Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
The Internet of Things (IoT) has risen from ubiquitous computing to the Internet itself. Internet of vehicles (IoV) is the next emerging trend in IoT. People can build intelligent transportation systems (ITS) using IoV. However, overheads are imposed on IoV network due to a massive quantity of information being transferred from the devices connected in IoV. One such overhead is the network connection between the units of an IoV. To make an efficient ITS using IoV, optimization of network connectivity is required.
- intelligent transport system (ITS)
- internet of things (IoT)
- internet of vehicles (IoV)
- vehicular ad hoc network (VANET)
- network optimization
1. Background of IoT
1.1. IoT Evolution
Kevin coined the term Internet of Things (IoT) in 1982 [28], in the US, when a connection between a cola vending machine and the Internet was established to inspect the amount of cola in the machine [1]. The IoT network is a collection of interconnected physical objects, including a data processing device, people, mechanical and digital machines embedded with software and electronic circuitry which enables these objects provided with unique identifiers to collect data and exchange accordingly. IoT devices will be more than seven times the present world population, as per a report [29]. Cisco expected the number of IoT connected devices to surpass between 50 billion in 2020. The IoT is accompanying the following advantages:
-
Allows connectivity between devices to develop smarter territories;
-
Making one’s life easier and comfortable through allowing automation;
-
Allows organizations to maximize efficiency and bring down costs;
-
Allows firms to deal with wastage and improve the deliverance of services;
-
Enables firms to develop and merge business models and improve productivity.
Along with this, new technologies and mechanisms have come up and have been advancing, such as wireless and sensor technologies, machine-to-machine (M2M) communication, big data analytics, artificial intelligence, and machine learning. With the increased number of gadgets on the network, the connectivity of heterogeneous gadgets imposes numerous new challenges. Such technologies and associated frameworks have given way to many extremely attractive IoT applications [30,31,32,33].
1.2. Difference among M2M, IoT, and IoE
The Internet of Everything (IoE) emerges as an advancement of IoT and it encompasses IoT and internet of vehicles (IoV). IoE is a connection of data, process, people, and things that are connected to change information into actions for creating more opportunities and better experiences. It is natural that all gadgets will be linked to the Internet in the future and all undertakings will be linked by device to device (D2D) correspondence. The accompanying advancements are assuming an indispensable part of the IoE. It joins communication from M2M, Machine to People (M2P), D2D, and People to People (P2P) [34]. The IoE is used in various applications with great execution and reaction time. Specific uses of IoE in ITS include self-driving cars, smart parking systems, smart traffic monitoring, connected cars, smart cities, and wearables (health monitoring of patients). Different smart wearable gadgets are distinguished to gather different health statuses, pulse, body glucose level, internal heat level, physical movement, etc. [35]. M2M is a subset of IoT that exist without the Internet which empowers ubiquitous networks among gadgets. The IoT, has evolved on the basis of M2M, that aims to offer many more functionalities, such as enabling communication among the same kind of machines, uniting distinct devices and systems to use different technologies, and provide interactive and fully-connected networks across varying environments. Some of the utilization of M2M communication are home and office security frameworks, traffic light frameworks, robotics, sensor networks in a petroleum processing plant, and so on. The previously mentioned uses can move the data to the server or client with good reaction time. To distinguish and accumulate diverse data from IoT gadgets, there is a requirement for cutting edge high-speed wireless network innovations, for example, 4G to 5G Networks. This advancement will have the option to satisfy their cases of high throughput, super-low latency, high reliability, accessibility, and transferring data to the client and server. This is additionally used to conquer the different issues in IoT, IoE, and M2M, such as network connectivity, and increase the speed of data flow between the numerous IoT gadgets. The above cutting edge innovations, for example, IoT, IoE, M2M, and 5G network convergence, are used to improve our lives.
1.3. IoT for Connected Vehicles
IoT is directly clearing a path for an associated future where vehicular nodes, gadgets, and other individual elements speak with one another in consolidated frameworks. ITS frameworks are a coordinated gathering of advancements, for example, IoT, IoV, 4G-LTE, 5G, RFID, and GPS. To manage the developing traffic requests in current urban areas, ITS frameworks, in general, adjust frameworks with a decentralized design. Vehicle information is accumulated utilizing traffic cameras, onboard sensors, radio frequency identification, infrared sensors, and information is transferred to the smart transport management system via Wi-Fi to automate and coordinate traffic signals and traffic monitoring. A service-centric heterogeneous vehicular network modelling for connected traffic environments is proposed in [36]. Safety and administration related applications in this area are sorted into three kinds.
-
Safety applications;
-
Efficient traffic management;
-
Support and infotainment applications.
1.3.1. Safety Applications
The foremost target of security and safety applications of vehicular networks is to maintain a safe distance from road mishaps as it involves lives. These applications are vulnerable against delay, security applications are required to work proactively to advance the driver and, as such, ultimately prevent the disaster from happening. On the chance that a mishap has happened, this application intends to give emergency vehicles at the earliest. A new architecture has been suggested to prevent intersection collisions build on DSRC [37]. It focuses on establishing secure RSU communications deployed near the intersection area where nodes exchange their status updates. Warning for traffic signal violation, i.e., at the traffic light signal, if the driver does not stop. Notifications can be obtained when RSUs relay traffic light signals while positioning RSUs with a traffic light controller [38]. A cooperative driving of automated vehicles using B-splines for trajectory planning has been proposed by Van et al. [39]. Logical scenarios parameterization for automated vehicle safety assessment in cut-in scenarios from Japanese and German highways has been surveyed in [40]. A framework for vehicle dynamics model validation has been proposed by Widner et al. [41]. Cao et al. has proposed an improved motion control with cyber-physical uncertainty tolerance for distributed drive electric vehicle [42]. Some of the other solutions are reported in the literature—mobile crowd sensing for traffic prediction in IoV [43], and hybrid recommendation system architecture for early safety predication using IoV [44].
1.3.2. Efficient Traffic Management
Intelligent traffic applications help by improving the progression of traffic and keeping away from the street clog. Vehicular nodes are informed about traffic situations early based on communication received. This may assist vehicles with changing their courses in case of traffic congestion and minimizes travel time [45,46]. The application for road congestion control helps ensure free flow of traffic by reducing road congestion. In addition, this increases the flexibility of the road and prevents traffic jams [47]. As per the necessity, before heading to a new area for direction, drivers can download maps of areas. It would also maximise the traffic flow instead of becoming trapped on the wrong road. The portal for accessing the content map database enables access to useful knowledge from home stations or mobile hot spots [48]. Non-signalized intersection network management with connected and automated vehicles is also proposed in [49]. Applications on intelligence, surveillance, and reconnaissance missions in cooperative routing problem for ground vehicle and unmanned aerial vehicle has been suggested in [50]. Niu et al. has presented an in-depth survey of space–air–ground integrated vehicular network for connected and automated vehicles and presented challenges and solutions [51]. A cost-effective traffic signal control was proposed in [52].
1.3.3. Support and Infotainment Applications
Support and Infotainment utilization are intended to upgrade the client’s comfort. Likewise, health monitoring applications give utilities to patients in crises. Gaming, file sharing, searching for the nearest milk parlour, theatre, cafe, open parking room, internet video streaming, carpooling, and network service provisioning are some of the examples of infotainment technologies. As it increases network reliability and available bandwidth with an increase in peer capacity, the peer-to-peer file sharing technology has benefits over the client-server architecture. One of the frequently used P2P applications is Bit Torrent. There is a recommended emergency routing protocol called VehiHealth to provide patients with pre-medical care by providing quick communication between hospital and ambulance [53,54,55]. Computationally efficient non-linear one- and two-track models for multi-trailer road vehicles is proposed in [56]. Xin et al. [57] have proposed an AI-based QoS optimization for multimedia transmission in IoV. They present a system for multi-modal communication in which multimedia IoV transmission through mobile devices offers the quality of experience optimization model. Musa et al. [58] have proposed a design of an information-centric network with mobility-aware proactive caching scheme to provide delay-sensitive services on IoV networks. The applications of IoT for connected vehicles are listed in Table 1.
Table 1. Applications of IoT.
| Safety Applications | Efficient Traffic Management | Support and Infotainment |
|---|---|---|
| 1. In-Vehicle Signage | 1. Road Clog Management | 1. Intelligent Parking Route |
| 2. Warning Turn Assistant | 2. Toll Management | 2. Vehicle Pooling |
| 3. Blind Merge Warning | 3. Computerized Map Downloading | 3. Web access Provisioning |
| 4. Vehicle Warning | 4. Intersection Management | 4. Distributed Data Sharing |
| 5. Emergency Electronic Brake Lights | 5. SOS Services | 5. Clinical Applications |
| 6. Early Detection Warning | ||
| 7. Pre-Crash Sensing | ||
| 8. Emergency Electronic Brake |
2. Towards IoV
Wireless ad hoc networks is a class comprising wireless networks, such as (i) mobile ad hoc networks (MANET), (ii) vehicular ad hoc networks (VANET), and (iii) wireless sensor networks (WSN) [59]. Generally, the WSN is classified into infrastructure and infrastructure-less networks. Based upon the geography and arrangement, ad hoc systems might be classified as homogeneous and heterogeneous systems. A homogeneous network is formed from similar nodes whereas a heterogeneous network is formed from dissimilar nodes. The concept of ad hoc networks is old which began in 1972, i.e., DARPA packet radio network, ALOHA, PRNET, etc. [60].
Infrastructure-less MANET is an organization of mobile devices, connected over a wireless network and follow different properties, i.e., self configuring, self healing, self protecting [60]. In MANET, because of mobility, frequent link breaks, and dynamic topology, nodes in these networks act as routers to transfer packets. It enables spatial spectrum reuse due to the limited bandwidth of each node, another type of ad hoc network is VANET which is shaped by various vehicles present on the road.
Different vehicles communicate with one another on the road and each of these vehicles has a tool called an On Board Unit (OBU). OBU can talk to vehicles and RSUs, which act as access points [61]. Vehicles are enabled to talk to one another in different ways. VANET is very helpful in spontaneous data exchange and it is a key component in ITS. It offers different applications concerning highway traffic, road congestion and accidents. The two communications considered in VANET are vehicle-to-vehicle communication (V2V) and vehicle-to-infrastructure communication (V2I)—between vehicles and roadside access points. VANET looks very similar to MANET, but it is slightly different in following route patterns, they follow predictable mobile patterns whereas MANET has unpredictable mobile patterns. The architecture of VANET is shown in Figure 1.
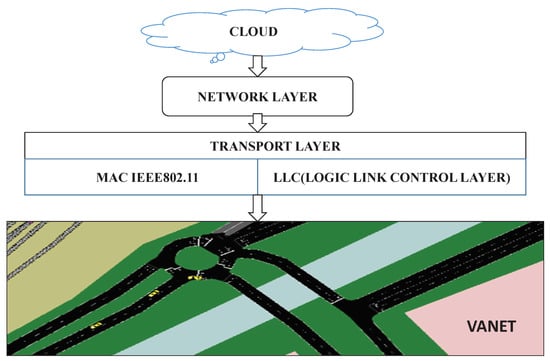
Figure 1. VANET architecture.
There are extensively three distinct segments of VANET, one is an OBU which is answerable for information collection from various sensors and other vehicles. The second-RSUs which offer an infrastructure that enables communication to the external network. The third communication technology helps these units to talk to each other, IEEE 1609.2 is commonly known as Dedicated Short Range Communication (DSRC) 802.11p [62]; vehicles must be equipped with the IEEE 802.11p based OBU and DSRC, along with added sensors to be completely aware of the condition where the vehicle find itself in [45]. A cooperative perception technology of autonomous driving in the internet of vehicles environment survey is reported in [63]. The VANET architecture is commonly divided into three sorts of classes namely:
-
Mobile and wireless LAN networks which are used to direct and obtain traffic data through fixed portals and WiMAX/Wi-Fi;
-
Pure ad hoc, that is, between vehicular nodes and defined gateways;
-
Hybrid, that is, blend of infrastructure and ad hoc networks.
Different standard structures of vehicular networks consolidate CALM (Continuous Air Interface for Long to Medium range) by ISO [64], and C2CNet (Car-to-Car Network) by C2C Consortium [65], and WAVE (Wireless Access in Vehicular Environment) by IEEE [66]. The IoV is viewed to be a development pertaining to V2V network [4]. The IoT is supporting the demand of traditional VANET to IoV scope, the IoV coordinates vehicular networks with data storage and data analytics services. The IoV brought intelligence to the communication of the vehicular network, which improves driving support for completely autonomous driving by facilitating the AI awareness to the encompassing vehicular situation. The components of IoV include [4] vehicles (network formed by vehicular nodes), RSU, infrastructure (street and traffic-related sensors), personal devices (smartphones and PDAs), and people (drivers). Accordingly, the different services that are possible are listed as follows.
-
Vehicle-to-vehicle information services;
-
Infrastructure and vehicle information services;
-
Sensors and vehicle information services;
-
RSU and vehicle information services;
-
Human and vehicle information services;
-
Vehicle and personal devices information services.
2.1. Architecture of the IoV
Numerous models have been proposed by researchers for IoV [4,67]. These architectures are helpful to meld various kinds of interactions. The basic IoV innovation stack incorporates three layers, namely: perception, networking, and the Internet and service platforms. The key concept of IoV is specified by its three-layer architecture. In the literature, two more layered architectures can be found—the five-layer architecture [68] and the seven-layer architecture [69], which also include the processing and business layers.
2.1.1. Layer 1: Perception
Sensors are implanted in the physical environment to collect and transfer data. Sensing devices do not associate legitimately to the web, they can synchronize with phones and different gadgets utilizing Bluetooth LE. Raw information was examined against the characteristics of the global positioning framework obtained through the sensors. IoT sensors are a fundamental aspect of IoT innovation.
2.1.2. Layer 2: Networking
Micro controllers regulate the information channeling to IoT sensors and various actuators. Micro controllers and Internet connectivity, share information obtained at the first layer and examine for second layer to make a further move. Networking, either wireless or wired, is the basic and most important responsibility of this layer.
2.1.3. Layer 3: Application
Service platforms take measures to adjust, alter, maintain, and monitor physical conditions after data investigation. Telematics, data mining, voice over Internet protocol (VOIP), blockchain, and Cloud SaaS stages are typical utilities.
The following data were taken from scientific publications related to attribute measuring using IoT sensors, methods of information transmission between smart sensors and actuators, networks, and protocols used in communication methods. Approaches to data storage can be seen in Figure 2.
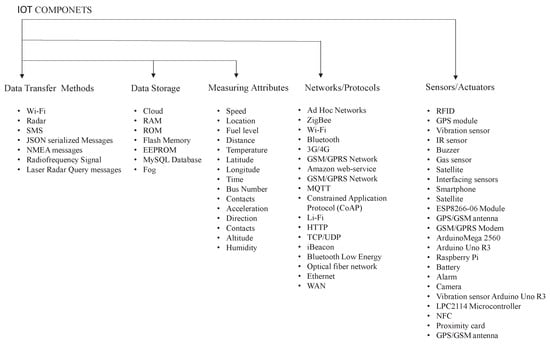
Figure 2. IoT components [4].
2.2. Network Protocols Used in Vehicular Networks
IoV systems include a network of vehicular nodes, fixed RSU, and a central server. Road-related alerts relevant to peer drivers are interchanged in V2V communication [70]. On the other hand, V2I communication is utilized for the collection of sensor information and dissipation of alerts based on locations to vehicles [9]. Mobile networks, DSRC/WAVE, Wi-Fi, and ZigBee are among the innovations for the wireless channels. DSRC and OBU combined with extra sensors are necessary to be completely conscious of the circumstance in which the vehicle finds itself in [71,72,73,74]. The IEEE 802.11ah long-range Wi-Fi, which can be supportively used in vehicle frameworks, especially when vehicles are spread over 1 km in road organisations. During conditions where the vehicles run at 160 kmph, the utilization of WiMAX might fit better [75]. The four driving radio access technologies (RATs) for V2I communication are 4G/long-term evolution advanced (LTE-A), 5G, Wi-Fi, and DSRC. As of now, car companies are pursuing numerous for open RATs to empower applications both for protection and security (primarily web access). Audi and Volvo have a lot number of vehicles that have Internet accessibility regulated by 3G, 4G LTE, and 5G [76]. Shah et al. [77] have proposed a novel cluster-based MAC protocol (CB-MAC) for VANETs and they have optimized the CB-MAC protocol [78]. Karabulut et al. [79] have proposed a multiple-input multiple-output (MIMO) and orthogonal frequency division multiplexing (OFDM) based MAC protocol which uses the advantages of both the techniques. Wu et al. [80] have designed a self-adaptive time division multiple access (TDMA)-based MAC protocol for VANETs to improve the stability of the time slot scheduling in VANETs. Han et al. [81] have proposed an adaptive time slot access MAC protocol in distributed VANET which improves the time slot access efficiency by adapting the access time slot according to the driving direction of the vehicle and the traffic density ratio.
The various communication technologies applicable are shown in Figure 3.
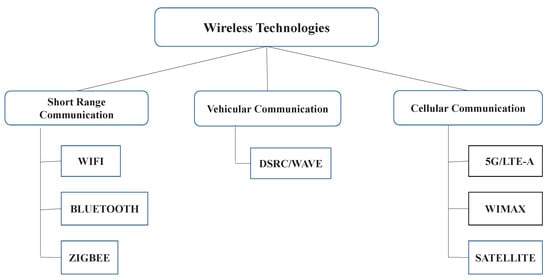
Figure 3. Communication technologies.
2.3. Routing in IoV
Many real-life situations need different technologies for vehicle networking. For instance, driving in metropolitan circumstances, drivers know the traffic conditions of urban roads ahead and alter their route direction according to the traffic situation on their route. By utilizing the cutting edge innovation of IoV, individuals can likewise diminish fuel utilization and environmental pollution. A significant exploration aspect in IoV is its routing conventions. Researchers have proposed different routing algorithms for IoV characteristics, i.e., heterogeneous communication range, dynamic topology, geographically constrained topology, mobility of the vehicles, time-dependent vehicular density, ad hoc network, and the elements that construct the network are vehicles. In recent days, most routing protocols on varying factors, such as energy, network lifetime, efficiency, scalability, multi casting, reliability, and load balancing have been made to satisfy IoV prerequisites.
Depending upon the number of senders and recipients participating, routing approaches can be sorted into three kinds: geocast/broadcast, multicast, and unicast approaches. Second, researchers arrange them into four classifications dependent on data needed to carry-out routing, i.e., map, topology, position, and path-based. Third, it is grouped to be delay-sensitive and delay-tolerant. Lastly, researchers identify protocols based on applicability in their various dimensions, for example, 1-dimensional, 2-dimensional, and 3-dimensional. The target networks are heterogeneous and homogeneous. The routing conventions that are often utilized (traditional routing algorithms) are dynamic source routing, optimized link state routing, ad hoc on-demand distance vector, geographic source routing, and greedy topology. These routing conventions are utilized to transfer the data packets between vehicular nodes. Under these routing conventions, the proactive approach relies on routing strategies associated with a table-driven method. Proactive routing conventions generally rely upon algorithms related to the optimal route. They store all the gathered information identified with the associated vehicular nodes in related predefined tables, as well as being the primary component of routing conventions. Each table in this approach is refreshed by its vehicular node when the network topology changes. Reactive routing conventions depend upon algorithms identified with on-demand actions. At the point when two vehicle nodes need to interact, they begin the path discovery of the route and one of its fundamental advantages is the reduction in network traffic [82]. Geographic dependent routing conventions are dependent on situations corresponding to the position technique utilizing area-based applications, such as GPS. Geographic applications are used while giving information for path selection [82]. In different scenarios, these traditional routing algorithms performed comparatively better, but failed to provide the optimal routing solution in IoV environment. To enhance the reliability of safety applications, bio-inspired approaches are used. Similarly, recently proposed protocols based on SI techniques, namely, ant colony and particle swarm algorithms, etc. In comparison with traditional techniques, these protocols have performed better individually.
3. Network Optimization
IoV, the evolving type of VANETs and MANETs, is more exceptional but more complex to adapt. Special IoV capabilities include high-processing, high-speed data access, robust usability, and variable network density. It is a hard job to prepare an efficient optimal routing protocol for information transmission in IoV, to hold all diverse aspects of vehicles on the route. Heterogeneous node density and networking, inconsistent connectivity, and variable mobility must be taken into account in an optimal routing protocol. Optimization is characterized and portrayed as the innovation utilized to enhance the performance of the network for any circumstance. Optimization is a numerical issue experienced in all engineering disciplines. It implies finding the most ideal/desirable solution. Optimization issues have widely occurred and, hence, various techniques for taking care of these issues should be an active research topic. Optimization algorithms can be either stochastic or deterministic. Strategies to tackle optimization issues require a lot of computational power, which will generally tend to fail as the problem size increases.
3.1. Optimization Techniques
Optimization generally parts into two different classes, one is deterministic algorithms and the other is stochastic algorithms. The issues that cannot be settled from the deterministic algorithm are named as non-deterministic algorithms and, thus, the novel solutions developed by stochastic algorithm assists with taking care of the non-deterministic problems up to an optimum standard. The non-deterministic problems are solved by meta-heuristic algorithms. Meta-heuristics are characterized as heuristics at a more significant level of frameworks. Thus, meta-heuristics are problem-independent approaches, though heuristics are problem specific. This heuristic technique helps with taking care of the complex problem [83]. Biological behaviour-influenced algorithms are known as bio-inspired stochastic algorithms. Bio-inspired stochastic algorithms have gained importance, especially for tackling complex enhancement issues of routing. These stochastic procedures that are created to accomplish near optimal solutions for huge scope optimization problems [84]. The traditional solution of NP-hard problems with a numerous variables and non-linear objective functions will sometimes fail (being stuck in a local optimum), leading to the development of alternative solutions. These techniques are moved by the characteristic biological evolution, as well as the social conduct of species. These approaches rely on natural patterns and behaviours that have the capacity for self-adaption and self-association and are utilized as powerful optimization tools.
Apart from these, there are other optimization methods in which the researchers have focused on vehicular congestions in urban areas. Authors proposed a centralized simulated annealing method for alleviating vehicular congestion in smart cities [85]. They used a novel dynamic centralized simulated annealing-based approach for finding optimal vehicle routes using a different type of cost function. Amer et al. proposed a hybrid game approach-based channel congestion control for IoV [86]. They developed a new hybrid game transmission rate and power channel congestion control approach on IoV networks, where the nodes play as greedy opponents demanding high information rates with the maximum power level. A new congestion control approach is proposed which is based on the concept of hybrid power control and contention window to ensure a reliable and safe communications architecture in IoV [87]. Fu et al. proposed an IoV system assisted by mobile edge computing which is used for cross-layer offloading to provide low latency and abundant computation resources [88].
Bio-inspired optimization techniques, swarm intelligence (SI), evolutionary algorithms (EAs) play a crucial part in the computer intelligence sector that has become famous over the recent times [89,90]. EAs which depend on Darwin’s hypothesis of natural selection and survival of the fittest. EAs and SI are taken from biological evolution processes, which depend on behavioural models of social animals, for example, ants, bumblebees, fireflies, fish, flying creatures, etc., hence, they look for food substance or a better environment, EAs commence with a collection of candidate solutions, create alternatives for offspring recursively, and evaluate solutions till an acceptable solution is found. Genetic algorithms (GAs) [91], evolution strategy (ES) [92], evolutionary programming (EP) [93], genetic programming (GP) [94], estimation of distribution algorithms (EDA) [95], differential evolution (DE) [96] are popular algorithms in this EA group. SI algorithms begin with a group of possible candidate solutions, and in every iteration, a novel group of candidate solutions is produced derived from verifiable and other applicable historical data. A few models of this kind comprises of an ant colony algorithm (ACO) [97], particle swarm optimization (PSO) [98], artificial bee colony optimization (ABC) [99], firefly algorithm optimization (FA) [99], salp algorithm (SA) [100], bacterial foraging optimization (BFO), artificial fish swarm optimization (AFS), etc. The bio-inspired optimization techniques are shown in Figure 4.
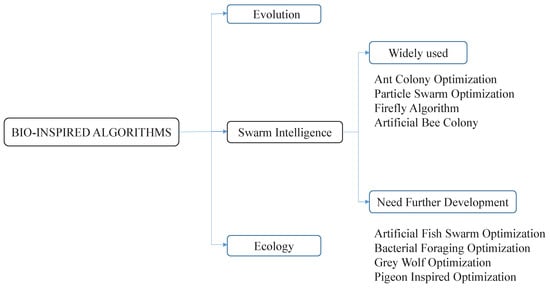
Figure 4. Bio-inspired optimization techniques.
3.2. Evolutionary and Bio-Inspired Algorithms
The SI algorithm understands the solution for the problem by learning from certain life or natural phenomena [101]. These types of techniques consolidate the self-association, self-learning, and self-versatile characteristics of the regular nature. In the computation cycle, the general population is searched for the solution space through the acquired estimated data. In the course of a search cycle, the populace advances by the fitness function values, which are fixed beforehand. Consequently, the algorithm has certain intelligence. Inferable from its points of advantage, when the SI algorithm is utilized to resolve a problem, it is not important to manage the solution issue ahead of time to acquire a detailed solution. It is, hence, conceivable to effectively tackle some highly complex problems. The swarm intelligence has proved its efficiency in tackling the routing issues in such self-organized systems as MANET, VANET, WSN, and IoV. ACO and PSO are the traditional SI optimization techniques. ABC, BFO, FA, AFS, and several others are less well-known techniques. Initially, Swarm techniques were intended for stationary optimization problems. Among them are ACO, ABC and PSO. Bees, ants, salps, and other swarm activity that resembles that of the nodes in the wireless ad hoc network. The most widely used SI algorithms listed in Table 2.
Table 2. Swarm based optimization techniques.
| Sl. | Algorithm | Publishing Year | Literature |
|---|---|---|---|
| 1 | Genetic Algorithm | Holland, 1992 [102] | [103,104,105,106] |
| 2 | Ant Colony Algorithm | Dorigo and Di Caro, 1999 [97] | [107,108,109] |
| 3 | Particle Swarm Optimization | Kennedy and Eberhart, 1995 [110] | [111,112,113] |
| 4 | Artificial Bee Colony | Karaboga, 2005 [99] | [114,115,116] |
| 5 | Firefly Algorithm | Yang, 2009 [117] | [118,119] |
| 6 | Salp Algorithm | Mirjalili, 2017 [100] | [120,121] |
This entry is adapted from the peer-reviewed paper 10.3390/s23010555
This entry is offline, you can click here to edit this entry!
