Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Yin, Z.; Lee, S.U. Web Open-Source Projects Based on Java and PHP. Encyclopedia. Available online: https://encyclopedia.pub/entry/48369 (accessed on 08 February 2026).
Yin Z, Lee SU. Web Open-Source Projects Based on Java and PHP. Encyclopedia. Available at: https://encyclopedia.pub/entry/48369. Accessed February 08, 2026.
Yin, Zhen, Scott Uk-Jin Lee. "Web Open-Source Projects Based on Java and PHP" Encyclopedia, https://encyclopedia.pub/entry/48369 (accessed February 08, 2026).
Yin, Z., & Lee, S.U. (2023, August 23). Web Open-Source Projects Based on Java and PHP. In Encyclopedia. https://encyclopedia.pub/entry/48369
Yin, Zhen and Scott Uk-Jin Lee. "Web Open-Source Projects Based on Java and PHP." Encyclopedia. Web. 23 August, 2023.
Copy Citation
During website development, the selection of suitable computer language and reasonable use of relevant open-source projects is imperative. Although the two languages, PHP and Java, have been extensively investigated in this context, there are not many security test reports based on their open-source projects.
PHP
Java
web security
1. Introduction
With the continuous development and improvement of computer languages, numerous excellent languages have emerged in the field of web development. PHP is currently the most-used language, followed by ASP.NET, Ruby, and Java [1]. The selection of a programming language is primarily based on each language’s unique features and standard library, I/O operations, operating system, and programming language compatibility for simulations. Furthermore, whilst graphical performance is important, raw performance (with graphics turned off or disabled) is far more so; start-up speed is barely relevant at all [2]. However, many developers prioritize implementing functions and satisfying user requirements over web security, which may lead to vulnerabilities that could be exploited to cause irreparable loss. Besides the strength of the selected language, poor security knowledge among web developers and the blind use of open-source projects also increase vulnerabilities [3]. Although abundant literature and multiple organizations (e.g., Open Web Application Security Project (OWASP)) have argued that web vulnerabilities are a major problem in modern computer languages, most current research analyzes single programming languages or a few types of web attacks [4][5]. In addition, comparative studies have been conducted primarily for attack analysis of Cross-site Scripting (XSS) and SQL injection, and few extensive security performance tests have been performed on web programs written in different programming languages. In early research, the strengths and weaknesses of PHP and Java were compared, revealing that Java is more robust than PHP, and data analysis was conducted on two common vulnerabilities of XSS and SQL injection [3]. It was concluded that web applications written using Java exhibit fewer vulnerabilities. A recent study evaluated the filtering capabilities of 12 popular XSS filters (a security mechanism to detect whether the user input content conforms to the specification) in terms of success rate and achieving comprehensive XSS filtering data analysis to help developers choose appropriate filters to ensure web safety [6]. However, with the continuous updating of language versions and mining of web vulnerabilities, a single attack test cannot guarantee the data security of web applications composed using specific programming languages.
To resolve this problem, a comprehensive web security test is performed on web-related open-source projects based on PHP and Java. To this end, different shooting range websites capable of carrying malicious payloads through the ten most popular open-source frameworks are designed [7]. The websites are equipped with the eight most popular filters and four SQL injection filters. The aforementioned experimental environment is used to conduct penetration tests comprising nearly 700 attack codes on XSS, Lightweight Directory Access Protocol (LDAP), Local File Inclusion (LFI), and SQL injection filter mechanisms. The security differences between web programs written in Java and PHP in open-source projects are evaluated by analyzing the filtering results of different shooting ranges corresponding to different attacks.
2. Web Open-Source Projects Based on Java and PHP
Helmiawan et al. (2020) analyzed the security of open-source web applications through the top ten of OWASP. This study showed the vulnerability of the web application in the experiment and what security risks they had [8], but it does not conduct further research on these security risks and only makes superficial suggestions.
Talib et al. (2021) adjusted the configuration of 12 popular open-source filters and provided suggestions for developers to use filters more reasonably [9]. However, in their research, they only modified some rules for those filters and did not deviate from the strategies of filters, so the suggestions given can only be effective within a certain range. The scheme proposed in this research can be used for security policy extension.
Shahriar et al. (2016) proposed a method to detect LDAP attacks and implemented it based on PHP [7]. However, the experimental object used in this test is a PHP application written for the experimental test, meaning it can’t guarantee the effectiveness of real environment tests such as open-source applications. In order to provide effective suggestions for developers to use open-source applications, this research selects some popular frameworks that support LDAP and conducts attack detection on the filtering rules of different frameworks to ensure the practicability of the suggestions.
Likaj et al. (2021) conducted the first security assessment of Cross-Site Request Forgery (CSRF) defense on popular web open-source frameworks, identified 16 defense measures and 18 security threats, and discussed the vulnerabilities of three of these frameworks [10]. The integration of popular frameworks in their research provided researchers with convenience. The top five frameworks in different languages from the framework rank were selected and used as test objects to conduct a more comprehensive attack test.
Che et al. (2021) demonstrated LFI vulnerability risks and implemented a LFI detection method based on Tor Proxy. The study pointed out that most of the current vulnerability scanners focus on SQL injection and XSS, so the security detection on LFI is relatively weak, and due to the difference in security awareness of developers, different artificial vulnerabilities will be generated [11]. The test experiment in this study uses the LFI testlevel of Damn Vulnerable Web Application (DVWA), considering the level of different developers, to verify the effectiveness of LFI attack from the attacker’s perspective at different levels.
3. XSS
XSS remains one of the most prevalent security vulnerabilities in web applications to this day [12]. XSS can be roughly classified into three types of attack methods—reflected XSS, DOM-based XSS, and stored XSS. The attack processes are illustrated in Figure 1. The general methodology of reflected XSS is based on malicious connections. The attacker deploys a connection to the server comprising a JavaScript code to obtain the target’s cookie value. The general methodology of stored XSS involves text box content input. Vulnerabilities are more common in social networking site message boards, comment areas, and other areas that allow users to input content freely. Further, in form submission areas, attackers often insert <img> or <script> tags within the content to steal information. Although most websites filter tags by limiting the number of strings in the filter or using regular expressions, code splitting is still active in several small websites. This scenario is discussed in the next section. DOM-type XSS is essentially a special type of reflective XSS—it is based on the DOM document object model. With the rapid development of single-page applications (SPAs), progressively more web programs are being dynamically handled by browsers, which increases the threat of such vulnerabilities. As illustrated in Figure 2, this type of XSS is implemented at the front end without bypassing the server. Thus, this type of vulnerability often exists in websites with tabbed navigation.
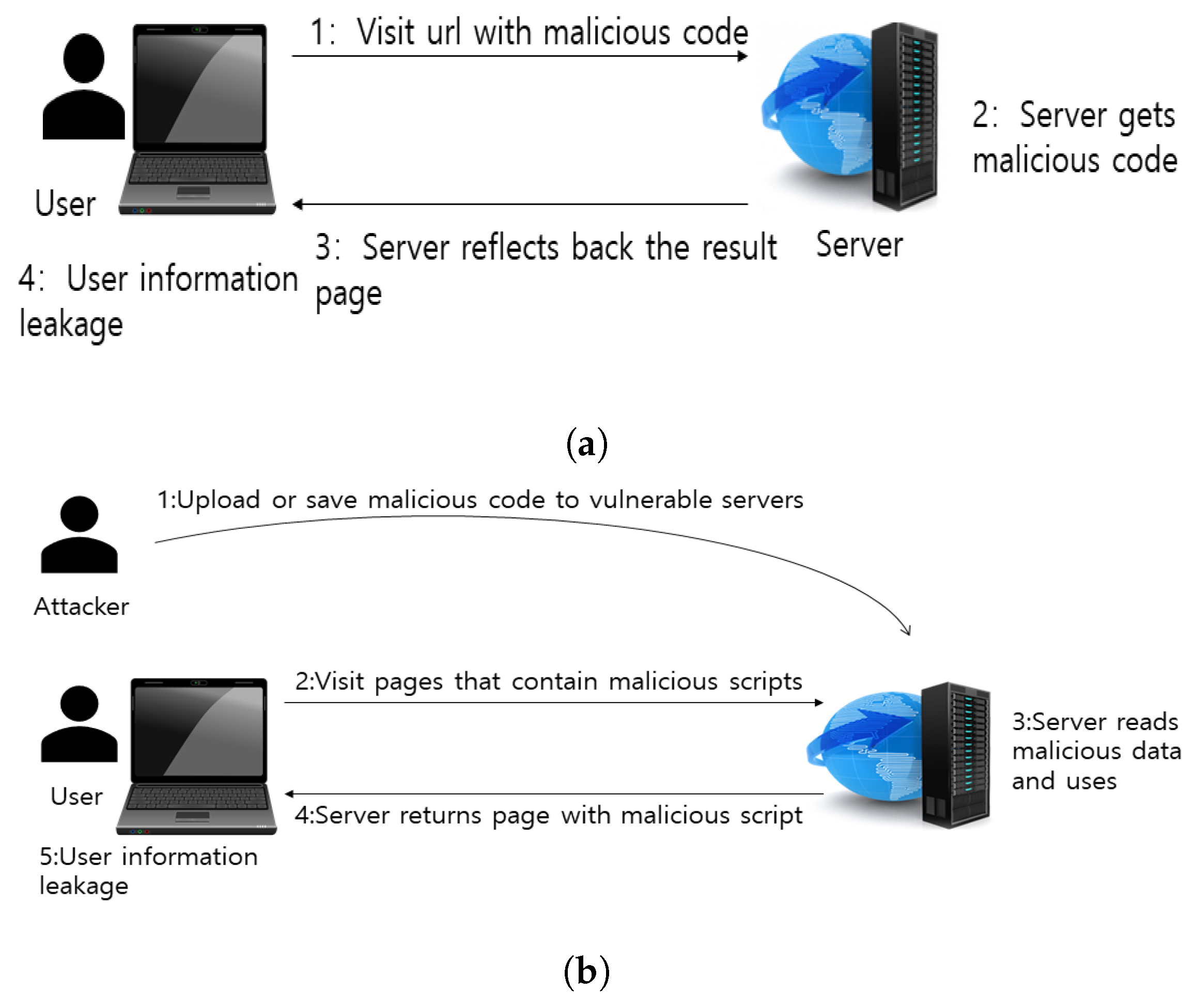
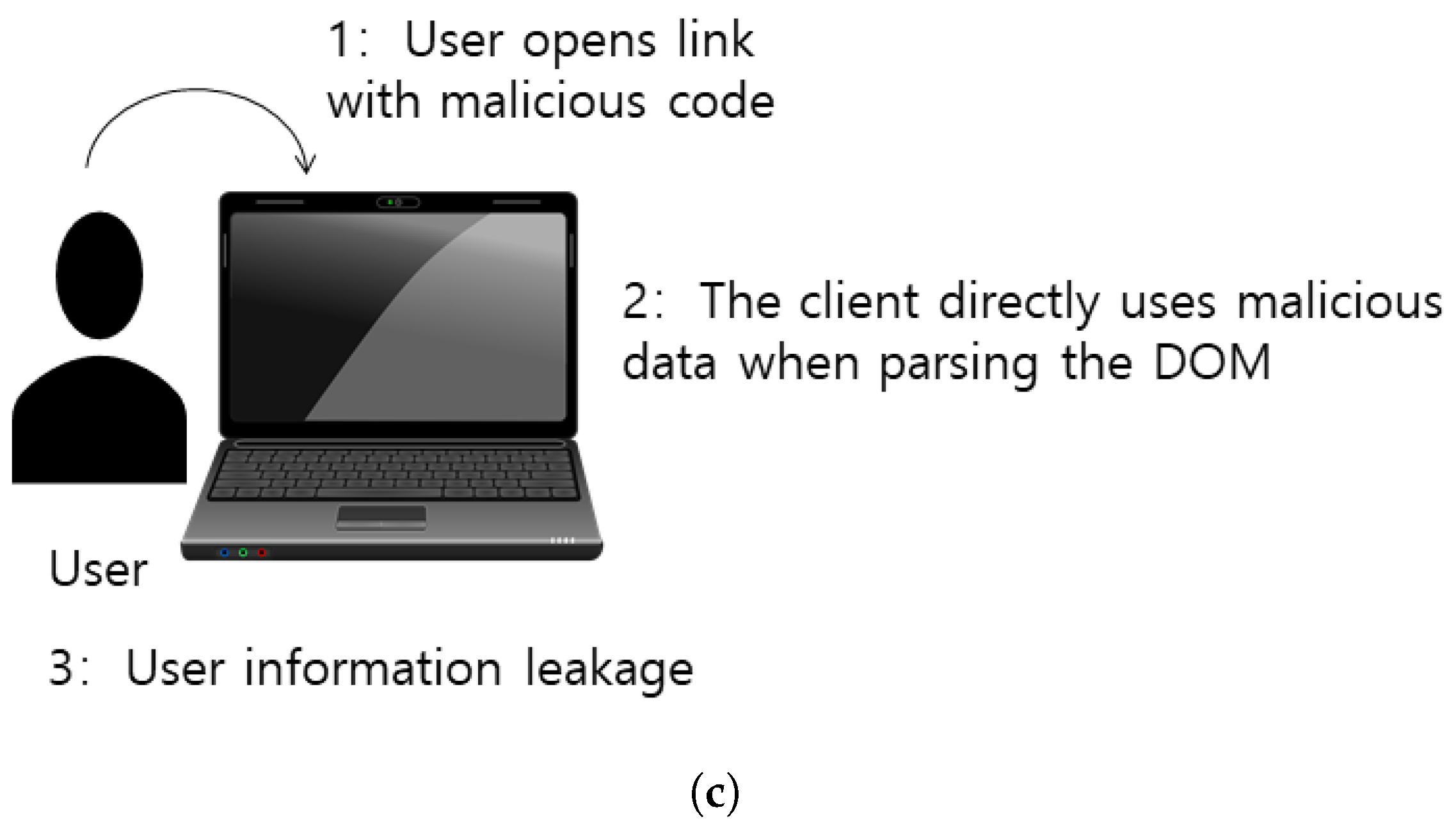
Figure 1. Types of XSS attack methods. (a) Reflect-XSS; (b) Stored-XSS; (c) Dom-XSS.
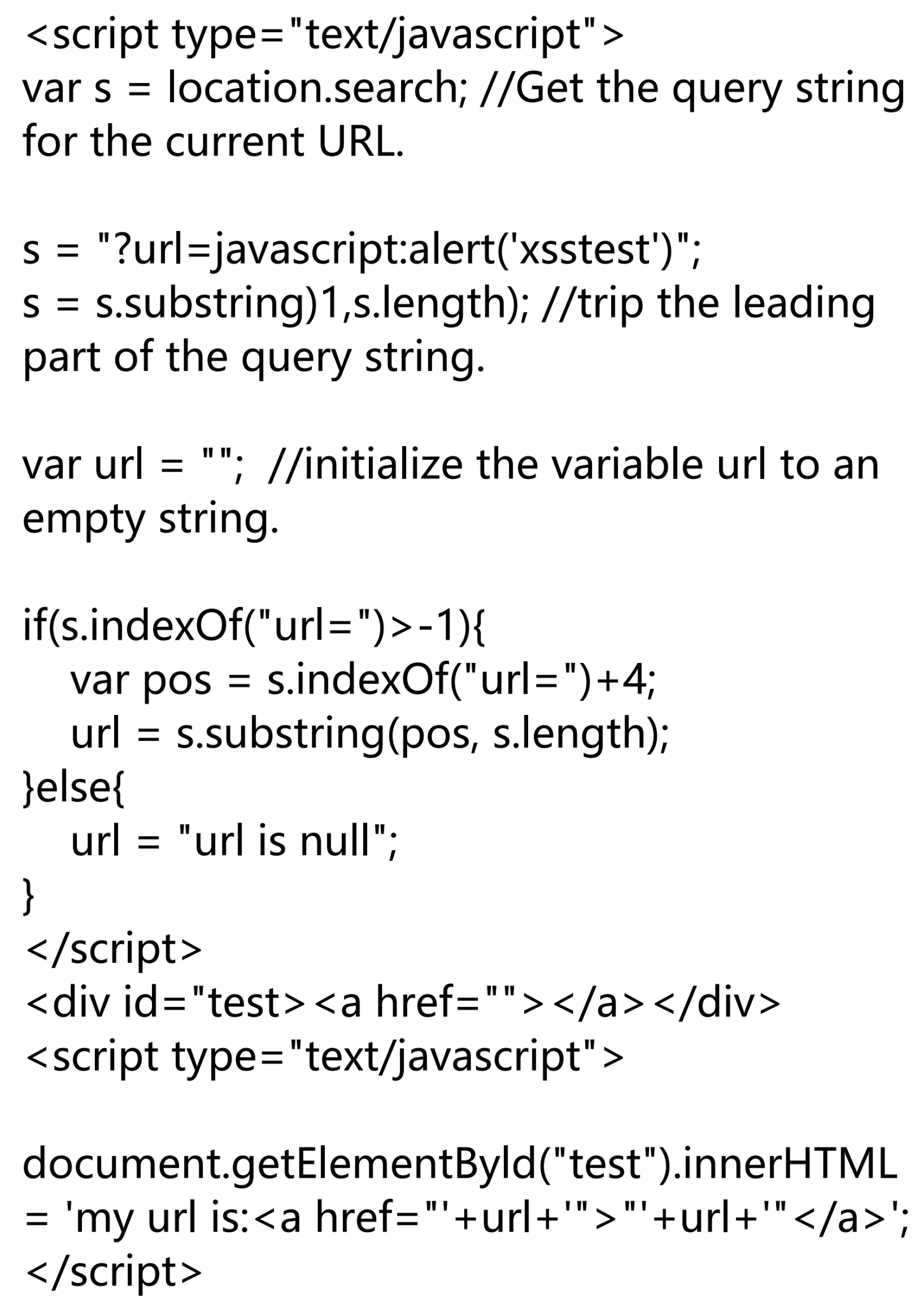
Figure 2. Web application with a DOM-Based XSS.
4. SQL Injection
SQL injection is a type of attack that targets databases specifically. General web applications utilize databases that are often more likely to be exploited by attackers than XSS vulnerabilities because of their involvement with data storage. Alert Logic Cloud Security recently stated that SQL injection accounted for 55% of the detected attacks [13]. The general test method for this vulnerability involves the construction of simple test code in the username and password input boxes, such as:
This method is often used on online login pages by attackers. Alternatively, vulnerabilities can be mined by adding &id = 1 and id = ‘1’ after the label in the URL bar. The existence of vulnerabilities of this type is conformed if no 404 or 403 warning is displayed and the new page’s content is identical to that of the old page. In addition, Boolean blind injection, timestamp injection, truncated injection and other methods can be used to determine the effectiveness of SQL injection on web applications.
5. LFI
LFI primarily affects web applications written in PHP [14]. When a file is imported through a PHP function, the incoming file name or path is not properly processed. Checking or operating unintended files may lead to accidental file leakage or even malicious code injection. The vulnerable functions in PHP are usually include(), require(), include_once(), and require_once(). In JSP/servlet, they are ava.io.File() and java.io.FileReader() functions instead.
6. LDAP
LDAP is a lightweight online directory access protocol; its information storage form is depicted in Figure 3. The usage of web applications has increased manifold recently, and the resources and data of these applications are distributed and stored in directories. Usually, different applications involve directories, called proprietary directories, dedicated to their related data. An increase in the number of proprietary directories leads to the formation of information islands (i.e., information systems that cannot interoperate or coordinate work with each other). This complicates the sharing and management of systems and resources. In this case, some web programs utilize LDAP to facilitate data query and processing, which may make them vulnerable to LDAP attacks [7][15]. LDAP injection is similar to SQL injection—parameters introduced by the user are used to generate LDAP queries, which can be divided into ‘and’ injection and ‘or’ injection, as depicted below:
If a server opens any of the ports 389, 636, or 3269, it is likely to exhibit LDAP vulnerability. An attacker can exploit this vulnerability to perform blind LDAP injection on test directory attributes and obtain document information [16].

Figure 3. LDAP information tree.
References
- Marashdih, A.W.; Zaaba, Z.F.; Suwais, K. Cross Site Scripting: Investigations in PHP Web Application. In Proceedings of the 2018 International Conference on Promising Electronic Technologies (ICPET), Deir El-Balah, Palestine, 3–4 October 2018; pp. 25–30.
- Tushnytskyy, R.; Levus, Y.; Branec, I. Computer language benchmarks tool. In Proceedings of the VIIth International Conference on Perspective Technologies and Methods in MEMS Design, Polyana, Ukraine, 11–14 May 2011; pp. 211–212.
- Seixas, N.; Fonseca, J.; Vieira, M.; Madeira, H. Looking at web security vulnerabilities from the programming language perspective: A field study. In Proceedings of the 2009 20th International Symposium on Software Reliability Engineering, Mysuru, India, 16–19 November 2009; pp. 129–135.
- Wang, Y.; Sang, Y. An Empirical Study of Security Risks of PHP Open-Source Software. Int. J. Softw. Eng. Knowl. Eng. 2014, 24, 1073–1086.
- Choudhary, S.; Kaur, P. A Study of Security Vulnerabilities on Java Web Application Frameworks. In Proceedings of the 2018 3rd International Conference on Computing Sciences (ICCS), Wuxi, China, 11–13 June 2018; pp. 167–171.
- Weinberger, J.; Saxena, P.; Akhawe, D.; Finifter, M.; Shin, R.; Song, D. A systematic analysis of XSS sanitization in web application frameworks. In Proceedings of the 16th European Symposium on Research in Computer Security, Leuven, Belgium, 12–14 September 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 150–171.
- Shahriar, H.; Haddad, H.; Bulusu, P. OCL Fault Injection-Based Detection of LDAP Query Injection Vulnerabilities. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; pp. 455–460.
- Helmiawan, M.A.; Firmansyah, E.; Fadil, I.; Sofivan, Y.; Mahardika, F.; Guntara, A. Analysis of web security using open web application security project. In Proceedings of the 2020 8th International Conference on Cyber and IT Service Management (CITSM), Pangkal, Indonesia, 23–24 October 2020; pp. 1–5.
- Talib, N.A.A.; Doh, K.G. Assessment of Dynamic Open-source Cross-site Scripting Filters for Web Application. KSII Trans. Internet Inf. Syst. (TIIS) 2021, 15, 3750–3770.
- Likaj, X.; Khodayari, S.; Pellegrino, G. Where We Stand (or Fall): An Analysis of CSRF Defenses in Web Frameworks. In Proceedings of the 24th International Symposium on Research in Attacks, Intrusions and Defenses, San Sebastian, Spain, 6–8 October 2021; pp. 370–385.
- Ku Mohd Sahidi, K.A.H.H.B.C.; Ariffin, M.A.M.; Ramli, M.I.; Kasiran, Z. Local File Inclusion Vulnerability Scanner with Tor Proxy. In Proceedings of the 2021 IEEE International Conference on Signal and Image Processing Applications (ICSIPA), Kuala Terengganu, Malaysia, 13–15 September 2021; pp. 244–249.
- Cui, Y.; Cui, J.; Hu, J. A survey on xss attack detection and prevention in web applications. In Proceedings of the 2020 12th International Conference on Machine Learning and Computing, Shenzhen, China, 15–17 February 2020; pp. 443–449.
- Rai, A.; Miraz, M.M.I.; Das, D.; Kaur, H. SQL Injection: Classification and Pre- vention. In Proceedings of the 2021 2nd International Conference on Intelligent Engineering and Management (ICIEM), London, UK, 28–30 April 2021; pp. 367–372.
- Available online: https://owasp.org/www-community/vulnerabilities/PHP_File_Inclusion (accessed on 10 April 2023).
- Alonso, C.; Bordón, R.; Beltrán, A. LDAP Injection & Blind LDAP Injection in Web Applications. Available online: https://www.blackhat.com/presentations/bh-europe-08/Alonso-Parada/Whitepaper/bh-eu-08-alonso-parada-WP.pdf (accessed on 10 April 2023).
- Vazquez, A. OpenLDAP Replication. In Practical LPIC-3 300; Apress: Berkeley, CA, USA, 2019; pp. 157–180.
More
Information
Subjects:
Others
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
676
Revisions:
2 times
(View History)
Update Date:
24 Aug 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




