Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Ali KARA | -- | 2096 | 2023-12-15 09:39:15 | | | |
| 2 | Sirius Huang | -2 word(s) | 2094 | 2023-12-18 02:28:54 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Awan, M.A.; Dalveren, Y.; Catak, F.O.; Kara, A. Radio Frequency Fingerprinting in Smart Grids. Encyclopedia. Available online: https://encyclopedia.pub/entry/52799 (accessed on 13 January 2026).
Awan MA, Dalveren Y, Catak FO, Kara A. Radio Frequency Fingerprinting in Smart Grids. Encyclopedia. Available at: https://encyclopedia.pub/entry/52799. Accessed January 13, 2026.
Awan, Maaz Ali, Yaser Dalveren, Ferhat Ozgur Catak, Ali Kara. "Radio Frequency Fingerprinting in Smart Grids" Encyclopedia, https://encyclopedia.pub/entry/52799 (accessed January 13, 2026).
Awan, M.A., Dalveren, Y., Catak, F.O., & Kara, A. (2023, December 15). Radio Frequency Fingerprinting in Smart Grids. In Encyclopedia. https://encyclopedia.pub/entry/52799
Awan, Maaz Ali, et al. "Radio Frequency Fingerprinting in Smart Grids." Encyclopedia. Web. 15 December, 2023.
Copy Citation
Smart grids incorporate diverse power equipment used for energy optimization in intelligent cities. This equipment may use Internet of Things (IoT) devices and services in the future. To ensure stable operation of smart grids, cybersecurity of IoT is paramount. To this end, use of cryptographic security methods is prevalent in existing IoT. The potential of radio frequency fingerprinting (RFF) in wireless communication of IoT devices to augment the cybersecurity of smart grids is discussed herein.
radio frequency fingerprinting
machine learning
deep learning
software-defined radio
Internet of Things
cybersecurity
smart city
smart grid
1. IoT in Smart Grids
The US Department of Energy defines smart grids as modernized electrical grids that leverage advanced technology to enhance the efficiency, reliability, and sustainability of electricity generation, distribution, and consumption [1]. They incorporate various power generation sources, including customer-generated energy, solar, wind, and more. Understanding the role of IoT in smart grids and the security challenges it presents is crucial before delving into discussions about the necessity to bolster cybersecurity.
1.1. D2D Wireless Communication in Smart Grids
The effectiveness of smart grids is rooted in their ability to anticipate fluctuations in energy supply, optimize grid operations, and promptly respond to changes in demand and power failures. This capability not only strengthens grid stability but also contributes to the reduction in energy wastage, enhancing overall sustainability [2]. Central to the realization of this concept is D2D wireless communication between IoT devices at the control center, the power station, and consumers. Figure 1 shows the evolution of power grids. The dotted lines mark the communication network, which is crucial in achieving the functionality of smart grids.
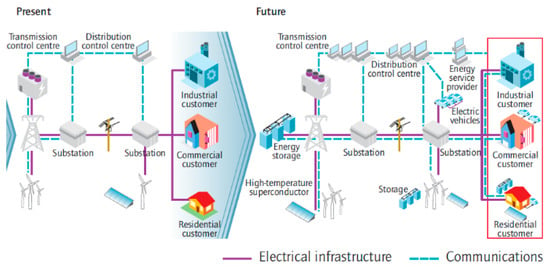
Figure 1. Evolution from conventional to smart grids [2].
1.2. Security Challenges in Wireless Communication
In wired networks, nodes are physically linked by cables. Conversely, wireless networks face heightened vulnerability due to their broadcast nature. They are susceptible to various malicious attacks, such as eavesdropping [3], denial-of-service (DoS) [4], spoofing [5], man-in-the-middle (MITM) [6], message falsification/injection [7], etc. To ensure confidentiality and authentication, existing systems commonly use cryptographic techniques to prevent eavesdropping and unauthorized access to networks [8][9].
Conventional cryptography ensures identity verification using techniques like message authentication codes, digital signatures, and challenge-response sessions [10]. However, in widely distributed IoT, security gaps persist due to reverse engineering threats [11], impracticality of rapid cryptographic protocol installation in insecure devices [12], and inefficacy against hijacked devices.
In a post-quantum computing era, the above cited challenges could be overcome using quantum cryptography. For instance, quantum light could be used to generate inherently unforgeable quantum cryptograms [13]. These cryptograms have exhibited the potential to be used in practical applications with near-term technology. Future IoT may benefit tremendously at the application layer as a solution to vulnerabilities present in symmetric cryptographic schemes. Non-cryptographic methods, such as device-specific signal pattern analysis, supplement traditional cryptography by identifying known devices and detecting rogue ones [14]. These approaches are crucial for enhancement of cybersecurity in IoT, without requiring major system modifications [15].
1.3. Cybersecurity in Smart Grids
The layered architecture in IoT of smart grids is illustrated in Figure 2 [16]. At the physical layer, data from sensors, actuators, and smart meters are collected at the gateways. At the network layer, data from multiple gateways are concentrated and relayed to the application layer operating on servers in the control center using legacy communication methods. The goal of cybersecurity in IoT is to ensure protection at every layer; the same is applicable in smart grids as well. A closer look at the threat spectrum being faced by smart grids underscores the importance of device authentication [17][18], although physical layer intrusion detection systems have the capacity to perform device authentication at the first stage of defense in wireless networks [19]. But, to this end, there has not been a study on the implementation of physical layer security measures in wireless communication between IoT devices of smart grids for authentication. To fill this gap, RFF emerges as a potential solution and this text builds the case for discussion on the associated deployment aspects in smart grids.
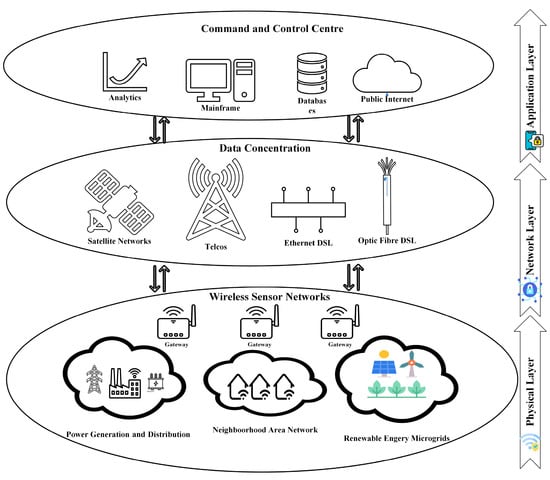
Figure 2. Cyber security in smart grids [16].
2. Deployment of RFF in Smart Grids
Existing IoT frameworks have been considered for seamless integration of RFF with minimal changes. The core idea is to present RFF as an addition to existing IoT infrastructure instead of reinventing the wheel. The following sub-sections provide considerations and requirements for deployment of RFF in smart grids.
2.1. Network Considerations
Performance metrics of existing IoT serve as a good starting point. Coverage and energy efficiency are important metrics for choosing a network topology [20]. Furthermore, data rate, range, application layer security, and localization are important factors for selecting a particular low-power wide-area network (LPWAN) [21]. From a practical standpoint, cost and scalability hold particular significance [22]. In the UK, smart meters communicate via cellular networks, utilizing 2G or 3G waveforms [23]. However, the use of a long-range wide-area network (LoRaWAN), a star-of-star network topology, in advanced metering infrastructure has been reported as well [24][25]. Given the novelty of RFF and the consideration of performance metrics including cost, energy efficiency, network topology, and communication range, LPWAN is a suitable candidate for the deployment of RFF.
2.2. Security Considerations
Cybersecurity experts have expressed concerns, revealing that 70% of IoT devices are vulnerable to cyberattacks [26]. The wireless sensor network of IoT exhibits vulnerabilities across various layers, and cyberattacks can manifest at different stages [27]. Likewise, LPWAN is not exempt from cyber threats [28]. Wireless sensor networks in smart grids comprise IoT devices equipped with temperature, humidity, light, and wind sensors. The threat from rogue IoT devices to generate falsified data is a significant concern. For instance, exaggerated sensor readings from a smart meter could lead to an unwarranted stimulus from the control station. Considering the vulnerability of higher layers to attacks, a novel approach is to secure the physical layer of D2D wireless communication across the network. It is proposed that this extra layer of security should always be in the loop for all end-to-end data transactions between IoT devices in the network.
2.3. Proposed RFF Framework
A key facet of smart grid infrastructure is the real-time estimation of household loads [1][2]. This requirement can be effectively addressed by smart energy meters transmitting data wirelessly at regular intervals. However, this simple task becomes challenging from a cybersecurity perspective in the presence of rogue devices. This scenario is accurately addressed in the physical layer security framework of RFF, as depicted in Figure 3. The proposed configuration ensures that all data transmission from the sensors must pass through the physical security barrier of the RFF system before reaching the control station. The star-of-stars network topology ensures that all the sensors first concentrate their data at their respective gateways. Hosted on the IoT gateways, RFF serves as a filter to allow readings from only legitimate sources while filtering the rogue ones on a per packet basis. Since these gateways can send and receive wireless data, they can filter data from rogue gateways as well.
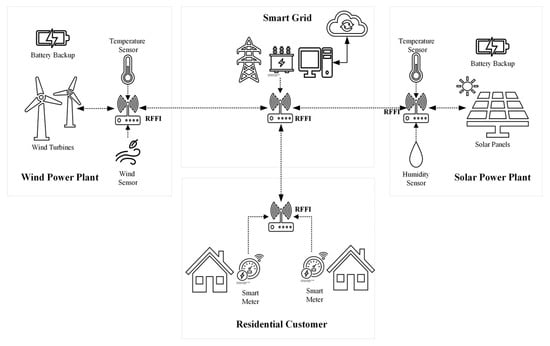
Figure 3. Proposed RFF framework for smart grids.
It is worth mentioning that within a mini star network, multiple gateways could be employed for time-based direction of arrival estimation. This can be extremely helpful in the localization of a rogue device followed by necessary remediation. The IoT devices equipped with sensors communicate unidirectionally with their respective IoT gateways. However, to cater for dynamic load requirements, the control station may issue commands to renewable energy plants, directing them to release stored energy into the system or increase power generation. This requires bidirectional communication in line with the fundamental characteristics of a smart grid [1][2]. This bidirectional communication offers a significant challenge for deployment of RFF in existing low-resource IoT devices.
2.4. Performance Considerations
Before a technology is deemed suitable for practical deployment, it is important to estimate its performance considering real-world conditions. The key performance indicator (KPI) of an RFF system is its classification accuracy. There has not been a study on the estimation of this KPI in a smart grid use case. However, previous work in [29] covered the performance comparison of various ML-aided classifiers with different SNR values of the received signal. Table 1 summarizes the experimental results from that study. The results show decent performance even in low SNR conditions. Given that the IoT devices in wireless sensor networks of smart grids are deployed in a static setting, empirical propagation measurements in urban environments may serve as a good reference for RSSI estimation [30].
Table 1. Comparison of classifiers with various levels of SNR [29].
| Classifier | SNR (dB) | ||
|---|---|---|---|
| (8–10) | (12–15) | (18–23) | |
| L-SVM | 79.3% | 82.1% | 90.5% |
| Complex Tree | 66.8% | 68.8% | 85.4% |
| LDA | 76.6% | 77.8% | 83.6% |
Subsequently, the resultant SNR could be used to estimate the classification accuracy using Table 1. It is expected that through careful decision making in the selection of appropriate classifier and signal attributes, decent classification accuracy can be achieved, even with low SNR. The classification accuracies of various signal representations for as many as 60 unique LoRa devices are given in Table 2. It may be noted that there is another important aspect in gauging the performance of an RFF system: the time required for training. It is only reasonable to assume that installation, repair, and maintenance of IoT devices in smart grids is likely to be conducted by electric supply companies. Hence, this one-time training activity, even in a practical deployment scenario, may be tolerable given the extraordinary classification performance achieved as a trade-off. Therefore, for a smart grid use case, training time may not be treated as a KPI. Referring to the star network topology outlined in Section 2.3, each wireless sensor network incorporates an IoT gateway. These gateways have been proposed as an optimal site for RFF, ensuring comprehensive access to all IoT devices within the network for accurate classification. Considering the performance metrics across a large set of devices, the findings from referred studies can be reasonably extrapolated as a valuable reference for the smart grid.
Table 2. Classification accuracy of different models with required training time [31].
| Signal Representation | DL Model | Accuracy | Number of Parameters | Training Time (minutes) | ||
|---|---|---|---|---|---|---|
| w/o CFO Comp. | w/o CFO Comp. | Hybrid | ||||
| I/Q samples | MLP | 54.08% | 55.73% | 78.26% | 19,018,009 | 25 |
| CNN | 64.10% | 92.26% | 98.11% | 4,361,545 | 75 | |
| LSTM | 61.16% | 89.54% | 95.14% | 4,267,289 | 70 | |
| FFT results | MLP | 55.44% | 94.48% | 96.17% | 19,018,009 | 25 |
| CNN | 61.14% | 82.10% | 85.58% | 4,361,545 | 75 | |
| LSTM | 49.20% | 58.26% | 82.81% | 4,267,289 | 69 | |
| Spectrogram | MLP | 88.60% | 91.82% | 95.95% | 8,821,017 | 22 |
| CNN | 83.53% | 95.35% | 96.40% | 1,545,193 | 20 | |
| LSTM | 68.16% | 89.50% | 98.04% | 3,427,609 | 80 | |
2.5. Implementation Aspects
The RFF for smart grids emerges as a highly feasible solution for deployment, primarily owing to its cost-effectiveness and seamless integration capabilities within existing systems. Positioned at the intersection of two prominent domains, RF and ML, RFF may seem intricate from a technical perspective, but from the user’s perspective, it can be offered as a plug-and-play solution, hence, simplifying its adoption into existing IoT. Smart grids, being a critical infrastructure from an operation standpoint, can benefit from the passive nature of RFF systems during training as well as inference stages. This can be helpful in ensuring uninterrupted functionality of the smart grids during the deployment process. RFF systems do not necessitate integration into every IoT device. Instead, they can be intelligently deployed only into IoT gateways and leverage the available processing prowess. Moreover, power efficiency poses no significant challenge since RFF systems operate in passive mode, necessitating no significant power requirement. Considering RFF is deployed as a technology, the hardware infrastructure overhead is minimal. In the features of a typical DL-aided RFF system, the ability to be receiver agnostic was discussed as a desirable feature. It would be a highly recommended feature in the event of a device failure, allowing hot replacement but not necessitating training the NN again. Lastly, an RFF system for smart grids was proposed as an open-set solution. This signifies that once the NN is trained on all legitimate IoT devices, any number of rogue devices could be detected [32]. This scalability further adds to the practicality of RFF. Overall, cost effectiveness, power efficiency, low deployment overhead, and scalability make RFF an appropriate practical choice. It is noteworthy that mobility-induced challenges such as antenna cross-polarization loss and Doppler shift may not pose significant hurdles within the context. This assertion is based on the observation that RFF gateways and IoT sensors predominantly exhibit static characteristics in the said application. These elements further simplify the implementation process.
2.6. Regulatory Requirements
The adherence to regulatory standards for RF-based systems stands as a crucial concern. Every country delineates unique requirements governing the utilization of frequency bands. Moreover, there is a limit on maximum permissible power levels for RF transmission. However, RFF, being a passive technology, poses no challenges in this regard. Since the addition of RFF has been proposed for existing LPWAN, the use of industrial, scientific, and medical (ISM) bands for operation is possible. The use of LPWAN in unlicensed bands is a viable direction for smart cities [14]. Having no additional regulatory compliance contributes to the overall feasibility and cost-effectiveness [15] of implementing RFF technology in wireless sensor networks of smart grids. However, the SDR of an RFF system may require EMC certification [33] subject to user needs.
References
- U.S. Department of Energy. Smart Grid. Available online: https://www.energy.gov/oe/services/technology-development/smart-grid (accessed on 16 September 2023).
- Txone Networks. Achieving Energy Transformation: Building a Cyber Resilient Smart Grid. Available online: https://media.txone.com/prod/uploads/2023/04/Achieving-Energy-Transformation-Building-a-Cyber-Resilient-Smart-Grid-TXOne-WP-202303.pdf (accessed on 16 September 2023).
- Lakshmanan, S.; Tsao, C.-L.; Sivakumar, R.; Sundaresan, K. Securing Wireless Data Networks against Eavesdropping Using Smart Antennas. In Proceedings of the 2008 the 28th International Conference on Distributed Computing Systems, Beijing, China, 17–20 June 2008; pp. 19–27.
- Raymond, D.R.; Midkiff, S.F. Denial-of-Service in Wireless Sensor Networks: Attacks and Defenses. IEEE Pervasive Comput. 2008, 7, 74–81.
- Kannhavong, B.; Nakayama, H.; Nemoto, Y.; Kato, N.; Jamalipour, A. A Survey of Routing Attacks in Mobile Ad Hoc Networks. IEEE Wirel. Commun. 2007, 14, 85–91.
- Meyer, U.; Wetzel, S. A Man-in-the-Middle Attack on UMTS. In Proceedings of the 3rd ACM Workshop on Wireless Security, Philadelphia, PA, USA, 1 October 2004; ACM: New York, NY, USA, 2004; pp. 90–97.
- Ohigashi, T.; Morii, M. A practical message falsification attack on WPA. In Proceedings of the 2009 Joint Workshop on Information Security, Kaohsiung, Taiwan, 6–7 August 2009.
- Paar, C.; Pelzl, J. Understanding Cryptography: A Textbook for Students and Practitioners; Springer: Berlin/Heidelberg, Germany, 2011; ISBN 9783642041006.
- Elliott, C. Quantum Cryptography. IEEE Secur. Priv. 2004, 2, 57–61.
- Wang, J.; Liu, Y.; Niu, S.; Song, H.; Jing, W.; Yuan, J. Blockchain Enabled Verification for Cellular-Connected Unmanned Aircraft System Networking. Future Gener. Comput. Syst. 2021, 123, 233–244.
- Shwartz, O.; Mathov, Y.; Bohadana, M.; Elovici, Y.; Oren, Y. Opening Pandora’s Box: Effective Techniques for Reverse Engineering IoT Devices. In Proceedings of the Smart Card Research and Advanced Applications: 16th International Conference, CARDIS 2017, Lugano, Switzerland, 13–15 November 2017; pp. 1–21.
- Lakew, Y.F.; Singh, A.K.; Bhatia, S. Assessing and Exploiting Security Vulnerabilities of Unmanned Aerial Vehicles. In Smart Systems and IoT: Innovations in Computing; Springer: Berlin/Heidelberg, Germany, 2020; pp. 701–710.
- Schiansky, P.; Kalb, J.; Sztatecsny, E.; Roehsner, M.-C.; Guggemos, T.; Trenti, A.; Bozzio, M.; Walther, P. Demonstration of Quantum-Digital Payments. Nat. Commun. 2023, 14, 3849.
- Wang, W.; Sun, Z.; Piao, S.; Zhu, B.; Ren, K. Wireless Physical-Layer Identification: Modeling and Validation. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2091–2106.
- Brik, V.; Banerjee, S.; Gruteser, M.; Oh, S. Wireless Device Identification with Radiometric Signatures. In Proceedings of the 14th ACM International Conference on Mobile Computing and Networking, San Francisco, CA, USA, 14 September 2008; ACM: New York, NY, USA, 2008; pp. 116–127.
- Communication Network Interdependencies in Smart Grids: Methodology for the Identification of Critical Communication Network Links and Components. Available online: https://www.enisa.europa.eu/publications/communication-network-interdependencies-in-smart-grids (accessed on 1 October 2023).
- Kimani, K.; Oduol, V.; Langat, K. Cyber Security Challenges for IoT-Based Smart Grid Networks. Int. J. Crit. Infrastruct. Prot. 2019, 25, 36–49.
- Wang, W.; Lu, Z. Cyber Security in the Smart Grid: Survey and Challenges. Comput. Netw. 2013, 57, 1344–1371.
- Yousaf, A.; Loan, A.; Babiceanu, R.F.; Yousaf, O. Physical-layer Intrusion Detection System for Smart Jamming Attacks. Trans. Emerg. Telecommun. Technol. 2017, 28, e3189.
- Mekki, K.; Bajic, E.; Chaxel, F.; Meyer, F. A Comparative Study of LPWAN Technologies for Large-Scale IoT Deployment. ICT Express 2019, 5, 1–7.
- Perez, M.; Sierra-Sanchez, F.E.; Chaparro, F.; Chaves, D.M.; Paez-Rueda, C.-I.; Galindo, G.P.; Fajardo, A. Coverage and Energy-Efficiency Experimental Test Performance for a Comparative Evaluation of Unlicensed LPWAN: LoRaWAN and SigFox. IEEE Access 2022, 10, 97183–97196.
- Hossain, M.I.; Markendahl, J.I. Comparison of LPWAN Technologies: Cost Structure and Scalability. Wirel. Pers. Commun. 2021, 121, 887–903.
- The Full Story on UK Smart Meters. Available online: https://www.smartme.co.uk/smets-2.html (accessed on 20 September 2023).
- Agung Enriko, I.K.; Zaenal Abidin, A.; Noor, A.S. Design and Implementation of LoRaWAN-Based Smart Meter System for Rural Electrification. In Proceedings of the 2021 International Conference on Green Energy, Computing and Sustainable Technology (GECOST), Miri, Malaysia, 7 July 2021; pp. 1–5.
- Gallardo, J.L.; Ahmed, M.A.; Jara, N. LoRa IoT-Based Architecture for Advanced Metering Infrastructure in Residential Smart Grid. IEEE Access 2021, 9, 124295–124312.
- Rawlinson, K. HP Study Reveals 70 Percent of Internet of Things Devices Vulnerable to Attack. Available online: https://www.proquest.com/docview/1549571608 (accessed on 3 December 2023).
- Brar, H.S.; Kumar, G. Cybercrimes: A Proposed Taxonomy and Challenges. J. Comput. Netw. Commun. 2018, 2018, 1798659.
- Bouzidi, M.; Amro, A.; Dalveren, Y.; Alaya Cheikh, F.; Derawi, M. LPWAN Cyber Security Risk Analysis: Building a Secure IQRF Solution. Sensors 2023, 23, 2078.
- Ali, A.M.; Uzundurukan, E.; Kara, A. Assessment of Features and Classifiers for Bluetooth RF Fingerprinting. IEEE Access 2019, 7, 50524–50535.
- Bouzidi, M.; Mohamed, M.; Dalveren, Y.; Moldsvor, A.; Cheikh, F.A.; Derawi, M. Propagation Measurements for IQRF Network in an Urban Environment. Sensors 2022, 22, 7012.
- Shen, G. Deep Learning Enhanced Radio Frequency Fingerprint Identification for LoRa. Ph.D. Thesis, University of Liverpool, Liverpool, UK, June 2023.
- Andrews, S.D. Extensions to Radio Frequency Fingerprinting. Ph.D. Thesis, Virginia Polytechnic Institute and State University, Blacksburg, VA, USA, 2019.
- EN 300 220-1 V2.4.1; Technical Characteristics and Test Methods. European Committee for Electrotechnical Standardization: Brussels, Belgium, January 2012.
More
Information
Subjects:
Engineering, Electrical & Electronic
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
494
Revisions:
2 times
(View History)
Update Date:
18 Dec 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




