principle, should provide an overall solution for CS of I&C systems.In addition to to adapted frameworks for CS, a number of approaches specifically developed for the CS of I&C systems of NPPs have appeared in the literature.The authors of [33][35] proposed a framework for CS assessment using an Early Fault Diagnostics System (EDS) during the operational stage. The EDS aims to prevent the evolution of the incident/accident by using a troubleshooting process in any plant operational mode. This would allow plant operators to identify any significant deviation of plant parameters from their normal value, well before reaching any undesired threshold that would potentially lead to a prohibited plant state, together with the cause that generated the deviation.The authors of [34][47] laid out a new systems-engineering-focused approach for addressing threats to NPPs, which they named System-Aware Security (SAS) for NPPs. The authors theoretically demonstrated a possible application of the methodology in order to address cyber attacks employed via embedded infections in NP systems. The authors highlighted that the approach still has several limitations, and further work in component integration and security analysis may be necessary to improve the model.To improve the robustness of key equipment under cyber attacks, the authors of [35][43] proposed a localized kit for key equipment in a process as a complementary detection method. The authors highlighted that the proposed model reduced the total number of variables used and improved the computational speed when compared to other models.The authors of [36][33] proposed a quantitative method for evaluating changes in CS when specific CS controls are applied in NPPs. The amount of improvement achieved by security controls was defined as the reduction of the probability that the system would fail to protect essential functions from a cyber attack. Additionally, the authors applied the concept of the intrusion-tolerant system. According to this concept, the tolerance to intrusion of a system is defined as the extent to which the system is able to provide the minimum level of safe operation when facing unexpected intrusions. The authors then constructed an event tree with the investigated intrusion-tolerant strategies for the case of protecting the availability of essential functions. The authors concluded that there still exist some limitations in estimating the efficacy of CS controls due to the lack of detail in the methods for obtaining the probability of the detection strategy and the GD strategy.Many researchers have realized in recent years that the concept of having a multi-layered CS defense system should not be exclusive to the implementation of safety and security measures, such as firewalls, intrusion detection systems, and fail-safe safety systems. It is not wise to expect that these measures will be able to anticipate all attack vectors and, as such, it is highly recommended that operators are readily responsive when it comes to detecting and preventing these types of incidents.The authors of [37][40] reviewed the role of reactor operators in detecting and mitigating cyber attacks in nuclear power plants. The authors introduced the idea of a cyber concept of operations, in which operators treat cyber intrusions in the same way that they would other hardware faults at the plant. A pilot study was conducted, in which reactor operators were asked to and succeeded in navigating the plant to a safe state despite cyber spoofing across multiple scenarios. The findings from the experiments confirmed that having dedicated operators can help ensure plant resilience to cyber attacks.By using n-conventional Fault Tree (FT) analysis, the author of kim2017systematic conducted a study on the effects of safety system unavailability on plant safety and analyzed human actions based on emergency operating procedures. Based on this combined analysis, the authors suggested a novel method of systematically developing cyber attack propagation scenarios, where a cyber attack is linked to its consequences. The analysis was focused on the operator’s actions and the effects on the system in case of the failure of action. Future research should focus on the study of the generation of the initiating event of a cyber attack, which was not discussed in this author’s work. In addition, operator behavior should also be analyzed in future studies in order to understand the effects of different types of training and any other factors that may influence their behavior.When it comes to evaluating the operator’s ability to successfully respond to malicious attacks or undesired events, the authors of [38] suggested using a cyber emulation of a digital control system coupled with a training simulator of a Generic Pressurized Water Reactor (GPWR). In an experiment set up by the authors, licensed operators were asked to complete a series of scenarios on the simulator, some of which were purposefully obfuscated. The results from the experiments showed that even after obfuscating certain indicators, the combination of security systems and operator actions was sufficient to detect the attack and protect the system. Limitations in the number of participants and indicator values should be overcome in later iterations of such experiments to allow for more realistic evaluations.To support cyber attack response and effective risk assessment, reduce the risk of cyber attacks, and improve the resilience of NPPs, the authors of [39][36] proposed a finite-horizon semi-Markov general-sum game between a defender and an attacker to obtain the time-sensitive attack response strategy and the real-time risk assessment in NPPs. By applying the model and the method to a simplified digital feedwater control system for a generic pressurized water reactor, the authors showed that the defender’s optimal strategy varies with different system states and different amounts of time remaining in the game. The authors concluded that more research must be conducted in order to collect datasets, understand real-world defender—attacker interactions, and integrate changes in operation due to malfunctioning or other unexpected occurrences.Unfortunately, it is not possible to conduct vulnerability tests directly on NPPs; this is because of the risks of adverse effects, which could provoke serious damages to the systems and interrupt their functioning. To circumvent this issue, testbeds are often used to test technical solutions.The authors of [40][18] suggested the design of a CS testbed for a Digital Plant Protection System (DPPS) and Plant Monitoring and Annunciator System (PMAS). Network connectivity was considered an important element for the analysis and design of the cyber security testbed. Unfortunately, the testbed has yet to be completed. Once completed, the authors have planned the development of a test to detect malware, such as APT for control systems, as well as a vulnerability test.The authors of [41][26] also presented the implementation of a cyber–physical testbed. Their testbed included the implementation of two simulated and interconnected Critical Infrastructures (CIs), namely, a power grid and a nuclear plant. Additionally, the following components were included in the testbed:- –
-
A simulated power market for providing the cost of the provided energy;
- –
-
An actual Programmable Logic Controller (PLC), which is interconnected with a specific bus of the power network;
- –
-
An emulated cyber network that interconnects and controls all of the aforementioned elements.The novelty of this system comes from interconnecting this diverse range of elements and, by doing so, aiding the understanding of the consequences of the interdependencies between the different systems. The authors showed that the effects of network parameters on a coordinated attack could be significant. The authors are planning to make use of the implementation to run more advanced experiments, which will include the actions of real operators in the cyber–physical testing/simulation process. Additionally, they plan to implement a set of countermeasures to tackle and mitigate the attacks based on the exchanged signals and their statistical analysis to detect anomalies.
