Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Hayat Mohammad Khan | -- | 2708 | 2023-01-05 14:01:46 | | | |
| 2 | Sirius Huang | Meta information modification | 2708 | 2023-01-08 17:13:20 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Khan, H.M.; Khan, A.; Khan, B.; Jeon, G. Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids. Encyclopedia. Available online: https://encyclopedia.pub/entry/39797 (accessed on 07 March 2026).
Khan HM, Khan A, Khan B, Jeon G. Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids. Encyclopedia. Available at: https://encyclopedia.pub/entry/39797. Accessed March 07, 2026.
Khan, Hayat Mohammad, Abid Khan, Basheir Khan, Gwanggil Jeon. "Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids" Encyclopedia, https://encyclopedia.pub/entry/39797 (accessed March 07, 2026).
Khan, H.M., Khan, A., Khan, B., & Jeon, G. (2023, January 05). Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids. In Encyclopedia. https://encyclopedia.pub/entry/39797
Khan, Hayat Mohammad, et al. "Fault-Tolerant Secure Data Aggregation Schemes in Smart Grids." Encyclopedia. Web. 05 January, 2023.
Copy Citation
Secure data aggregation is an important process that enables a smart meter to perform efficiently and accurately. However, the fault tolerance and privacy of the user data are the most serious concerns in this process.
Smart Grid
fault tolerance
differential privacy
privacy preserving
data aggregation
1. Introduction
The Smart Grid (SG) refers to the integration of power system engineering, communications, and information technology [1]. It offers the most robust, efficient, and trustworthy energy system. The smartness of the system provides the additional facility of peer-to-peer or bi-directional communication [2] and intelligently satisfies the energy demands in real-time with flawless transmission and distribution of electric energy from the suppliers to the home users. It enables the customers to view their current electricity usage through a web interface. In comparison to the traditional power grid, the SG has made power generation, transmission, and distribution to customers more robust, flexible, and effective through the integration of various technologies. Important components of the SG are the cloud control centre (CCC), gateway (GW)/fog node (FN), users (U), and smart meter (SM). SMs are installed at customer premises and submit their usage data through intermediate nodes (GW/FN) to the CCC in a secure manner. At the CCC, overall usage is calculated. At the SG level, numerous analytics relating to demand–response, forecasting, and load management are carried out based on consumption data. Figure 1 shows the high-level model of the SG.
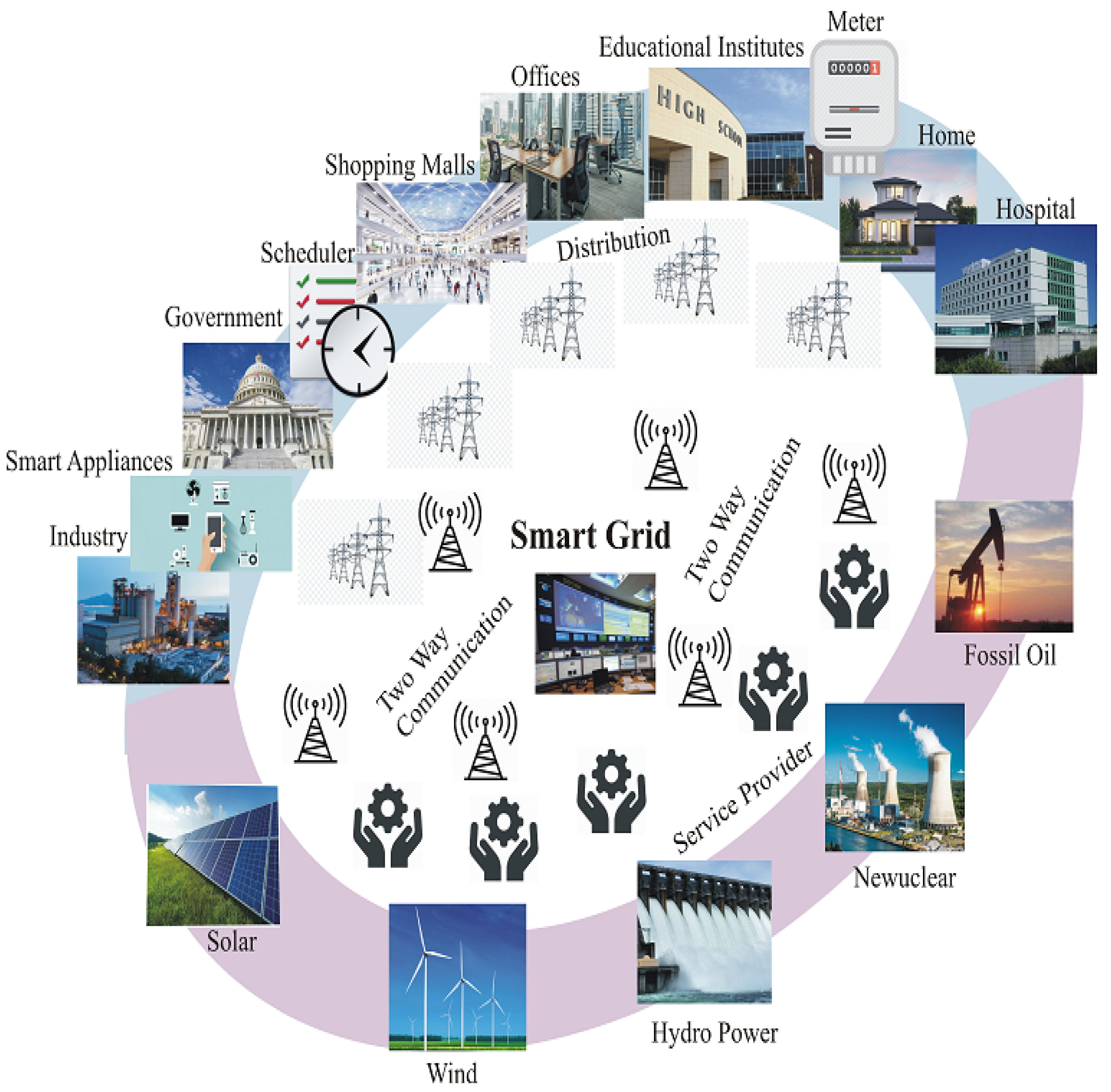
Figure 1. Model of a Smart Grid.
The SG’s physical infrastructure is vulnerable to a variety of cyber security attacks. Security incidents related to facility disturbances threaten the lives of citizens and even compromise national security [3]. Researchers have been studying various areas of the SG, such as the physical setup, communication technologies, legal issues, reliability, early diagnosis of failures and their recovery, demand–response management, data aggregation capability, cyber security, and customer privacy [3][4].
The two types of data collected by SG technologies are personally identifiable information and consumer-specific energy usage data. Submitting data at regular intervals in plaintext to the CCC results in privacy issues. Through secure data aggregation and by placing an intermediate gateway server (GW) between the SM and CCC, privacy and communication overhead can be reduced significantly [5]. During data aggregation, some SMs or GW/FN can drop or malfunction. If some SMs are malfunctioning or faulty and do not submit their data, this will introduce a delay in data aggregation activity, and subsequently, the CCC will not be able to calculate electricity usage; this will impact the SG operations with respect to demand–response and load management. In a fault-tolerant secure data aggregation (FTSDA) scheme, if there are some faulty SMs, this will not impact data aggregation activity [6].
Some of the existing SDA schemes achieve FT by using: (i) the addition of subtle strings [7], (ii) dummy text addition [8], (iii) the isolation of malfunctioning meters [9], (iv) future ciphertext [10], (v) the most recent reading stored at the FN level [11], and (vi) error detection through paring [12]. In Figure 2, FT achieved by various schemes during data collection in SG is presented.
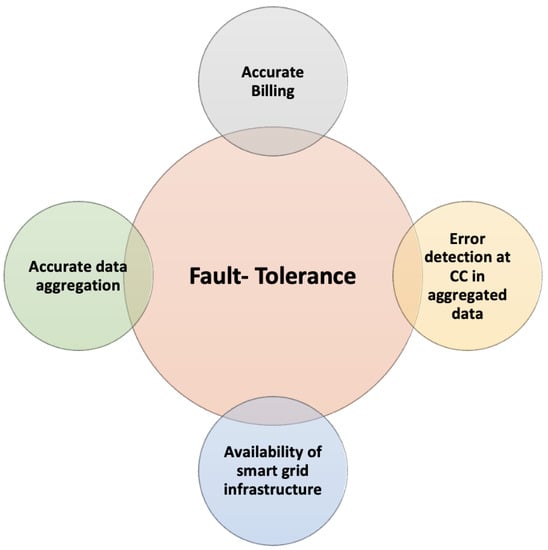
Figure 2. Fault tolerance in the Smart Grid.
2. Fault-Tolerant SDA Schemes in SGs
The FT schemes in SGs are divided into cryptographic and non-cryptographic categories. The crypto category is further divided into symmetric and asymmetric. The asymmetric category is further divided into lattice, homomorphic, and non-homomorphic schemes. The non-crypto schemes are divided into binary tree model, pairwise streaming, and coding theory schemes.
Cryptography Based FT SDA Schemes
The cryptographic schemes can be divided into symmetric and asymmetric schemes.
Symmetric Cryptography based FT SDA Schemes: Symmetric key cryptography, also known as private key cryptography, is the scheme in which a single, or master key, is used in the encryption and decryption processes. The transformation of plaintext to ciphertext utilizing the master key is known as encryption. In any case, changing ciphertext into plaintext is known as decryption, which is the reverse process of encryption. In symmetric cryptography, a single shared key needs to be kept secret at both ends to enable secure communication between a sender and receiver. Lu et al. [7] proposed a lightweight data aggregation scheme. The scheme’s most notable feature is that it supports secure aggregation with FT. A session key, AES encryption, and a Laplace distribution are used to achieve privacy-preserving SDA. The authors added subtle strings during the data collection phase to deal with the faulty SM scenario. Sun et al. [13] proposed a fault-tolerant pairwise private stream aggregation scheme. The limitation of their scheme is that a faulty meter can be paired with another faulty meter due to random pairing. In Chan et al.’s [9] secure aggregation scheme, faulty SMs are handled through a binary tree based architecture. Their scheme is also secure against differential privacy attacks and supports dynamic SM addition and removal. In Wu et al.’s [14] scheme, the authors proposed a novel key management scheme that combines the symmetric key technique and the elliptic curve public key technique. The agents receive the symmetric key for internal communication from trusted anchors. If one of the trusted anchors is faulty, agents can be assigned to other less-loaded trust anchors for session key generation. Won et al. [10] proposed a proactive fault-tolerant aggregation algorithm based on future ciphertexts. During data submission, every SM divides its ciphertext into the current ciphertext and the future ciphertext. Future ciphertexts must be stored to ensure FT during SDA. However, it requires more storage on the aggregator end. A fog-enabled data aggregation (PPFA) scheme was proposed by Li et al. [15]. FNs periodically gather and aggregate data from the corresponding SMs. The CCC aggregates the data gathered from all FNs. OTP is employed for encryption, while the PKC is configured for authentication. One disadvantage of the preceding approach is that keys of the same length as the plaintext must be created, as well as new keys each time. Furthermore, if any SMs fail, data aggregation will require an additional round of communication.
Asymmetric Cryptography based FT SDA Schemes: In asymmetric cryptography [16], two keys are used instead of a single key. It consists of a public key and a private key. The public key is available to everyone and serves only to encrypt data. The private key is only available to the key owner and is used to decrypt messages. Asymmetric cryptography provides several security features, such as message integrity, authentication, and non-repudiation. However, compared to symmetric cryptography, it is costly in terms of computation. Many schemes have been proposed based on asymmetric cryptography in the context of SDA in the SG. Asymmetric schemes can be divided into the subtypes homomorphic and non-homomorphic schemes.
Non-homomorphic schemes: Ni et al. [17] proposed a differentially private smart metering scheme (DiPrism) with FT and range-based filtering. Lifted-El Gamal encryption was used to aggregate SM data at the GW level. The range-based filtering method detects abnormal readings by comparing them to normal readings. All SMs’ data are required to decrypt the aggregated data at the CCC level. When there are faulty SMs, the CCC works with the GW to obtain the aggregation values for the faulty SMs. Their scheme is secure against false data injection attacks by using the zero-knowledge range proof. In Li et al.’s [6] scheme, authentication is provided through a BLS-based signature during data aggregation. If one of the collectors is out of service, the standby collector can complete the authentication process through digital signatures and the minimum spanning tree (MST) without any further additional setup or configuration. Their scheme is resistant to replay and denial-of-service attacks. The disadvantage of this scheme is that it requires many computational resources.
Secure multiparty computation-based schemes: Secure multiparty computation (SMPC) is a branch of cryptography that enables distributed parties to jointly compute a function using their own inputs without disclosing their outputs. With the intention of enabling distributed computation without the requirement for a reliable third party, the initial work on SMPC started in 1970. In the 1980s, Yao published his first paper on SMPC [18]. Since then, SMPC has made significant strides in both theory and application [19]. Thoma et al. [20] proposed the SMPC-based homomorphic encryption scheme on the basis of individual SM load management. The utility can execute real-time demand management with specific consumers using SMC and a well-designed power plan without knowing the true value of each user’s consumption data. Mustafa et al. [21] proposed an innovative solution based on SMPC that allows SG operators and suppliers to collect users’ electricity metering data securely and privately. SMPC helps all recipients receive data related to transmission, distribution, and fee collections. The SPMC-based Shamir secret scheme is implemented in C++, and the BGW protocol [22][23] is used to support homomorphic encryption. A fog-enabled secure multiparty computation (SMPC) aggregation scheme in the SG was presented by Hayat et al. [24]. The scheme is robust against the collusion and false data injection (FDI) attacks during metering data collection. A collusion attack is managed through Shamir’s enhanced secret scheme.
Homomorphic schemes: Homomorphic encryption (HE) is a method for performing operations on encrypted data while maintaining the confidentiality and integrity of the underlying data. There are two types of homomorphic encryption schemes: the fog-based and non-fog-based. Partial homomorphic encryption (PHE), somewhat homomorphic encryption (SWHE), and fully homomorphic encryption (FHE) schemes [25] are the three types of homomorphic encryption schemes.
Partial homomorphic encryption (PHE) schemes: The Paillier [8], Boneh–Goh–Nissim [26][27], and El Gamal encryption schemes are classical and state-of-the-art homomorphic encryption (HE) algorithms used in SG data aggregation. Bilinear mapping [6][14] is also commonly used to generate and exchange keys for SG entities and during data aggregation.
Paillier encryption scheme: Chen et al. [8] proposed a privacy-preserving data aggregation scheme with FT in the SG. Their scheme supports customer data protections against an adversary that has the capability to compromise servers at the CCC. SM data are encrypted through Paillier encryption. For missing SMs, decryption activity can be completed by adjusting the default values provided by the TA. Zhitao et al. [28] proposed a fault-tolerant data aggregation scheme based on secret sharing. In their scheme, all SMs are split into different groups. SM IDs are masked through the anonymization process. Privacy is achieved through Paillier encryption by splitting secrets among SMs in a particular group. The malfunctioning SM is identified by comparing the group hash table value to the values of other groups. FT is achieved through a substitution mechanism. The proposed scheme is secure against collusion attacks. Jawurek et al. [16] proposed a protocol to calculate diverse statistics on SMs’ data that supports FT and differential privacy. In the proposed scheme, the GW and TA are considered non-trustworthy. Paillier homomorphic encryption is used to encrypt SM data, and symmetric geometric distribution is used to ensure privacy. The scheme allows the aggregator to compute statistics based on available SMs’ data, even if some SMs are faulty. Liu et al.’s [29] scheme supports statistical functions on encrypted data for IoT devices. The scheme is secure and fault-tolerant. FT is achieved through future data buffering mechanism.
El Gamal encryption scheme: Ni et al. [17] proposed a data aggregation scheme (DiPrism) for the SG that supports differential privacy, FT, and range-based filtering for AMI (advanced metering infrastructure). The metering data are encrypted through EI Gamal homomorphic encryption. Every SM includes a zero-knowledge (KW) proof during the encryption stage to ensure that readings are within a pre-defined range. Abnormal readings are filtered out based on the zero-knowledge proof. The Laplace distribution is used to add noise to achieve differential privacy.
Somewhat homomorphic encryption (SWHE): Somewhat homomorphic encryption (SWHE) is a homomorphic public key infrastructure (PKI). SWHE was the first of its kind to allow both multiplication and addition operations on encrypted data. Bao et al. [30] proposed a privacy-preserving data aggregation scheme with differential privacy and FT. Their scheme supports data aggregation activity in the presence of faulty SMs. The authors used the Boneh–Goh–Nissim (BGN) cryptosystem [31] to encrypt SM data and introduce noise via a Laplace distribution. To handle faulty SMs, a random value is added to the SM data. On the basis of this random value, the decryption activity is completed for working SMs. The scheme provides protection against the DP and eavesdropping attacks. Fu et al. [32] proposed a privacy-preserving and secure multidimensional aggregation scheme for the SG. Mykletun homomorphic encryption and the Boneh signature system are used in the proposed scheme to achieve privacy, integrity, authentication, and the identification of accidental errors. If some SMs have not submitted their data due to selective forwarding attacks or random errors, the GW will notify the CCC and TA of the list of faulty SMs. The CCC will calculate the hash sum of the faulty SMs and recover their data. Hayat et al. [11] presented a fog-enabled privacy-preserving SDA scheme with FT. The scheme provides protection against the FDI and replay attacks and ensures the confidentiality and authenticity of customer data. Techniques such as the modified BGN cryptosystem, homomorphic aggregation, and the elliptic curve digital signature algorithm (ECDSA) authentication mechanism are used to reduce the computational costs and communication overhead. Furthermore, the proposed scheme allows data aggregation to continue in the presence of faulty SMs.
Lattice-based schemes: Lattice-based cryptography is the alternative to the RSA and elliptic curve cryptography (ECC) public-key schemes. In Nth-degree truncated polynomial ring unit (NTRU) schemes, the encryption and decryption processes are simply polynomial arithmetic operations. Therefore, NTRU’s implementation is efficient as compared to other asymmetric schemes. Asmaa et al. [33] proposed a lattice-based homomorphic privacy-preserving scheme in the SG. In this scheme, all appliances installed in one particular home aggregate their data and submit them to the installed SM. The SM applies NTRU-based encryption to the aggregated data and submits them to the CCC. The proposed scheme supports customer privacy, integrity, and confidentiality. Furthermore, it is lightweight in terms of computational cost and communication overhead.
Table 1 gives an overview of existing FT aggregation schemes for the SG.
Table 1. Overview of fault-tolerance schemes in smart grids.
| Technique Used | Attack Model | System Model | Strength | Weakness |
|---|---|---|---|---|
| Diluted geometric distribution, quad tree, key management centre (KMC) [34] | Malware, data pollution attacks | SM, CC, GW | Privacy, DP, FT, low compu. and comm. cost | Less effective, inefficient, and unreliable |
| Needham–Schroeder authentication protocol [14] | Replay, DDoS, MITM attack | SM, TA, GW | Scalability, FT | Unreliable, high comm. overhead and compu. cost |
| BLS signature aggregation, batch verification, signature amortization [6] | Replay, DDoS attack | SM, TTP, CA, GW | FT, availability, low comm. and compu. cost. | Less effective, inefficient, and unreliable |
| Paillier homomorphic cryptosystem, distributed key-managing authority [16] | Aggregator obliviousness, malicious data consumer | SM, aggregator | Exchangeable statistical functions, group key management, DP, FT | Only group signature verification facility |
| Binary tree, block aggregation, geometric distribution [9] | Colluding, data pollution attack | SM, aggregator, TA | FT, no peer-to-peer comm., dynamic leaver/joiner | Extra communication if tree expanded |
| Pairwise private stream aggregation scheme [13] | Eavesdrop, privacy-divulging attack | KMC, SM, CCC | FT, privacy | Extra comm. overhead |
| Coding theory, spread spectrum communication over CDMA [35] | DP, MITM, inference attack | SM, TA, GW, CDMA, CCC | Low comm. and compu. cost, high performance | Extra storage, unreliable |
| Homomorphic encryption, geometric distribution [36] | Privacy divulging, data attack | CCC, TA, GW, SM, CH | FT, DP privacy, low compu. and comm. cost | Slow verification process, configuration and maintenance issues |
| Paillier-based homomorphic encryption [12] | DP, malware, privacy divulging, data alteration attack | CC, TA, GW, KMC, SMs | Decentralized, FT, DP | High storage, comm., and compu cost |
| Paillier homomorphic encryption [8] | Data mining, DDoS, replay attack | SM, GW, CCC | Privacy, FT, comp. efficiency, DP | Less efficient, high compu. cost |
| BGN, Diffie–Hellmann key exchange protocol [30] | Internal, external, and differential attack | CC, TA, GW, SM | Privacy, FT, DP, low error, less comp. cost | High storage cost, configuration and maintenance issue |
| SMPC, homomorphic encryption [37] | MITM, data mining and differential attack | One aggregator model | Privacy-preserving | No secure channel, high comp. and compu. cost |
| HE signature scheme, El Gamal cryptosystem [38] | Chosen message attacks | CCC, SMs, GW | Less comm. and comp. cost, privacy, FT | Less efficient, high storage cost, unreliable |
| Modular addition symmetric key, digital certificates [39] | Curious aggregator, chosen message and chosen ciphertext attack | SM, Aggregator | Scalability, FT, DP, high accuracy | High bandwidth, extra storage requirement |
| El Gamal homomorphic encryption, 0-knowledge range proof, PKI cert [17] | DDoS, n data mining attacks | CCC, n GW, n SM, n TA | Privacy, n DP, n FT, n range-based filtering | Comm. overhead, compu. cost |
Figure 3 shows the proposed taxonomy of fault-tolerant SDA schemes in the SG.

Figure 3. Taxonomy of FTSDA schemes in smart grids.
References
- Farhangi, H. The path of the Smart Grid. IEEE Power Energy Mag. 2009, 8, 18–28.
- Lu, R.; Liang, X.; Li, X.; Lin, X.; Shen, X. EPPA: An efficient and privacy-preserving aggregation scheme for secure Smart Grid communications. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1621–1631.
- Li, X.; Liang, X.; Lu, R.; Shen, X.; Lin, X.; Zhu, H. Securing Smart Grid: Cyber attacks, countermeasures, and challenges. IEEE Commun. Mag. 2012, 50, 38–45.
- Wang, W.; Lu, Z. Cyber security in the Smart Grid: Survey and challenges. Comput. Netw. 2013, 57, 1344–1371.
- Ferrag, M.A.; Maglaras, L.A.; Janicke, H.; Jiang, J.; Shu, L. A systematic review of data protection and privacy preservation schemes for Smart Grid communications. Sustain. Cities Soc. 2018, 38, 806–835.
- Li, D.; Aung, Z.; Williams, J.R.; Sanchez, A. Efficient authentication scheme for data aggregation in Smart Grid with fault tolerance and fault diagnosis. In Proceedings of the 2012 IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 16–20 January 2012; pp. 1–8.
- Bao, H.; Lu, R. A lightweight data aggregation scheme achieving privacy preservation and data integrity with differential privacy and fault tolerance. Peer-to-Peer Netw. Appl. 2017, 10, 106–121.
- Chen, L.; Lu, R.; Cao, Z. PDAFT: A privacy-preserving data aggregation scheme with fault tolerance for Smart Grid communications. Peer-to-Peer Netw. Appl. 2015, 8, 1122–1132.
- Chan, T.H.H.; Shi, E.; Song, D. Privacy-preserving stream aggregation with fault tolerance. In Proceedings of the International Conference on Financial Cryptography and Data Security; Springer: Cham, Switzerland, 2012; pp. 200–214.
- Won, J.; Ma, C.Y.; Yau, D.K.; Rao, N.S. Privacy-assured aggregation protocol for smart metering: A proactive fault-tolerant approach. IEEE/ACM Trans. Netw. 2015, 24, 1661–1674.
- Khan, H.M.; Khan, A.; Jabeen, F.; Rahman, A.U. Privacy preserving data aggregation with fault tolerance in fog-enabled Smart Grids. Sustain. Cities Soc. 2021, 64, 102522.
- Shi, Z.; Sun, R.; Lu, R.; Chen, L.; Chen, J.; Shen, X.S. Diverse grouping-based aggregation protocol with error detection for Smart Grid communications. IEEE Trans. Smart Grid 2015, 6, 2856–2868.
- Sun, R.; Shi, Z.; Lu, R.; Lu, M.; Shen, X. APED: An efficient aggregation protocol with error detection for Smart Grid communications. In Proceedings of the 2013 IEEE Global Communications Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013; pp. 432–437.
- Wu, D.; Zhou, C. Fault-tolerant and scalable key management for Smart Grid. IEEE Trans. Smart Grid 2011, 2, 375–381.
- Lyu, L.; Nandakumar, K.; Rubinstein, B.; Jin, J.; Bedo, J.; Palaniswami, M. PPFA: Privacy preserving fog-enabled aggregation in Smart Grid. IEEE Trans. Ind. Inform. 2018, 14, 3733–3744.
- Jawurek, M.; Kerschbaum, F. Fault-tolerant privacy-preserving statistics. In Proceedings of the International Symposium on Privacy Enhancing Technologies Symposium; Springer: Cham, Switzerland, 2012; pp. 221–238.
- Ni, J.; Zhang, K.; Alharbi, K.; Lin, X.; Zhang, N.; Shen, X.S. Differentially private smart metering with fault tolerance and range-based filtering. IEEE Trans. Smart Grid 2017, 8, 2483–2493.
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science (SFCS 1982), Chicago, IL, USA, 3–5 November 1982; pp. 160–164.
- Zhao, C.; Zhao, S.; Zhao, M.; Chen, Z.; Gao, C.Z.; Li, H.; Tan, Y.a. Secure multiparty computation: Theory, practice and applications. Inf. Sci. 2019, 476, 357–372.
- Thoma, C.; Cui, T.; Franchetti, F. Secure multiparty computation based privacy preserving smart metering system. In Proceedings of the 2012 North American Power Symposium (NAPS), Champaign, IL, USA, 9–11 September 2012; pp. 1–6.
- Mustafa, M.A.; Cleemput, S.; Aly, A.; Abidin, A. An MPC-based protocol for secure and privacy-preserving smart metering. In Proceedings of the 2017 IEEE PES Innovative Smart Grid Technologies Conference Europe (ISGT-Europe), Torino, Italy, 26–29 September 2017; pp. 1–6.
- Ben-Or, M.; Goldwasser, S.; Wigderson, A. Completeness theorems for non-cryptographic fault-tolerant distributed computation. In Providing Sound Foundations for Cryptography: On the Work of Shafi Goldwasser and Silvio Micali; ACM: New York, NY, USA, 2019; pp. 351–371.
- Mustafa, M.A.; Cleemput, S.; Aly, A.; Abidin, A. A secure and privacy-preserving protocol for smart metering operational data collection. IEEE Trans. Smart Grid 2019, 10, 6481–6490.
- Khan, H.M.; Khan, A.; Jabeen, F.; Anjum, A.; Jeon, G. Fog-enabled secure multiparty computation based aggregation scheme in Smart Grid. Comput. Electr. Eng. 2021, 94, 107358.
- Tonyali, S.; Akkaya, K.; Saputro, N.; Uluagac, A.S.; Nojoumian, M. Privacy-preserving protocols for secure and reliable data aggregation in IoT-enabled smart metering systems. Future Gener. Comput. Syst. 2018, 78, 547–557.
- Sridhar, S.; Hahn, A.; Govindarasu, M. Cyber–physical system security for the electric power grid. Proc. IEEE 2011, 100, 210–224.
- Ács, G.; Castelluccia, C. I have a dream!(differentially private smart metering). In Proceedings of the International Workshop on Information Hiding; Springer: Cham, Switzerland, 2011; pp. 118–132.
- Guan, Z.; Si, G.; Du, X.; Liu, P. Protecting User Privacy Based on Secret Sharing with Error Tolerance for Big Data in Smart Grid. arXiv 2018, arXiv:1811.06918.
- Liu, H.; Chen, J.; Lin, L.; Ye, A.; Huang, C. An efficient and privacy-preserving data aggregation scheme supporting arbitrary statistical functions in IoT. China Commun. 2022, 19, 91–104.
- Bao, H.; Lu, R. A new differentially private data aggregation with fault tolerance for Smart Grid communications. IEEE Internet Things J. 2015, 2, 248–258.
- Boneh, D.; Goh, E.J.; Nissim, K. Evaluating 2-DNF formulas on ciphertexts. In Proceedings of the Theory of Cryptography Conference; Springer: Cham, Switzerland, 2005; pp. 325–341.
- Fu, S.; Ma, J.; Li, H.; Jiang, Q. A robust and privacy-preserving aggregation scheme for secure smart grid communications in digital communities. Secur. Commun. Netw. 2016, 9, 2779–2788.
- Abdallah, A.; Shen, X.S. A lightweight lattice-based homomorphic privacy-preserving data aggregation scheme for Smart Grid. IEEE Trans. Smart Grid 2016, 9, 396–405.
- Lu, M.; Shi, Z.; Lu, R.; Sun, R.; Shen, X.S. PPPA: A practical privacy-preserving aggregation scheme for smart grid communications. In Proceedings of the 2013 IEEE/CIC International Conference on Communications in China (ICCC), Xi’an, China, 12–14 August 2013; pp. 692–697.
- Alamatsaz, N.; Boustani, A.; Jadliwala, M.; Namboodiri, V. Agsec: Secure and efficient cdma-based aggregation for smart metering systems. In Proceedings of the 2014 IEEE 11th Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2014; pp. 489–494.
- Bao, H.; Lu, R. Ddpft: Secure data aggregation scheme with differential privacy and fault tolerance. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 7240–7245.
- Jung, T.; Li, X.Y.; Wan, M. Collusion-tolerable privacy-preserving sum and product calculation without secure channel. IEEE Trans. Dependable Secur. Comput. 2014, 12, 45–57.
- Won, J.; Ma, C.Y.; Yau, D.K.; Rao, N.S. Proactive fault-tolerant aggregation protocol for privacy-assured smart metering. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 2804–2812.
- Shi, R.; Chow, R.; Chan, T.H.H. Privacy-Preserving Aggregation of Time-Series Data. European Patent Office EP2485430B1, 14 September 2016.
More
Information
Subjects:
Computer Science, Software Engineering
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
810
Revisions:
2 times
(View History)
Update Date:
08 Jan 2023
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No





