Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Hamed Taherdoost and Version 2 by Camila Xu.
Blockchain is the foundation of all cryptocurrencies, while machine learning (ML) is one of the most popular technologies with a wide range of possibilities. Blockchain may be improved and made more effective by using ML.
- blockchain
- security analysis
- machine learning
- algorithms
- applications
1. Introduction
Several fields in the real world have already begun to make use of and conduct extensive research into machine learning (ML) [1][2][1,2]. User-generated data in the tens of thousands per day may be utilized to train ML models, and those models can then be put to use solving a wide range of problems in business and society. Despite the progress of ML, data and model difficulties still exist. For instance, it is challenging to generalize ML models to reflect the future because current training methods require large amounts of data, which are often unavailable in practice [3] or limited due to the high cost of collection [4]. Concerns about data leakage and privacy [5] also exist. Filtering out “bad data” is a constant fight with malicious contributors or spammers, who can submit low-effort or illogical data and still receive rewards [6]. Additionally, it is difficult to generalize ML models to reflect the future due to outdated training [7], especially in subjects such as the Industrial Internet of Things (IIoT) [8], etc.
Most people agree that a blockchain is an efficient option that can guarantee security and reliability. However, as explained in [9], it may be vulnerable to attacks and security issues. Specifically, two significant attacks that undermined the network’s functioning recently occurred on Ethereum Classic [10], a permissionless (public) blockchain-based decentralized platform for smart contracts [11]. The blockchain is defined roughly by a global ledger that can efficiently and permanently record transactions via a timed chain of blocks, or blocks. Each block is added to the chain after being validated, based on a distributed consensus procedure, and contains information about the transactions. When enough nodes authenticate the block, which is subsequently regarded as reliable, the consensus is obtained. The whole procedure is recorded, and data may be gathered to describe the events taking place in the underlying ledger [12]. It is sensible to wonder whether such information may be used to monitor the process and provide early detection and analysis systems that can alert users to unusual events and potential attacks.
2. Security and Blockchain
There has been a significant surge in the number of reported security incidents involving the personal data of users. As a result, third parties may have access to the data and gather all personally identifiable information. This intermediary can be eliminated through the use of blockchain technology, which allows for direct transactions between two parties. The quantity of data in the environment has increased lately, and personal and sensitive information need not be safe in the hands of third parties as they are targeted for abuse and assault. Blockchain technology helps users who are not required to rely on a third party and acknowledges people as the owners of their data. However, it needs to have its regulations and norms, which is where the term “smart contract” comes in. Before initiating a transaction, the gateway keeper needs to draft a set of rules and a contract, which will facilitate peer-to-peer (P2P) interaction [13][14][21,22]. Many operations in cryptography are performed to provide various security services, including non-repudiation (ensuring authentication and integrity) [15][23], confidentiality (keeping information secret from communication parties), integrity, and authenticity. When asymmetrical cryptography is used, which has a set of public keys accessible to everyone and a set of private keys visible only to the owner, blockchain systems are naturally secure. These keys are used to ensure the integrity and ownership of a transaction [16][17][24,25]. The security of the blockchain system is linked to the integrity, confidentiality, and authorization of transactions. Unlike centrally kept data, which is more susceptible to security breaches, the decentralized structure of blockchain systems requires a P2P consensus mechanism, which reduces single points of failure for data [18][26]. There are many creative applications for blockchain, some of which are briefly discussed below. For example, Gai et al. [19][27] claim that integrating blockchain technology with an existing cloud solution could significantly improve the performance and security of cloud data centers. Recently, Wang et al. [20][28] implemented a secure and mutual authentication protocol to support the use of blockchain for identity verification issues in the smart grid. Similarly, before suggesting a blockchain-based authentication method for the smart grid, Wang et al. [21][29] highlighted a potential security threat to the infrastructure of the smart grid. Despite the high level of security provided by blockchain systems, they are still vulnerable to various security and data integrity attacks [22][30]. PoW consensus-related attacks, such as 51% majority manipulation [23][31], consensus delay due to distributed denial of service [24][25][32,33], block ingestion, de-anonymization, blockchain forking, orphaned blocks, pollution log, and selfish mining [26][34], as well as attacks against double-spending [24][32] and liveness attacks [27][35] are some examples of these types of attacks. Based on the evidence, the majority of security issues arise from three primary areas: transactions, authentication, and network connectivity. Therefore, technologies that allow inappropriate connections and their integration with other technologies may pose several security risks [28][36]. Since the inception of blockchain technology, there have been five generations of technological advancements, and the range of applications has significantly expanded [29][37]. Blockchain security issues need to be addressed because, despite its potential benefits, blockchain technology introduces new security concerns that need to be addressed. Blockchain networks are decentralized, transparent, and immutable, which makes them a desirable target for malicious actors attempting to exploit system vulnerabilities [30][38]. A total of 51% of attacks, smart contract vulnerabilities, consensus algorithm flaws, and privacy concerns are some of the most significant security obstacles in blockchain networks. These security issues can result in data intrusions, monetary loss, and reputational harm for individuals and organizations that utilize blockchain networks. Consequently, it is essential to resolve these challenges through research and innovation to improve the security of blockchain systems and facilitate the pervasive adoption of this technology.3. Blockchain and the Importance of ML
Through the usage of Bitcoin, blockchain [31][39] was largely promoted in the banking industry. It has been incorporated into many other sectors recently, including pharmaceutical manufacturing, supply chain operations, the healthcare sector, and many other important areas. Although ML is known for its automation of problem-solving by applying statistical computer algorithms or models, blockchain is often used for preserving financial transactions/data by maintaining a decentralized digital ledger that keeps all data in a highly safe manner. In addition to processing enormous amounts of business data and building an effective prediction system that makes decisions automatically, ML is well known for its ability to analyze patterns in a dataset and interpret patterns in business data to produce excellent visual graphs and interpolations that can be used to provide insights into top management. In the insurance sector, cutting-edge ML algorithms have recently been utilized to predict financial risks. Insurance firms may accurately estimate the risks involved with charging new insurance premiums thanks to ML, which runs its algorithms on massive amounts of financial information and discovers a certain hidden pattern. Blockchain establishes a distributed ledger with a secure transactional database that has precise timestamps and immutable and permanent data instances. The main reason blockchain is so well-known is that it uses digital signatures as a particular method of reaching an agreement on financial data entities. Large amounts of data are needed for ML to produce credible models. Gathering, organizing, and auditing data is a straightforward approach made possible by blockchain that may increase data accuracy [32][40]. Blockchain greatly enhances data protection by automating the prediction of which types of data need to be stored and processed in a chain for making instances as accessible as possible. Blockchain has incredible support for standards for securing a lot of data at different nodes and makes data available at any instance in an encrypted manner. Since they are decentralized, blockchains may have security flaws [33][41]. The most prevalent issue is that the consensus procedure may be disrupted as a result of an assault, allowing a few mining farms to control which blocks are put into the network. This specific risk exists in public blockchains. Private versions are immune to this assault since each node is uniquely recognized, and a suitable consensus process is in place. In the field of security, combining blockchain with ML may result in new and reliable solutions (Figure 1). For example, blockchain may be used to establish an immutable record of transactions that cannot be changed, and ML algorithms can be taught to identify patterns of fraudulent conduct in financial transactions. Blockchain may also be used to securely store data about network activities, and ML algorithms can be used to identify and stop cyberattacks in real time. ML may be used to validate users’ identities based on biometric data, which can be utilized for identity verification. It is more difficult for hackers to obtain and use this data if it is securely stored in a decentralized way using blockchain. ML algorithms may be used to evaluate this data and find patterns of suspicious behavior or possible security breaches in supply chain security. Blockchain can be used to produce a safe and transparent record of every step in a supply chain. Lastly, ML can be used to analyze the behavior of these contracts and spot potential security flaws, helping to avoid the loss of money or other assets. Smart contracts are automatically executed based on predefined conditions and can be created using blockchain.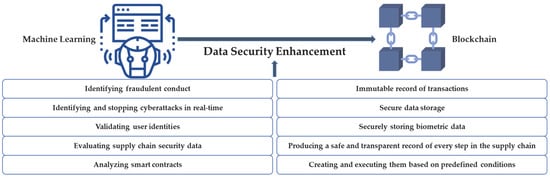
Figure 1.
ML method to enhance data security of blockchain.
