Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Javier Bermejo Higuera and Version 3 by Jessie Wu.
The rapid proliferation of Internet of Things (IoT) networks in Colombia and various global regions has unquestionably resulted in a significant increase in cyberattacks. This rapid expansion of interconnected devices carries significant implications for individuals, organizations, and governing entities.
- machine learning techniques
- cyberattack prevention
- Internet of Things (IoT)
1. Introduction
As a result, deficiencies in security updates and transparency regarding Internet of Thing (IoT) T device security, coupled with unsafe internet deployment practices, leave these devices vulnerable to cybercriminal activities. Periodic assessments conducted by cybersecurity firms highlight the suboptimal security landscape of IoT infrastructure. Given the widespread deployment of IoT devices not only in private environments [1][4], but also in a variety of settings, including critical infrastructure installations [2][1], it is imperative to protect these devices and their associated infrastructures. Numerous techniques are currently available to identify cyberattacks targeting IoT infrastructures. Machine-based methodologies offer distinct advantages over signature-based analysis, such as enhanced detection precision and reduced false positives [3] (p. 5), while also facilitating the identification of both anomalies and novel attack characteristics. Nevertheless, these approaches are not devoid of drawbacks [4][5], such as the demand for supplementary hardware resources and diminished data-processing velocities.
A viable countermeasure to this burgeoning menace involves the employment of machine learning methodologies. By harnessing intelligent algorithms, detection and prevention of cyber-intrusions upon IoT infrastructures become feasible. Nevertheless, it is essential to recognize these techniques’ limitations and necessitate scrupulous supervision and perpetual modification to outpace the everchanging tactics employed by cyber-malefactors [2][1].
-
To effectively attenuate these hazards, it is imperative for individuals, organizations, and governing authorities to engage in close cooperation towards devising comprehensive cybersecurity protocols tailored explicitly for IoT systems [2][1]. Unswerving vigilance and anticipatory endeavors are crucial in maintaining a strategic advantage over nefarious actors seeking to capitalize on susceptibilities within Colombia’s rapidly developing digital terrain [2][1].
-
This document provides an explanation of the utilization of machine learning algorithms within the Internet of Things (IoT) security landscape [5][6]. The transparency and traceability afforded by blockchain facilitate secure and verifiable data transactions, enabling ML algorithms to operate on trustworthy datasets [6][7]. This synergy not only fortifies the reliability of AI-driven decisions in IoT applications but also establishes a resilient defense against potential security breaches, providing a meticulous overview of fundamental principles and key attributes technology, elucidating how these features can be strategically harnessed to augment the capabilities of AI in application issues.
-
In general, each cyber-attack has a solution that improves the impact on the economy [7][8] and the introduction of good practices for globalization change:
-
Symbiotic integration for decentralized economies: Delving into the synergistic potential of integrating AI and blockchain [8][9], elucidating how this union could cultivate a novel ecosystem characterized by decentralized economic structures. Additionally, outlining the inherent benefits derived from this transformative integration.
-
Comprehensive taxonomy of IoT ecosystem: Offering a meticulous taxonomy encompassing diverse dimensions, including blockchain platforms, architectural frameworks, infrastructure typologies, and consensus protocols. This taxonomy is complemented by an exploration of existing applications of decentralized AI within this comprehensive framework.
-
Examination of practical applications: Presenting a thorough examination and discussion of multiple practical use cases wherein AI applications leverage blockchain technology across various vertical domains.
-
The ongoing research on Internet of Things (IoT) anomaly detection [9][10][10,11] is a rapidly expanding field. This growth necessitates an analysis of application trends and current gaps. The vast majority of publications focus on areas such as network and infrastructure security, sensor monitoring [11][12], and applications for smart homes and smart cities, and are extending into even more sectors. Recent advancements in the field have increased the need to study the numerous applications of anomaly detection [3][6][12][3,7,13] in IoT. This respapesarchr commences with a summary of detection methods based in ML and applications into the Colombia ecosystem, followed by a discussion of categorizing anomaly detection algorithms in IoT. Subsequently, researcherswe scrutinize current publications to identify distinct application domains, examining selected documents based on researchers'our search criteria. Different surveys encompass 64 documents among recent publications released between January 2019 and July 2021. In these recent publications, researcherswe observe a shortage of anomaly detection methodologies in IoT [13][14], for instance, when confronting the integration of systems with various sensors obtained with distributive data analytics, changes in data and conceptual shifts, and data augmentation where there is a scarcity of ground truth data.
2. Advanced Persistent ThreadT Comparison and Actual Perspective
Currently, advanced persistent threats (APTs) known to be associated with cyberattacks around the world have an imminent vision related with an actual perspective [14][18]. ENISA establishes a point of reference for all threats applying to assets related to information and communication technology (ICT) [15][19] and different scenarios such as IoT and Industrial Internet of Things (IIoT), where collaborative efforts among governments, industry leaders, and organizations are imperative to formulate comprehensive strategies that effectively tackle the expanding threat landscape surrounding IoT networks. Through strategic investments in cutting-edge security solutions and the adoption of proactive measures, including robust encryption protocols and advanced intrusion detection systems, reswearchers can successfully mitigate the risks associated with cyberattacks on critical infrastructures. Ref. [15][19] (p. 11) indicates an attacks incidents taxonomy related with a combination of cybercrime subject (motive), action (method), object (outcome). EUROPOL’s European Cybercrime Centre has categorized incidents based on their type and event, which is a crucial aspect of incident management along two vectors where organizations can effectively analyze and respond to various types of events in a structured manner [16][20]. With regard to APT events in a critical cyber infrastructure (CCI) in a digital ecosystem, APT types are defined by NIST (US National Institute of Standards and Technology) [17][21]. TTPS enabled at the IoT layers (MI-TRE ATT&CK methodology) and consequently areas of interest [18][22] such as industry, smart grids, transport and medical services involve the implementation of restricted requirements based on security, privacy and trust. The cyber-physical perspective with detection and prevention systems has some paradigms in IoT systems related to perimeters. I. Stellios et al. [19][23] describe edge nodes as (i) edge nodes (e.g., RFIDs, sensors), (ii) edge computing (fog), and (iii) communications. Other paradigms to consider are the OT/IoT reference security architecture NIST SP 800-82r3 [20][24] or scenarios, such as Mirai, and DDOS cyber-attacks [21][25] when there are undefined parameters and constant changes, high heterogeneity, autonomous entities, inclusion of non-traditional devices, and limited permission granularity. Along these lines, the expansion of DDOS cyber-attacks is significant among hyper-connected devices as follows [17][21]:-
Computers in general;
-
Network nodes;
-
Mobile devices;
-
Wearable items;
-
Video games;
-
Home automation items;
-
Storage devices;
-
Surveillance items;
-
Work devices;
-
Domestic virtual assistants;
-
Cars;
-
Media and TV items;
-
Appliances examples;
-
Other generic items.
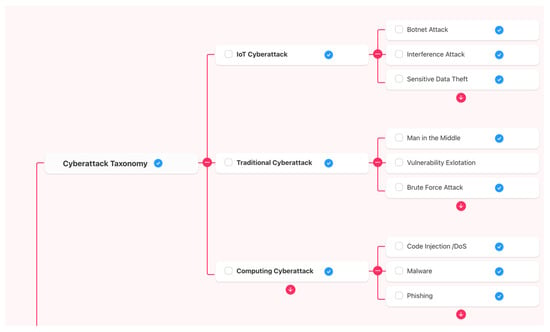
3. Common Systems Behavioral (CSB) Sources Used for Attack Detection
The consequence related with taxonomy use, according to [23][27], is that the lifecycle of APT and IoT (implementation 5G in Colombia) must contribute an Annual Cybersecurity Survey 2022–2023 [27][31]. Consequently, a methodology applicable and adaptable in Colombia is created to identify the root cause of approximately 157,000 daily cyberattacks [28][32] suffered by the country, a large percentage of which are aimed at IoT technologies, which can be implemented with the emergence and implementation of the 5G network. The consequence related to taxonomy use, according to [24][28], including the lifecycle of APT and description of some main factors on IoT (5G implementation in Colombia) is attributed in part to the increase of cybercrime in Colombia, according to Annual Cybersecurity Survey 2022–2023 [28][32], with the balance in 2021–2022 of 62% of cybercrime infractions in Colombia. The context in this order of ideas indicates that the cost could exceed USD 90 million by 2025. In [27][31] (page 19) the same report, it indicates that AI for early detection and anticipation of such actions is one of the major challenges in the development of innovative solutions against cyberattacks. Indeed, Colombia has been facing an adversarial context since 2019 [29][33], particularly in relation to behavioral patterns associated with identified advanced persistent threats (APTs) such as APT-related Cyberattacks in Colombia:-
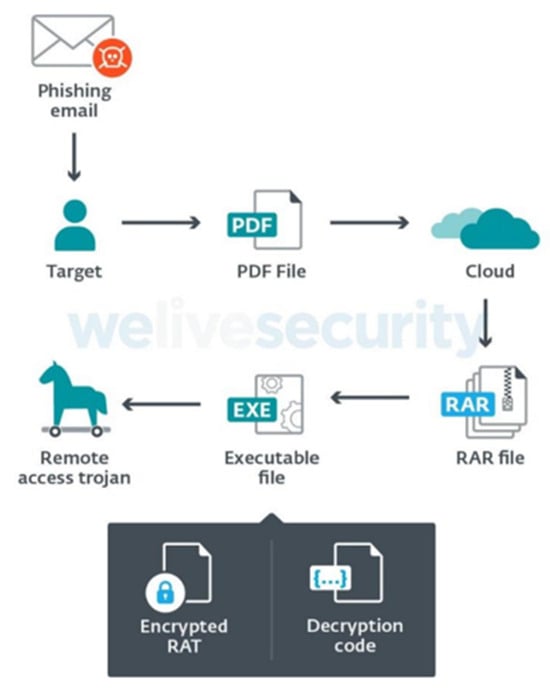
(APT-C-36) [30][34] “Attackers coming from South America carried out continuous targeted attacks against Colombian government institutions as well as important corporations in financial sector, petroleum industry, professional manufacturing”, as per the Spalax Operation in 2021 with a RAT (remote-access Trojan) scuh as: Remcos, njRAT, AsyncRAT, and others (see Figure 2).
-
Alerts instances correlation:
- -
-
Alert instances filters.
- -
-
Alert instances clustering.
- -
-
APT attack scenario.
-
Victim–host IP
- -
-
Preliminary correlation.
- -
-
Log instances community detection.
4. Advanced Persistent ThreadPT and Cyberattacks Detection (ML) and (CPS) Approaches
The first step for detection and identification of an APT behavior [23][35][27,38] is to connect sources by origin and destiny. Depending on the design stage, the TTP fingerprint was specifically developed and configured to detect advanced persistent threat (APT) attacks. This fingerprint leverages the correlation between the attack tree and MITRE framework, which serves as a comprehensive reference for mobile tactics and techniques associated with APT attacks. According to reference [35][38], the attack tree implemented in the fingerprint encompasses all relevant mobile tactics and techniques outlined by the MITRE framework. This ensures that a wide array of potential APT attack vectors can be accurately identified and mitigated through this sophisticated detection system. Related with APT-C 36, there are components for evaluating [29][31][33,35] a CSB where detection systems can identify [22][26] anomalies according to [1][4] behavioral needs:- -
-
Anomaly detection: [6][12][7,13]: Construct a taxonomy [19][23] or ontology [24][28] based [14][18] correlation (Table 1) and convert a BE (behavioral execution) in an input coordinated with a CSB detected. The inclusion analyzes the interrelationships of machine learning use in cybersecurity and CPS [12][13], e.g., virtual MAC spoofing detection [36][39].
-
Number Attributes Description 1 Timestamp The time the alert occurs. 2 Alert_Type The type of alert. 3 Src_Ip The source IP of the attack step. 4 Dest_Ip The destination IP of the attack step. 5 Src_Port The source port number of the attack step. 6 Dest_Port The destination port number of the attack step. 7 Victim_HostIp The IP of the host victimized by the attack step. 8 APT type (associate) The CSB detected (1). Classic attack 9 TTP associate The CSB detected (2). 10 Vector associate The CSB detected (3). 11 Actor associate The CSB detected (4). 12 Purpose associate The CSB detected (5). 13 APT attribution - -
-
Misuse detection: The second dataset is the distance from the data to the nearest neighbor within the cluster or CPS (correlated). Furthermore, the approach rebuilds the data features by using the distances, and formats the data features as logistic regression, naïve Bayes, perceptron, and k-nearest neighbor (k-NN) classifier.
-
