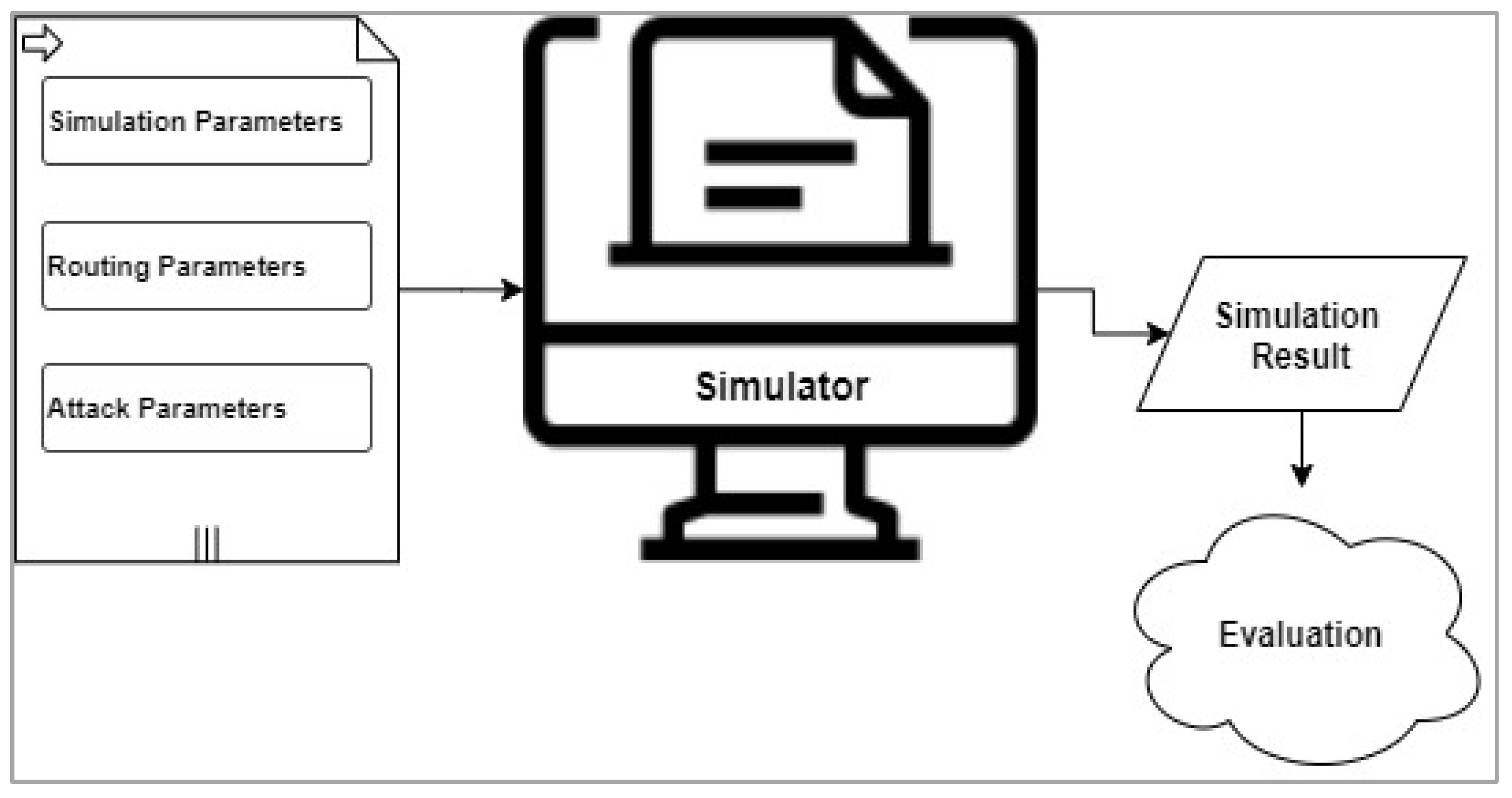
A mobile ad hoc network (MANET) is an infrastructure-less network where mobile nodes can share information through wireless links without dedicated hardware that handles the network routing. MANETs’ nodes create on-the-fly connections with each other to share information, and they frequently join and leave MANET during run time. Therefore, flexibility in MANETs is needed to be able to handle variations in the number of existing network nodes. An effective routing protocol should be used to be able to route data packets within this dynamic network. Lacking centralized infrastructure in MANETs makes it harder to secure communication between network nodes, and this lack of infrastructure makes network nodes vulnerable to harmful attacks. Testbeds might be used to test MANETs under specific conditions, but researchers prefer to use simulators to obtain more flexibility and less cost during MANETs’ environment setup and testing. A MANET’s environment is dependent on the required scenario, and an appropriate choice of the used simulator that fulfills the researcher’s needs is important. Furthermore, researchers need to define the simulation parameters and the other parameters required by the routing protocol used. In addition, if the MANET’s environment handles some conditions where malicious nodes perform network attacks, the parameters affecting the MANET from the attack perspective need to be understood.
- MANET attacks
- MANET configuration parameters
- MANET evaluation
- MANET simulation
- aodv
1. Introduction
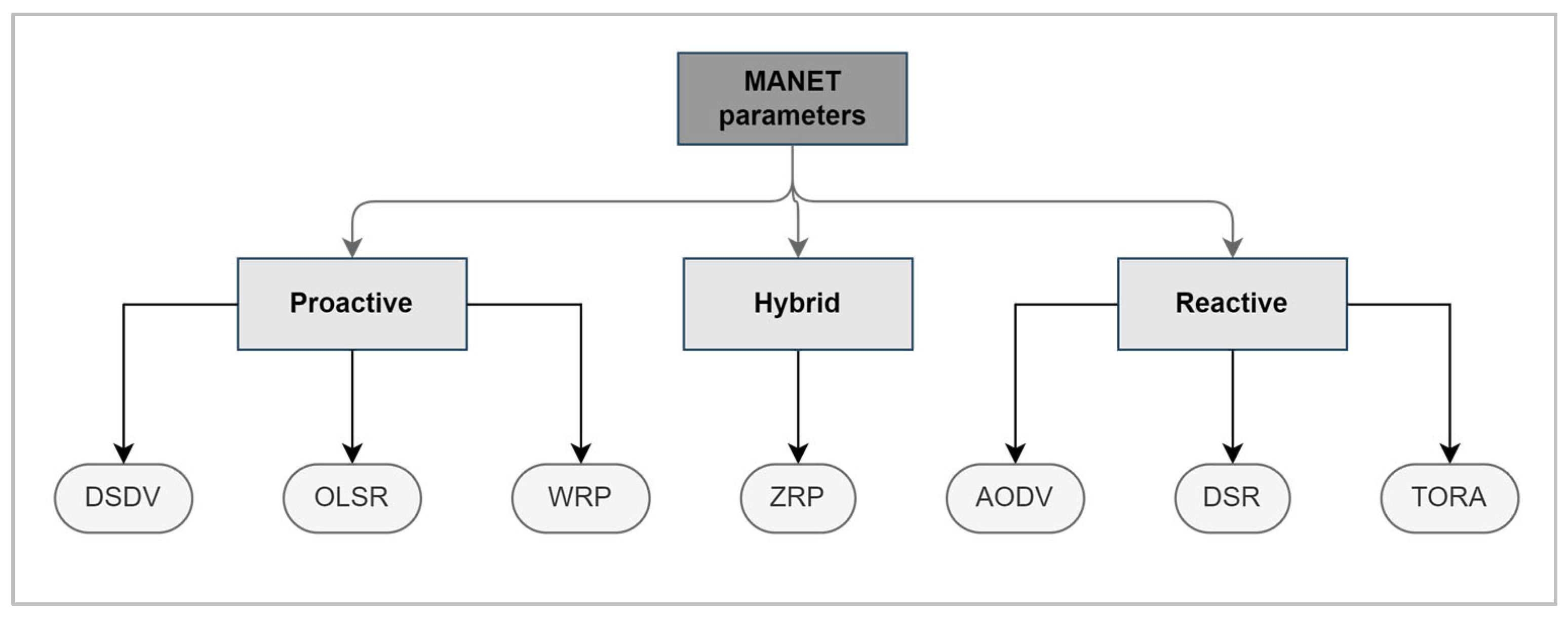
2. Routing in MANETs
-
Proactive routing protocols: For example, OLSR, each node maintains its routing table by periodically updating its information [6]; this increases network overhead. On the other hand, routes will always be available with a minimum delay. Proactive protocols provide better performance than reactive protocols as each node continuously updates its awareness of network changes. When a request is received, the packet forwarding procedure is directly handled.
-
Reactive routing protocols: For example, AODV and DSR, when a source node tries to perform a packet transmission, it initiates a route discovery mechanism to know how to reach the destination. After the route is determined and updated in the routing table, the packet is forwarded [7]. Reactive protocols have minimal network overhead, but there is a delay time consumed in the route discovery.
-
Hybrid routing protocols: For example, ZRP, the close local neighbors to a node are periodically updated, and the global nodes that are not direct neighbors will be updated on demand such as in reactive routing protocols [8].
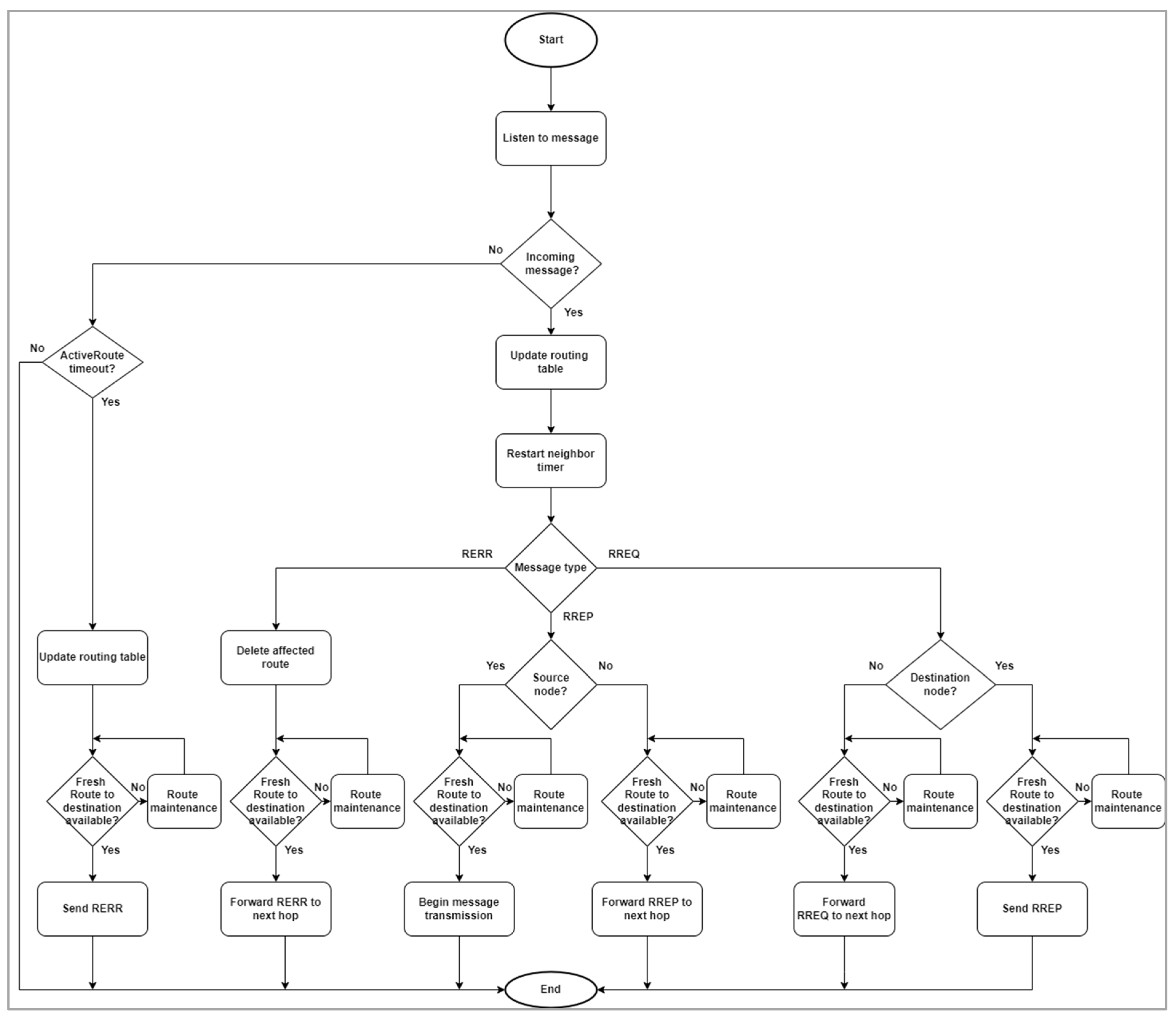
2.1. AODV Routing Protocol
-
Destination node address;
-
Number of hop counts to reach the destination;
-
Intermediate nodes address;
-
Route entry expiry time;
-
Destination node sequence number.
-
Network diameter: The network diameter value sets the maximum number of hop counts between two nodes in MANETs. The network diameter default value is up to thirty-five hops at most as per RFC 3561 standard.
-
Node transversal time: The node transversal time is the estimation of packet transversal time between two neighbor nodes; this estimation should consider the network, processing, and transfer delay time. The default configuration time is 40 ms.
-
Network transversal time: The network transversal time is the expected time between sending the RREQ packet and the reception of the RREP packet as per the equation [14]:
-
Route request retry: If a route reply is not received by the source node within the maximum network transversal time, the source node can retry to request the route discovery again for a maximum route request retry times. If the route discovery exceeds the route request retry times, the destination node should be considered unreachable. The default value for the route request retry parameter is equal to 2 retries.
-
Blacklist timeout: When the RREP transmission from node A to node B fails, node A records node B in its blacklist buffer. During this blocking time, node A discards any RREQ from neighbor node B until the blacklist timeout is reached. After the blacklist timeout expires, node B is removed from the blacklist [14].
-
Route request rate limits: The route request rate limit is the maximum number of RREQ packets for the source node to originate per second. The route request rate limit’s default value is ten packets per second.
-
Active route timeout: The neighbor node is recorded in the routing table and considered an active node when the active route timeout is not exceeded. When a neighbor node is active, the recorded route to this neighbor should be used [15]. The active route timeout default value is 3000 ms.
-
Hello interval: All MANET nodes should reveal their existence in the network within a hello interval time [16]. If a node does not contribute to the routing activities for a hello interval time, it should broadcast a hello message with TTL = 1. Hello interval default value is set to be 1000 ms.
-
Allowed hello loss: If a node does not receive any contribution to routing activities from its direct neighbor node for more than (HelloInterval × AllowedHelloLoss), the node should assume a link failure to this neighbor [17]. The allowed hello loss default value is two link failures.
-
DPC: After the delete period constant time is expired, the expired route will be deleted from the routing table [18]. The default value for DPC is 5 s.
| AODV Parameter | Default Value |
|---|---|
| NetworkDiameter | 35 hops |
| NodeTransversalTime | 40 ms |
| NetworkTransversalTime | 1400 ms |
| RouteRequestRetry | 2 retries |
| BlackListTimeout | 2800 ms |
| RouteRequestRateLimits | 10 packets/s |
| ActiveRouteTimeout | 3000 ms |
| HelloInterval | 1000 ms |
| AllowedHelloLoss | 2 times |
| Delete Period Constant | 5 s |
3. Simulation in MANETs
3.1. MANETs Simulators
| Simulator Name | Languages Supported | Platform Support | License | Advantages | Disadvantages |
|---|---|---|---|---|---|
| OPNET | C, C++ | Windows, Sun Solaris, RedHat Linux | Commercial, Free Educational License |
|
|
| OMNeT++ | C++, NED | Windows, MacOS, and any Unix-like systems | Open source |
|
|
| NS-2 | C++, OTCL | Windows, MacOS, Ubuntu, Sun Solaris, Fedora Linux, and any Unix-like systems | Open source |
|
|
| NS-3 | C++, Python | MacOS, FreeBSD, Linux | Open source |
|
|
| GloMoSim | C, PERSEC | Windows XP/7, FreeBSD, Sun Solaris, Fedora Linux | Free |
|
|
| QualNet and EXATA/cyber | JAVA | Windows NT/2000/XP/Professional, macOS, Sun Solaris, and most Unix-like systems | Commercial |
|
|
| JIST/SWANS | JAVA, Tcl | Windows, macOS, Sun Solaris Linux | Commercial |
|
|
| J-SIM | JAVA | Windows, Sun Solaris Linux | Open source |
|
|
3.2. Attacks on MANETs’ Routing Protocols
-
Routing table overflow attack: In this attack, the attacking node tends to crowd the network by advertising several non-existing nodes to overflow the routing table [22]. This prevents legitimate nodes from being aware of network nodes and routing their packets normally.
-
Flooding attack: In a flooding attack, malicious nodes tend to waste network resources such as memory, bandwidth, and battery by flooding the network with bogus packets [23]. For example, flooding RREQ packets prevents the MANET from functioning normally.
-
DDoS attack: In a DDoS attack, attackers tend to keep the targeted legitimate node busy by continuously requesting RREQ messages from collaborative attackers at the same time without respecting the TTL time [24].
-
False removal of working route: In this attack, the malicious node advertises a false state of the link with the destination node as if the link is broken. This enforces the source node to re-initiate route discovery protocol to find another path to reach the destination. Additionally, it slows down packet transmission. False removal of working route attack could be used with another collaborative attack to isolate the targeted legitimate node from MANET.
-
Node isolation attack: Attackers isolate an innocent node by blocking routing information about this targeted node from the entire network [25]. This leads to an ignorance of the presence of this innocent node.
-
Routing table poisoning: In this attack, the attacker sends false RREQ packets with a higher sequence number to force all nodes to delete the old genuine route to a destination and update this route with a corrupted one.
-
Blackhole attack: The attacker tends to change the routing protocol packets to be the best route known for a targeted destination, and when it is requested to forward data packets to the destination node, it starts discarding the received packets to slow down the network performance [26].
-
Grayhole attack: Grayhole attack is an instance of a blackhole attack where an attacker selectively drops some data packets and normally forwards others [27], or drops all packets but only at a certain time. This makes the attack difficult to detect.
-
Wormhole attack: In a wormhole attack, two attacking nodes cooperate where one attacker at a specific location encapsulates some packets and tunnels them to the second attacker, bypassing all intermediate nodes to introduce itself as the fastest route to a destination and then drop the data packets later [28]. It can also be used to replay the received data packets in the other side of the network to disrupt the routing protocol.
-
Rushing attack: In a rushing attack, the malicious node sends RREQ messages with high-power transmission to introduce itself as the shortest path to any destination with only one hop count [29], this manipulates all network nodes to use this routing path. The rushing attack is most likely used alongside another attack such as dropping the network packets that need forwarding.
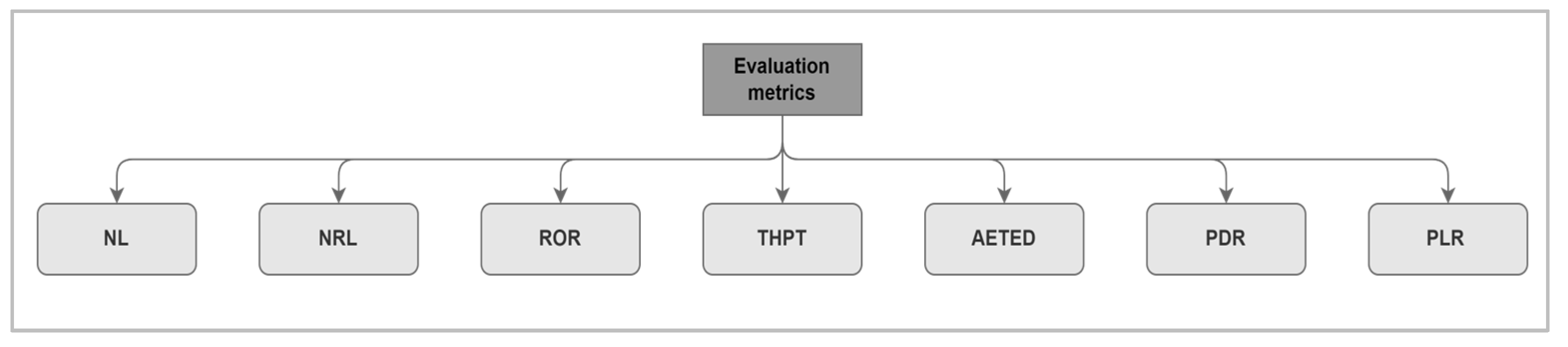
4. Evaluation Metrics and Performance Analysis in MANETs
-
THPT: Throughput is the rate of successfully delivered packets that reached the receiver node per time slot [30]. Throughput is affected by topology changes, noise on communication links, the power of transmission from the source node, and the existence of malicious nodes affecting the throughput ratio.
-
AETED: Average end-to-end delay is the average time taken to send a packet to the destination node [31]. This delay is due to many reasons such as route discovery queuing and process latency, delays caused by wireless links, and processing delays at both the sender and the receiver sides.
-
PDR: Packet delivery ratio is the ratio of packets that are received by the destination across the overall transmitted packets from the source node [32]. The packet delivery ratio represents the maximum throughput that can be achieved by the MANET network.
-
PLR: The packet loss ratio is the opposite of PDR; PLR measures the total lost packets that did not reach the destination node across the overall transmitted packets [33].
-
ROR: Routing overhead ratio is the size of control and header packets needed by the protocol for route discovery and maintenance over the total data packets received by the destination node [34].
-
NRL: Normalized routing load is the ratio between the total number of control packets sent by a source node over the total number of data packets received by a destination node [35]. An increase in normalized routing load metric indicates the efficiency of the used routing protocol.
-
NL: The network load is the average amount of data packets that are being carried by the entire network over time [36]. Increasing the network load ratio increases the possibility of data collision in the wireless medium.
This entry is adapted from the peer-reviewed paper 10.3390/electronics12091956
References
- Reddy, B.; Dhananjaya, B. The AODV routing protocol with built-in security to counter blackhole attack in MANET. Mater. Today Proc. 2022, 50, 1152–1158.
- Ahmed, D.E.; Ibrahim, H.; Khalifa, O. Performance Evaluation of AODV, OLSR, and GRP for Transmitting Video Conferencing over MANETs. Int. J. Comput. Sci. Inf. Secur. 2020, 18, 45–51.
- Kurniawan, A.; Kristalina, P.; Hadi, M.Z.S. Performance Analysis of Routing Protocols AODV, OLSR and DSDV on MANET using NS3. In Proceedings of the 2020 International Electronics Symposium (IES), Surabaya, Indonesia, 29–30 September 2020; pp. 199–206.
- Skaggs-Schellenberg, R.; Wang, N.; Wright, D. Performance Evaluation and Analysis of Proactive and Reactive MANET Protocols at Varied Speeds. In Proceedings of the 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 0981–0985.
- Ferdous, R.; Muthukkumarasamy, V. A Comparative Performance Analysis of MANETs Routing Protocols in Trust-Based Models. In Proceedings of the International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 15–17 December 2016; pp. 880–885.
- Govindasamy, J.; Punniakody, S. A comparative study of reactive, proactive and hybrid routing protocol in wireless sensor network under wormhole attack. J. Electr. Syst. Inf. Technol. 2018, 5, 735–744.
- Bai, Y.; Mai, Y.; Wang, N. Performance comparison and evaluation of the proactive and reactive routing protocols for MANETs. In Proceedings of the Wireless Telecommunications Symposium (WTS), Chicago, IL, USA, 26–28 April 2017; pp. 1–5.
- Panda, N.; Patra, B.; Hota, S. Manet Routing Attacks and Their Countermeasures: A Survey. J. Crit. Rev. 2020, 7, 2777–2792.
- Saudi, N.A.M.; Arshad, M.A.; Buja, A.G.; Fadzil, A.F.A.; Saidi, R. Mobile Ad-Hoc Network (MANET) Routing Protocols: A Performance Assessment. In Proceedings of the Third International Conference on Computing, Mathematics and Statistics, Singapore, 27 March 2019; pp. 53–59.
- Shrestha, S.; Baidya, R.; Giri, B.; Thapa, A. Securing Blackhole Attacks in MANETs using Modified Sequence Number in AODV Routing Protocol. In Proceedings of the 8th International Electrical Engineering Congress (iEECON), Chiang Mai, Thailand, 4–6 March 2020; pp. 1–4.
- Kumari, A.; Krishnan, S. Simulation-Based Study of Blackhole Attack Under AODV Protocol. In Proceedings of the Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018; pp. 1–6.
- Jubair, M.A.; Muniyandi, R.C. NS2 Simulator to Evaluate the Effective of Nodes Number and Simulation Time on the Reactive Routing Protocols in MANET. Int. J. Appl. Eng. Res. 2016, 11, 11394–11399.
- Agrawal, R.; Tripathi, R.; Tiwari, S. Performance Evaluation and Comparison of AODV and DSR Under Adversarial Envi-ronment. In Proceedings of the International Conference on Computational Intelligence and Communication Networks, Gwalior, India, 7–9 October 2011; pp. 596–600.
- Perkins, C.; Belding-Royer, E.; Das, S. RFC3561: Ad Hoc On-Demand Distance Vector (AODV) Routing; IETF: Santa Barbara, CA, USA, 2003.
- Gupta, S.K.; Saket, R.K. Observation of AODV Routing Protocol’s Performance at Variation in ART Value for Various Node’s Mobility. In Proceedings of the First International Conference on Information and Communication Technology for Intelligent Systems: Volume 1. Smart Innovation, Systems and Technologies, Maghreb, Tunisia, 18–20 December 2018; Springer: Cham, Switzerland, 2016; Volume 50.
- Sharma, Y.; Sharma, A.; Sengupta, J. Performance evaluation of Mobile Ad hoc Network routing protocols under various se-curity attacks. In Proceedings of the International Conference on Methods and Models in Computer Science, New Delhi, India, 13–14 December 2010; pp. 117–124.
- Gupta, S.K.; Alsamhi, S.; Saket, R.K. Optimal Relation between ART and Mobility & Transmission Range at Default QualNet & Calculated Transmission Powers. In Proceedings of the 6th International Conference on Advances in Engineering Sciences and Applied Mathematics (ICAESAM-2016), Kuala Lumpur, Malaysia, 21–22 December 2016.
- Agrawal, N.; Fatima, M. Impact of Active Route Time Out and Delete Period Constant on AODV Performance. Int. J. Comput. Appl. 2016, 147, 19–25.
- Malhotra, J. A survey on MANET simulation tools. In Proceedings of the 2014 Innovative Applications of Computational In-telligence on Power, Energy and Controls with their impact on Humanity (CIPECH), Ghaziabad, India, 28–29 November 2014; pp. 495–498.
- Dorathy, I.; Chandrasekaran, M. Simulation tools for mobile ad hoc networks: A survey. J. Appl. Res. Technol. 2018, 16, 437–445.
- Kumar, A.; Varadarajan, V.; Kumar, A.; Dadheech, P.; Choudhary, S.S.; Kumar, V.A.; Panigrahi, B.; Veluvolu, K.C. Black hole attack detection in vehicular ad-hoc network using secure AODV routing algorithm. Microprocess. Microsyst. 2020, 80, 103352.
- Ahamed, U.; Fernando, S. Identifying the Impacts of Active and Passive Attacks on Network Layer in a Mobile Ad-hoc Network: A Simulation Perspective. Int. J. Adv. Comput. Sci. Appl. 2020, 11, 600–605.
- Fiade, A.; Triadi, A.Y.; Sulhi, A.; Masruroh, S.U.; Handayani, V.; Suseno, H.B. Performance Analysis of Black Hole Attack and Flooding Attack AODV Routing Protocol on VANET (Vehicular Ad-Hoc Network). In Proceedings of the 8th International Conference on Cyber and IT Service Management, Pangkal Pinang, Indonesia, 23–24 October 2020; pp. 1–5.
- Kaur, T.; Kumar, R. Mitigation of Blackhole Attacks and Wormhole Attacks in Wireless Sensor Networks Using AODV Protocol. In Proceedings of the IEEE International Conference on Smart Energy Grid Engineering, Oshawa, ON, Canada, 12–15 August 2018; pp. 288–292.
- Poongodi, T.; Khan, M.S.; Patan, R.; Gandomi, A.H.; Balusamy, B. Robust Defense Scheme Against Selective Drop Attack in Wireless Ad Hoc Networks. IEEE Access 2019, 7, 18409–18419.
- Hameed, A.; Al-Omary, A. Survey of Blackhole attack on MANET. In Proceedings of the 2nd Smart Cities Symposium, Bahrain, Bahrain, 24–26 March 2019; pp. 1–4.
- Yadav, S.; Kumar, R.; Tiwari, N.; Bajpai, A. An Effective Approach to Detect and Prevent Collaborative Grayhole Attack by Malicious Node in MANET. In Intelligent Systems Design and Applications, Advances in Intelligent Systems and Computing; Springer: Cham, Switzerland, 2021; Volume 1181.
- Dash, S.P. Study of Blackhole Attack and Wormhole Attack in Vanet Environment and Their Countermeasure. Master’s Thesis, Michigan Technological University, Houghton, MI, USA, 2019.
- Sivanesh, S.; Dhulipala, V.S. Comparaitive Analysis of Blackhole and Rushing Attack in MANET. In Proceedings of the In-ternational Conference on Microwave Integrated Circuits, Photonics and Wireless Networks, Tiruchirappalli, India, 22–24 May 2019; pp. 495–499.
- Vo, T.T.; Luong, T.N. Vra-Aodv: Routing Protocol Detects Blackhole and Grayhole Attacks in Mobile Ad hoc Network. J. Comput. 2018, 13, 222–235.
- Mai, Y.; Bai, Y.; Wang, N. Performance Comparison and Evaluation of the Routing Protocols for MANETs Using NS3. J. Electr. Eng. 2017, 5, 187–195.
- Gurung, S.; Chauhan, S. A dynamic threshold based algorithm for improving security and performance of AODV under black-hole attack in MANET. Wirel. Netw. 2019, 25, 1685–1695.
- Ourouss, K.; Naja, N.; Jamali, A. Defending Against Smart Grayhole Attack Within MANETs: A Reputation-Based Ant Colony Optimization Approach for Secure Route Discovery in DSR Protocol. Wirel. Pers. Commun. 2021, 116, 207–222.
- Gurung, S.; Chauhan, S. A novel approach for mitigating gray hole attack in MANET. Wirel. Netw. 2018, 24, 565–579.
- Husieen, N.A.; Kadhum, A.N. The Effect of Pause Time on the Performance of Mobile Ad-hoc Network Routing Protocols. In Proceedings of the 4th International Conference on Intelligent Information Technology Application, Qinghuangdao, China, 5–7 November 2010.
- El-Kabbany, A.F.; Ali, H.M.; Hussein, A.; Tawfeek, B. Comparative study of routing protocols for mobile ad hoc networks. Int. J. Intell. Comput. Inf. Sci. 2017, 17, 31–43.
