Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Stavros Shiaeles | -- | 3014 | 2023-09-22 12:37:43 | | | |
| 2 | Lindsay Dong | Meta information modification | 3014 | 2023-09-22 17:09:45 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Chauhan, M.; Shiaeles, S. Problems and Proposed Solutions of Cloud Security Frameworks. Encyclopedia. Available online: https://encyclopedia.pub/entry/49526 (accessed on 08 February 2026).
Chauhan M, Shiaeles S. Problems and Proposed Solutions of Cloud Security Frameworks. Encyclopedia. Available at: https://encyclopedia.pub/entry/49526. Accessed February 08, 2026.
Chauhan, Milan, Stavros Shiaeles. "Problems and Proposed Solutions of Cloud Security Frameworks" Encyclopedia, https://encyclopedia.pub/entry/49526 (accessed February 08, 2026).
Chauhan, M., & Shiaeles, S. (2023, September 22). Problems and Proposed Solutions of Cloud Security Frameworks. In Encyclopedia. https://encyclopedia.pub/entry/49526
Chauhan, Milan and Stavros Shiaeles. "Problems and Proposed Solutions of Cloud Security Frameworks." Encyclopedia. Web. 22 September, 2023.
Copy Citation
Cloud computing has its roots in several fundamental concepts and technologies. In the 1960s, J.C.R. Licklider, a prominent computer scientist, envisioned an “Intergalactic Computer Network” that allowed remote access to programs and data, laying the groundwork for distributed computing models.
cloud security
security frameworks
NIST
COBIT
ISO
AWS
ENISA
1. Introduction
First and foremost, what exactly is cloud computing? Cloud computing is a technology that allows anybody to remotely access high computing equipment and computing services without having to purchase physical infrastructure. And the fundamental advantage of cloud computing is that it only costs on a pay-as-you-go basis. The cloud is a game-changing technology because it enables flexibility, scalability, and a cost-effective means of managing IT resources. According to recent predictions, the worldwide cloud computing market will exceed $800 billion in the next 2–3 years [1][2][3].
However, the acceptance and expanded use of cloud computing raises security concerns. Data breaches, unauthorized access, and data loss during transfer or due to system failure are examples of security issues. Five factors determine the major component of security concerns [4][5][6].
-
Network related
-
Confidentiality and privacy
-
Data-related issues
-
Virtualization-related issues
-
Others
Cloud security frameworks are created to assist organizations in understanding their vulnerabilities when building cloud infrastructure. Cloud security frameworks are a collection of rules, standards, and best that companies may use to safeguard their cloud environments against security risks. Its core overview is the required policies, tools, settings, and procedures for securing and managing cloud infrastructure. It helps organizations to identify, access, and reduce risks by providing a systematic method for managing cloud security threats.
There are several well-known frameworks available. CSA STAR (Cloud Security Alliance Control Matrix), FedRAMP, NIST (National Institute of Standards and Technology), COBIT 5, International Organization for Standardization, and Well-Architected Cloud Frameworks (AWS, Azure, Google) are a few examples. Companies confront considerable issues when it comes to guaranteeing the confidentiality, integrity, and availability of their data and applications in cloud environments. Inadequate cloud security typically leads to vulnerabilities, unauthorized access, data breaches, and significant harm to the organization’s brand and consumer confidence.
2. Cloud Computing
Cloud computing has its roots in several fundamental concepts and technologies. In the 1960s, J.C.R. Licklider, a prominent computer scientist, envisioned an “Intergalactic Computer Network” that allowed remote access to programs and data, laying the groundwork for distributed computing models. In the 1990s, grid computing emerged as a way to harness geographically dispersed resources for computationally intensive tasks. The Globus Toolkit, developed by Ian Foster and Carl Kesselman, provided a software infrastructure for managing computational grids. Utility computing also emerged during this time, offering computing resources as a pay-per-use utility. Sun Microsystems and Amazon introduced utility computing models, demonstrating the benefits of on-demand resource rental.
The phrase “cloud computing” first appeared in the mid-2000s, revolutionizing how computer resources are distributed and utilized. Amazon Web Services (AWS) established Infrastructure as a Service (IaaS) in 2006, providing virtualized servers, storage, and networking capabilities via the Internet. This revolutionized traditional hosting paradigms by introducing scalable and adaptable cloud-based infrastructure. The National Institute of Standards and Technology (NIST) was instrumental in standardizing cloud computing, describing it in 2011 as a concept that allows on-demand network access to a shared pool of programmable computing resources. NIST emphasized the model’s ease of use and universality. Extensive study has been conducted to examine many views on cloud computing, offering insight into its consequences and potential.
2.1. Cloud Security Frameworks
2.1.1. Ability of Framework
Cloud security frameworks are designed to ensure an organization’s data’s confidentiality, integrity and availability in a cloud environment [3]. Undertook a critical examination of the usefulness of new security frameworks in increasing cloud security. The study aims to analyze and evaluate various cloud security standards and frameworks to assess their strengths, limitations, and overall influence on improving cloud security posture. The authors undertook a thorough examination of many well-known cloud security frameworks, including the Cloud Security Alliance (CSA) Security Guidance, the NIST Cloud Computing Security Reference Architecture, and the ISO/IEC 27017:2015 Cloud Security Controls. These frameworks were assessed based on their ability to meet important cloud security concerns such as data protection, access management, encryption, and incident response. The study revealed the benefits and drawbacks of each framework through a comparison. It provided readers with insights into the precise security controls and recommendations provided by these standards, allowing them to grasp their application and significance in various cloud deployment models. Furthermore, the study looked at how new security frameworks fared compared to earlier standards [5].

2.1.2. Use of Framework
It went over how these frameworks addressed new security problems including container security, DevOps security, and threat information sharing. The study’s findings offer light on the changing landscape of cloud security frameworks and their influence on cloud security. It emphasized the significance of continuously evaluating and improving these frameworks in order to with the dynamic nature of cloud threats. ISACA recommends adopting the COBIT 5 framework to oversee and manage cloud investments, guaranteeing consistency in order to maximize value and minimize risk. Overall, strategy alignment and goal accomplishment are critical in cloud computing, making cloud governance a crucial feature. This framework integrates several crucial components, including governance, risk management, compliance, incident response, and ongoing monitoring. It stresses the necessity for a comprehensive and proactive approach to ensuring cybersecurity in cloud settings.
2.1.3. Implementation Challenges
Implementing cloud security frameworks presents a range of challenges stemming from the complex nature of cloud ecosystems and evolving threat landscapes. Studies by [7][8] emphasize the following challenges:
Integration Complexity: Organizations often struggle with integrating cloud security frameworks seamlessly into existing IT infrastructures, resulting in interoperability issues and redundant controls.
Resource Allocation: Limited resources, both human and financial, can hinder effective implementation [9] suggest that organizations must carefully allocate resources to address critical security controls.
Shared Responsibility Model: Cloud providers and users share responsibility for security. Defining roles and responsibilities can lead to ambiguity and gaps in implementation.
Compliance and Regulations: Ensuring compliance with industry regulations and data protection laws adds complexity to implementation [9] highlight the need to adapt frameworks to meet specific regulatory requirements.
Dynamic Environment: Cloud environments are dynamic and scalable, making continuous monitoring and control adaptation a challenge. Automation and real-time threat detection are vital to maintaining security.
While the literature on cloud security frameworks is rich, earlier research has highlighted many limitations. These gaps represent areas where further research and development are required to improve the efficacy of cloud security systems.
2.2. Cloud Security Problems and Solutions
Cloud computing has revolutionized the way organizations store, process, and access data and applications. However, this paradigm shift has introduced a range of security challenges (as shown in Figure 1) that need to be addressed to ensure the confidentiality, integrity, and availability of data in the cloud [10][11][12].

Figure 1. Main Components of Cloud Security Issues. Image Source: [13].
2.2.1. Cloud Security Problems
Data Privacy and Leakage: Data privacy concerns arise due to the shared nature of cloud environments. Unauthorized access or data breaches can lead to sensitive information leakage [14].
Data Location and Jurisdiction: The dynamic nature of cloud infrastructures can lead to uncertainty about the physical location of data, potentially causing conflicts with data protection regulations and legal jurisdictions [15].
Multi-tenancy Risks: Multi-tenancy introduces the risk of resource and data co-residency, where data from different customers may reside on the same physical hardware, potentially leading to data exposure [16].
Inadequate Access Control: Ensuring proper access control mechanisms to prevent unauthorized users from accessing resources and data is challenging in cloud environments with complex access requirements [16].
2.2.2. Cloud Security Solutions
Various methods have been suggested and used to solve the issues and lessen the dangers connected with cloud security. Here are some examples.
Encryption and Key Management: Encrypting data at rest and in transit helps protect against unauthorized access. Proper key management solutions are crucial to maintaining the security of encryption mechanisms [17].
Identity and Access Management (IAM): Robust IAM solutions are essential for managing user identities, roles, and permissions. Implementing the principle of least privilege helps minimize potential risks [18].
Virtualization Security: Properly securing the virtualization layer is essential to prevent attacks that target vulnerabilities in the hypervisor or virtual machine instances [14].
Cloud-specific Security Tools: Utilizing cloud-native security tools can enhance threat detection and response within the cloud environment. Tools like AWS GuardDuty and Azure Security Center offer real-time monitoring.
Security Monitoring and Incident Reaction: The use of comprehensive security monitoring technologies and methodologies enables the identification and timely reaction to security issues. Continuous monitoring, log analysis, and threat intelligence are all critical in detecting and mitigating security breaches [7].
Standards and Certifications for Cloud Security: Industry-recognized security standards and certifications provide a framework for analyzing and assuring the security of cloud services. ISO 27001, CSA STAR, and FedRAMP standards assist organizations in evaluating the security capabilities of CSPs [8]. Regular security assessments and audits assist organizations in identifying vulnerabilities and ensuring compliance with security regulations. A proactive security strategy includes independent audits, penetration testing, and vulnerability scanning [10]. Implementing safe setups for cloud services as well as hardening the underlying infrastructure to mitigate possible vulnerabilities [19][20].
3. Cloud Security Frameworks
The growing use of cloud computing in recent years has altered the way businesses handle and store data. The cloud has various advantages, including scalability, cost-effectiveness, and flexibility. However, with the growing reliance on cloud services, implementing adequate security measures is critical. Cloud security frameworks help organizations define and implement security policies that are particular to their cloud environments [21][22]. They provide advice on risk assessment, selecting and implementing security measures, security monitoring, incident response planning, and continuing security improvement. Table 1 introduce to different type of frameworks available in the market.
Table 1. Introduction to Frameworks.
| Frameworks | Description |
|---|---|
| COBIT 5 for Cloud Computing | The COBIT framework is extended to solve unique cloud computing concerns. |
| NIST | Provides standards and best practices for cloud computing security and privacy issues. |
| ISO 27017 | Code of practice for information security measures for cloud services based on ISO/IEC 27002. |
| FedRAMP | A federal program in the United States provides a standardized method for cloud security evaluation and authorization. |
| AWS Well-Architected Framework | Best practices and guidelines for creating and running safe and efficient cloud infrastructures are provided. |
| CSA STAR | A registry that details the security practices of cloud service providers using the CSA’s Cloud Control Matrix. |
| ENISA Cloud Security Guide | Addresses several security topics while providing information on analyzing and reducing threats in cloud settings. |
| CIS Controls for Cloud | Based on the CIS Controls, tailored security controls and practices for safeguarding cloud environments. |
| Cloud Controls Matrix (CCM) | Provides a set of cloud-specific security measures that are compliant with industry standards and legislation. |
| CSA Security Guidance | Describes thorough security best practices and controls for various cloud service architectures and deployments. |
3.1. COBIT 5 for Cloud Security
ISACA (Information Systems Audit and Control Association) developed COBIT 5 is a worldwide recognized methodology for enterprise IT governance and management [23]. While COBIT 5 is not created expressly for cloud security, it does present a complete set of principles and practices that can be used to successfully regulate and safeguard cloud computing systems [24]. It provides governance, risk management, and control objectives that allow organizations to successfully manage and secure cloud services.
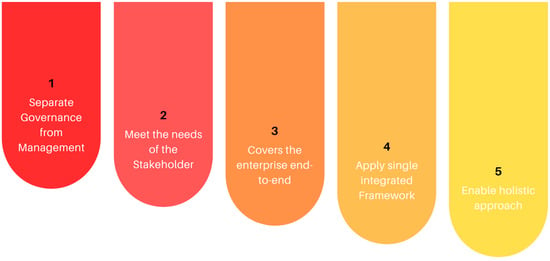
Here is the understable definition of each principles of the Figure 2.

Figure 2. COBIT5 Principles.
3.2. NIST SP 800-144
The National Institute of Standards and Technology (NIST) has created a framework to help businesses defend their cloud infrastructure. This framework offers a complete collection of concepts, rules, and best for cloud-based environment security. Organizations may improve the security of their cloud infrastructure and efficiently manage risks by adopting the NIST methodology [25][26]. However, it is critical to recognize both the NIST framework’s strengths and limits. However, the parent framework of NIST SP 800-144 consists of five core functions [27].
Identify: Understanding the organization’s systems, assets, data, and capabilities is part of this role. It entails identifying and recording the resources that must be safeguarded, as well as the hazards connected with them. This role serves as the foundation for creating successful cybersecurity policies and procedures.
Protect: The Protect function is responsible for putting protections in place to assure the delivery of key services and the security of data. Access control, data encryption, training and awareness programs, and adopting security measures to reduce identified risks are all part of it.
Detect: The Detect function is responsible for designing and deploying tools to quickly identify cybersecurity occurrences. It contains methods for continuous monitoring, anomaly detection, and incident response to detect and respond to cybersecurity events in real-time.
Respond: The Respond function is responsible for developing and implementing a response strategy to reduce the effects of cybersecurity events. It includes creating an incident response strategy, doing incident analysis, and taking the necessary steps to contain and recover from cybersecurity problems.
Recover: The Recover function’s goal is to restore services and capabilities that have been impacted by cybersecurity events while also preventing future occurrences. It comprises tasks such as system recovery, stakeholder communication, and using lessons gained to enhance future incident response.
3.3. ISO 27017:2015
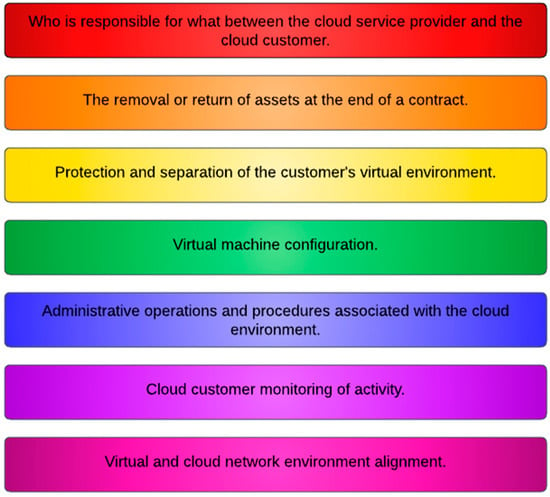
ISO 27017 was created as part of the ISO 27000 series to address the particular security problems associated with cloud computing. It is based on the larger ISO 27001 standard, which specifies the criteria for implementing an information security management system (ISMS). ISO 27017 tailors these criteria explicitly for cloud service providers and clients, giving additional guidelines and controls to improve cloud security. ISO/IEC 27017 provides guidelines for information security controls relevant to the use of cloud services by giving further implementation instructions for the 37 controls listed in ISO/IEC 27002 as well as seven additional cloud-related controls (As shown in Figure 3) that address the following.

Figure 3. Standards of ISO/IEC 27017.
3.4. Cloud Security Alliance (STAR)
The Cloud Security Alliance (CSA) created the CSA STAR (Security, Trust, and Assurance Registry) architecture to address the requirement for transparency and assurance in cloud service provider (CSP) security. It offers a collection of best guidelines for identifying and managing the security risks associated with cloud services [28].
Cloud Security: The framework focuses on safeguarding cloud-based systems and data from unauthorized access, data breaches, and other security risks.
Trust: It is critical to establish trust between cloud service providers and cloud clients. The framework’s goal is to increase openness, accountability, and trust in the cloud environment.
Assurance: Providing proof and validation of security controls and practices is what assurance is all about. The framework encourages third-party audits and certifications to improve cloud security assurance.

3.5. AWS Well-Architected Framework
AWS Well-Architected is an Amazon Web Services (AWS) framework that provides architectural best practices and guidelines for creating and maintaining cloud-based applications. It outlines the fundamental ideas and best practices for developing safe, high-performing, robust, and efficient systems on AWS. The Six pillars of the Well-Architected Framework are shown in Figure 4.

Figure 4. Six Pillars of AWS (Source: Tutorials Dojo).
4. Cloud Security Challenges and Proposed Solutions
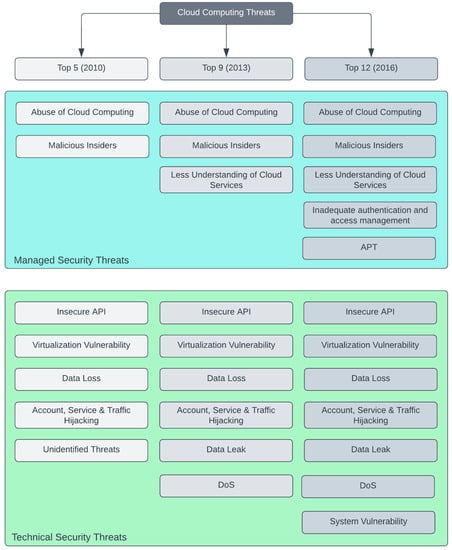
“Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications and services) that can be rapidly provisioned and released with minimal management effort and or service provider interaction”, According to the National Institute of Standards and Technology (NIST), cloud computing is a fast emerging technology. Many individuals utilize cloud computing unconsciously in their daily lives through services such as Microsoft Office 365, Gmail, and Dropbox. Adopting cloud computing has several benefits, including anytime-anywhere accessibility, increased geographic coverage, lower infrastructure investment, and more [29]. There are, however, security risks involved with cloud computing. These risks can jeopardize the security of cloud-stored data, programs, and infrastructure. With organizations increasingly utilizing cloud services, it is critical to recognize and manage these threats in order to protect the confidentiality, integrity, and availability of cloud resources. The diagram below depicts some frequent cloud security issues. The given Figure 5 describes some common cloud security problems [30][31][32] and Table 2 describe the effects on cloud & affected cloud services.

Figure 5. Top Cloud Security threats.
Table 2. Comparative Study of Cloud security problems.
| Threats | Affected Cloud Services | Effects | Solutions |
|---|---|---|---|
| Abuse of Cloud Computing | PaaS and IaaS | Validation Loss, Service Fraud, Strong attacks due to unidentified sign-up | Network analysis, Robust registration and multifactor authentication |
| Insecure API | PaaS, SaaS, IaaS | Improper authentication and authorization, the wrong transmission of Content | Data Encryption, Strong access control and multi-factor authentication |
| Malicious Insider | PaaS, SaaS and IaaS | Assets damage, productivity loss and confidentiality break | Duty Segregation, IAM policies |
| Data Loss | PaaS, SaaS and IaaS | Removal, modification and stealing of confidential and personal data | Disaster, backup and recovery management |
| Service and Account hijacking | PaaS, SaaS and IaaS | Breaching into critical areas of cloud and server, access of root account | Adoption of strong authentication, and security policies. |
5. Conclusions
These frameworks give useful guidelines and controls for protecting cloud computing systems, addressing critical security concerns, and maintaining data and resource confidentiality, integrity, and availability. The investigation indicated that there are several frameworks available to meet the particular issues involved with protecting cloud systems in terms of cloud security frameworks. Each framework has its own set of characteristics, strengths, and shortcomings. When several frameworks are compared and contrasted, it becomes clear that no single framework can fully fulfill all criteria for any cloud deployment because every framework has disadvantages and limitations. To choose the best framework or mix of frameworks, organizations must carefully examine their unique demands, compliance requirements, and risk tolerance. Furthermore, the research effort provided light on typical challenges and weaknesses in cloud security. Data breaches, unauthorized access, unsecured APIs, insider risks, and insufficient security measures are examples of these. These problems highlight the crucial importance of strong security, extensive risk assessments, and constant monitoring and enhancement of cloud infrastructures. Cloud security issues offer substantial concerns for organizations that use cloud computing services. These issues, however, may be efficiently managed with proactive steps and solid security systems. Data breaches, unprotected APIs, cloud computing abuse, and hostile insider threats are just a few of the major cloud security issues. Organizations should focus on adopting solutions such as tight access restrictions, encryption of sensitive data, frequent security assessments, monitoring and analysis of user actions, and robust authentication systems such as multi-factor authentication to address these issues. Furthermore, educating users on cloud security risks and recommending and utilizing third-party security services can all help to improve cloud security.
References
- Rayaprolu, A. How-Many-Companies-Use-Cloud-Computing/#gref, Techjury, February 2023. Available online: https://techjury.net/blog (accessed on 2 April 2023).
- Marston, S.; Li, Z.; Bandyopadhyay, S.; Zhang, J.; Ghalsasi, A. Cloud computing—The business perspective. Decis. Support Syst. 2011, 51, 176–189.
- Weinhardt, C.; Anandasivam, A.; Blau, B.; Borissov, N.; Meinl, T. Cloud Computing—A Classification, Business Models, and Research Directions. Bus. Inf. Syst. Eng. 2009, 1, 391–399.
- Bhushan, K.; Gupta, B.B. Security challenges in cloud computing: State-of-art. Int. J. Big Data Intell. 2017, 4, 81–107.
- Di Giulio, C.; Sprabery, R.; Kamhoua, C.; Kwiat, K.; Campbell, R.H.; Bashir, M.N. Cloud Standards in Comparison: Are New Security Frameworks Improving Cloud Security? IEEE: Honololu, HI, USA, 2017.
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; Rabkin, A.; Stoica, I.; et al. A view of cloud computing. Commun. ACM 2010, 53, 50–58.
- Mohanan, S.; Sridhar, N.; Bhatia, S. Comparative Analysis of Various Cloud Security Frameworks. In Proceedings of the 6th International Congress on Information and Communication Technology, London, UK, 25–26 February 2019.
- Popa, D.; Cremene, M.; Borda, M.; Boudaoud, K. A security framework for mobile cloud applications. In Proceedings of the 11th RoEduNet International Conference, Sinaia, Romania, 17–19 January 2013.
- Ukil, A.; Jana, D.; Das, A. A Security Framework in Cloud Computing Infrastructure. Int. J. Netw. Secur. Its Appl. 2013, 5, 11–24.
- Hashizume, K.; Rosado, D.G.; Fernández-Medina, E.; Fernandez, E.B. An analysis of security issues for cloud computing. J. Internet Serv. Appl. 2013, 4, 1–13.
- Grobauer, B.; Walloschek, T.; Stocker, E. Understanding Cloud Computing Vulnerabilities; IEEE: Piscataway, NJ, USA, 2011.
- Rodero-Merino, L.; Vaquero, L.M.; Caron, E.; Muresan, A.; Desprez, F. Building Safe PaaS Clouds: A Survey on Security in Multitenant Software Platforms. Comput. Secur. 2012, 31, 96–108.
- Tsochev, G.R.; Trifonov, R.I. Cloud computing security requirements: A Review. IOP Conf. Ser. Mater. Sci. Eng. 2022, 1216, 012001.
- Ristenpart, T.; Tromer, E.; Shacham, H.; Savage, S. Hey you get off of my cloud: Exploring information leakage in third-party compute clouds. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009.
- European Commission. MEMO_12_713. European Commission. 27 September 2012. Available online: https://ec.europa.eu/commission/presscorner/detail/en/ (accessed on 4 April 2023).
- Subashini, S.; Kavitha, V. A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 2011, 34, 1–11.
- Kamara, S.; Lauter, K. Cryptographic Cloud Storage. In Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6054, pp. 136–149.
- Sonam Sudha, M.A. Identity and Access Management in Cloud. J. Res. Appl. Sci. 2014, 7.
- Amara, N.; Huang, Z.; Awais, A. Cloud Computing Security Threats and Attacks with Their Mitigation Techniques. In Proceedings of the 2017 International Conference on Cyber-Enabled Distributed Computing and Knowledge Discovery (CyberC), Nanjing, China, 12–14 October 2017.
- Neves Calheiros, R.; Ranjan, R.; Beloglazov, A.; De Rose, C.A.; Buyya, R. CloudSim: A toolkit for modeling and simulation of cloud computing environments and evaluation of resource provisioning algorithms. Softw. Pract. Exp. 2011, 41, 23–50.
- Youssef, A.; Alageel, M. A Framework for Secure Cloud Computing. Int. J. Comput. Sci. Issues 2012, 9.
- Patel, V. A framework for secure and decentralized sharing of medical imaging data. Health Inform. J. 2019, 25, 1398–1411.
- ISACA. Security Considerations for Cloud Computing; ISACA: Schaumburg, IL, USA, 2012.
- OIlloh, O.; Aghili, S.; Butakov, S. Using COBIT 5 for Risk to Develop Cloud Computing SLA Evaluation Templates. In Proceedings of the 12th International Conference on Services Oriented Computing 2014, Paris, France, 3–6 November 2014.
- Mell, P.; Grance, T. The NIST Definition of Cloud Computing (NIST Special Publication 800-145); National Institute of Standards and Technology: Gaithersburg, MD, USA, 2011.
- Jansen, W.; Grance, T. Guidelines on Security and Privacy in Public Cloud Computing; NIST: Gaithersburg, MD, USA, 2011.
- NIST. NIST US Government Cloud Computing Technology Roadmap, Release 1.0 (Draft); NIST: Gaithersburg, MD, USA, 2011.
- CSA. Security Guidance for Critical Areas of Focus in Cloud Computing v3.0; CSA: Toronto, ON, Canada, 2011.
- Sharma, R.; Trivedi, R.K. Literature review: Cloud Computing—Security Issues, Solution and Technologies. Int. J. Eng. Res. 2014, 3, 221–225.
- Park, S.-J.; Lee, Y.-J.; Park, W.-H. Configuration Method of AWS Security Architecture That Is Applicable to the Cloud Lifecycle for Sustainable Social Network. Commun. Secur. Soc.-Oriented Cyber Spaces 2021, 2021, 3686423.
- Suo, H.; Wan, J.; Zou, C.; Liu, J. Security in the internet of things: A review. In Proceedings of the 10th International Conference on Frontiers of Information Technology, Hangzhou, China, 23–25 March 2012.
- Rittinghouse, J.W.; Ransome, J.F. Cloud Computing: Implementation, Management, and Security; CRC Press: Boca Raton, FL, USA, 2016.
More
Information
Subjects:
Computer Science, Information Systems
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
1.2K
Revisions:
2 times
(View History)
Update Date:
22 Sep 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




