You're using an outdated browser. Please upgrade to a modern browser for the best experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Abdelkader Ouda | -- | 2525 | 2022-12-22 16:25:46 | | | |
| 2 | Vivi Li | -50 word(s) | 2475 | 2022-12-23 04:19:29 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Voege, P.; Sulayman, I.I.M.A.; Ouda, A. Smart Chatbot for User Authentication. Encyclopedia. Available online: https://encyclopedia.pub/entry/39109 (accessed on 26 December 2025).
Voege P, Sulayman IIMA, Ouda A. Smart Chatbot for User Authentication. Encyclopedia. Available at: https://encyclopedia.pub/entry/39109. Accessed December 26, 2025.
Voege, Peter, Iman I. M. Abu Sulayman, Abdelkader Ouda. "Smart Chatbot for User Authentication" Encyclopedia, https://encyclopedia.pub/entry/39109 (accessed December 26, 2025).
Voege, P., Sulayman, I.I.M.A., & Ouda, A. (2022, December 22). Smart Chatbot for User Authentication. In Encyclopedia. https://encyclopedia.pub/entry/39109
Voege, Peter, et al. "Smart Chatbot for User Authentication." Encyclopedia. Web. 22 December, 2022.
Copy Citation
Despite being the most widely used authentication mechanism, password-based authentication is not very secure, being easily guessed or brute-forced. To address this, many systems which especially value security adopt Multi-Factor Authentication (MFA), in which multiple different authentication mechanisms are used concurrently. JitHDA (Just-in-time human dynamics based authentication engine) is a new authentication mechanism which can add another option to MFA capabilities. JitHDA observes human behaviour and human dynamics to gather up to date information on the user from which authentication questions can be dynamically generated.
machine learning
authentication
natural language understanding
big data
chatbots
1. Introduction
User authentication is a vital component of daily operation of the modern world. Many applications and institutions rely on complete security for their users’ accounts, and in a digital environment where an access request can come from any location at any time regardless of authenticity, it is imperative to have robust authentication technology.
Authentication techniques can be divided into four different categories. You can authenticate someone based on something they know, something they have, something they are, and something they do. Authentication based on something you know takes the shape of systems such as passwords and PIN numbers. Authentication based on something you have takes the shape of systems such as keys or ID cards. Authentication based on something you are takes the shape of biometrics such as fingerprint or iris scans. Authentication based on something you do takes the shape of systems such as analysing a user’s typing habits.
‘Something you know’ authentication is very convenient and accessible, as the authentication merely requires inputting the information you have stored into your head, which can be completed in seconds on almost any authentication medium. However, it is also very insecure, as it is easy for the information to leak and when that happens any bad actor with the information is able to impersonate you. ‘Something you have’ authentication is only moderately convenient and accessible, as you must have the object in question available to you if you want to perform authentication, but is somewhat more secure than ‘something you know’ authentication because there is only one copy of the object to misplace and it cannot be taken without your notice. ‘Something you are’ authentication is highly secure, as it is difficult to fake biometric scans, but is comparatively inconvenient and inaccessible as you generally need specialized hardware present to perform the biometric scan. ‘Something you do’ authentication is a new form of authentication that operates by using user behavioural patterns, which can be very difficult to fake [1]. Typing rhythm and voice patterns are examples of the kind of user behaviour that qualifies for ‘something you do’ authentication, as they are unique to each user and difficult to impersonate [2].
None of these techniques are perfect. There are a great many considerations that a successful authentication system must perform well on [3], and in any given context researchers must choose one based on its situational advantages and disadvantages as there is no universally ideal authentication system. The most common method by far is ‘something you know’ authentication, which faces a continual struggle to maintain strong security without compromising accessibility [4]. To accomplish this, researchers propose a synthesis of ‘something you do’ and ‘something you know’ authentication achieved by analysing a user’s behaviour in their life activities and then questioning them on said activities. This behaviour-driven authentication system applies the security of ‘something you do’ authentication to the accessibility of ‘something you know’ authentication to create a strong, convenient method of authentication that anyone can make use of.
This system, which researchers call Autonomous Inquiry-based Authentication Chatbot (AIAC), will be a chatbot interacting with the user which continuously generates new questions based off of recent data, such that information used for authentication is quickly rendered useless for exploitation by bad actors, even if they do learn what it is. As a result, relying on ‘something you know’ authentication will not carry the risk that bad actors will acquire the user’s authentication information and impersonate them, thus making it much more secure as an authentication strategy.
Ouda et al. [5] has developed a new authentication framework based on “something you do” authentication principles and leveraging Big Data analytics to create dynamic and personalized authentication challenges. This framework is made up of three core components, as shown in Figure 1, each developed separately from different perspectives.
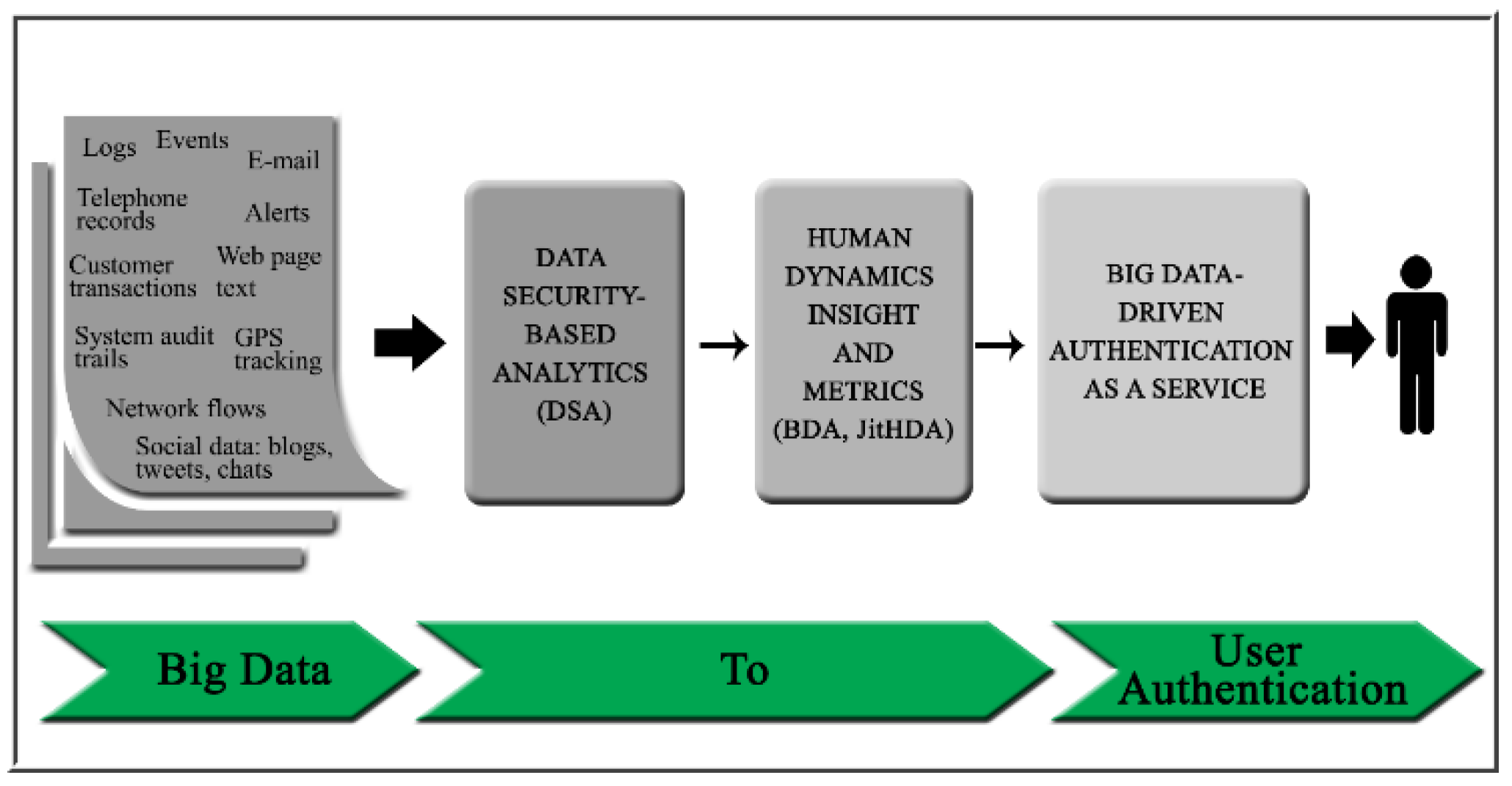
Figure 1. The components of Dr. Ouda’s authentication framework [5].
The first component, known as Data Security-based Analystics (DSA), describes ways to leverage Big Data analytics to form accurate up-to-date models of user behaviour. The second component, known as Big Data-driven Authentication tool (BDA), identifies patterns in DSA models and then uses said patterns to detect anomalous activity from the user and assemble a security profile about the user. The third component, known as Just-in-time Human Dynamics based Authentication engine (JitHDA), uses the user profiles to dynamically create secure authentication questions in real-time which derive from the user’s recent behaviour [6].
When all of these components are used in sequence, the complete authentication framework is formed, creating a novel ‘something you do’-based method of authentication.
The goal of this entry is to present a module that achieves that synthesis for the purposes of implementing JitHDA [5]. JitHDA is an authentication chatbot that focuses on forming authentication challenges just-in-time in order to remove the increasing temporal risk of static authentication information and on constructing the authentication challenges from observed human dynamics. JitHDA is exactly the synthesis of ‘something you do’ and ‘something you know’ authentication that researchers seek to make possible.
A fully implemented JitHDA would have the following qualities: (i) The expected answer should be based on a recent action that the user has taken. (ii) The question created should be randomly chosen from a list of possible questions. (iii) Questions should not be repeated. The complete authentication framework is composed of two modules: the location of anomalous events from recent user actions, and the construction of authentication challenges from the located anomalous events. JitHDA describes the latter module, and AIAC is designed to implement JitHDA.
2. Related Work on Smart Chatbot for User Authentication
To understand the relevance of AIAC, researchers must look at the other works in this domain to see how researchers' contribution compares to what they have accomplished, and what overlap in purpose can be found.
B. Liu et al. [7] analyses user statements to build up a user profile that helps chatbots personalize interaction with the user. Drawing on historical context, a two-branch neural network is used to compare the model of the user both with the provided user post and a candidate response in order to determine the suitability of the candidate response, with the results updating the user model for future conversational fine-tuning. This is relevant to JitHDA’s goal of personalized chatbot sessions with the user, but approaches that concept by dynamically integrating user posts in real-time instead of creating personalized profiles of the user to construct sessions from.
C. Kao et al. [8] creates a model for chatbots to display emotions in response to the user behaviour. It includes a mechanism to analyse user input and determine the emotions present in the sentences, and uses that to determine a suitable output emotion to affect the output text. This paper is also relevant to JitHDA’s goal of personalized chatbot sessions with the user, but accomplishes it from real-time use of user input instead of pre-assembled user information.
F. Patel et al. [9] seeks to determine if a user is feeling stressed or depressed by analysing chat text from them, for the purposes of identifying how the chatbot can help the user maintain a healthy mental state. It uses a Convolutional Neural Network, a Recurrent Neural Network, and a Hierarchical Attention Network as the possible methods to build a profile on the user’s emotional state. This too is relevant to JitHDA’s goal of personalized chatbot sessions with the user, but this paper also achieves its goal by examining specific user statements in real-time instead of constructing the personalized session information from knowledge acquired beforehand.
P. Srivastava et al. [10] describes a chatbot which can automatically diagnose a person’s medical troubles. It begins from a position of ignorance and converses with the user until it can determine a shortlist of possible illnesses and eventually a most probable illness, and then proceeds to make recommendations for dealing with the problem. The system is similar to AIAC in that it iteratively asks dynamically chosen questions of a user in an attempt to form a model of the user. This paper is relevant to JitHDA’s goal of asking questions of the user and refining a model from the responses until a conclusion can be reached. Its main difference is that it starts from a position of ignorance and refines its questions as it advances to prune a wide possibility space to a single option, whereas JitHDA starts with ample information and uses it to create questions that discern between two possible states. The strategies and goals are similar, but ultimately approach the task in significantly different ways.
T. Zhu et al. [11] deals with authentication of mobile devices with the intent of warding against the threat of someone’s phone getting into the wrong hands. It discusses various biometric-based (‘something you are’) authentication and chooses to use widely used motion sensors found in many mobile devices to learn the patterns and behaviour of the authentic user for the purpose of authentication. This paper is relevant to JitHDA’s goal to use human dynamics to augment authentication capabilities, but focuses more on the physical handling of a device rather than a user’s knowledge of their past behaviour.
S. Kim et al. [12] proposed an extension to the SASL (Simple Authentication and Security Layer) authentication framework that allows the user to select various authentication levels with various permissions after authentication. This allows people to customize what level of security they make use of based on their current needs for the application, rather than accessing unlimited access every time. This paper focuses on the tradeoff between security and convenience that JitHDA is designed to remedy, but otherwise does not help create a JitHDA process in and of itself.
L. Dostálek et al. [13] creates a structure for dynamically changing the required authentication method in response to suspicious behaviour or hostile attacks. Authentication methods can be rated based on a set of metrics, including whether the user has unlimited retries or whether it is possible to eavesdrop on the authentication. By rating authentication methods this way, it becomes possible to respond to suspicious behaviour by merely selecting a better-rating authentication mechanism. This paper is another angle on the tradeoff between security and convenience, as it allows a system to only enable the inconvenient security measures when there is reason to suspect that something is amiss. While it does not help implement JitHDA, a JitHDA implementation would likely be very useful in such a system.
T. Tuna et al. [14] describes a method of performing in-depth examination of social media content in order to discern useful information about a given user. It discusses a variety of example features, such as gender, geolocation, and profession using a variety of methods. With this information, this paper creates a model able to understand social media users well enough to estimate useful metrics such as their expected future behaviour, which can be used for marketing purposes, or their risk of radicalization. It also uses this model to form a categorization system that allows for automatic detection of spammers and bot accounts.
While many of these papers provide novel and interesting advancements to chatbot and authentication technology, none of them are specifically applicable to implementing a JitHDA system. However, based on the favourable results of the experiments conducted above, researchers believe that AIAC is exactly suited to implementing JitHDA.
3. The Need for a Stronger Authentication
An ideal authentication system should be maximally (i) secure, (ii) accessible, and (iii) convenient. Such a system would allow any authentic user to authenticate themselves from any access point with minimal effort, while simultaneously rendering it impossible for any bad actors to fraudulently authenticate themselves.
When a situation does not permit achieving all of these goals at once, trade-offs must be made. ’Something you know’ authentication often performs very well on ease of use, and is consequently a favoured option for many applications, but can be insecure if the bad actor acquires the relevant knowledge. ’Something you are’ authentication can be extremely secure with fingerprint or iris scans that a bad actor would have no way to replicate [15], but can be very inaccessible if you need specialized hardware to perform the task adequately. Many recent applications combine ’something you know’ authentication with ’something you have’ authentication with Two-Factor Authentication systems that rely on both knowledge of a password and possession of a specific phone in order to be authenticated. This configuration has higher security than pure ’something you know’ authentication on account of both systems needing to fail at the same time and the two systems not having overlapping vulnerabilities, at a minor cost to convenience.
The most core problem with ’something you know’ authentication is the risk that the information used for such systems, such as passwords or recovery questions, can eventually find their way into the hands of bad actors, whereupon they become able to easily pretend to be the user from then on. The high danger of this stems from the fact that passwords, recovery questions, and other similar methods tend to stay the same over long periods of time, giving a bad actor plenty of time to find a user’s information. As an example, a recovery question based on the user’s first pet will always have the same answer no matter when it is asked, and a bad actor therefore has all the time in the world to figure out the relevant information and apply it to breaking the security of the question.
As such, properly secure ’something you know’ authentication requires three qualities. The first quality is that the information be hard to guess from a fraudulent user, the second quality is that the information be easy to recall from an authentic user, and the third quality is that the information not be repeated from previous authentication sessions. Passwords do not achieve this, instead being complex, repeated across many authentication sessions, and only hard to guess if the user actively chooses hard to guess passwords. A properly implemented JitHDA would be able to accomplish this, as JitHDA uses no repeat questions and builds each question from the recent actions of the user, which should be easy for authentic users to remember and hard for fraudulent users to guess. Therefore, a two-factor-authentication system utilizing both passwords and JitHDA will be much more secure than a one-factor-authentication employing only passwords.
References
- Ashibani, Y.; Mahmoud, Q.H. A multi-feature user authentication model based on mobile app interactions. IEEE Access 2020, 8, 96322–96339.
- Wong, A.B. Authentication through Sensing of Tongue and Lip Motion via Smartphone. In Proceedings of the 2021 18th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Rome, Italy, 6–9 July 2021.
- Mohamed, N.; Al-Jaroodi, J.; Jawhar, I.; Kesserwan, N. Data-driven security for smart city systems: Carving a trail. IEEE Access 2020, 8, 147211–147230.
- Raponi, S.; Pietro, R.D. A Longitudinal Study on Web-Sites Password Management (in)Security: Evidence and Remedies. IEEE Access 2020, 8, 52075–52090.
- Ouda, A. A framework for next generation user authentication. In Proceedings of the 2016 3rd MEC International Conference on Big Data and Smart City (ICBDSC), Muscat, Oman, 15–16 March 2016; pp. 1–4.
- Abu Sulayman, I.I.M.; Ouda, A. Designing Security User Profiles via Anomaly Detection for User Authentication. In Proceedings of the International Symposium on Networks, Computers and Communications (ISNCC), Montreal, QC, Canada, 20–22 October 2020.
- Liu, B.; Xu, Z.; Sun, C.; Wang, B.; Wang, X.; Wong, D.F.; Zhang, M. Content-oriented user modeling for personalized response ranking in chatbots. IEEE/ACM Trans. Audio Speech Lang. Process. 2018, 26, 122–133.
- Kao, C.; Chen, C.; Tsai, Y. Model of multi-turn dialogue in emotional chatbot. In Proceedings of the 2019 International Conference on Technologies and Applications of Artificial Intelligence (TAAI), Kaohsiung, Taiwan, 21–23 November 2019; pp. 1–5.
- Patel, F.; Thakore, R.; Nandwani, I.; Bharti, S.K. Combating depression in students using an intelligent chatbot: A cognitive behavioral therapy. In Proceedings of the 2019 IEEE 16th India Council International Conference (INDICON), Rajkot, India, 13–15 December 2019; pp. 1–4.
- Srivastava, P.; Singh, N. Automatized medical chatbot (medibot). In Proceedings of the 2020 International Conference on Power Electronics IoT Applications in Renewable Energy and Its Control (PARC), Mathura, India, 28–29 February 2020; pp. 351–354.
- Zhu, T.; Qu, Z.; Xu, H.; Zhang, J.; Shao, Z.; Chen, Y.; Prabhakar, S.; Yang, J. Riskcog: Unobtrusive real-time user authentication on mobile devices in the wild. IEEE Trans. Mob. Comput. 2020, 19, 466–483.
- Kim, S.; Kim, S. General authentication scheme in user-centric idm. In Proceedings of the 2016 18th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Republic of Korea, 31 January 2016–3 February 2016; pp. 737–740.
- Dostálek, L. Multi-factor authentication modeling. In Proceedings of the 2019 9th International Conference on Advanced Computer Information Technologies (ACIT), Ceske Budejovice, Czech Republic, 5–7 June 2019; pp. 443–446.
- Tuna, T.; Akbas, E.; Aksoy, A.; Canbaz, M.A.; Karabiyik, U.; Gonen, B.; Aygun, R. User characterization for online social networks. Soc. Netw. Anal. Min. 2016, 6, 104.
- Gahi, Y.; Lamrani, M.; Zoglat, A.; Guennoun, M.; Kapralos, B.; El-Khatib, K. Biometric identification system based on electrocardiogram data. In Proceedings of the 2008 New Technologies, Mobility and Security, Tangier, Morocco, 5–7 November 2008; pp. 1–5.
More
Information
Subjects:
Computer Science, Information Systems
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
823
Revisions:
2 times
(View History)
Update Date:
23 Dec 2022
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




