Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Santiago Criollo-C and Version 2 by Camila Xu.
Online, distance, and hybrid study modalities, due to the isolation caused by the pandemic, had an incredible surge. It has been a challenge for higher education institutions to adapt to these changes due to the new educational needs and the digital culture of the new generation of students.
- education
- innovative learning
- learning models
- automation
- Phyton
- web application
1. Introduction
During the last decade, higher education has undergone significant changes marked by the development of technology and its influence on the new generation of students [1][2][1,2]. Current educational models have introduced innovative practices using digital technologies to enhance traditional education methodologies [3]. An example of this are the academic models that use blended learning, e-Learning, and mobile learning, as well as continuous and ubiquitous education initiatives and programs such as MOOCs, online classes, the use of mobile educational applications, augmented reality, virtual reality, web applications, etc. [4]. These models, being new and innovative, reveal a deficiency in learning; the causes of this deficiency can be associated with factors such as educational modality, educational materials and resources, learning challenges, and assessment methods [5]. In a traditional modality, the teacher becomes the main actor of learning; they are the one who defines what and how students learn in the classroom, which is a controlled environment [6]. By eliminating the environment and the control that the teacher exercises over the group, problems increase, especially when the resources, activities, and methods of the face-to-face model are not adapted to the new modality [7]. These factors cause a lack of interest in the student, who by not having the physical presence of the teacher, avoids their participation, which can create gaps in learning that are difficult to identify until they become problems such as academic dropout [8].
Online, distance, and hybrid study modalities, due to the isolation caused by the pandemic, had an incredible surge [9]. It has been a challenge for higher education institutions to adapt to these changes due to the new educational needs and the digital culture of the new generation of students [10]. This adaptation can generate indicators, which must be properly addressed for a correct deployment in the implementation of new strategies and methodologies that use digital technologies in the educational context [11]. In addition, this need for the use of digital technologies in education arises from the new educational modalities and technological contexts in which students and their new learning needs are included [12]. Nowadays, the use of technology plays an important role in education, and an educational model that is shaped using digital technologies and emphasizes student-centered learning activities is possible [4][13][4,13]. The learning process using digital technologies can provide students with a self-paced learning environment [14]. In this way, students can learn according to their learning ability. In addition, it has been shown in several empirical studies that the use of technology can improve academic performance in students [15].
Nowadays, the development of technological skills in the educational context is a priority in formal education from early learning to higher education [16]. All this must go hand in hand with teacher training and professional development, which involves identifying the role of the teacher and the student to transform the learning environment [17]. These skills and innovative educational models supported by emerging technologies contribute directly to the fourth Sustainable Development Goal (SDG) [18]. This goal seeks to improve access to quality education and thus ensure the sustainable development of countries [19].
2. Emerging Digital Technologies in Education
Today’s education has become one of the biggest challenges; in many countries, teachers face material shortages, lack of content, lack of equipment, and lack of opportunities for self-directed learning [20]. To address these challenges, educators are turning to the use of digital technologies to help improve the quality of teaching and learning [21]. The integration of technology in education can give way to the creation of educational models in online, face-to-face, blended, and hybrid modalities [7]. It is for this reason that the use of technology in education has the potential to reach people living in remote places, in conditions of vulnerability, and where there are no educational institutions, teachers, or libraries [22]. Therefore, it is expected that in the future, the use of digital tools will become the basis for the creation of new and innovative learning environments [23]. Higher educational institutions have several challenges to address for the deployment of digital technologies in education, but undoubtedly, a point in favor is the new generations of students [12]. Digital natives have a new way of accessing knowledge; they are technologically advanced, and this contributes to the use of technologies in the educational model [10]. In recent years, initiatives have been developed using digital technologies as a support in the educational model [15][24][15,24]. Some works use mobile applications for learning indigenous languages to preserve the culture of a country [25]. Another example is the use of augmented reality (AR) for learning enhancement in higher education [15][26][27][15,26,27]. Virtual reality has also been used in the educational context to create immersive educational environments so that students can observe how knowledge can be applied [28][29][30][28,29,30]. In recent years, the concept of gamification has become relevant in education through gamification [1]. Motivation, entertainment, and competition mean that this digital technology is being used in the educational environment with very encouraging results regarding learning [1][31][32][1,31,32]. Whether a technology is considered emergent depends on where it is being used, the domain and knowledge of its operation, and the application given to it [33]. An important characteristic of these technologies is that they do not need to have a limited life, even when they have been used for a long period of time. They can begin to become emerging when they are used in innovative ways in the service of people to achieve their objectives [34][35][34,35]. Emerging technologies for education (ELTs) are those that are being incorporated into education, which favor communication and allow easy access to educational information [36]. Some of the ELTs that contribute to an innovation system in higher education are mobile learning, MOOCs, social networks, gamification, augmented reality, virtual reality, and web applications [14][33][14,33]. The use of ELTs is quite diverse, for example, one research proposes the use of smartphones to run educational applications and contribute to improving the quality of teaching and learning. In addition, the author indicates that the use of mobile learning helps to compensate for the lack of infrastructure and the scarcity of school supplies and books in the place where the research was conducted [37]. They are also used for learning English as a second language for native speakers of Chinese [38]. One of the most widely used digital technologies is web pages which, depending on their design, can store information, generate educational games, serious games, manage learning resources, and automate processes, etc. [39][40][41][39,40,41].3. Literature Review on Network Automation
Network automation is performed using software, which automatically performs the configuration, provisioning, management, and testing of data network devices [42]. This technology is used by organizations and service providers seeking to improve the efficiency of their network management and administration processes [43]. In addition, using network automation can reduce human errors and operational expenses involved in existing manual configuration [42][44][45][42,44,45]. Network automation tools can perform simple jobs such as basic network mapping or much more complex jobs such as managing and evaluating the configuration of a technology infrastructure and provisioning resources needed for a virtual network [44]. Automation can be used in any type of network—for example, a local area network (LAN)—and even encompasses a wide area network (WAN). In addition, it can be used in data centers, in the cloud, and in wireless networks; that is, any network equipment that uses the command line interface (CLI) or an application programming interface (API) can be automated [42]. In recent years, as organizations have begun to digitally transform, their technology infrastructure has become much more complex, which has made way for new open-source programming languages, such as Python and Ruby, which have gained popularity for their ease of use and flexibility of work [42][46][47][42,46,47].3.1. Network Automation Benefits
Some of the benefits associated with network automation are as follows:-
Reduce operational expenses. By eliminating manual tasks, network equipment provisioning, and management can be improved, allowing organizations to operate in an agile and efficient manner [44].
-
Improves network efficiency. Automating the configuration processes in a technological infrastructure immediately improves network efficiency, as there is no need to perform time-consuming manual tasks [44].
-
Improves network performance. Without the need for disruption from manual network configuration, organizations can offer and deliver a higher level of services consistently [46].
-
Improves monitoring. Automation allows better control of the network, making it adaptable to specific needs. In addition, it allows for greater capacity and response to changes and better resolution of incidents and problems [44].
3.2. Network Automation Tools
For configuration automation in data network equipment, there are several platforms and protocols, based on scripts and software. These tools are open source, and examples of them are Ansible, Chef, and Puppet [48]. These tools offer an automation model and provide a library of common commands or workflows that can be easily used [45]. In recent years, automation has been used in the configuration of networking equipment. Software-based platforms have been developed that offer automation capabilities that work only with specific brands of networking equipment and use a specialized API [42][44][49][42,44,49]. All these tools simplify the amount of work and eliminate repetitive processes in the configuration of IT infrastructure equipment [50]. Some initiatives use Python libraries to perform data network automation, but these automation tools were not created for educational environments [44][46][51][44,46,51]. Examples include the web tool called Network Configuration Manager, which automates backups, monitoring, and change management, thus improving the productivity and reliability of the enterprise data network [52]. Another available web tool is Ansible Automation, which is used to install system software, automate daily tasks, prepare internal infrastructure, and improve data network security [45]. Mazin, et al. [51] in their research shows positive results regarding the efficiency of using automation in network equipment configuration versus using CLI, but their results were not analyzed in an educational environment with students. Other network automation initiatives using emerging technologies include “Implementación de un sistema para la administración de las funciones básicas de un Cisco Meraki MR33 mediante Cisco Devnet y Amazon Alexa en el Data Center académico de la Universidad de las Américas”. Its objective was to implement a system for the administration and management of the functionalities of Cisco Meraki equipment through Cisco DevNet Sandbox and Amazon Alexa, using Python as a tool for the migration of the UCS admin system [53]. In “Network Automation and Abstraction using Python Programming Methods”, a network was simulated in the GNS3 simulator with an Ubuntu container in Docker to run the Python scripts. Netmiko and Paramiko libraries were used to perform virtual network configuration, routing protocols, and backup configuration independently of the network equipment vendor [46]. The goal of “Diseño e implementación de un agente de administración, configuración y monitoreo para dispositivos de red Cisco” was achieved by using functions that enable serial communication between the computer running the program and the network equipment to which it is connected [54].4. Web Application to Automate the Configuration of Networking Equipment
To achieve the objectives of this research, an educational web application was designed and built, which contains a GUI for the automated configuration of equipment in a data network or technological infrastructure.4.1. Programming Languages and Frameworks
The tools listed in Table 1 were used to develop the web application.Table 1.
Tools used to develop the web application.
| Programming Language/Framework |
Definition |
|---|---|
| Python | It is a computer programming language that is often used to create websites and software, automate tasks, and perform data analysis. Python is a general-purpose language, which means that it can be used to create a variety of programs for different purposes [42][55][42,55]. |
| WTForms | It is a flexible form validation and rendering library for web development in the Python programming language. This library can work with any web framework and any template engine of choice [56]. |
| Netmiko | It is a multivendor Python library that facilitates the process of connecting to network devices through the SSH protocol, allowing better management and administration of network equipment through programs or scripts. In addition, it works with a variety of equipment—for example, Arista vEOS, Cisco ASA, Cisco IOS, Cisco IOS-XR, Cisco SG300, HP Comware7, HP ProCurve, Juniper Junos, and Linux Servers [57]. |
| Flask | It is a framework for a lightweight web application that is developed for easy deployment. Moreover, it is scalable for complex applications, making it one of the most popular Python web application frameworks. Flask makes it easy for the developer to freely choose the tools and libraries he needs [ |
-
User mode (User EXEC)
| Equipment Configuration Mode | Command for the CLI | Command for the CLI |
|---|
- Privileged execution mode (Privileged EXEC)
| router# | show running-config | These commands are used to display data related to the current configuration of the equipment, such as protocols and VLANs, among others. |
| show versión | ||
| show protocols | ||
| 58 | ]. | |
| Jinja | It is a modern templating language for Python developers. It is used to create HTML, XML, or other markup formats that are returned to the user via an HTTP request [59]. | |
| Bootstrap | It is a giant collection of practical and reusable bits of code written in HTML, CSS, and JavaScript. Additionally, it is a front-end development framework that allows developers and designers to quickly create fully responsive websites [60]. |
4.2. Configuration Modes in Network Equipment
The executable file Putty with an SSH client is used for secure access to communication equipment and input and output peripherals (monitor and keyboard). This tool allows securely connecting to remote servers and communication equipment through a serial session allowing remote administration of equipment within a data network [61]. The Internetwork Operating System (IOS) is the software used by most Cisco-branded equipment [- Global configuration mode
-
Specific configuration modes
Table 2.
Commands used for configuration using the CLI.
| Basic Commands to Monitor the Initial Configuration of the Equipment | ||
|---|---|---|
| show vlan | ||
| show ip interface brief | ||
| show ip route | ||
| show access-list | ||
| IPv4 addressing configuration | ||
| router(config)# | interface type number | These commands are used to assign an IP address to the interface of a network computer. |
| ip address ip address mask | ||
| no shutdown | ||
| DHCP protocol configuration for dynamic IPv4 address allocation | ||
| router(config)# | ip dhcp pool pool name | With these commands you can configure a network computer as a DHCP server. |
| network ip mask | ||
| domain-name domain name | ||
| dns-server server ip | ||
| Configuration of dynamic routing protocols, RIP, RIPv2 and OSPF | ||
| router(config)# | router ospf ospf id | These commands can be used to configure the OSPF protocol on the routers. |
| router-id router id | ||
| network ip wildcard area | ||
| router(config)# | router rip | These commands are used to configure the RIP protocol on the network equipment. |
| versión 2 | ||
| network ip address | ||
| no auto-summary | ||
| Creating and configuring a virtual LAN (VLAN) | ||
| switch(config)# | vlan vlan id | These commands are used to create VLANs with their respective names on the computers. |
| name vlan name | ||
| Configuring security on layer two communication equipment ports on the switch | ||
| switch(config)# | interface type number | These commands are used to configure layer two port security on network equipment. |
| switchport mode access | ||
| switchport port-security | ||
| switchport port-security maximum MAC address number | ||
| switchport port-security mac-address sticky | ||
| switchport port-security violation shutdown | restrict | protect | ||
| Initial configuration of a layer three equipment, the router | ||
| router(config)# | username username password password | With these commands you can create a new user on a network computer. |
| Username username privilege privilege level | ||
| Static routing configuration for communication between different data networks | ||
| router(config)# | ip route network-ip network mask next hop ip | These commands are used to create a static route to another network. |
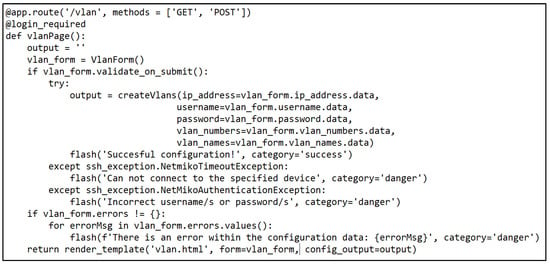
Figure 1.
Path code for VLAN creation.
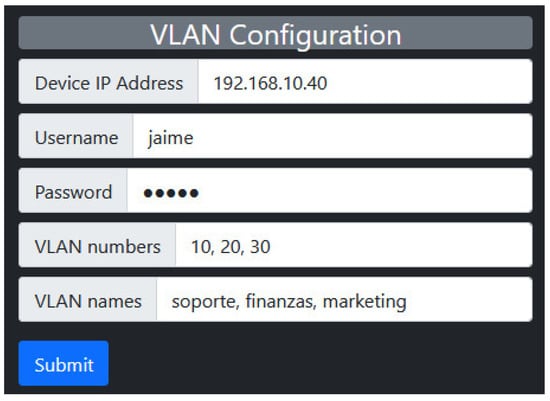
Figure 2.
Configuration and testing for VLAN creation.
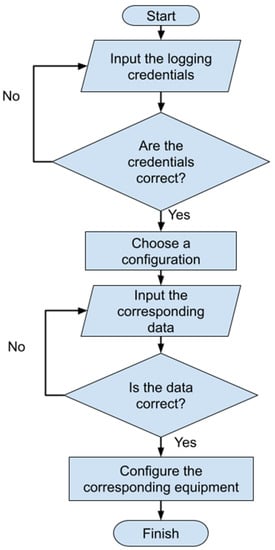
Figure 3.
Application flowchart.
