Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Marco Grossi and Version 2 by Camila Xu.
Ethernet is a widely used networking technology that finds its application in local area networks (LANs), metropolitan area networks (MANs), wide area networks (WANs), and other fields, such as industry, avionics, telecommunication, and multimedia. The Ethernet technology was introduced in 1980, and the first standardization was conducted in 1983 by IEEE 802.3.
- network security
- packet sniffer
- packet classification
- FPGA
1. Introduction
The Internet of Things (IoT) has interconnected embedded technologies, causing networks to become more complex due to the growth of web applications and business transactions. Consequently, networks have become more susceptible to cyberattacks, which can lead to unauthorized access, denial of service, and theft or alteration of sensitive data [1][2][3][1,2,3]. Cyberattacks pose a threat in various fields, such as Industry 4.0 [4][5][6][4,5,6] and healthcare [7][8][9][7,8,9].
Firewalls and packet sniffers are two common types of network security systems that can be used to prevent cyberattacks and protect computer networks. Firewalls work by monitoring and controlling incoming and outgoing network traffic based on pre-defined rules, while packet sniffers analyze network traffic in real time to detect and isolate potential threats. With the increasing complexity of computer networks and the growing number of cyberattacks, it is becoming more important than ever to have effective network security measures in place. These devices aim to detect any malicious traffic by either comparing packets with known attack samples (the signature-based approach) or by identifying abnormal traffic that does not match with known legitimate packets (the anomaly-based approach).
The difference between a firewall (or intrusion prevention system, IPS) and a packet sniffer (or intrusion detection system, IDS) is that an IPS possesses, either physically or logically, two ports. When the network data enter one port, these are transparently transferred to the output of the other port if no threats are detected or blocked otherwise [10]. An IDS, on the other hand, works in passive mode, reading all data received at its input port, and sending alarm messages to a remote server when potential threats are detected [11][12][11,12]. For home or business networks, where the speeds rarely exceed 1 Gbps, firewalls and packet sniffers can be effectively implemented in software running on a server. In 2017, Nivedita and Kumar proposed an innovative approach for a firewall using a hybrid frame of Netfilter for Linux web servers [13]. In 2016, Nivethan and Papa proposed a new methodology that extended existing Linux-based firewalls to protect the US smart grid, specifically for systems that use the DNP3 protocol. The aim of this approach was to prevent cyberattacks and ensure the security of the smart grid, which is becoming increasingly important in today’s interconnected world [14]. In 2022, Tirumala and colleagues conducted a study on the hardware capabilities of Raspberry Pi network interfaces to handle high volumes of incoming traffic for protecting small- and medium-sized enterprises and smart homes [15]. In 2015, Phalguni and Krishna presented a software firewall for the application layer running on an ARM9-based single-board computer based on the Iptables/Netfilter frame in Linux [16]. In 2013, Oluwabukola et al. proposed Psniffer, a packet sniffer software application for network security in Java [17]. In 2008, Phang et al. presented V6SNIFF, an efficient packet sniffer capable of analyzing Ipv6 packets [18]. In 2017, Goyal et al. conducted a comparative study between the two most popular packet sniffing software tools (Tcpdump and Wireshark) [19].
Firewalls and packet sniffers that are based on software running on a standard computer are generally reliable in most situations. However, when the amount of data being transferred and the transfer speed increase beyond a certain threshold, these systems may lose their effectiveness. In such situations, it is preferable to use a hardware implementation since it can guarantee real-time operations and much higher data throughputs. It is common for commercial firewall and packet sniffer products to be based on application-specific integrated circuits (ASICs), which are highly optimized devices designed and manufactured for a specific application. They offer top performances in terms of speed, power consumption, and production cost per unit. However, ASICs are also known for their complex design and high non-recurrent design costs, which make them ideal for high production volumes. Field-programmable gate arrays (FPGAs) are more suitable for products designed for small production volumes and research projects. These semiconductor devices feature quick design steps and negligible non-recurrent engineering costs. In 2019, Niemiec et al. conducted a survey addressing the open research challenges that need to be tackled for the adoption of FPGAs in accelerating virtualized network functions [20]. In 2011, Wicaksana and Sasongko presented a prototype of a hardware stateless firewall designed using Cyclone II FPGA working at 91 MHz [21]. According to these authors, the implementation only included packet classification, and due to the absence of an efficient FIFO buffer, it hinders high-speed data transfer. In 2017, Lin et al. presented an Ethernet firewall based on a FPGA that achieves a data throughput of 950 Mbit/s. The FPGA can be interfaced to ARM devices to realize a management server [22]. In 2012, Prajapati and Khare proposed a framework for a firewall hardware on a FPGA designed in Verilog that can handle IPv4 and IPv6 network data [23]. In 2020, the same authors presented a reconfigurable firewall based on a Xilinx Virtex-6 FPGA. This firewall achieves a throughput of 142 Gbit/s at a clock rate of 442.6 MHz for a minimum packet size of 40 bytes [24]. Mohammed and Ueno proposed a FPGA-based firewall in 2018, which was based on a Xilinx Kintex-7 XC7K325T device. The proposed firewall exploits content addressable memory to achieve a much better performance than a Linux firewall based on Iptables [25]. In 2021, Hilgurt presented a brief overview of various approaches, methods, and techniques used for designing a FPGA-based IDS [26]. In 2022, Stój et al. introduced an Ethernet packet sniffer based on a Xilinx Kintex-7 FPGA platform, which was designed for network intrusion detection in Industry 4.0 [27]. In 2013, Pal et al. proposed E-Sniff, a small special-purpose embedded system for capturing and logging network data based on a Cyclone II FPGA [28]. In 2005, Song and Lockwood published a paper on an efficient packet classification system for network intrusion detection using a FPGA that achieved a data rate of 2.5 Gbit/s [29]. Faria et al.’s FPGA-based Ethernet sniffer for real-time networks, which they proposed in 2009, can be interfaced via USB to a host computer for the generation of graphics and statistical data [30]. In 2016, Fiessler and colleagues proposed a hybrid packet classification approach called HyPaFilter. This approach handles simple operations in hardware designed with a FPGA, while complex operations are dealt with using a Linux-based software firewall [31].
2. Ethernet Frame Format
Ethernet is a widely used networking technology that finds its application in local area networks (LANs), metropolitan area networks (MANs), wide area networks (WANs), and other fields, such as industry, avionics, telecommunication, and multimedia. The Ethernet technology was introduced in 1980, and the first standardization was conducted in 1983 by IEEE 802.3 [32][34]. The data transfer rate of Ethernet has evolved from the initial 2.94 Mbps up to 100 Gbps [33][35]. In Ethernet networking, the data are described according to different levels of abstraction in the OSI model [34][36]. At level 2 (data link layer) of the OSI model, the data are described in the form of frames. The format of an Ethernet II frame is displayed in Figure 1. It always starts with a preamble and a start frame delimiter (SFD), and it ends with a frame checksum (FCS), a four-byte CRC that detects any corrupted data in the frame. The header of the Ethernet frame consists of the following fields: a destination and source media access control (MAC) address, a VLAN tag (an optional field), and the protocol type of level 3 (network layer), while the payload represents the data of the network layer. The packet formats of two of the most important protocols of the network layer, ARP, and IP, are presented in Figure 2 and Figure 3, respectively. The IP header also includes the protocol of the level 4 layer (transport layer), whose data are present in the IP payload. Three different protocols of the transport layer were considered, namely TCP, UDP, and ICMP, and their packet formats are presented in Figure 4, Figure 5 and Figure 6, respectively.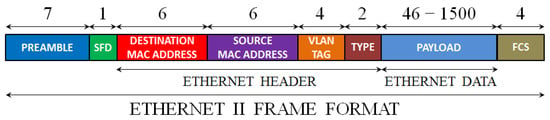
Figure 1.
The format of an Ethernet II frame. The length of each field of the frame is reported as the number of bytes.
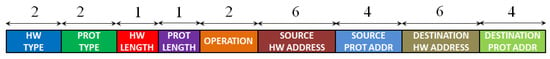
Figure 2.
The format of an ARP packet. The length of each field of the frame is reported as the number of bytes.
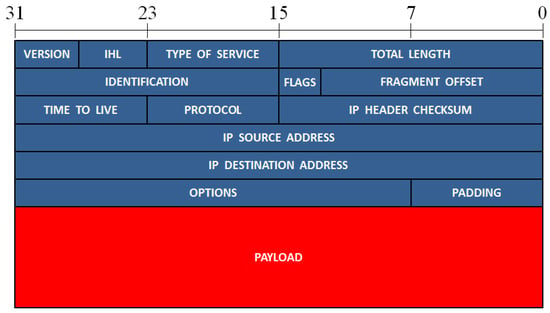
Figure 3.
The format of an IP packet. The different fields of this packet are presented in rows of 32 bits.
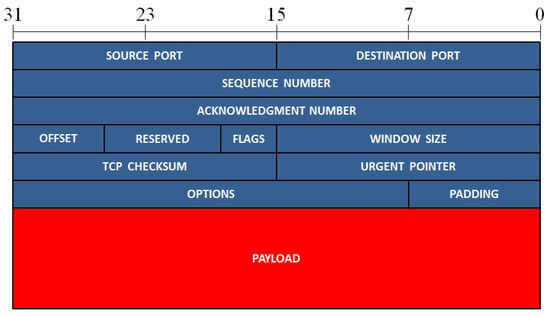
Figure 4.
The format of a TCP packet. The different fields of this packet are presented in rows of 32 bits.
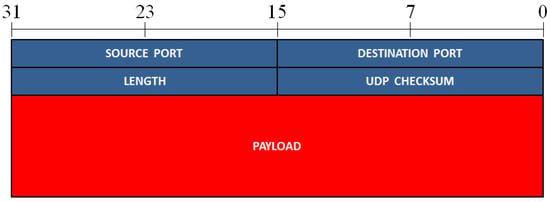
Figure 5.
The format of an UDP packet. The different fields of this packet are presented in rows of 32 bits.
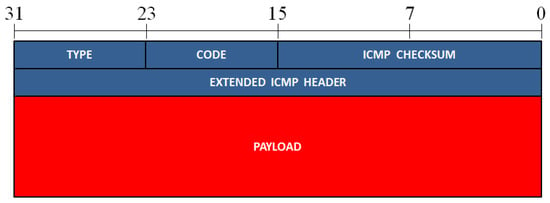
Figure 6.
The format of an ICMP packet. The different fields of this packet are presented in rows of 32 bits.
