Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Amal Alhosban | -- | 1772 | 2024-02-05 01:38:57 | | | |
| 2 | Rita Xu | Meta information modification | 1772 | 2024-02-05 03:52:43 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Alhosban, A.; Pesingu, S.; Kalyanam, K. Cloud Vendor Lock-In. Encyclopedia. Available online: https://encyclopedia.pub/entry/54739 (accessed on 02 March 2026).
Alhosban A, Pesingu S, Kalyanam K. Cloud Vendor Lock-In. Encyclopedia. Available at: https://encyclopedia.pub/entry/54739. Accessed March 02, 2026.
Alhosban, Amal, Saichand Pesingu, Krishnaveni Kalyanam. "Cloud Vendor Lock-In" Encyclopedia, https://encyclopedia.pub/entry/54739 (accessed March 02, 2026).
Alhosban, A., Pesingu, S., & Kalyanam, K. (2024, February 05). Cloud Vendor Lock-In. In Encyclopedia. https://encyclopedia.pub/entry/54739
Alhosban, Amal, et al. "Cloud Vendor Lock-In." Encyclopedia. Web. 05 February, 2024.
Copy Citation
Cloud computing has become an integral part of businesses and personal lives due to its scalability, cost-effectiveness, accessibility, and user-friendliness. Its popularity has led to widespread adoption by people and businesses alike, resulting in significant market growth.
cloud vendor lock-in
dependency analysis
cloud service providers
1. Introduction
By 2022, the market size is expected to reach around USD 490 billion, with annual growth predicted to be 15.7% from 2022 to 2030. This trajectory would result in a market size of USD 1500 billion by the end of the next decade. The rising demand for cloud services is fueled by digital transformation initiatives, the surge in remote work, and the increasing reliance on online services. However, potential factors such as technological breakthroughs, evolving regulations, economic fluctuations, and shifts in business approaches may influence the growth rate.
Cloud computing is essential in contemporary society, as it enables sizable enterprises to lease their hardware infrastructure to smaller businesses that lack the means to procure the hardware independently. This includes an array of services such as storage, servers, databases, networking, analytics, software, and intelligence, all delivered via the Internet. One of the most significant advantages of cloud computing is its inherent scalability, allowing businesses to expand seamlessly while accommodating evolving needs and reducing operational expenses.
In a broad context, cloud computing represents a forward-thinking abstraction of Internet-based computing resources and services, harnessed by system developers to implement intricate web-based systems [1]. In simpler terms, cloud computing leverages a network of remote servers hosted on the Internet for data storage, management, and processing, supplanting the traditional local server approach. A finer understanding of cloud computing emerges when examining its deployment models and service categories. Four distinct deployment models shape the landscape: private, public, community, and hybrid. A public cloud is universally accessible, whereas a private cloud is owned by a specific entity. The community-based model is shared among multiple entities, while the hybrid model amalgamates elements of the other three. Furthermore, three core cloud service models categorize its functionalities. Software as a Service (SaaS) encapsulates complete software applications complete with user interfaces. Infrastructure as a Service (IaaS) supplies machines, storage, and networking resources that developers manage by incorporating their supportive assets. Platform as a Service (PaaS) furnishes a platform where developers deploy their applications [2].
The cloud computing industry faces several challenges, including data breaches, compliance with regulatory mandates, a lack of IT expertise, cloud migration, unsecured APIs, insider threats, and many others. These challenges usually fall into three main categories: security and privacy, data protection, and vendor lock-in.
1.1. Security and Privacy
Ensuring the security of cloud computing requires a comprehensive approach that takes into account the persistent growth of challenges that come with technological advancements. As technology evolves, it becomes increasingly important to provide robust protection. Protecting digital environments requires mitigating potential threats and pre-empting attacks to build user confidence in using services, platforms, and software. The level of security provided by a cloud service is directly linked to user adoption and acceptance. Unlike traditional systems where physical access often leads to vulnerabilities, the remote nature of cloud computing changes this dynamic. However, the increasing sophistication of hackers remains a significant challenge. To enhance cloud computing security, a combination of strategies is essential. This includes implementing strict authentication mechanisms, robust encryption protocols, and vigilant intrusion detection systems. In addition, proactive monitoring, the timely patching of vulnerabilities, and continuous security audits are critical. Emphasizing user education and awareness regarding best security practices can also play a crucial role in fortifying the overall cloud environment. By addressing security concerns comprehensively, cloud providers and users can contribute to a safer ecosystem that safeguards against threats and creates a climate of trust, enabling cloud services to thrive despite evolving cyber threats [3].
1.2. Data Protection
Organizations must ensure that their data comply with regulations such as GDPR, HIPAA, and industry-specific standards. The location of data storage and processing can impact compliance [4]. Given that computing takes place over the Internet, the eventuality of a data breach is a concern that necessitates proactive measures to safeguard both businesses’ and their customers’ data. While striving to strike a balance amidst various challenges can be complex, prioritizing prevention is advisable. Mitigating the occurrence of breaches is key to pre-empting a potential fallout. Furthermore, the onus often falls on the cloud computing provider to furnish a significant portion of the security framework. However, this dynamic can limit the extent of control businesses possess over the security protocols. Hence, a strategic approach involves collaborative efforts between stakeholders to ensure a robust security posture while navigating the inherent complexities of cloud computing. By adopting a foresighted and preventative approach, businesses can mitigate risks, enhance security, and establish a resilient cloud environment that instills trust and safeguards data integrity. As of 2023, the Cost of a Data Breach report jointly conducted by IBM and the Ponemon Institute reveals that the average expense incurred due to a data breach has surged to an all-time high of USD 4.45 million [5].
2. Vendor Lock-In
Vendor lock-in is a situation in cloud computing where a customer becomes heavily dependent on a specific cloud provider due to various reasons such as technical aspects, contract terms, or other factors. This dependency can result in limited options for the customer to switch to another provider, even if the current provider is not performing well. This creates difficulties for customers who want to switch to a different provider, as it involves significant obstacles, expenses, and disruptions. Vendor lock-in can occur when a cloud provider uses proprietary technologies, formats, or interfaces that are not easily interoperable with other providers, making it difficult for the customer to migrate their applications and data. It can also result from exclusive licensing terms, complex integration requirements, or custom configurations that tie the customer to the specific provider’s ecosystem. This lack of portability and flexibility can limit the customer’s ability to adapt to changing needs or take advantage of competitive offerings, potentially impacting cost-effectiveness and innovation.
2.1. Vendor Lock-In Scenario
Company TechWay, a rapidly growing Software as a Service (SaaS) provider, initially selected Cloud Provider XYZ to host their application and oversee their cloud infrastructure. They were drawn by competitive rates, dependable services, and most features aligned with their needs.
Over time, TechWay integrated its application with Cloud Provider XYZ’s offerings, relying on databases, serverless functions, and AI services for data processing. However, challenges arose when their evolving needs exceeded Cloud Provider XYZ’s AI services. They turned to Cloud Provider ABC, which offered advanced machine learning options like natural language processing and image recognition (see Figure 1).
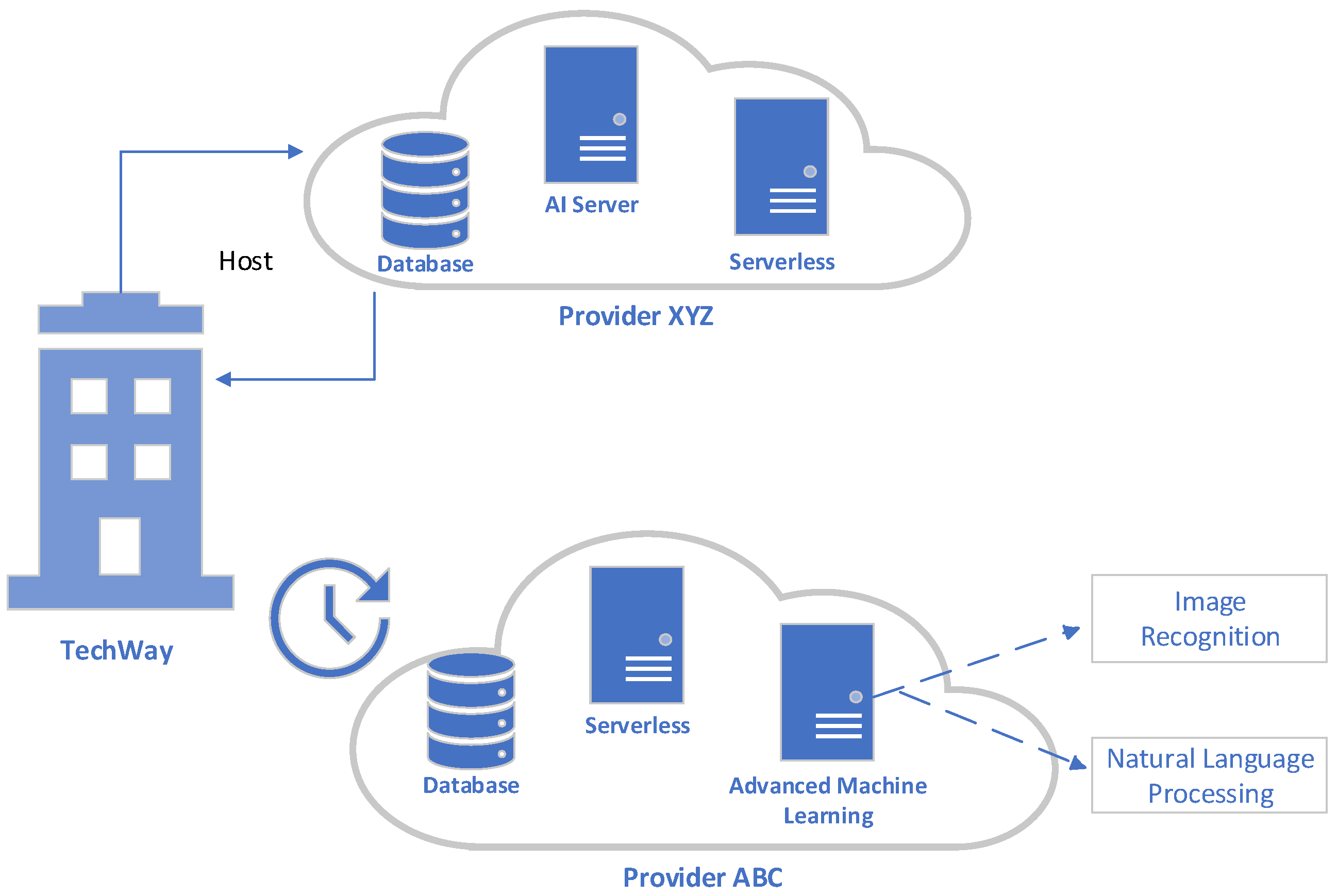
Figure 1. TechWay company scenario.
At this point, the vendor lock-in issue emerged. Shifting from Cloud Provider XYZ to Cloud Provider ABC would be intricate and time-intensive. They would need to modify their code, adapt data formats, and restructure workflows to align with Cloud Provider ABC. Furthermore, high data egress charges by Cloud Provider XYZ added to the migration expenses.
TechWay also faced the hurdle of their proficient developers specializing in Cloud Provider XYZ’s tools. Adapting to Cloud Provider ABC would require training or hiring new talent familiar with their ecosystem.
Cloud computing is marked by the arduous and costly process of transferring applications and data to alternate providers. Cloud software vendors employ various strategies to bind customers, such as creating systems that are incompatible with other vendor software, utilizing closed architectures or proprietary standards that lack interoperability with other applications, and imposing exclusive licensing conditions [6]. This practice dissuades organizations from embracing cloud technology, posing a formidable obstacle that demands substantial efforts to surmount [7].
As elucidated by [7], the mounting market demand and the quest for increased customer engagement exert pressure on cloud providers to prioritize interoperability—a direct advantage that circumvents the pitfalls of vendor lock-in. Prior studies have largely explored interoperability issues and the concerns tied to vendor lock-in. Numerous standardization solutions have emerged to enhance interoperability [8][9]. However, limited research has been devoted to a comprehensive investigation of vendor lock-in review and its implications for cloud computing adoption.
2.2. Vendor Lock-In Types
In cloud computing, vendor lock-in appears in different ways, such as technical lock-in, data lock-in, service lock-in, certification lock-in, contract lock-in, economic lock-in, and network lock-in (Figure 2). The technical lock-in occurs when a cloud service provider offers proprietary technologies, APIs, or data formats that are not easily transferable to other providers. Customers become dependent on these unique features, making it challenging to migrate to alternative platforms without significant redevelopment effort. For example, when the service consumer is using database solutions with cloud-specific functions.
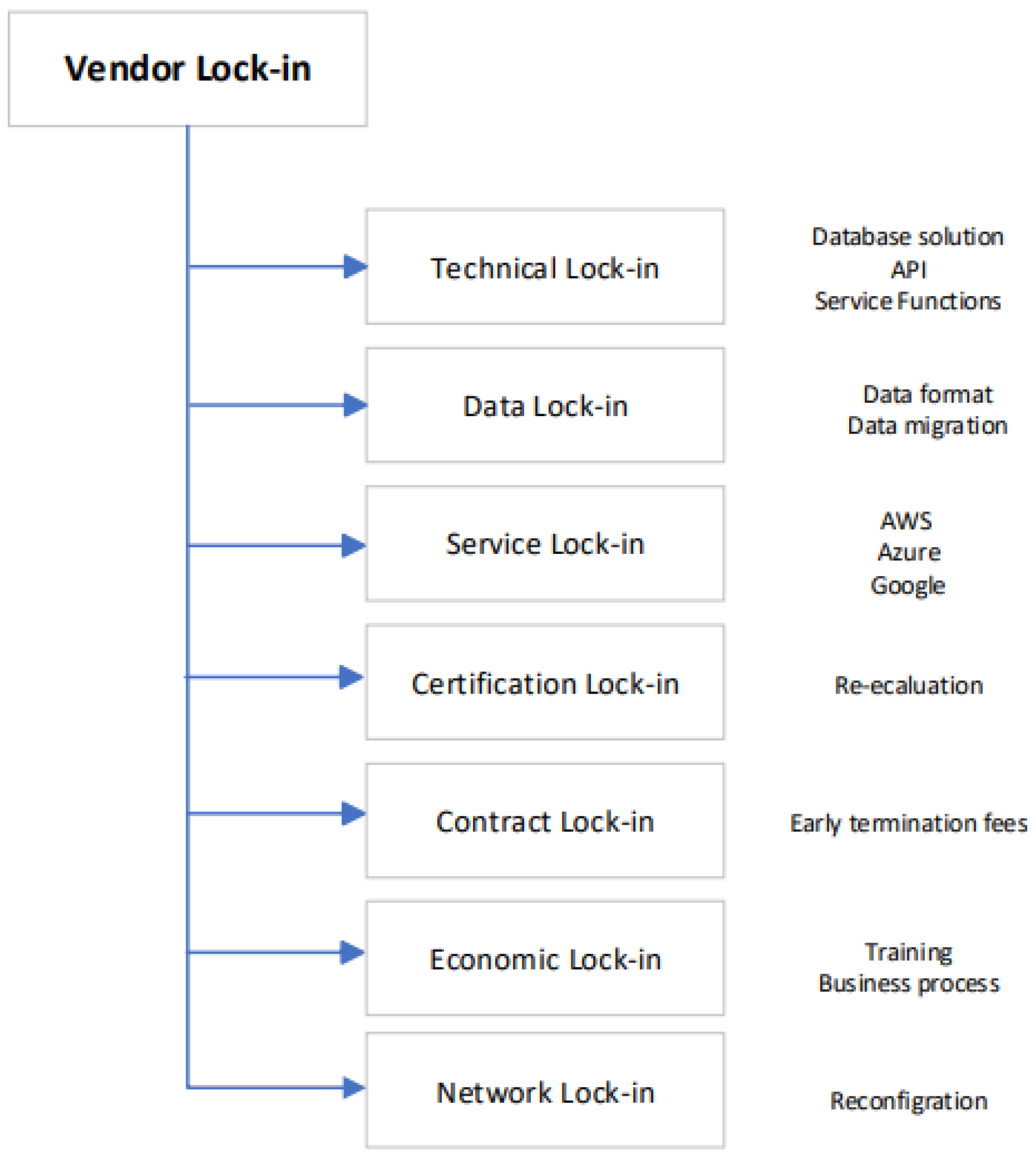
Figure 2. Vendor lock-in Ttypes.
In data lock-in, the data storage formats and structures are owned by the cloud providers. Cloud consumers should store their data in the specified formats, which makes it difficult to move these structured data to another service provider or to a different infrastructure. The migration of service consumer data will need transformation, which will increase the data migration complexities. Data transformation will lead to high costs and time-consuming processes. Service lock-in occurs when a service provider offers a wide range of services, such as analytical services, serverless computing, and machine learning. Service consumers who integrate these services into their applications will find it challenging to switch to another cloud provider because of the tight coupling with the provider’s system. For example, AWS Lambda functions are not easily transferable to Azure Functions or other cloud providers, such as Google. In certification lock-in, some industries require specific certifications or standards. The service consumer should follow the roles and standards listed in the cloud provider certifications. Switching service providers requires a re-evaluation of the roles and standards of the certification, which will be costly and time-consuming. Contract lock-in appears in many cases especially when it is a long-term contract with cloud providers. Most of the contracts have penalties and/or termination fees for early termination, making it financially challenging for service consumers to switch to another service provider. Over time, service consumers may invest heavily in a specific cloud provider’s ecosystem, which can lead to economic lock-in. This includes the direct costs associated with cloud services, the training of staff, the development of cloud applications, and the adoption of specific tools. The last type is network lock-in, which appears when the cloud providers offer a variety of networking services, and service consumers configure their network infrastructure to work with a particular provider’s services. Migrating to a new provider will require network re-configuring.
Mitigating cloud vendor lock-in involves careful planning, the use of open standards and technologies when possible, and adopting strategies like multi-cloud or hybrid cloud architectures. It is crucial for organizations to weigh the benefits of cloud services against the potential lock-in risks when making cloud-related decisions.
References
- Almorsy, M.; Grundy, J.; Müller, I. An analysis of the cloud computing security problem. arXiv 2016, arXiv:1609.01107.
- Vinoth, S.; Vemula, H.L.; Haralayya, B.; Mamgain, P.; Hasan, M.F.; Naved, M. Application of cloud computing in banking and e-commerce and related security threats. Mater. Today Proc. 2022, 51, 2172–2175.
- Subashini, S.; Kavitha, V. A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 2011, 34, 1–11.
- Pearson, S. Taking account of privacy when designing cloud computing services. Int. J. Inf. Manag. 2011, 31, 353–357.
- Kang, Y. Development of Large-Scale Farming Based on Explainable Machine Learning for a Sustainable Rural Economy: The Case of Cyber Risk Analysis to Prevent Costly Data Breaches. Appl. Artif. Intell. 2023, 37, 2223862.
- Fitzpatrick, B.W.; Lueck, J. The Case Against Data Lock-in: Want to keep your users? Just make it easy for them to leave. Queue 2010, 8, 20–26.
- Govindarajan, A.; Lakshmanan. Overview of cloud standards. Cloud Comput. Princ. Syst. Appl. 2010, 77–89.
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.H.; Konwinski, A.; Lee, G.; Patterson, D.A.; Rabkin, A.; Stoica, I.; et al. A view of cloud computing. Commun. ACM 2010, 53, 50–58.
- Opara-Martins, J.; Sahandi, R.; Tian, F. Critical review of vendor lock-in and its impact on adoption of cloud computing. In Proceedings of the International Conference on Information Society (i-Society 2014), London, UK, 10–12 November 2014; pp. 92–97.
More
Information
Subjects:
Computer Science, Software Engineering
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
1.8K
Revisions:
2 times
(View History)
Update Date:
05 Feb 2024
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No





