Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Sara Rouhani and Version 2 by Sirius Huang.
Blockchain technology and, in particular, smart contracts based on it, offers a new, decentralized mechanism for entering into and fulfilling contracts in diverse markets. Energy markets are no exception, and indeed, the decentralized nature of the blockchain may be particularly important for them as the penetration of residential prosumers offering microgeneration to the grid grows.
- energy systems
- distributed
- BC
- smart contract
- smart grid
- energy market
1. Introduction
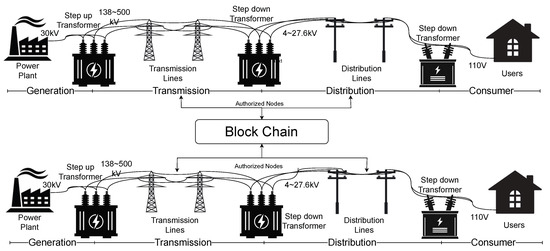
Energy systems today are undergoing tremendous change, as the energy demands of a growing population conflict with the need to decarbonize generation and transmission. The Smart Grid, which leverages Information Technology (IT) to improve energy system efficiencies, is a key response to these needs. Blockchain (BC) technologies, and especially Smart Contracts (SCs), are important frontiers in designing the IT infrastructure of the Smart Grid. A number of studies indicate that they may be suitable for decentralization and distributed management of system resources at multiple layers of the Smart Grid. A BC is a distributed shared ledger replicated across all nodes in a network, which communicate through a peer-to-peer protocol. Data are attached to this ledger as a group of transactions called blocks, with each block cryptographically linked to the previous one. BCs thus offer immutability, tamper resistance, and data provenance. BCs employ decentralized consensus algorithms to validate transactions and add blocks to the chain. Within a BC, SCs are executable code that implements the logic behind each transaction [1][2][1,2]. SCs enable the design of distributed applications based on BCs; they specify how data are read from, analyzed, and written to the BC. In particular, SCs for decentralized energy systems can verify and prepare energy data for the ledger and then analyze the stored data. BC-based management of energy systems may offer several advantages. Data are protected against loss, tampering, and single points of failure. Security and privacy are enhanced through business rules in the SCs and the inherent features of BCs [3][4][3,4], while costs are simultaneously reduced [1]. BCs can allow parties with no history of trusting each other to transact safely without needing guarantors [5]. They can also promote social cohesion and a sense of community, preference satisfaction, and uncertainty reduction [6].2. Smart Contract Design in Energy Systems
This literature breaks down into four categories: energy trading markets, ancillary services, auditing and monitoring, and cybersecurity, which are shown in Figure 13.
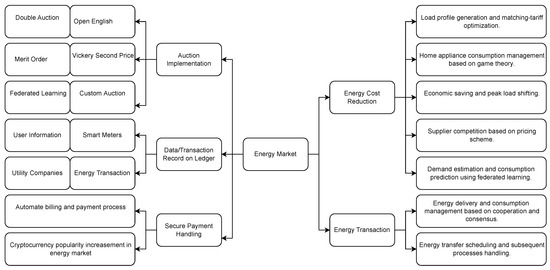
2.1. Energy Trading Markets
Energy trading is the most common application of BCs in energy systems. Multiple studies have investigated BC approaches to energy markets, which eliminate third parties in establishing, regulating, or operating them [5]. Such approaches can make energy system operations more efficient while reducing the peak load [3], increase market efficiency by reducing the threshold of participation for small retailers [1], reduce the cost of energy for residential users [11][32], and encourage investment in renewable generation plants [12][33]. A radically decentralized ledger can save and process the necessary trading information, which can improve the efficiency and privacy of energy trading in the smart grid [13][34]. Based on this theoretical research, energy trading platforms based on BC have been developed [14][35].
2.1.1. User Registration and Data Collection
For permissioned BCs, market participants must be authenticated and authorized to interact with the BC. Kang et al. [35][13] implemented user registration SCs, which also monitor energy usage and energy remaining in real-time. Prosumers are registered along with their conditions and sell price and are then matched with buyers.
SCs can also collect and record necessary data in the ledger. Such data are commonly generated off-chain and may come from prosumers, utility companies, etc. The data may include selling price and amounts of energy, auction bids, closed bid data [4][5][4,5], user energy profiles [36][9], user satisfaction [15][36], generation information, demand information [16][17][37,38], and smart-meter readings [18][19][39,40].
2.1.2. Contract Formation, Fulfillment, and Settlement
Multiple studies use SCs to collect user buy and sell prices for a given time window, which are entered into a selected auction format. These include double auctions [4][20][21][4,41,42], open English auctions [3][22][3,43], Vickrey second price auctions [5][23][24][5,44,45], Merit Order [37][56], and several other formats [7][25][26][27][28][29][38][39][11,46,47,48,49,50,57,58]. Auction winners form power purchase contracts. The process then repeats for the next time window (which is potentially as short as five minutes). Comparative studies of SC-based auction models have examined market dynamics (e.g., market efficiency or bidding strategies) [4][23][4,44] or BC network performance (e.g transaction latency or throughput) [23][44]. Both involve simulating the auction on a chosen BC network.
Contract fulfillment can be automated if the BC is integrated with metering infrastructure. The source of energy consumed can be tracked, proving fulfillment and enabling automated billing. Munising et al. [8][12] presented a decentralized optimal power-flow model for batteries, shapeable loads, and deferrable loads in a distribution network. This can also track the generation source of consumed energy (renewables, fossil fuel, etc.) and its cost [18][39]. Using this tracked information, it is also possible for the SC to dynamically change the power sources dispatched to fulfill contracts for a given consumer [40][59]. Individual prosumers in the energy trading market can be dynamically selected as validators of the BC in [30][51].
Contract settlement via SCs is another frequent topic of research [4][20][25][4,41,46]. Using BCs improves data privacy, identity management, and resilience toward cyber threats. In addition, the atomicity of data transactions in computing results, release, and payment can be assured [41][42][7,60]. Some utilities also accept cryptocurrencies for energy and electricity payments. PowerLedger operates a BC-based energy market using the POWER token [43][61]. Numerous researchers either employ existing cryptocurrencies or create new tokens, e.g., Han et al. [4], El-Syed et al. [44][62], and Muzumdar et al. [23][44].
2.1.3. Reducing Energy Cost
SC-based energy markets reduce costs by eliminating third parties [45][63], providing market access for smaller-scale, low-cost providers, and matching producers and consumers with congruent production and demand patterns. This enables cost reduction, peak load reduction, and enhanced market efficiency [1][11][31][32][33][1,32,52,53,54]. Jiang et al. [34][55] proposed an SC that can respond to energy demand based on the Stackelberg game, which can reduce the energy loss while maximizing the trading revenue considering the randomness of various energy sources. Gao et al. [46][64] achieved a 20% reduction in energy transmission cost with a BC based on a fog-computing paradigm. Large-scale energy auctions in this framework can be processed efficiently and with low latency even under conditions of high participation. Knirsch et al. [31][52] proposed an SC that matches utility generation with forecast consumer loads for optimal tariff selection. Saxena et al. [45][63] proposed a BC-based energy market for residential communities that reduced peak demand by 46% and energy costs overall by 6%. Bouachir et al. [38][57] proposed a federated learning method to predict demand and consumption in an auction round, reducing costs by 17.8%. Suther et al. [47][15] and Kang et al. [35][13] also proposed an SC-based local energy market. SC-based optimization in a time-of-use tariff model is proposed in [48][65]. SCs can also react to demand–response pricing signals [49][66].
2.1.4. Energy Transfer
SCs can schedule energy transfers between consumers and producers. This is distinct from contract fulfillment in that energy transfer requires the physical dispatch of power along a power grid. SCs can define business rules, e.g., scheduled or event-based delivery, or respond to particular situations [50][51][52][67,68,69]. Each SC can invoke another one, carrying out subsequent delivery processes [44][62]. Utz et al. [19][40] connected metering points via SCs, linking each one to a balancing group for settling energy delivery and consumption. In [17][38], energy trading among multiple regions can be interconnected by soft open points through SCs. This improves flexibility, while the voltage stability and power quality in the system are maintained. Figure 24 showed the semantic network for ancillary services.
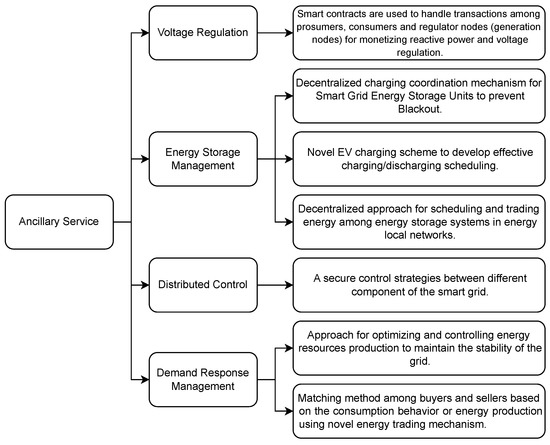
2.2. Ancillary Services
Ancillary services ensure the electric system provides acceptable power quality while ensuring reliability and security. Electric System Operators (ESOs) are responsible for organizing these services to ensure reliability. For example, The Alberta Electric System Operator (AESO) in Alberta, Canada [53][70], procures ancillary services including Operating Reserve (OR), Transmission Must-Run (TMR), Black Start, and Load Shed Services for imports (LSSi).
- 1
-
Operating Reserve: These reserves provide additional capacity or frequency support to the system when the energy supply is not adequate for the present demand. Regulating reserves are immediately available whenever a momentary imbalance in supply and demand would cause a voltage sag. Spinning reserve refers to generators that are synchronized to the grid but not yet delivering power; they can quickly inject substantial additional energy into the grid when needed. Supplemental (“standby”) reserve refers to generators that are available but not yet synchronized to the grid.
- 2
-
Transmission Must-Run (TMR): TMR generation compensates for insufficient local transmission infrastructure relative to local demand.
- 3
-
Black Start Service: Some generators need start-up power provided to them. Generators that do not are contracted to provide this power in the event of a total system blackout.
- 4
-
Load Shed Services for imports (LSSi): LSSi contracts permit AESO to shut down power flow to selected high-demand consumers when necessary to balance energy demand with available supply.
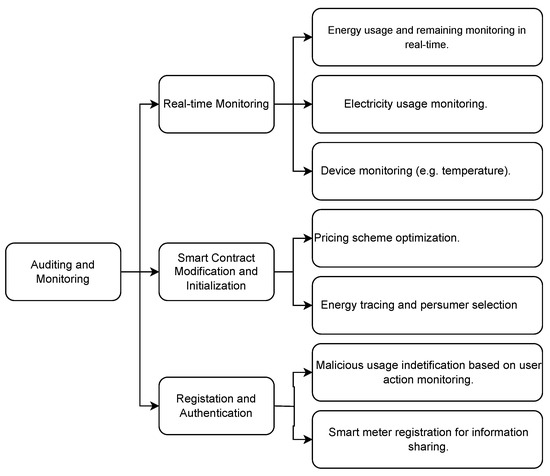
SC implementations of decentralized control systems can be robust, reliable, transparent, traceable, and secure. Energy supply can be optimized by tracking production and consumption and managing and prioritizing energy delivery [8][17][36][9,12,38]. SCs enable secure transactions, can monitor users’ behavior and data, define rules, and provide decision support, all of which are particularly important for renewables in microgrids. The intermittency of, e.g., solar or wind power, becomes a larger problem when a grid has a smaller power capacity, covers a smaller physical area, and serves a more homogeneous user base. Danzi et al. [54][71] proposed an SC-based control scheme using a subset of Distributed Energy Resources (DERs) to act as voltage regulators. Decentralized energy trading allows prosumers to sell excess power [55][8]. Figure 35 showed the semantic diagram for auditing and monitoring.
Energy storage units (ESUs) are essential for integrating renewables into the power grid and need to be integrated into energy markets. Yang et al. [57][10] introduce an Automated Demand Response framework using SCs for local scheduling and trading of energy among ESUs. It is also essential to coordinate ESU charging/discharging, or else the grid could be destabilized. Baza et al. [58][73] proposed an SC for scheduling ESU charging. The ESU’s power demand, time-to-complete-charging (TCC), and battery state-of-charge (SoC) determine which ESU(s) are charged in the current time window. Liu et al. [59][74] proposed an SC for electric vehicle (EV) charging to minimize grid fluctuations and charging costs for EV owners. Silvestre et al. [60][75] present a BC-based management framework for microgrids covering ancillary operations, particularly voltage regulation. [61][76] developed an SC-based decentralized voltage stability algorithm. They evaluated the performance of SCs in real-time control and investigated sharding mechanisms to improve scalability. Thomas et al. [26][47] and Mhaisen et al. [56][72] used SCs to implement security control strategies between different components of the Smart Grid.
2.3. Auditing and Monitoring
SCs can monitor devices, users, and data to detect malicious behavior or prevent threats to the system. Auditing refers to SCs tracking energy usage in real-time, initiating contracts, or auditing user preferences such as price, time, etc. Monitoring applications include Gao et al.’s [9][14] proposal to identify malicious usage of electrical power and data. Li et al. [62][77] design a distributed renewable energy system for residential, commercial, and industrial users; SCs are used to maintain stability even under such different load profiles. Yang et al. [63][16] allow residential consumers to track power usage and interior air temperature and to purchase additional power when needed. Yuhong Li et al. [36][9] allow consumers to trace the generation of consumed energy and form SCs to select generation sources of their choosing. Monitoring often involves Distributed State Estimation (DSE) using asynchronous data; delays in data transfer can negatively affect DSE. Asefi et al. [64][78] utilize an SC to improve delayed-delivery tolerance in DSE.
2.4. Cybersecurity
The cybersecurity literature on BCs in the Smart Grid usually focuses on two threats: unauthorized use of personal data or the security of energy transactions (either consumer-to-utility or peer-to-peer). Numerous studies have shown that patterns of energy usage, even just observed on the main feeder, can often be mapped to the identities and activities of persons in a private home [65][79]. The security of energy transactions, meanwhile, addresses necessary characteristics such as authorization, integrity, non-repudiation, and auditable fulfillment of a contract. The main difference between these two strands of research appears to be the presence or absence of a middleware layer that protects data privacy.
Studies focused on privacy protection rely on ensuring that a data requestor can only access data that the owner explicitly permits them to access, and that, furthermore, the requestor only receives anonymized summarized reports. Access to the raw data itself is not provided, ensuring that the owner’s privacy cannot be breached by accident, malicious intent, or external penetration of the requestor’s IT systems. Figure 46 is a good example of this approach [41][7].
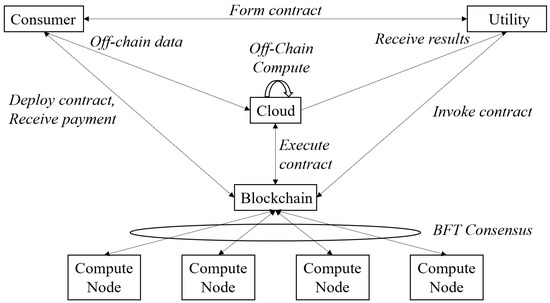
In Figure 46, a utility wishes to access consumer data. The consumer will securely store his/her data in an off-chain database (assumed to be cloud-based). The utility and consumer will negotiate an SC defining the data to be provided and the compensation to the consumer. The consumer deploys this contract to the BC. The utility can invoke the SC, triggering a (third-party) cloud-based off-chain computation involving the consumer’s data. Only the result of this computation is returned to the utility, and the consumer is paid [41][7]. Another approach to securing raw data is to deliberately add noise to the data, as in Gai et al. [66][80].
Dorri et al. [42][60] presented a framework for negotiating an energy price using BCs by using a routing method based on the destination public key. A two-phase commit protocol ensures contract fulfillment and settlement. They evaluate a Proof-of-Concept (PoC) implementation in a second paper [67][81]. They also investigated removable BC networks to improve scalability, throughput, latency, and privacy [68][82]. J. Wang et al. [69][83] proposed an anonymous authentication and key agreement protocol for SCs.
The second research theme, securing energy transactions, is very much a classic application of BCs. The literature on energy trading, in general, is vast, and the readers can refer to those sources for further discussion. The basic approach of [70][84] illustrates several key concepts. In Figure 57, consumers and generators negotiate SCs for energy delivery. Each generator creates at least one Authorized Node, which can form contracts and interact with the underlying BC as a peer. In this example, an Ethereum BC is used, using Ethereum’s Proof of Stake consensus algorithm. That algorithm requires the Ether coin, and so [70][84] settlement is also carried out in Ether coins.
Gai et al. [71][85] proposed a permissioned BC to counter fraudulent energy usage, communication interference, and data-center attacks. Lombardi et al. [72][86] implement auctions with SCs, which can also detect and isolate insecure smart meters. Gao et al. [9][14] used SCs to detect fraudulent power usage. W. Wang et al. [73][87] suggested a framework for identification and authentication in the smart grid. Hao et al. [74][88] propose a BC-based anonymous authentication scheme to facilitate fast and privacy-aware roaming and protect private information. SCs are used for user registration, signature verification, and user logout. Aung et al. [75][89] focus on the privacy of homeowners’ data, but they also developed an access control mechanism giving service personnel elevated privileges during emergencies. Guan et al. [76][90] aim to protect the privacy of both the data owner and receiver. An SC with a novel data obfuscation method based on ring signatures is proposed.