
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Aristeidis Karras | -- | 1669 | 2023-08-17 14:41:37 | | | |
| 2 | Wendy Huang | Meta information modification | 1669 | 2023-08-18 05:43:34 | | |
Video Upload Options
Autonomous vehicles (AVs), defined as vehicles capable of navigation and decision-making independent of human intervention, represent a revolutionary advancement in transportation technology. These vehicles operate by synthesizing an array of sophisticated technologies, including sensors, cameras, GPS, radar, light imaging detection and ranging (LiDAR), and advanced computing systems. These components work in concert to accurately perceive the vehicle’s environment, ensuring the capacity to make optimal decisions in real time. At the heart of AV functionality lies the ability to facilitate intercommunication between vehicles and with critical road infrastructure—a characteristic that, while central to their efficacy, also renders them susceptible to cyber threats. The potential infiltration of these communication channels poses a severe threat, enabling the possibility of personal information theft or the introduction of malicious software that could compromise vehicle safety.
1. Introduction
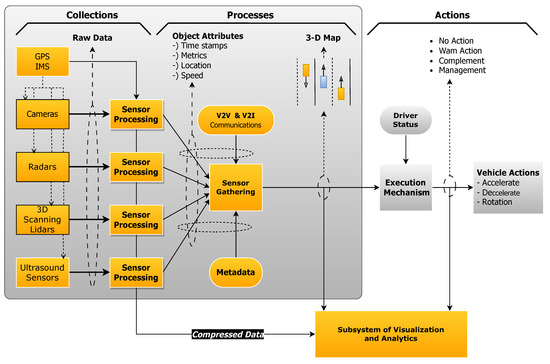
-
Key fob hacking: Remote vehicle access and ignition made possible by key fob technology can be compromised. By using devices to strengthen the signal transmitted by a vehicle’s key transponder, hackers can gain unauthorized entry and even remotely start the vehicle [3].
-
Control area network (CAN) bus attacks: The CAN bus, which operates as the electrical network that connects the various electronic control units (ECUs) within a vehicle, is an attractive target for hackers. By exploiting vulnerabilities in the CAN bus, hackers can take control of fundamental vehicle functions such as braking and steering [3].
-
Entertainment system hacking: Given its connection to the CAN bus, a vehicle’s entertainment system can provide a back door for hackers, which, once breached, could potentially grant a hacker full control over the vehicle’s systems [3].
-
Adversarial machine learning techniques: Autonomous vehicles rely heavily on machine learning algorithms to interpret sensor data and make operational decisions. By employing adversarial machine learning techniques, such as evasion or poisoning attacks, hackers can manipulate sensor data, causing the vehicle to make faulty and potentially hazardous decisions [4].
-
User data theft: Considering the plethora of user data stored in autonomous vehicles, these vehicles become prime targets for cyber criminals. A hacked vehicle can lead to significant privacy violations and impose safety risks to the driver and others on the road.
-
Remote vehicle hijacking: In a potentially dangerous scenario, hackers might gain remote control of a self-driving car, causing passengers to experience difficulty.
-
Denial-of-service (DoS) attacks: The launching of DoS attacks against the vehicle’s systems could lead to system shutdown or failure.
2. Hardware Vulnerabilities: Onboard Diagnostic Port (OBD)
3. Hardware Vulnerabilities: Engine Control Unit (ECU)
References
- Can Driverless Vehicles Be Hacked? Available online: https://www.hlmlawfirm.com/blog/can-driverless-vehicles-be-hacked/ (accessed on 19 July 2023).
- HackerNoon. Available online: https://hackernoon.com/how-to-hack-self-driving-cars-vulnerabilities-in-autonomous-vehicles-jh3r37cz (accessed on 19 July 2023).
- Algarni, A.; Thayananthan, V. Autonomous Vehicles: The Cybersecurity Vulnerabilities and Countermeasures for Big Data Communication. Symmetry 2022, 14, 2494.
- Kumar, K.N.; Vishnu, C.; Mitra, R.; Mohan, C.K. Black-box adversarial attacks in autonomous vehicle technology. In Proceedings of the 2020 IEEE Applied Imagery Pattern Recognition Workshop (AIPR), Washington, DC, USA, 13–15 October 2020; pp. 1–7.
- Santa, J.; Bernal-Escobedo, L.; Sanchez-Iborra, R. On-board unit to connect personal mobility vehicles to the IoT. Procedia Comput. Sci. 2020, 175, 173–180.
- Chang, X.; Li, H.; Rong, J.; Huang, Z.; Chen, X.; Zhang, Y. Effects of on-board unit on driving behavior in connected vehicle traffic flow. J. Adv. Transp. 2019, 2019, 1–12.
- Zhang, B.; Wang, X.; Xie, R.; Li, C.; Zhang, H.; Jiang, F. A reputation mechanism based Deep Reinforcement Learning and blockchain to suppress selfish node attack motivation in Vehicular Ad-Hoc Network. Future Gener. Comput. Syst. 2023, 139, 17–28.
- Karmakar, G.; Chowdhury, A.; Das, R.; Kamruzzaman, J.; Islam, S. Assessing trust level of a driverless car using deep learning. IEEE Trans. Intell. Transp. Syst. 2021, 22, 4457–4466.
- Zhang, Y.; Ge, B.; Li, X.; Shi, B.; Li, B. Controlling a Car Through OBD Injection. In Proceedings of the 2016 IEEE 3rd International Conference on Cyber Security and Cloud Computing (CSCloud), Beijing, China, 25–27 June 2016; pp. 26–29.
- Yan, W. A two-year survey on security challenges in automotive threat landscape. In Proceedings of the 2015 International Conference on Connected Vehicles and Expo (ICCVE), Shenzhen, China, 19–23 October 2015; pp. 185–189.
- Yadav, A.; Bose, G.; Bhange, R.; Kapoor, K. Security, Vulnerability and Protection of Vehicular On-board Diagnostics. Int. J. Secur. Its Appl. 2016, 10, 405–422.
- Oka, D.K.; Larson, U.E. Conducting Forensic Investigations of Cyber Attacks on Automobile In-Vehicle Networks. Int. J. Digit. Crime Forensics 2009, 2, 28–41.
- Vallance, C. Car Hack Uses Digital-Radio Broadcasts to Seize Control. 22 July 2015. Available online: www.bbc.com/news/technology-33622298 (accessed on 23 July 2023).
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive experimental analyses of automotive attack surfaces. In Proceedings of the 20th USENIX Conference on Security, San Francisco, CA, USA, 8–12 August 2011.




