Your browser does not fully support modern features. Please upgrade for a smoother experience.

Submitted Successfully!
Thank you for your contribution! You can also upload a video entry or images related to this topic.
For video creation, please contact our Academic Video Service.
| Version | Summary | Created by | Modification | Content Size | Created at | Operation |
|---|---|---|---|---|---|---|
| 1 | Qasem Abu Al-Haija | -- | 1624 | 2022-11-09 23:44:08 | | | |
| 2 | Camila Xu | Meta information modification | 1624 | 2022-11-10 03:05:19 | | |
Video Upload Options
We provide professional Academic Video Service to translate complex research into visually appealing presentations. Would you like to try it?
Cite
If you have any further questions, please contact Encyclopedia Editorial Office.
Al-Haija, Q.A.; Alsulami, A.A. Remote Keyless Using Pre-Trained Deep Neural Network. Encyclopedia. Available online: https://encyclopedia.pub/entry/33771 (accessed on 08 February 2026).
Al-Haija QA, Alsulami AA. Remote Keyless Using Pre-Trained Deep Neural Network. Encyclopedia. Available at: https://encyclopedia.pub/entry/33771. Accessed February 08, 2026.
Al-Haija, Qasem Abu, Abdulaziz A. Alsulami. "Remote Keyless Using Pre-Trained Deep Neural Network" Encyclopedia, https://encyclopedia.pub/entry/33771 (accessed February 08, 2026).
Al-Haija, Q.A., & Alsulami, A.A. (2022, November 09). Remote Keyless Using Pre-Trained Deep Neural Network. In Encyclopedia. https://encyclopedia.pub/entry/33771
Al-Haija, Qasem Abu and Abdulaziz A. Alsulami. "Remote Keyless Using Pre-Trained Deep Neural Network." Encyclopedia. Web. 09 November, 2022.
Copy Citation
Keyless systems have replaced the old-fashioned methods of inserting physical keys into keyholes to unlock the door, which are inconvenient and easily exploited by threat actors. Keyless systems use the technology of radio frequency (RF) as an interface to transmit signals from the key fob to the vehicle.
artificial intelligence
cybersecurity
remote control
1. Introduction
Rapid technological advancement allows the usage of computers and wireless devices with modern vehicles to increase customer security and convenience [1]. Keyless systems are considered a vital component of modern vehicles because they perform several functions, such as locking and unlocking the doors, opening and closing the trunk, and starting the engine [2]. The first remote keyless system used with a vehicle was introduced in 1982 [3]. Keyless systems have replaced the old fashion methods of inserting physical keys into the keyhole to unlock the door, which are inconvenient and easily exploited by threat actors [4]. Generally, there are two types of keyless systems, remote keyless entry (RKE) and passive keyless entry (PKE) [5]. Both keyless systems use the technology of radio frequency (RF) as an interface to transmit signals from the key fob to the vehicle. In the RKE system, the driver needs to press the fob button to send the intended command to the vehicle, i.e., unlock the door. Then, the authenticated protocol is used to validate the vehicle’s owner [6]. However, the PKE system does not require drivers to press any button. Still, once the fob becomes close to the proximity distance of the vehicle, an authentication protocol establishes before the automated command is sent to the vehicle [7].
The early keyless system was developed based on static code sent from the key fob to the receiver, which is easily compromised by a thread actor who intercepts the transmitted signal and performs a replay attack [6]. A replay attack is also called a playback attack, when authorized legitimated data are captured and copied during transmission by a threat actor to be repeated for fraudulent purposes, as illustrated in Figure 1 [8]. Rolling codes attempted to overcome this issue by producing a changed code based on a counter. Therefore, a new code is generated every time the keyless system is used; however, a rolling code is also suspectable to different types of replay attacks [9]. Due to the vulnerability of the keyless systems, threat actors can exploit them to steal vehicles or owner belongings. For example, United Kingdom police broadcasted a video illustrating how a threat actor can steal a vehicle within 1 min using relay devices [10]. Furthermore, increasing the number of installed communication technologies, such as keyless, WiFi, and Bluetooth systems in a vehicle, leverages drivers’ and passengers’ convenience and enables fast transformation into automation. However, this opens the gate to more opportunities for establishing cyberattacks [11].
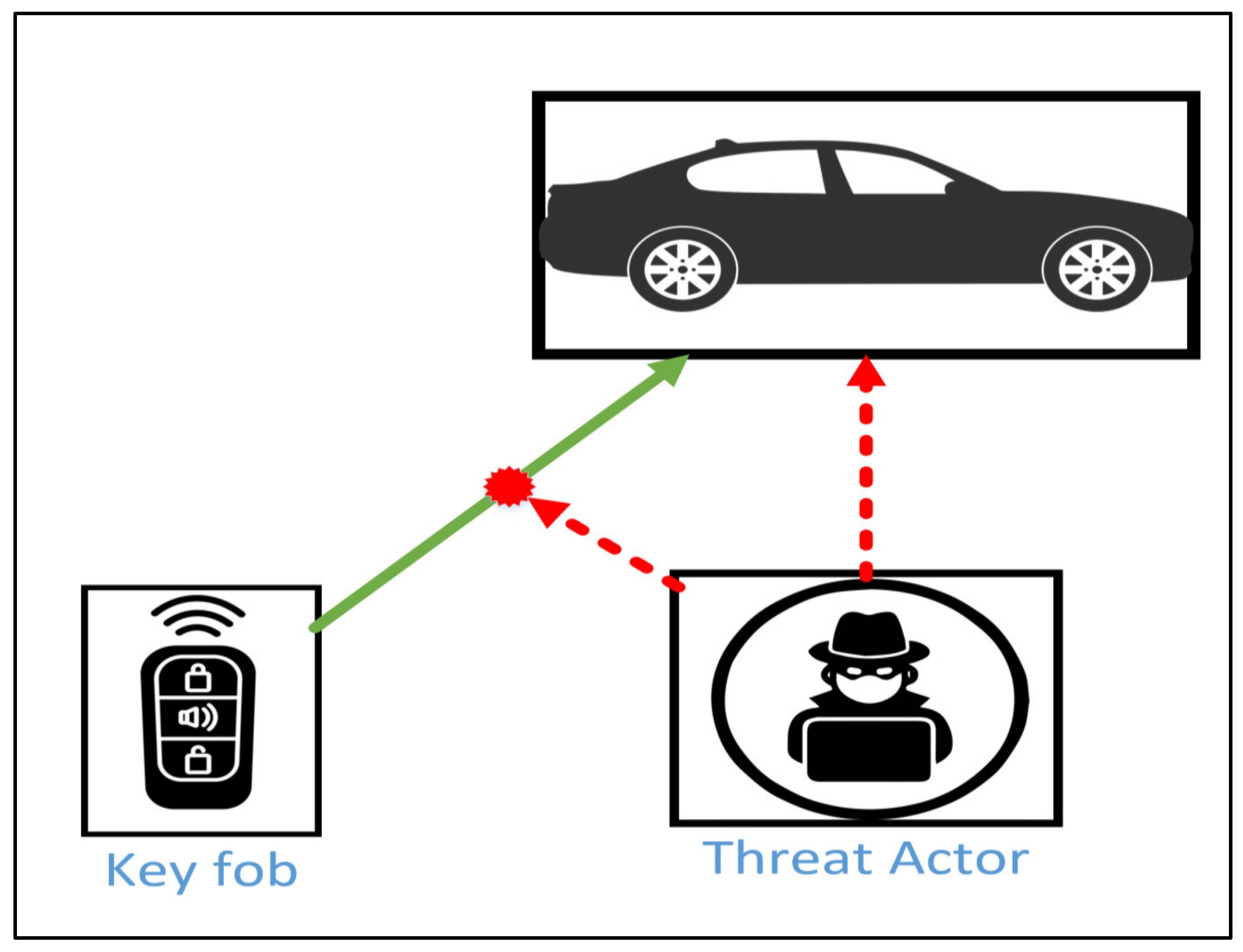
Figure 1. Replay Attack Targeting keyless system.
The theory of the CIA triad model, which is the conditionality, integrity, and availability, can be used to measure the security level of a system [11]. Conditionality assures that data will not be accessed by unauthorized users, programs, or procedures. To guarantee that only authorized users can access the data, sufficient control mechanisms are used. Integrity has much to do with reliability; thus, unauthorized users must not modify the data. Finally, availability ensures that data must be available and not prevented when users need it [12].
Recently, researchers used different authentication techniques to mitigate and prevent threats on keyless systems, such as authentication using smartphones [13], authentication using bioinformatics [14], and authentication using blockchain [15][16]. However, this field still needs more research to investigate how to resist malicious activities on keyless systems.
2. Remote Keyless Controlled Vehicles Using Pre-Trained Deep Neural Network
Modern vehicles are designed to rely on the keyless system when starting the engine and unlocking and locking doors instead of using traditional keys for the convenience of vehicle owners. However, there is a cost to using such technology because keyless systems are susceptible to various attacks, such as replay, relay, and man-in-the-middle (MITM) attacks [17].
Cryptography could be used to eliminate replay attacks, as the authors of [6] developed an encryption algorithm to prevent replay attacks on remote keyless vehicles. Their model was built based on asymmetrical and hashing methods to allow authentication between the vehicle and the owner. The authors of [18] also used cryptography methods to mitigate replay attacks in remote keyless systems by enhancing the performance of the KeeLoq algorithm. However, the authors of [4] illustrated that encryption techniques are insufficient for authentication, and there is a need for more security layers; therefore, they proposed the HODOR technique to detect attacks targeting keyless systems using a classifier algorithm they implemented. The vehicle owner needs to hold the door handle, and radio frequency fingerprinting is used to detect unauthorized commands based on collected features.
To enhance the authentication mechanism of the remote keyless system, [19] introduced an authentication protocol based on challenge-response pairs integrated with the RKE system. Therefore, the command sent from the key fob to the vehicle is first verified then a challenge is computed. Next, the computed challenge is sent from the vehicle to the key fob. Finally, the key fob computes the challenge and sends the response to the vehicle that verifies the response and executes the command.
Smart vehicles that use a controlled area network (CAN) for communication purposes are vulnerable to cyberattacks since CAN protocol has limited security mechanisms to provide comprehensive, secure communication [20]. There are several reasons for CAN vulnerabilities of cyberattacks, such as that the exchanged messages between the physical components are not encrypted, and all components are connected with the same CAN bus; therefore, the same message can be broadcasted to all components [20]. Aldhyani et al. [21] implemented a deep learning model that integrates a convolution neural network (CNN) with long short-term memory (LSTM) to defend the self-driving car network from various cyberattacks, such as packets, replaying, and spoofing attacks. The authors evaluated their model using a collected dataset from real network traffic of CAN that was injected with the cyberattacks above. They achieved 97.30% using the classification accuracy metric.
The authors of [22] proposed a biometric method to enhance the security of the keyless system. Their model integrates two security levels: face recognition and fingerprint. In the face recognition phase, the driver’s face is captured using a camera attached to the vehicle door, and a spoofing algorithm is used to perform anomaly detection to identify the legitimacy of the driver. In the fingerprint phase, the driver’s fingerprint is scanned using another spoofing algorithm; therefore, if the fingerprint is confirmed, the driver can access the vehicle. However, this model has a challenge in finding the perfect position of the camera used for face recognition.
Blockchain is a recent technology that can also be used to enhance the security of the keyless system. It is an advanced technology built to increase the security of pair-to-pair networks. Blockchain is considered a decentralized distributed system. It is a well-known technology used to secure transactions in the cryptocurrency market, such as Bitcoin [23]. The authors of [8] proposed an authentication model based on a Blockchain system. Basically, the transmitted data between the key fob and the vehicle is encrypted using hash algorithms. The authors compared secure hash algorithms: SHA-1, SHA-256, SHA-512, and message digest (Md5).
Machine learning (ml) techniques can be used to mitigate the impacts of attacks targeting keyless systems. The authors of [24] implemented a data-intensive model using ml to prevent relay attacks on the PKE system. The authors developed their models based on artificial neural networks (ANN), K-nearest neighbors (KNN), support vector machines (SVM), and decision trees. They trained their ml algorithms using the following features: date, time, elapsed time, location, type of day, key fob signal strength, and key fob acceleration. According to the authors, the decision tree outperformed the other ml algorithms and reached 99% accuracy based on the classification accuracy metric.
Most keyless systems use radio-frequency identification (RFID) technology as an interface to transmit a command from the key fob to the vehicle. However, RFID could be vulnerable to various malicious attacks, such as relay attacks. Therefore, the authors of [25] used several security features to proximity identify the location of the vehicle based on contextual information, such as global positioning system (GPS) coordinates, receiving signal strength indicator (RSSI), and WiFi access points. Therefore, their technique helps to overcome the vulnerability of RFDI, which can be compromised using a variety of attacks, such as relay attacks. Moreover, the authors of [10] proposed a context detection method to detect relay attacks on passive keyless entry systems using a smartphone. Therefore, a secure connection between the vehicle owner’s smartphone and the vehicle is established using Bluetooth low energy (BLE) technology to track the location of the vehicle’s owner and determine their proximity to the vehicle, then evaluate the legality of the owner.
The authors of [26] proposed a timestamp-based method to defend remote keyless systems from replay attacks. The authors enhanced the rolling-code algorithm by adding a timestamp factor (time in seconds) to the generated code. Therefore, each time the rolling-code algorithm generates code, the time in seconds is added as a parameter with the generated code. Even though a threat actor captures the generated code, they still need to know when the code was generated. However, this method requires the clock to be synchronized between the sender and receiver. Table 1. lists a summary of the most recent proposed solutions to leverage the security of the keyless system.
Table 1. Summary of recently proposed solutions for the security of the keyless system.
| Research | Proposed Solution |
|---|---|
| [6] Poolat et al. | Asymmetrical and hashing methods |
| [18] Madhumitha et al. | Enhanced KeeLoq algorithm |
| [4] Kyungho et al. | HODOR |
| [19] Jinita et al. | Challenge-response pairs |
| [21] Aldhyani et al. | CNN and LSTM |
| [22] Béatrix-May et al. | Biometric |
| [8] Husain et al. | Blockchain |
| [24] Usman et al. | ML |
| [25] Juan et al. | Contextual information |
| [10] Jing et al. | Contextual information |
| [26] Greene et al. | Timestamp-based |
References
- Lennert, W.; Benedikt, G.; Bart, P. My other car is your car: Compromising the Tesla Model X keyless entry system. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2021, 2021, 149–172.
- Kyle, G.; Deven, R.; Henry, D.; Quamar, N.; Khair, A.S.; Vijay, D. A Defense Mechanism Against Replay Attack in Remote Keyless Entry Systems Using Timestamping and XOR Logic. IEEE Consum. Electron. Mag. 2021, 10, 101–108.
- Marin, E.; Ashur, T.; Gierlichs, B.; Preneel, B. Fast, Furious and Insecure: Passive Keyless Entry and Start Systems in Modern Supercars. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 66–85.
- Kyungho, J.; Wonsuk, C.; Hoon, L.D. Hold the Door! Fingerprinting Your Car Key to Prevent Keyless Entry Car Theft. arXiv 2020, arXiv:2003.13251.
- KiranRaj, K.S.; Ananya, C.; Ratan, S. Analysing Remote Keyless Entity Systems. Int. J. Res. Anal. Rev. 2019, 6, 136–138.
- Poolat, P.R.; Biplab, S. An Authentication Mechanism for Remote Keyless Entry Systems in Cars to Prevent Replay and RollJam Attacks. In IEEE Intelligent Vehicles Symposium (IV); IEEE: Aachen, Germany, 2022.
- Abu Al-Haija, Q.; Al Badawi, A. High-performance intrusion detection system for networked UAVs via deep learning. Neural Comput. Appl. 2022, 34, 10885–10900.
- Husain, R.; Khan, R.; Tyagi, R.K. Novel Technique for Secure Keyless Car Authentication using Block-Chain System. I-Manag. J. Comput. Sci. 2020, 8, 12020.
- Tobias, V.C.; Carlo, M.; Veelasha, M.; Erik, P. Security Analysis of Aftermarket Remote Keyless Entry Systems for Consumer Vehicles; Radboud University Nijmegen: Nijmegen, The Netherlands, 2020.
- Jing, L.; Yabo, D.; Shengkai, F.; Haowen, Z.; Duanqing, X. User Context Detection for Relay Attack Resistance in Passive Keyless Entry and Start System. Sensors 2020, 20, 4446.
- Al-Haija, Q.A.; Alsulami, A.A. High-Performance Classification Model to Identify Ransomware Payments for Heterogeneous Bitcoin Networks. Electronics 2021, 10, 2113.
- De la Cruz, J.E.C.; Romero, G.C.A.; Delgado, C.C. Open VProxy: Low-Cost Squid Proxy Based Teleworking Environment with OpenVPN Encrypted Tunnels to Provide Confidentiality, Integrity and Availability. In Proceedings of the IEEE Engineering International Research Conference (EIRCON), Lima, Peru, 21–23 October 2020.
- Paul, S.; Kai, J.; Christian, Z.; Christof, P. Securing Phone as a Key Against Relay Attacks. In Proceedings of the 18th Escar Europe: The World’s Leading Automotive Cyber Security Conference (Konferenzveröffentlichung), Berlin, Germany, 11–12 November 2020.
- Asadullah, A.; Karthik, P.; Sharath, D.; Mohammad, A.; Sourik, M.; Chidambaram, V. Mechanism to Identify Legitimate Vehicle User in Remote Keyless Entry System; SAE Technical Paper; SAE International: Warrendale, PA, USA, 2022.
- Pouyan, R.; Abdollah, K.-F.; Morteza, D.; Tao, J.; Wencong, S. Ultra-Lightweight Mutual Authentication in the Vehicle Based on Smart Contract Blockchain: Case of MITM Attack. IEEE Sens. J. 2020, 21, 15839–15848.
- Ibrahim, R.F.; Abu Al-Haija, Q.; Ahmad, A. DDoS Attack Prevention for Internet of Thing Devices Using Ethereum Blockchain Technology. Sensors 2022, 22, 6806.
- Juan, W.; Karim, L.; Mohammad, Z. CSKES: A Context-Based Secure Keyless Entry System. In Proceedings of the EEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019.
- Madhumitha, S.S.; Rohini, P.; Arunkumar, R.; Gunasekaran, R. Effective Cryptography Mechanism for Enhancing Security in Smart Key System. In Proceedings of the Tenth International Conference on Advanced Computing (ICoAC), Chennai, India, 13–15 December 2018.
- Jinita, P.; Lal, D.M.; Sukumar, N. On the Security of Remote Key Less Entry for Vehicles. In Proceedings of the IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Indore, India, 16–19 December 2018.
- Emad, A.; Omer, R.; Charith, P.; Peter, B. Cyberattacks and Countermeasures for In-Vehicle Networks. ACM Comput. Surv. 2022, 54, 1–37.
- Theyazn, H.A.; Orcid, H.; Hasan, A. Attacks to Automatous Vehicles: A Deep Learning Algorithm for Cybersecurity. Sensors 2022, 22, 360.
- Béatrix-May, B.; Ştefan, S.I.; Claudia, P.-N.A.; Florin, P. Cyber-Physical Systems—A New Approach for Keyless Entry Systems. In Proceedings of the 23rd International Conference on Control Systems and Computer Science (CSCS), Bucharest, Romania, 26–28 May 2021.
- Odeh, A.; Keshta, I.; Al-Haija, Q.A. Analysis of Blockchain in the Healthcare Sector: Application and Issues. Symmetry 2022, 14, 1760.
- Usman, A.; Hong, S.; Awais, B.; Mamoun, A.; Alireza, J. Secure Passive Keyless Entry and Start System Using Machine Learning. Security, Privacy, and Anonymity in Computation. Commun. Storage 2018, 11342, 304–313.
- Wang, J. A Secure Keyless Entry System Based on Contextual Information, Proquest. Ph.D. Thesis, Queen’s University, Kingston, ON, Canada, 2019.
- Kyle, G.; Deven, R.; Henry, D.; Kyle, M.; Quamar, N.; Khair, A.S. Timestamp-based Defense Mechanism Against Replay Attack in Remote Keyless Entry Systems. In Proceedings of the IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 4–6 January 2020.
More
Information
Contributors
MDPI registered users' name will be linked to their SciProfiles pages. To register with us, please refer to https://encyclopedia.pub/register
:
View Times:
1.1K
Revisions:
2 times
(View History)
Update Date:
10 Nov 2022
Notice
You are not a member of the advisory board for this topic. If you want to update advisory board member profile, please contact office@encyclopedia.pub.
OK
Confirm
Only members of the Encyclopedia advisory board for this topic are allowed to note entries. Would you like to become an advisory board member of the Encyclopedia?
Yes
No
${ textCharacter }/${ maxCharacter }
Submit
Cancel
Back
Comments
${ item }
|
More
No more~
There is no comment~
${ textCharacter }/${ maxCharacter }
Submit
Cancel
${ selectedItem.replyTextCharacter }/${ selectedItem.replyMaxCharacter }
Submit
Cancel
Confirm
Are you sure to Delete?
Yes
No




