1. Introduction
Wireless sensor networks serve as the link between the digital and the physical worlds. Forthcoming wireless network sensors are expected to be deployed in almost every sphere of the human activity system and used in a manner not yet envisaged. Thus, the need to mass produce low-cost integrated sensor nodes that will enhance the use of technology for bridging a myriad of domains cannot be overemphasized. Some of the few areas where future sensor networks can be deployed include earthquake monitoring, environmental monitoring, factory automation, home and office controls, inventory monitoring, medicine,
etc. The increasing prevalence of wireless networks has not only increased the possibilities of information integration into applications, but has also influenced our interactions with others, in study and work. A typical example of such an information source is location information, which is of great importance in many applications. The term localization is the ability to determine the physical position of a static or mobile sensor node or wireless device. The use of a wireless device for tracking locations is a growing trend that holds great prospects for a wide range of applications, particularly for those employed in physical security, asset tracking, geographic routing and workflow management [
1].
The increase in the use of these wireless devices by both people and objects has brought to light the importance of precision in node positioning in sensor and wireless networks. This is because of the important input role played by sensor location in various high-level networking tasks and applications. For example, nowadays, received signal strength (RSS) measurement hardware is included in all modern radio chip sets, so as to determine the transmitted packets. This comes at a very high cost and deployment benefit when the existing communication network’s RSS infrastructure is re-used for localization. The typical pattern for most RSS-based localization strategies is a transmitter or receiver that takes measurements of the RSS of a number of landmarks at known positions, also known as the device. The device is then positioned using a fingerprint method or the resulting RSS values [
2].
Despite the wide variety of algorithmic strategies, such as machine learning approaches and minimization of least squares methods, proposed by different studies, the issue of multipath effects still remains a key challenge in the domain of wireless localization based on RSS. Some of the challenges range from signal blocking or shadowing, waves bouncing off an object or reflection, waves spreading as a result of obstacles or diffraction and waves bending as they pass through different mediums or refraction. All of these impact negatively on the RSS, thereby making it a tedious task to accurately determine their effects in complex indoor environments. The typical localization error averages between 10 ft to 30 ft or more for maximum errors. Furthermore, there is a tendency for the frequency and power level to negatively influence the localization performance as a result of the wireless signal propagation. The distance at which the signal can travel is dependent on the power level of the signal propagation, while the frequency of the signal transmission determines how the environment can influence the mode of the propagated signal [
3].
Sensor nodes, unlike traditional networks, usually operate in attack-prone areas, thus increasing physical attack risks, which may lead to the modification of their underlying code or cryptographic material exposure. The complexity of this problem is evidenced by the inability to produce tamper-resistant sensor nodes because of the marginal cost effect of the hardware. This makes sensor nodes more vulnerable to physical attack under such environments compared to a typical personal computer located in a secure place and subjected to individual attacks from its network.
As localization is becoming popular, numerous attacks on the localization process are also on the rise. These attacks confuse the localization process and cause location estimation errors. Therefore, the ability to have efficient wireless sensor network localization accuracy in the presence of physical signal strength attacks is a challenging and extreme undertaking.
Several recent researchers were unable to accomplish a highly secured localization performance without utilizing the cryptographic technique, which requires a complex hardware design. While the main important task of the new proposed solution based on the multi-frequency multi-power localization (MFMPL) algorithm is to detect, eliminate and overcome the influence of these physical attacks (barrier attacks) under the shadow fading propagation system model without using cryptographic techniques, the new proposed solution is expected to achieve an accurate and effective performance.
5. Proposed Solution
We propose a solution based on multi-frequency multi-power transmission through using two techniques: a step function multi-frequency multi-power localization (SF-MFMPL) and a combination of multi-frequency multi-power localization (C-MFMPL). In order to mitigate the influence of shadow fading, the averaging of all RSS over all of the transmitted frequencies will be performed. In our solution, the anchor or access point (AP) nodes will transmit signals in multi-frequencies at multiple power levels. Sensor nodes receive these signals and construct the average RSS fingerprint from them. All of the sensors are already coded with the knowledge of the expected frequencies and the power level from the AP. By observing the RSS fingerprint that is expected, the sensor will be able to find if there is a barrier attenuating or degrading the signal. The sensor will reject the RSS fingerprints that it doubts as attenuation or degradation. Leaving those corrupted RSS fingerprints, the sensor nodes will choose the remaining RSS fingerprints from the uncorrupted RSS and utilize lateration with non-linear least squares to get the location of the sensor node.
The sensor and the AP are strictly time synchronized. This can be done by running a quartz crystal clock in all of the sensors and the AP. With the help of the quartz crystal, all of them are time synchronized. Quartz crystal-based time synchronization is easy to implement, and it is inexpensive. More information about other time synchronization methods in wireless sensor networks can be found in [
30,
31].
In order to avoid the estimation being affected by interference and reflection, we propose a technique to filter those signals by estimating the approximate angle of arrival of the signal. In addition, we also propose a method to get the estimation of the attack area in the network. By estimating the attack area and alerting the network administrator, those barriers can be removed and the localization accuracy improved.
5.1. Modified Robust Localization Based on the Multi-Frequency Multi-Power Approach
Location is achieved by utilizing a multi-frequency multi-power transmission. The knowledge of the frequency and power level from the expected antenna is known a priori by the sensor. We vary the frequency by three levels, 400 MHz, 600 MHz and 800 MHz, as well as synchronously vary the power level by three levels, 4 dB, 6 dB and 8 dB. After averaging each received power level that has been transmitted by the three frequency levels, three dimensions of the RSS between the sensor and each landmark result. The use of three levels of frequency and power transmission will be suitable enough to accomplish an accurate performance without any extra computational cost and complexity, as well as reducing the fingerprint database memory size.
The receiver at the sensor node will try to synchronize and check the expected power level and frequency to check if there is any signal degradation or attenuation in the path of the signal. The lateration technique is applied on the position of the sensor and the distance measurement to get the location of the sensors. In addition, based on the signal irregularities at all sensors, the map of the region of attack is found. By cooperating with all sensors, the sensor is able to identify the area of the physical barrier attack.
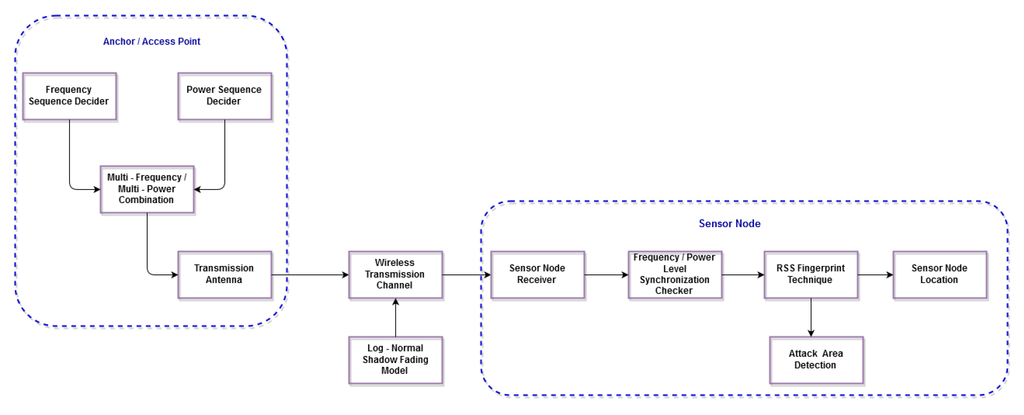
The functional block diagram of our previous work (SF-MFMPL) can be found in [
32]. illustrates the functional block diagram of the (C-MFMPL) scheme.
Figure 1. Block diagram of the proposed localization solution.
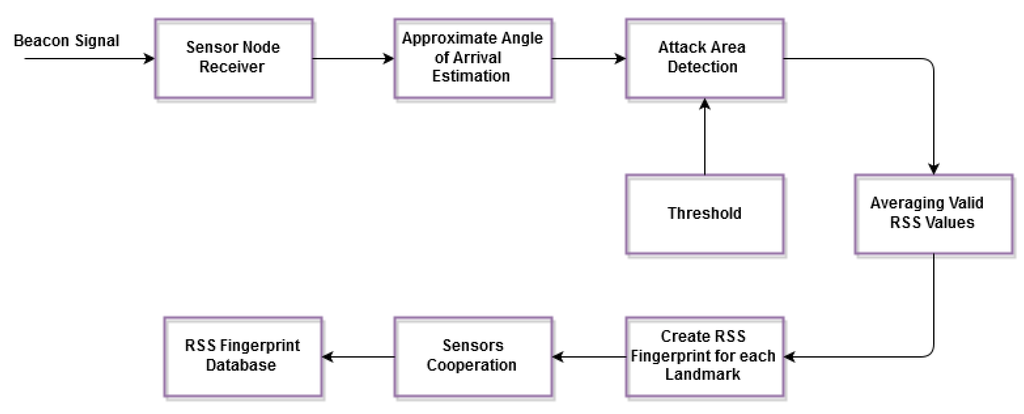
The fingerprint of the proposed solution consists of two phases, offline and online. In the offline phase, the beacon signal will be checked first through various stages until the final stage, which creates the RSS fingerprint for each landmark. The sensor device is assumed to have knowledge about the AP’s position and the approximate angle of the AP’s location. Knowing the approximate angle range in which the AP is located helps to avoid any faulty measurements due to signal interference or reflection by the barriers. Since sensor nodes are placed randomly in the network, the angle of arrival of the signal from the AP is found by sensor tuning in each direction till the maximal power is received. This process has to be done for each AP at the initial deployment time. The threshold is the amount of tolerance between that estimated and the actual one. It can be measured by placing a small obstacle for signal degradation at different points in the network and measuring the error. The size of the obstacle will be the maximum obstacle size that our network can tolerate. This is done to accommodate certain infrastructure provisions made by the administrator of the network. The stage of averaging each received power level that has been transmitted by the three frequency levels is very important to overcome the effect of the log-normal shadow fading effects. Finally, the last stage in the offline phase is the cooperation of the sensor nodes to create the RSS fingerprint database of the whole network, while in the online phase, the sensor node receives the beacon signal, then averages the RSS and matches it to the fingerprint database, besides using the lateration and trilateration techniques to pin-point the sensor node position.
1. Offline Phase:
The fingerprints are produced and stored in a database during this phase containing the average RSS readings of the anchor nodes’ positions. Actually, the location of the anchor nodes ought not to change during the online phase. shows the block diagram of the offline phase.
Figure 2. Offline phase of the proposed solution.
The representation of the fingerprint database for the (C-MFMPL) solution can be utilized by a set of RSS with the coordinates of the anchor nodes gathered by each sensor in the network, as shown in Equation (
14).
where: f1, f2, f3 are the transmitted frequencies; P1, P2, P3 are the decided power levels.
The average RSS all over the transmitted frequencies that are stored in the fingerprint database can be defined in Equations (
15) and (
16), respectively.
rjirij represents the average RSS readings estimated from anchor j, and m represents the number of anchors utilized in the network.
Moreover, Equation (
17) shows the
RofflineRoffline set that is gathered and stored in the fingerprint database during the offline phase.
The PofflinePoffline and SofflineSoffline sets represent the anchor nodes’ coordinates and the average RSS measurements, respectively.
While in the (SF-MFMPL) solution, each anchor (AP) sends beacons according to a step function, each decided power level will be sent with a decided frequency [
32]. In order to mitigate the effect of the log-normal shadow fading, the averaging of N (RSS) values collected from each anchor (AP) has been performed in this solution according to Equation (
18).
The value of (N = 3) will be taken for this solution to maintain the same system model conditions that are used for the (C-MFMPL) technique.
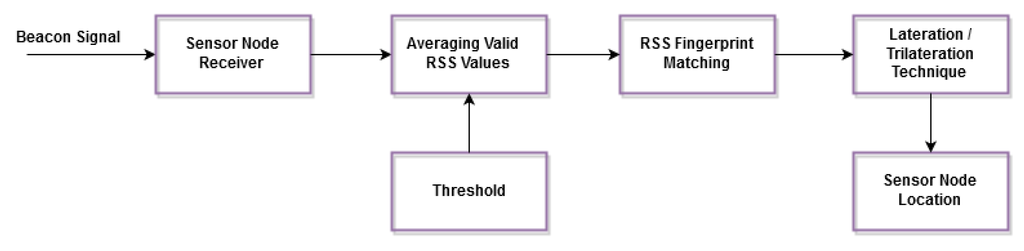
2. Online Phase:
During the online phase, the sensor nodes receive the transmitted beacons from the anchors with the same combinations of the frequency and power levels. illustrates the online phase of the proposed solution.
Figure 3. Online phase of the proposed solution.
Therefore, another measurement set of the RSS, called
SonlineSonline, is produced, which will be utilized for seeking the right fingerprints according to the fingerprint matching database, as shown in Equations (
19) and (
20), respectively.
Ronline denotes the average RSS readings received from each anchor node.
Eventually, the online phase depends on the RSS fingerprints generated by the offline phase to find the best matching RSS values for the estimation of the sensor node location. The RSS fingerprint machine learning database plays the most important key role in the proposed algorithm, first through filtering the physical barrier attack effects with the help of the proposed grid coloring algorithm, which depends on the angle of arrivals of the beacon signals received from each anchor (AP), and, second, participating in the process of mitigating the harsh shadow fading environment.
5.2. RSS Measurement
As an aspect of sensor network communication and sensing subsystems, various sensor designs have been supported by the angle of arrival (AOA) mechanism, such as tracking and other applications, which accord improved monitoring in the orientation of the target by means of beamforming [
33]. Sensors might also be supported by directional antenna arrays, so that the communication transmission can be directed toward the required destination and lessening the neighbor sensor interference. With the antenna beam pattern information, a single radio receiver with a multiple antennae system might also be utilized for the efficient angle of arrival determination of the RF signal.
A multiple beam pattern of the directional antenna array can be used to determine the received signal strength RSS ratio. This solution establishes a low complexity and cost for the sensor network design. Each anchor (AP) is assigned a combination of the frequency and power level transmission. Before starting localization, each sensor node tunes in to the approximate angle in which an AP is located to capture the signal and measure the RSS. By tuning in to the approximate angle, we are able to filter out the RSS measurement errors due to reflection and interference signals from other directions. Each sensor calculates the estimated signal frequency and power according to the defined frequency and power level combination. Depending on Equations (
21) and (
22), the tuning is done in a way to minimize the error between the actual transmitted frequency and power level.
If the deviation in the error within the approximate angle is greater than the threshold, the RSS value from that AP must be rejected, as it is an indication of signal attenuation or degradation by the attacker; the deviation in error can be calculated from Equations (
23) and (
24), respectively.
Df and Dp must be less than threshold T for the RSS value in order to be accepted. Every sensor must measure the average RSS value all over the transmitted frequencies for the same anchor (AP). The best value of the RSS with the lower values of Df and Dp must be taken. The AP’s location (x, y) together with its measured average RSS value constitutes the RSS fingerprint for that AP. Each sensor node must calculate the average RSS fingerprint for all of the APs whose Df and Dp is less than the threshold T.
In this paper, The RSS error between the original measurements and the reconstructed measurements at a certain threshold, which presents the least amount of error for an individual network to be localized, is identified by the RSS error threshold value. Intuitively, as the discard threshold increases, the error increases (that is, the ability to reconstruct a true representation of the original signal degrades), for which the RSS error from each anchor (AP) increasing by more than 15% of the nominal RSS will be neglected, while RSS error less than 15% will be accepted. In order to select an appropriate RSS threshold, the use of an exhaustive search based on computer simulations is mandatory, due to the complexity involved in the problem at hand. Meanwhile, finding the optimum threshold value is difficult and needs extensive training for the simulation procedure. Hence, based on the relevant empirical and experimental studies related to the threshold value selection, we consider the RSS error up to 15% of the nominal RSS as the acceptable approximate threshold.
5.3. Localization
Localization involves two stages: ranging and lateration. Ranging estimates the distance d from the position of the sensor node to the anchor (AP). The RSS can be expressed according to Equation (
25).
Therefore, the distance can be determined from Equation (
26) as follows:
where:
PoPo is the power received in dBm at a 1-m distance; d is the distance between the node and the AP;
α is the path loss component.
Lateration gets the position of the sensor node from the distance measurement for different anchors (AP) and their locations. There are two popular methods to get the location estimate: non-linear least squares (NLS) and linear least squares (LLS). In NLS, from the estimated distance di and known positions Li = (xi,yi) of the landmarks, the position (x,y) of the target device can be estimated by finding
(xˆ,yˆ)(x^,y^) satisfying Equation (
27).
where i = 1…n for n total landmarks.
Since solving this equation is computationally complex, we can approximate this relation as shown in Equation (
28) [
34].
where:
and:
A is described by the coordinates of landmarks, and b is composed of the estimated distance to landmarks. The position estimation is solved by Equation (
31).
Moreover, for the localization based on a trilateration technique, the anchor nodes’ coordinates defined by the i-th beacon Bi are (xBi, yBi); the coordinates of the unknown sensor node are (x,y); RSSIi refers to the signal strength measurements between the sensor node and each anchor node; and di is the distance estimation among the sensor node and the i-th beacon node Bi. Assume three beacons (b1, b2, b3) with three distance estimations (d1, d2, d3), then the sensor node coordinates can be obtained as follows [
14]:
By utilizing the earlier two equation minus the third one, respectively, we can determine the following equations:
By expressing Equation (
33) in matrix form, we get:
Along these lines, rather than using the real distance di, it is sensible to utilize the noisy estimations
diˆdi^, then Equation (
34) can be denoted as follows:
where
(xˆ,yˆ)(x^,y^) is the unknown node coordinate estimation. By subtracting Equation (
36) from Equation (
34), we can get the localization error of the unknown sensor node as below:
In view of Equation (
37), it demonstrates the localization error for utilizing the trilateration method, which is identified with both the RSSI ranging errors and the anchor node coordinates, as it is known
a priori that the anchor nodes are fixed nodes with known coordinates, so that the localization error is resolved in terms of the RSSI ranging error only, besides the anchor nodes having to be deployed legitimately. Along these lines, the error in the localization accuracy can be determined by the equation below:
5.4. Detecting Attack-Prone Regions
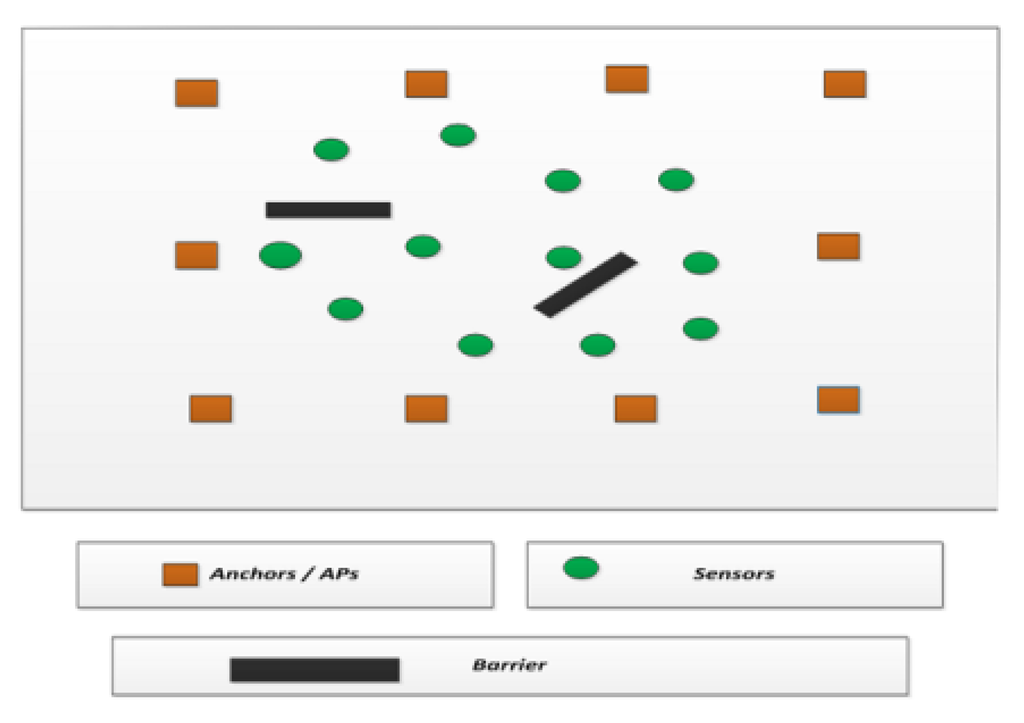
One of the important advantages of our solution is that we can detect the region of attack and take some corrective action. In our solution, each sensor node can identify the AP that has barriers in the path of the sensor node. Each sensor node sends data to a signal fusion center, which marks the boundary of the attack region and handles it by eliminating barriers effect.
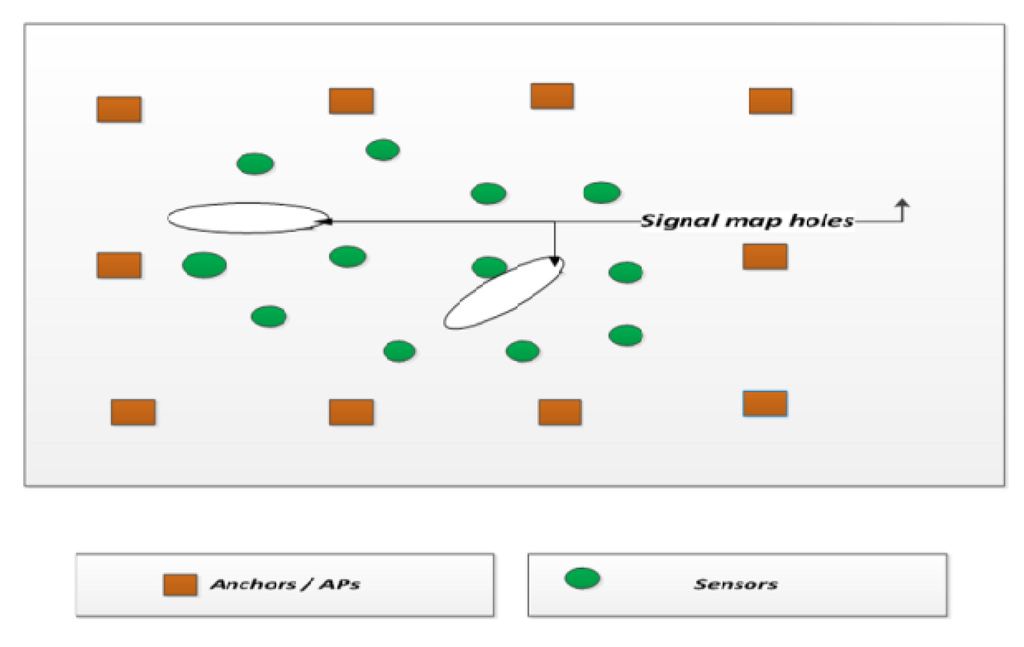
shows a network with APs, sensors and barriers. With the accepted AP (whose error deviation is less than the threshold) and the rejected AP (whose error deviation is above the threshold), the sensor node location estimated is provided to the signal fusion center. The signal fusion center is also aware of the direction of the propagation of the signal from the anchor (AP) to the sensor nodes.
Figure 4. Wireless sensor network system model with APs, sensors and the barriers.
Based on this information, the signal fusion center constructs a signal map. The signal map is the representation of points where the signals from the APs are able to traverse the network. Signal map holes are places where the signal from the AP is not accepted at the sensor node due to a larger error deviation in the signal power, as shown in .
Figure 5. Signal map holes at the fusion center.
Actually, sensor nodes have the flexibility to communicate with the anchor node, so as to build the radio signal map by means of the wireless channel. As a rule, a fusion center at each sensor node is jointly processing the signal in order to make accurate situational estimations. For the detection part, the fusion center necessitate making a decision concerning the presence of an attenuation of the received signal strength due to a barrier attack. Typically, a threshold value should be utilized to make a proper decision, and it is a significant parameter for the detection procedure.
Based on the whole network signal map defined by the RSS fingerprint database, which is created by the cooperating sensor nodes, actually, the valid RSS readings will be utilized for the estimation of the sensor node location, while the neglected RSS values refer to the signal holes in the fingerprint to be taken into consideration for detecting the area of attack. This mechanism introduces the basis of the fusion center at each sensor node to make the proper decision for identifying the signal holes in the network.
Through construction of the signal map, we are able to identify the signal holes in the network. Signal holes are the regions of attack in the network and must be corrected. The usual corrective action is to remove the barrier manually.
To detect the signal hole, we propose a grid coloring algorithm. The algorithm splits the entire network into small equally-sized grids. Initially, all of the grids are white. The sensor locations are marked in the grids. When a sensor accepts the AP’s RSS value (since the error deviation in the signal power is less than the threshold), the grids in the direction from the AP to the sensor node along the direction of the signal are colored gray. This process is performed for all sensors for all of the accepted AP. Once the process is complete, all of the grids still in white are the signal holes.
The algorithm code is given below:
| Algorithm 1 Signal hole detection. |
-
Require: GM[][]←SplitnetworkintosmallgridsN*NGM[][]←SplitnetworkintosmallgridsN*N
-
for i=1: N do
-
for j=1: N do
-
GM[i][j] = White
-
end for
-
end for
-
for i=1: NoofSensor do
-
for j=1:NoofAP do
-
if error_deviation(AP)<thresholderror_deviation(AP)<threshold then
-
for X=1: N do
-
for Y=1: N do
-
if Grid(X,Y)isindirectionofAP,sensor(i)Grid(X,Y)isindirectionofAP,sensor(i) then
-
GM(X,Y)←grayGM(X,Y)←gray
-
end if
-
end for
-
end for
-
end if
-
end for
-
end for
|
Error in the estimated attack area is calculated by Equation (
40).
Error in the estimated attack area is calculated by Equation (
40).
where:
nGActnGAct is the No. of gray squares actually in the attack area;
nGFnGF is the No. of gray squares estimated in the attack area.
6. Performance Analysis
We simulate the proposed solution by using MATLAB. The simulation area consists of a 1000 × 1000 m two-dimensional terrain. The optimal number and placement of the anchor (AP) is important. We assume a small, but reasonable beacon node population of 20 beacon nodes (approximately five beacons in each direction), which are scattered uniformly over the 1000 m × 1000 m areas. We place a maximum of 10 barriers of a length of 1 m and a width of 1 m randomly in the network. The barriers can cause signal strength degradation and have a severe effect on the RSS. This section presents the performance evaluation of the localization accuracy for both of the proposed solutions SF-MFMPL and C-MFMPL in the face of the log-normal shadow fading environment. shows the system model specification.
Table 1. System model specifications.
It is essential for an examination to assess all outline and advancement works with respect to the research goals. In this way, the performance evaluation is given with respect to this issue. The performance evaluation is performed according to two main parts: first, the localization accuracy, which is defined by the average localization error for different parameters of the network system model, as well as different shadow fading propagation models, and the second part is the detection efficiency of the physical signal strength attacks, which is performed according to the detected area of attacks error.
The average localization error has been achieved according to two cases:
Case I: path loss exponent α = 3, standard deviation of the log-normal shadow fading σ = 5 dB;
Case II: path loss exponent α = 4, standard deviation of the log-normal shadow fading σ = 6 dB.
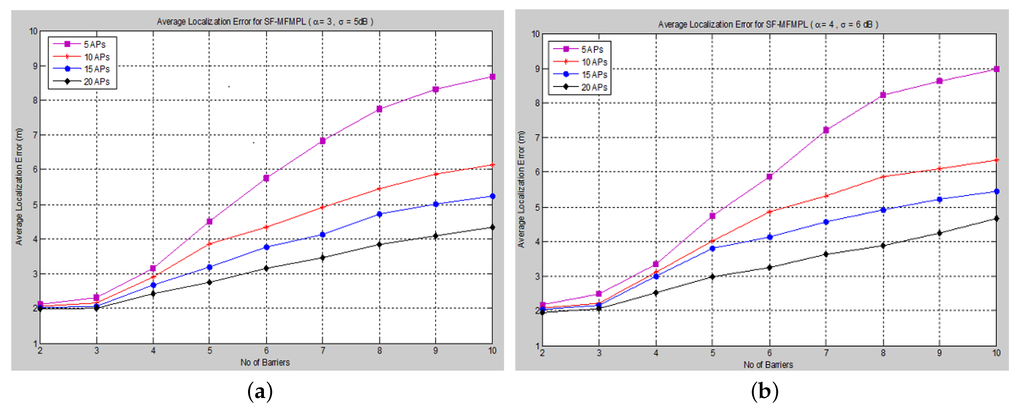
Figure 6. Average localization error versus the number of barriers for the step function multi-frequency multi-power localization (SF-MFMPL) algorithm. (a) Lateration technique Case I; (b) Lateration technique Case II.
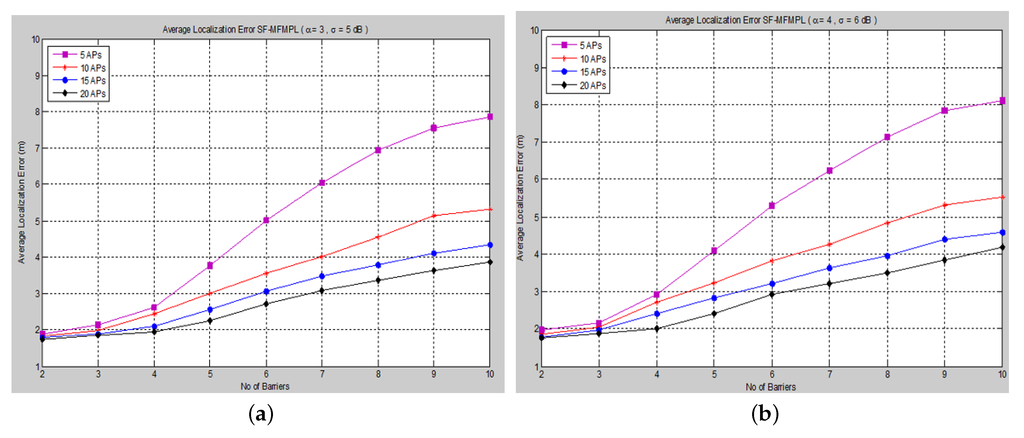
The average localization error is calculated between the actual and the estimated locations for all sensor nodes. The performance is measured in terms of average localization error by varying the number of barriers in the network for different numbers of APs and for both propagation system model cases. and show the average localization error for the (SF-MFMPL) specified by the lateration and trilateration method, respectively.
Figure 7. Average localization error versus the number of barriers for the SF-MFMPL algorithm. (a) Trilateration technique Case I; (b) Trilateration technique Case II.
It is surely understood that expanding the density of anchor nodes accordingly improves localization. However, increasing the number of anchor nodes may not be a feasible solution due to the extra hardware requirements, which may be more expensive.
The simulation results in and show an efficient localization accuracy with respect to the few and reasonable number of anchor nodes that have been applied.
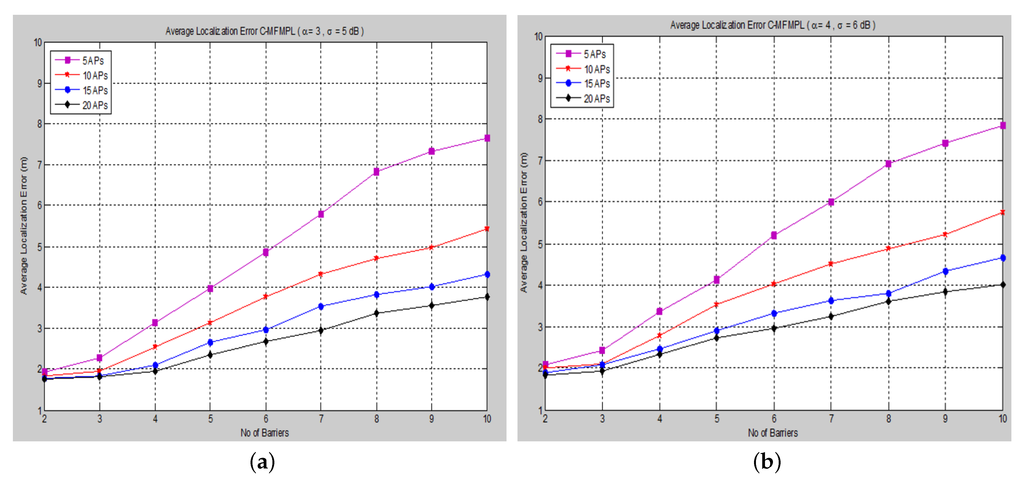
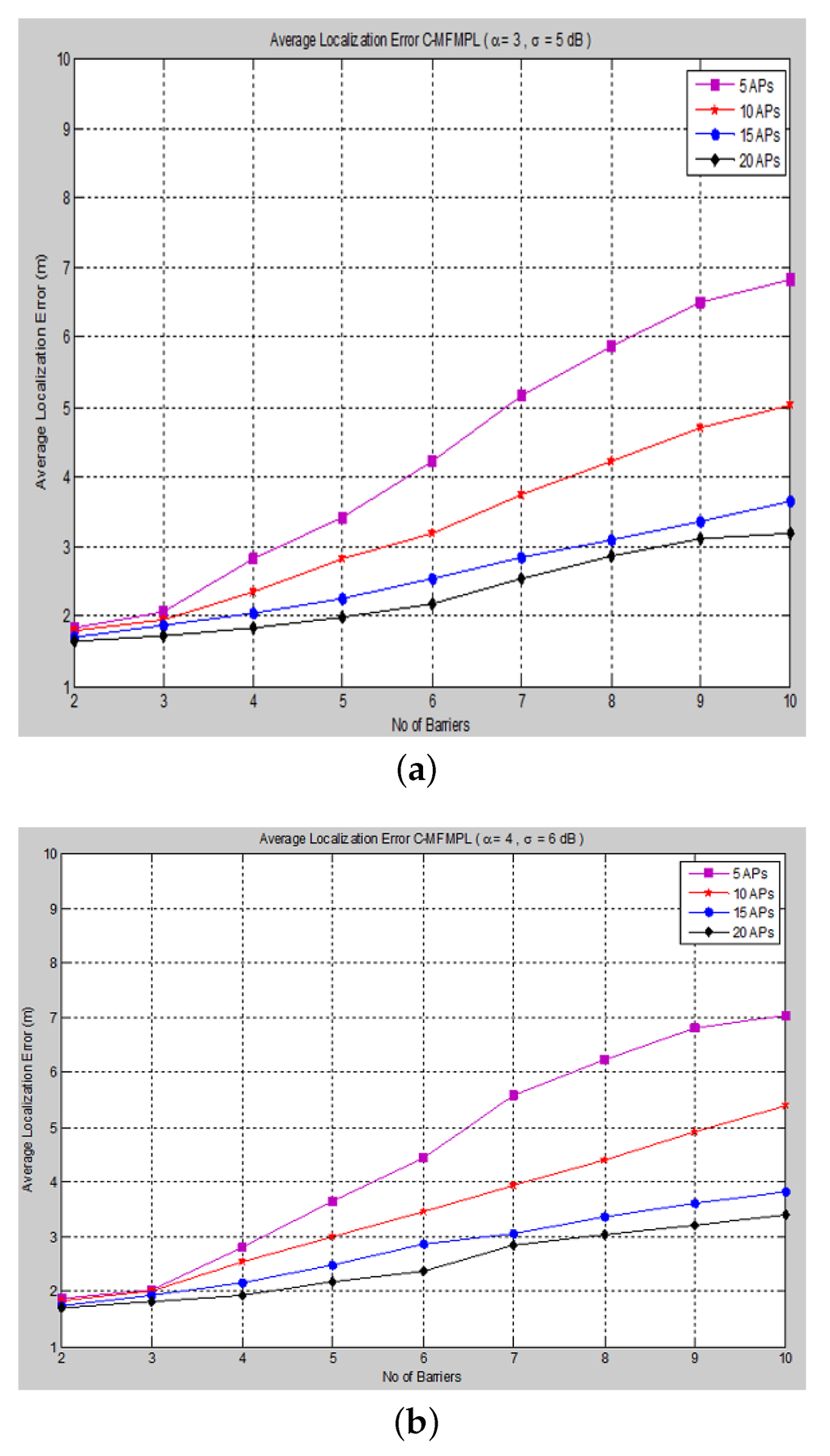
Moreover, and show the average localization error for the (C-MFMPL) specified by the lateration and trilateration methods, respectively.
Figure 8. Average localization error versus the number of barriers for the combination of multi-frequency multi-power localization (C-MFMPL) algorithm. (a) Lateration technique Case I; (b) Lateration technique Case II.
From the simulation results, we observe that the number of anchors (APs) is a significant factor and plays a key role affecting the localization accuracy. Hence, in our approach, the increasing of the number of the anchors (APs) for the system model will lead to reducing the localization error very rapidly, because the number of variables used in non-linear regression increases, as well. On the other hand, utilizing the trilateration technique enhances the performance of the localization clearly, as compared to the performance based on lateration.
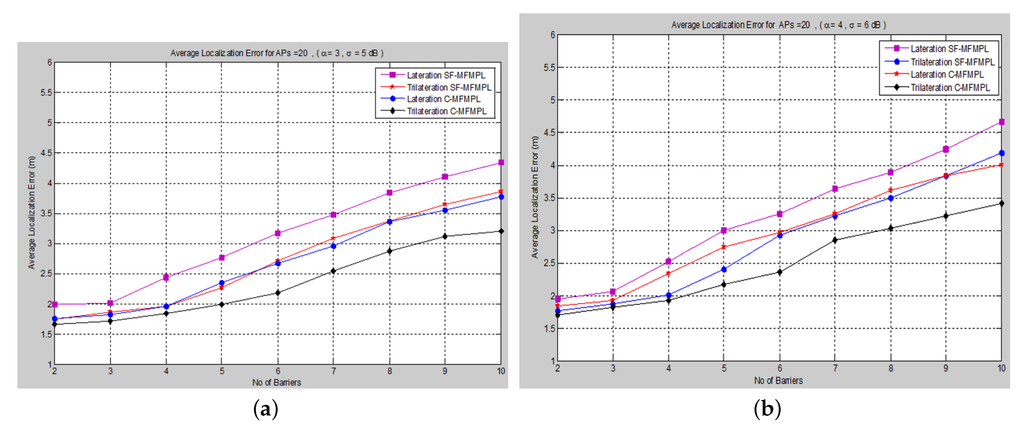
A comparison of the average localization error for both the (SF-MFMPL) and (C-MFMPL) algorithms according to 20 anchors (APs) and two propagation model cases is shown in .
With regards to the simulation results above, we observe that for the localization accuracy identified by the average localization error for both proposed solutions, C-MFMPL is better than the proposed solution based on SF-MFMPL in both cases of the shadow fading propagation model, as well as the lateration and trilateration techniques. This is due to different strategies of using multi-frequency and multi-power for the two algorithms. Meanwhile, the propagation parameters α and σ are clearly subject to and depend on the transmission frequency and power level. In (SF-MFMPL), each power level is indicated by a specific transmitted frequency, while in (C-MFMPL), a combination of multiple frequencies and power levels has been indicated. Hence, the difference in the two algorithms’ strategies will lead to different results in the face of the impact of shadow fading. In addition, simulation results of the trilateration technique showed the best performance for both proposed solutions and under various simulation conditions. illustrates a comparison summary of the average localization error for the two proposed solutions according to 20 anchors (APs) and two propagation model cases.
Figure 9. Average localization error versus the number of barriers for the C-MFMPL algorithm. (a) Trilateration technique Case I; (b) Trilateration technique Case II.
Figure 10. A comparison of the average localization error for both algorithms, (SF-MFMPL) and (C-MFMPL), respectively. (a) Case I; (b) Case II.
Table 2. Average localization error comparison of the two proposed solutions according to 20 anchors (APs) and two propagation model cases.
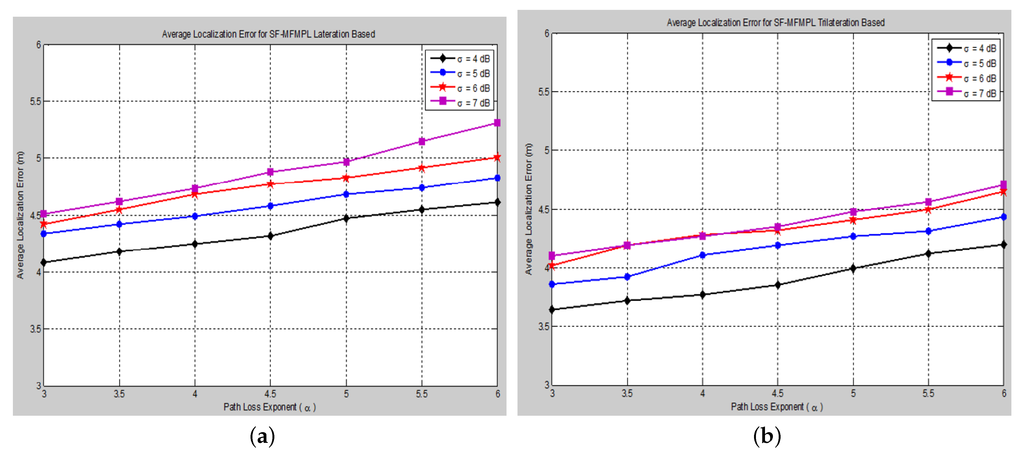
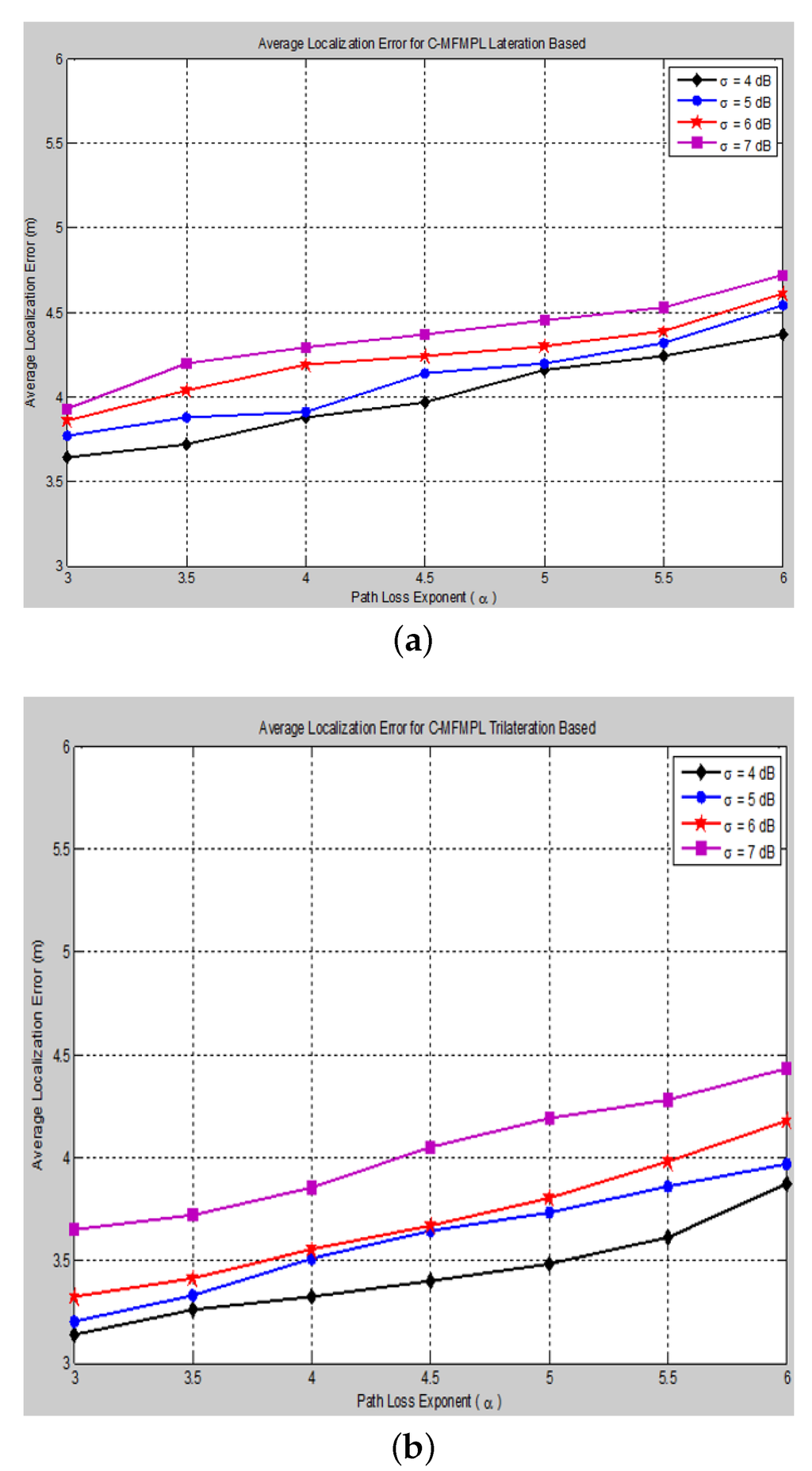
The effect of changing the path loss exponent (α) on the average localization error with respect to different values of the log-normal shadow fading standard deviation (σ) has been taken into consideration of the simulation analysis for both proposed algorithms, (SF-MFMPL) and (C-MFMPL), as shown in and , respectively.
Figure 11. Average localization error versus different path loss exponent values for the SF-MFMPL algorithm (No. of barriers = 10, APs = 20). (a) Lateration technique based; (b) Trilateration technique based.
Figure 12. Average localization error versus different path loss exponent values for the C-MFMPL algorithm (No. of barriers = 10, APs 20). (a) Lateration technique based; (b) Trilateration technique based.
In practice, the shadow fading propagation model parameters are unpredictable; therefore, it will be susceptible to errors; therefore, we considered the influence of changing the propagation model parameters identified by the path loss exponent and the standard deviation on the localization accuracy for both of our proposed solutions. As illustrated in the figures above, our proposed algorithms showed an efficient and accurate performance for the estimation of the sensor nodes’ positions with an acceptable localization error. In addition, the proposed solution based on (C-MFMPL) has a better performance than the (SF-MFMPL) solution in both cases of lateration and trilateration. and indicate a comparison of the performance evaluation for our proposed solutions with respect to the changing of the shadow fading propagation parameters based on the lateration and trilateration techniques, respectively.
Table 3. Average localization error comparison of the two proposed solutions according to changing the shadow fading propagation parameters (lateration based).
Table 4. Average localization error comparison of the two proposed solutions according to changing the shadow fading propagation parameters (trilateration based).
The other cause of localization error arises due to the anchor node’s position. We considered the effect of the anchor node’s positions on localization accuracy. Hence, the anchor node’s placement and geometry have a crucial role to play with respect to localization performance. The average localization error for the random anchor placement configuration is measured for both the (SF-MFMPL) and (C-MFMPL) algorithms, respectively, as illustrated in .
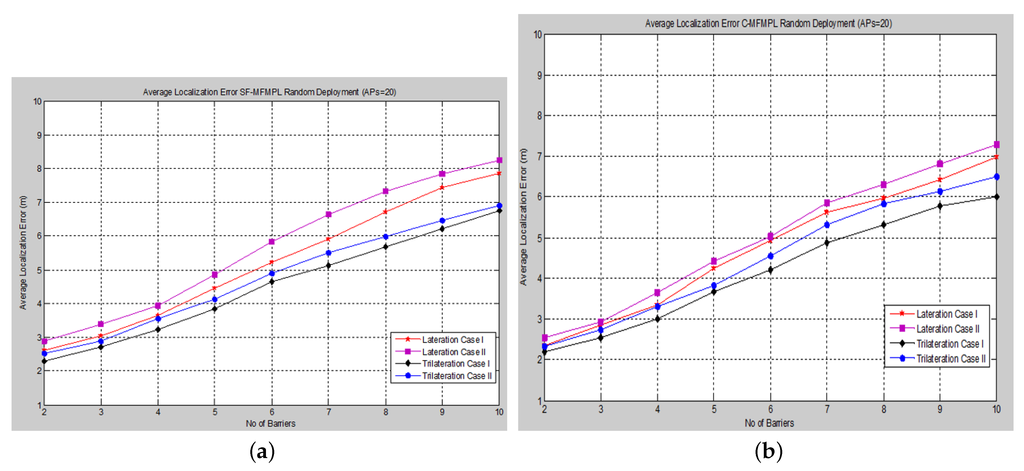
Figure 13. Localization error versus the number of barriers for a random placement configuration of APs. (a) SF-MFMPL; (b) C-MFMPL.
According to the simulation results above, it is clearly observed that the localization accuracy in the case of the random deployment of the anchor nodes (APs) drops slightly with respect to the increase of the number of barriers in the network. However, the average localization error for this case is still within the acceptable error range regarding the RSSI-based localization technique.
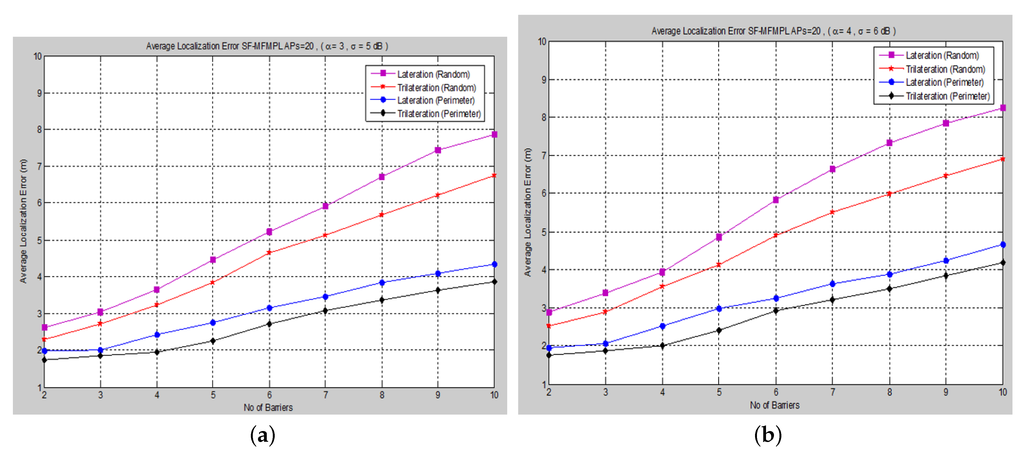
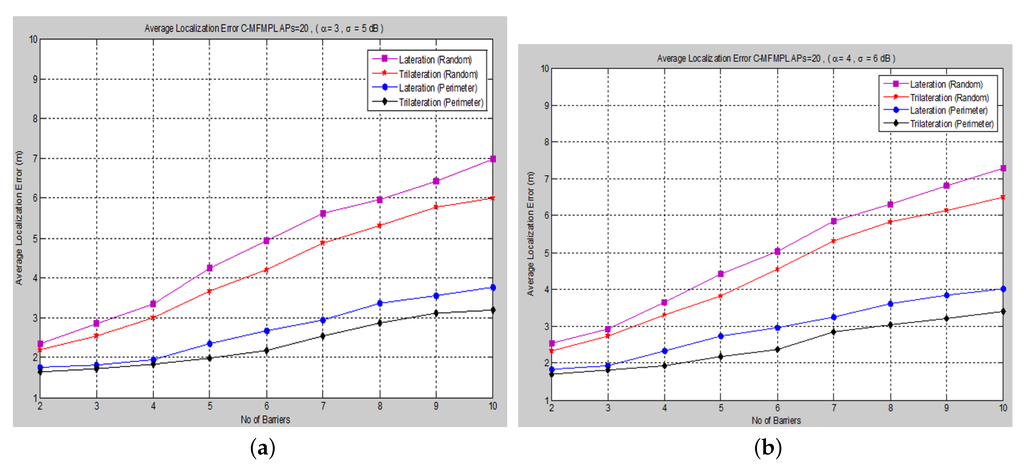
Proper positioning of anchor nodes is necessary for the effective localization accuracy of wireless sensor networks. Since the performance of the localization accuracy depends on the placement of the anchors (APs) in the network. The performance analysis in such an environment has been compared among various anchor (AP) deployment mechanisms; and illustrate the performance evaluation for a uniform, around the perimeter and random deployment mechanism and for both algorithms, (SF-MFMPL) and (C-MFMPL), respectively.
Figure 14. Localization error versus the number of barriers for SF-MFMPL with a random, around the perimeter placement configuration of APs. (a) Case I; (b) Case II.
Figure 15. Localization error versus the number of barriers for C-MFMPL with a random, around the perimeter placement configuration of APs. (a) Case I; (b) Case II.
In accordance with the simulation results above, we have indicated the impact of the anchor node deployment, and it is clearly affected by the localization performance. A comparison of the performance evaluation for both proposed solutions, SF-MFMPL and C-MFMPL, under the two cases of the anchor node (AP) deployment mechanisms has been summarized in and .
Table 5. Average localization error comparison of the SF-MFMPL proposed solution according to the anchor node deployment configuration.
Table 6. Average localization error comparison of the C-MFMPL proposed solution according to the anchor node deployment configuration.
According to the simulation results stated in and , the localization performance of the uniform, around the perimeter deployment of the anchor nodes is better than the random deployment, as well as being the optimal placement configuration for an effective localization accuracy. In addition, the proposed algorithm C-MFMPL showed a better performance than the SF-MFMPL algorithm for both the lateration and the trilateration technique.
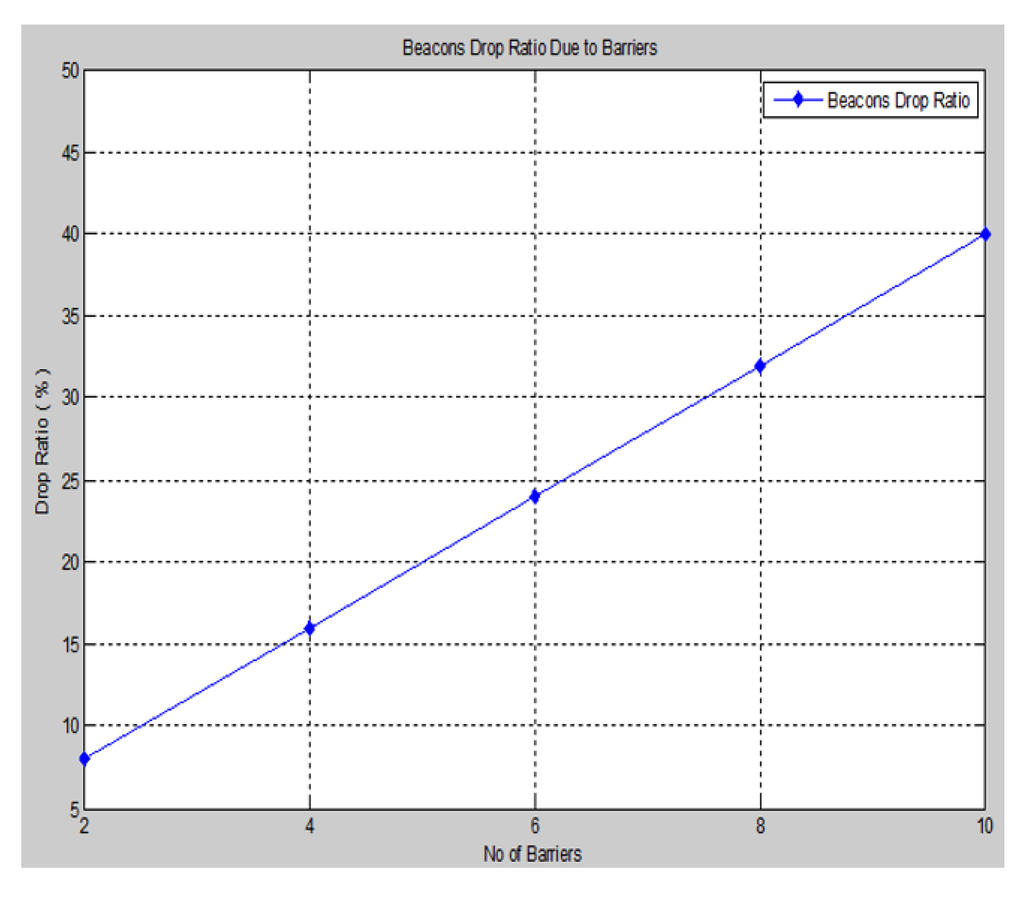
Figure 16. Invalid beacon drop ratio vs. No. of barriers.
Another important metric that indicates the effect of the barrier attack on the localization performance is the percentage of the invalid beacon drop ration due to the barrier attenuation of the signal with respect of the total percentage of available beacons for the proposed system, as shown in .
We observe from the figure above that as the number of barriers increases, a greater number of invalid beacons will appear in the network, and drop ratio is increased, as well. In spite of the 40% invalid beacon drop rate from the case of 10 barriers, the performance of our proposed approach is still accurate and contributes to a lesser localization error.
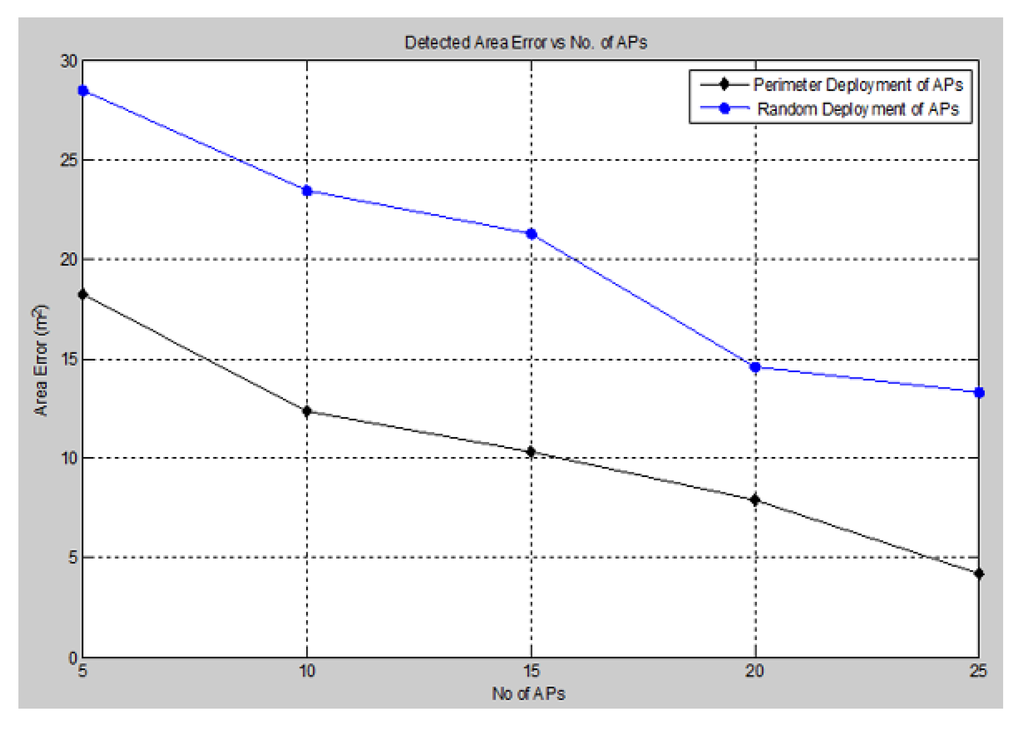
One of the most significant performance evaluation criteria is the accuracy of the detected area of attack. This accuracy is measured in terms of the difference between the actual area occupied by the barrier and the detected area of the signal holes. We varied the number of anchors (APs), as well as the deployment configuration in order to determine the optimum placement positions for the detection mechanism. The accuracy of the detected area of attack is illustrated in .
Figure 17. Detected area error vs. No. of APs.
Based on the simulation results above, we observe that as the number of anchors (APs) increases, the detected area error reduces greatly, as well as the optimum placement configuration of anchors (APs) around the perimeter showed more accurate performance through identifying the attack area with great precision.
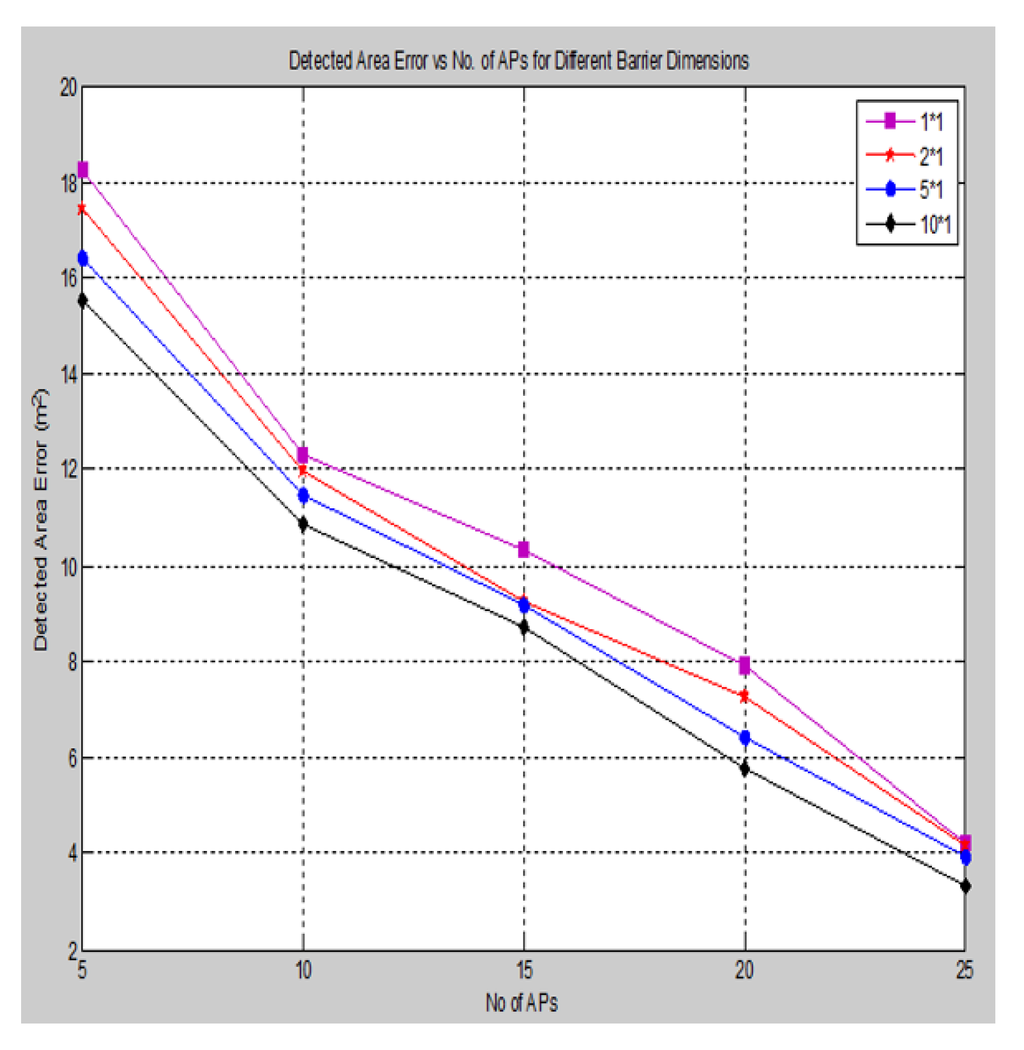
The accuracy of detecting the area of attack also depends on the shape and dimension of the barrier attack that is introduced into the network. We introduced a rectangular barrier of various dimensions and measured the accuracy of the detected area of attack, as shown in .
Figure 18. Detected area error for different barrier dimensions.
In accordance with the simulation results above, initially, when the barrier size increases, the error in the detected area of attack is decreased gradually with respect to the increasing of the anchors (APs); this is due to more beacon signals being affected by these barriers with more RSS error deviations having been neglected, so that there is more information available for detecting the area of attack. On the other hand, increasing the barrier size will lead to increasing the localization error slightly.