Represented by reactive security defense mechanisms, cyber defense possesses a static, reactive, and deterministic nature, with overwhelmingly high costs to defend against ever-changing attackers. To change this situation, researchers have proposed moving target defense (MTD), which introduces the concept of an attack surface to define cyber defense in a brand-new manner, aiming to provide a dynamic, continuous, and proactive defense mechanism. With the increasing use of machine learning in networking, researchers have discovered that MTD techniques based on machine learning can provide omni-bearing defense capabilities and reduce defense costs at multiple levels.
- moving target defense
- cyber security
- affordable defense
- self-adaptive defense
1. Background
-
Traditional defenses aim to enhance the defense capabilities of static facilities and minimize their vulnerabilities’ exposure. In contrast, MTD concentrates on dynamically shifting the attack surface [1] to increase resilience.
-
Traditional defenses often focus on monitoring, detecting, preventing, and remediating attacks on static infrastructure. MTD emphasizes faster and more comprehensive attack detection and timely responses to mitigate potential damages.
-
Traditional defenses rely on known attack patterns for defense and may be limited in addressing emerging or novel threats. MTD seeks to proactively address such unpredictable attacks through its dynamic nature.
-
Unlike traditional defense mechanisms, which operate in a fixed dimension, MTD adapts and changes constantly to protect against attacks on ever-changing systems. This approach significantly limits attackers’ research time and ability to penetrate compromised systems.
-
Minimizing defense costs (e.g., system deployment overhead)
-
Maximizing service availability for users
-
Maintaining the required defense security levels
2. Design and Classification
2.1. What to Move
| The Attack Surfaces Often Utilized in Recent Years (Since ′18) | ||
|---|---|---|
| Network L. | ❏IP address/Port [2][3][4][5][6][7][8][9][10][11][12][13][14] | ❏Route/Network topology [15][16][17][18][19] |
| Platform L. | ❏Virtual Machines [20][21][22][23][24] | ❏Proxies [25] |
| Rt. Env. L. | ❏Operation Systems [26][27][28] | |
| Software L. | ❏Software [29][30][31][32][33] | |
| Data L. | ❏Instruction sets [34][35] | ❏Codes [36][37] |
2.2. How to Move
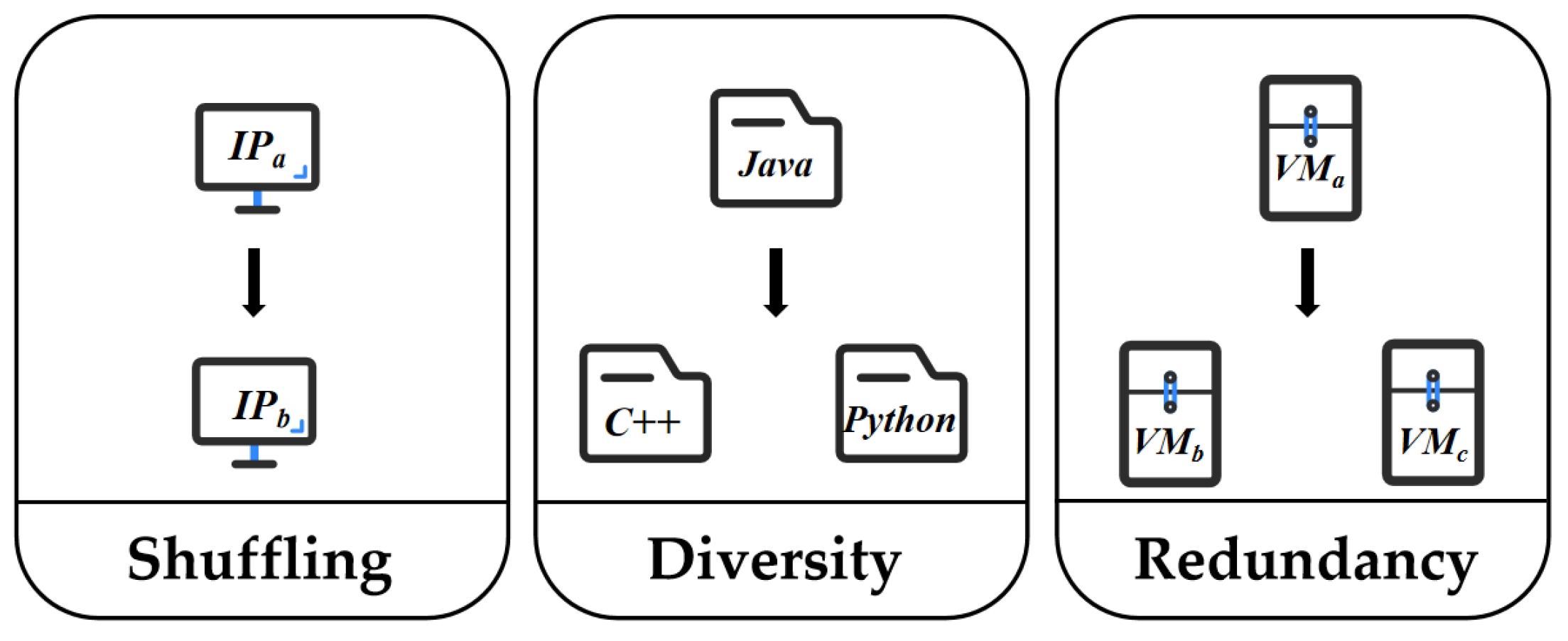
-
Shuffling
-
Diversity
-
Redundancy
-
Hybrid
2.3. When to Move
-
Fixed-time triggering: MTD techniques periodically shift the attack surface at fixed intervals. Setting the triggering interval requires a technique-specific analysis, but for each technique, researchers need to find the right triggering point. If the interval is too long, attackers have enough time to penetrate the system and launch an attack. If it is too short, the MTD mechanism is triggered frequently, leading to wasted resources and degraded performance. Additionally, frequent triggering of MTD can significantly degrade the QoS and users’ experience.
-
Ad hoc event triggering: MTD shifts the attack surface when the system detects an attacker’s access or a precursor to an attack. Self-adaptive MTD adopts this approach, and its main challenge is accurately predicting attacks that can trigger MTD effectively.
3. Development Trends and Challenges for Existing MTD Techniques
3.1. Systematic Development
3.2. Integration with Existing Security Defense Mechanisms
3.3. Combination with New Techniques
-
SDN-based MTD
-
MTD-applied cloud computing
3.4. Challenges for Existing MTD Techniques
-
Large resource consumption and high defense costs.
-
For example, in the face of the attacker’s scanning, the existing MTD’s countermeasure is to perform IP hopping when scanning behavior is detected, and their representative techniques include but are not limited to OF-RHM [2], SEHT [3], DDS [4], and NATD [5]. Their common problem is a lack of accuracy and efficiency in identifying attack manners, the waste of resources caused by untargeted hops, and a lack of integration with the affordable defense pursued by MTD.
-
They have an incapability of balancing multi-constraints (e.g., costs, security performance, and service availability).
-
For instance, routing randomization has been proven to be an effective method against eavesdropping attacks. Currently, representative routing randomization techniques include but are not limited to: RRM [44], AE-RRM [41], AT-RRM [45], and SSO-RM [46]. However, RRM and AE-RRM implement random transformations only on the routes of data transmission between nodes, without considering different attack behaviors and protecting network QoS under such circumstances. As for AT-RRM and SSO-RM, they can dynamically adjust transformation strategies to some extent, but their protection effectiveness for QoS is still unsatisfactory, and they fail to consider the varying demands of different applications for latency and bandwidth. Besides, all of their packets’ granularity is too coarse, making it easy for attackers to intercept continuous data packets and render the defense ineffective.
-
Relatively fixed defense strategies (easy to be reconnoitered and recognized by attackers).
This entry is adapted from the peer-reviewed paper 10.3390/app13095367
References
- Okhravi, H.; Rabe, M.; Leonard, W.; Hobson, T.; Bigelow; Streilein, W. Survey of Cyber Moving Targets; Technical Report, 1166; MIT Lincoln Laboratory: Lexington, MA, USA, 2013.
- Jafarian, J.H.; Al-Shaer, E.; Duan, Q. Openflow Random Host Mutation: Transparent Moving Target Defense Using Software Defined Networking. In Proceedings of the First Workshop on Hot Topics in Software Defined Networks, New York, NY, USA, 13 August 2012; pp. 127–132.
- Lei, C.; Zhang, H.; Ma, D.; Yang, Y. Network Moving Target Defense Technique Based on Self-Adaptive End-Point Hopping. Arab. J. Sci. Eng. 2017, 42, 3249–3262.
- Miao, L.; Hu, H.; Cheng, G. The Design and Implementation of a Dynamic IP Defense System Accelerated by Vector Packet Processing. In Proceedings of the International Conference on Industrial Control Network and System Engineering Research, New York, NY, USA, 15–16 March 2019; pp. 64–69.
- Smith, R.J.; Zincir-Heywood, A.N.; Heywood, M.I.; Jacobs, J.T. Initiating a Moving Target Cyber Defense with a Real-Time Neuro-Evolutionary Detector. In Proceedings of the 2016 on Genetic and Evolutionary Computation Conference Companion, New York, NY, USA, 20–24 July 2016; pp. 1095–1102.
- Al-Shaer, E.; Duan, Q.; Jafarian, J.H. Random host mutation for moving target defense. In Security and Privacy in Communication Networks, 8th International ICST Conference, SecureComm 2012, Padua, Italy, 3–5 September 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 106.
- Antonatos, S.; Akritidis, P.; Markatos, E.P.; Anagnostakis, K.G. Defending against Hitlist Worms Using Network Address Space Randomization. In Proceedings of the 2005 ACM Workshop on Rapid Malcode, Computer Networks, New York, NY, USA, 11 November 2005; pp. 3471–3490.
- Kewley, D.; Fink, R.; Lowry, J.; Dean, M. Dynamic Approaches to Thwart Adversary Intelligence Gathering. In Proceedings of the DARPA Information Survivability Conference and exposition II (DISCEX), Anaheim, CA, USA, 12–14 June 2001; Volume 1, pp. 176–185.
- Sharma, D.P.; Kim, D.S.; Yoon, S.; Lim, H.; Cho, J.; Moore, T.J. FRVM: Flexible Random Virtual IP Multiplexing in Software-Defined Networks. In Proceedings of the IEEE TrustCom, New York, NY, USA, 1–3 August 2018; pp. 579–587.
- Xu, X.; Hu, H.; Liu, Y.; Zhang, H.; Chang, D. An Adaptive IP Hopping Approach for Moving Target Defense Using a Light-Weight CNN Detector. Secur. Commun. Netw. 2021, 2021, 8848473.
- Luo, Y.B.; Wang, B.S.; Wang, X.F.; Hu, X.F.; Cai, G.L.; Sun, H. RPAH: Random Port and Address Hopping for Thwarting Internal and External Adversaries. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; pp. 263–270.
- Carroll, T.E.; Crouse, M.; Fulp, E.W.; Berenhaut, K.S. Analysis of Network Address Shuffling as a Moving Target Defense. In Proceedings of the IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 701–706.
- MacFarland, D.C.; Shue, C.A. The SDN shuffle: Creating a Moving-Target Defense Using Host-Based Software-Defined Networking. In Proceedings of the 2nd ACM Workshop on Moving Target Defense (MTD), Denver, CO, USA, 12 October 2015; pp. 37–41.
- Kampanakis, P.; Perros, H.; Beyene, T. SDN-Based Solutions for Moving Target Defense Network Protection. In Proceedings of the IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), Sydney, NSW, Australia, 19 June 2014; pp. 1–6.
- Achleitner, S.; Porta, T.L.; McDaniel, P.; Sugrim, S.; Krishnamurthy, S.V.; Chadha, R. Deceiving network reconnaissance using SDN-based virtual topologies. IEEE Trans. Netw. Serv. Manag. 2017, 14, 1098–1112.
- Achleitner, S.; La Porta, T.; McDaniel, P.; Sugrim, S.; Krishnamurthy, S.V.; Chadha, R. Cyber Deception: Virtual Networks to Defend Insider Reconnaissance. In Proceedings of the 8th ACM CCS International Workshop on Managing Insider Security Threats, New York, NY, USA, 28 October 2016; pp. 57–68.
- Hong, J.B.; Yoon, S.; Lim, H.; Kim, D.S. Optimized Network Reconfiguration for Software Defined Networks Using Shuffle-Based Online MTD. In Proceedings of the IEEE Symposium on Reliable Distributed Systems (SRDS), Hong Kong, China, 26–29 September 2017.
- Xu, X.; Hu, H.; Liu, Y.; Tan, J.; Zhang, H.; Song, H. Moving target defense of routing randomization with deep reinforcement learning against eavesdropping attack. Digit. Commun. Netw. 2022, 8, 373–387.
- Trassare, S.T.; Beverly, R.; Alderson, D. A Technique for Network Topology Deception. In Proceedings of the MILCOM 2013—2013 IEEE Military Communications Conference, San Diego, CA, USA, 18–20 November 2013; pp. 1795–1800.
- Hong, J.B.; Enoch, S.Y.; Kim, D.S.; Nhlabatsi, A.; Fetais, N.; Khan, K.M. Dynamic security metrics for measuring the effectiveness of moving target defense techniques. Comput. Secur. 2018, 79, 33–52.
- Danev, B.; Masti, R.; Karame, G.; Capkun, S. Enabling Secure VM-vTPM Migration in Private Clouds. In Proceedings of the 27th Annual Computer Security Applications Conference (ACSAC), New York, NY, USA, 5–9 December 2011; pp. 187–196.
- Zhang, Y.; Li, M.; Bai, K.; Yu, M.; Zang, W. Incentive Compatible Moving Target Defense against VM-Colocation Attacks in Clouds. In Proceedings of the IFIP International Information Security Conference, Heraklion, Greece, 4–6 June 2012; pp. 388–399.
- Penner, T.; Guirguis, M. Combating the Bandits in the Cloud: A Moving Target Defense Approach. In Proceedings of the 17th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, Madrid, Spain, 14–17 May 2017; pp. 411–420.
- Peng, W.; Li, F.; Huang, C.-T.; Zou, X. A Moving Target Defense Strategy for Cloud-Based Services with Heterogeneous and Dynamic Attack Surfaces. In Proceedings of the IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 804–809.
- Jia, Q.; Sun, K.; Stavrou, A. Motag: Moving Target Defense against Internet Denial of Service Attacks. In Proceedings of the 22nd International Conference on Computer Communications and Networks (ICCCN), Nassau, Bahamas, 30 July–2 August 2013; pp. 1–9.
- Thompson, M.; Evans, N.; Kisekka, V. Multiple OS Rotational Environment an Implemented Moving Target Defense. In Proceedings of the 2014 7th International Symposium on Resilient Control Systems (ISRCS), Denver, CO, USA, 19–21 August 2014; pp. 1–6.
- Colbaugh, R.; Glass, K. Predictability-Oriented Defense against Adaptive Adversaries. In Proceedings of the 2012 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Seoul, Republic of Korea, 14–17 October 2012; pp. 2721–2727.
- Huang, Y.; Ghosh, A.K.; Bracewell, T.; Mastropietro, B. A Security Evaluation of a Novel Resilient Web Serving Architecture: Lessons Learned Through Industry/Academia Collaboration. In Proceedings of the IEEE/IFIP International Conference on Dependable Systems and Networks Workshops (DSN-W), Chicago, IL, USA, 28 June–1 July 2010; pp. 188–193.
- Jackson, T.; Salamat, B.; Homescu, A.; Manivannan, K.; Wagner, G.; Gal, A.; Brunthaler, S.; Wimmer, C.; Franz, M. Compiler-generated software diversity. In Moving Target Defense; Springer: Berlin/Heidelberg, Germany, 2011; pp. 77–98.
- Vikram, S.; Yang, C.; Gu, G. Nomad: Towards Nonintrusive Moving-Target Defense against Web Bots. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 55–63.
- Casola, V.; Benedictis, A.D.; Albanese, M. A Moving Target Defense Approach for Protecting Resource-Constrained Distributed Devices. In Proceedings of the IEEE 14th International Conference on Information Reuse Integration (IRI), San Francisco, CA, USA, 14–16 August 2013; pp. 22–29.
- Yuan, E.; Malek, S.; Schmerl, B.; Garlan, D.; Gennari, J. Architecture-Based Self-Protecting Software Systems. In Proceedings of the 9th International ACM SIGSOFT Conference on Quality of Software Architectures, New York, NY, USA, 17–21 June 2013; pp. 33–42.
- Larsen, P.; Homescu, A.; Brunthaler, S.; Franz, M. SoK: Automated Software Diversity. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; pp. 276–291.
- Kc, G.S.; Keromytis, A.D.; Prevelakis, V. Countering Code-Injection Attacks with Instruction-Set Randomization. In Proceedings of the 10th ACM Conference on Computer and Communications Security (CCS), New York, NY, USA, 27–30 October 2003; pp. 272–280.
- Portokalidis, G.; Keromytis, A.D. Global ISR: Toward a Comprehensive Defense against Unauthorized Code Execution. In Moving Target Defense: Creating Asymmetric Uncertainty for Cyber Threats; Springer: New York, NY, USA, 2011; pp. 49–76.
- Azab, M.; Hassan, R.; Eltoweissy, M. Chameleonsoft: A Moving Target Defense System. In Proceedings of the 7th International Conference on Collaborative Computing: Networking, Applications and Worksharing (CollaborateCom), Orlando, FL, USA, 15–18 October 2011; pp. 241–250.
- Kohli, T. An Efficient Threat Detection Framework for Docker Containers using AppArmor Profile and Clair Vulnerability Scanning Tool. Master’s Thesis, National College of Ireland, Dublin, Ireland, 2022.
- Cho, J.-H.; Yoon, S.; Kim, D.S. Toward Proactive, Adaptive Defense: A Survey on Moving Target Defense. IEEE Commun. Surv. Tutor. 2020, 22, 709–745.
- Lei, C.; Zhang, H.-Q.; Tan, J.-L.; Zhang, Y.-C.; Liu, X.-H. Moving target defense techniques: A survey. Secur. Commun. Netw. 2018, 3759626.
- Debroy, S.; Calyam, P.; Nguyen, M.; Neupane, R.L.; Mukherjee, B.; Eeralla, A.K.; Salah, K. Frequency-minimal utility-maximal moving target defense against DDoS in SDN-based systems. IEEE Trans. Netw. Serv. Manag. 2020, 17, 890–903.
- Aseeri, A.; Netjinda, N.; Hewett, R. Alleviating Eavesdropping Attacks in Software-Defined Networking Data Plane. In Proceedings of the 12th Annual Conference on Cyber and Information Security Research, New York, NY, USA, 4–6 April 2017; pp. 1–8.
- Li, Y.; Dai, R.; Zhang, J. Morphing Communications of Cyber-Physical Systems Towards Moving-Target Defense. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 592–598.
- Torquato, M.; Vieira, M. Moving target defense in cloud computing: A systematic mapping study. Comput. Secur. 2020, 92, 101742.
- Duan, Q.; Al-Shaer, E.; Jafarian, H. Efficient Random Route Mutation Considering Flow and Network Constraints. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013; pp. 260–268.
- Liu, J.; Zhang, H.; Guo, Z. A defense mechanism of random routing mutation in SDN. IEICE Trans. Inf. Syst. 2017, 100, 1046–1054.
- Zhou, Z.; Xu, C.; Kuang, X. An Efficient and Agile Spatio-Temporal Route Mutation Moving Target Defense Mechanism. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6.
- Ganz, J.; Peisert, S. ASLR: How Robust Is the Randomness? In Proceedings of the 2017 IEEE Cybersecurity Development (SecDev), Cambridge, MA, USA, 24–26 September 2017; pp. 34–41.
- Bittau, A.; Belay, A.; Mashtizadeh, A.; Mazières, D.; Boneh, D. Hacking Blind. In Proceedings of the 2014 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 18–21 May 2014; pp. 227–242.
