Industry 4.0 is seeking to advance traditional construction practices towards more efficient and internet of things (IoT)-based construction practices, such as offsite construction. Offsite construction (OSC) allows for the simultaneous fabrication of building modules and onsite work. Integrating IoT technologies in construction practice is projected to improve the industry’s growth. However, there is an increase in cybersecurity vulnerabilities. Cyber threats are becoming more disruptive and targeted, resulting in monetary and infrastructure losses.
- cybersecurity
- off-site construction
- vulnerabilities
1. Introduction
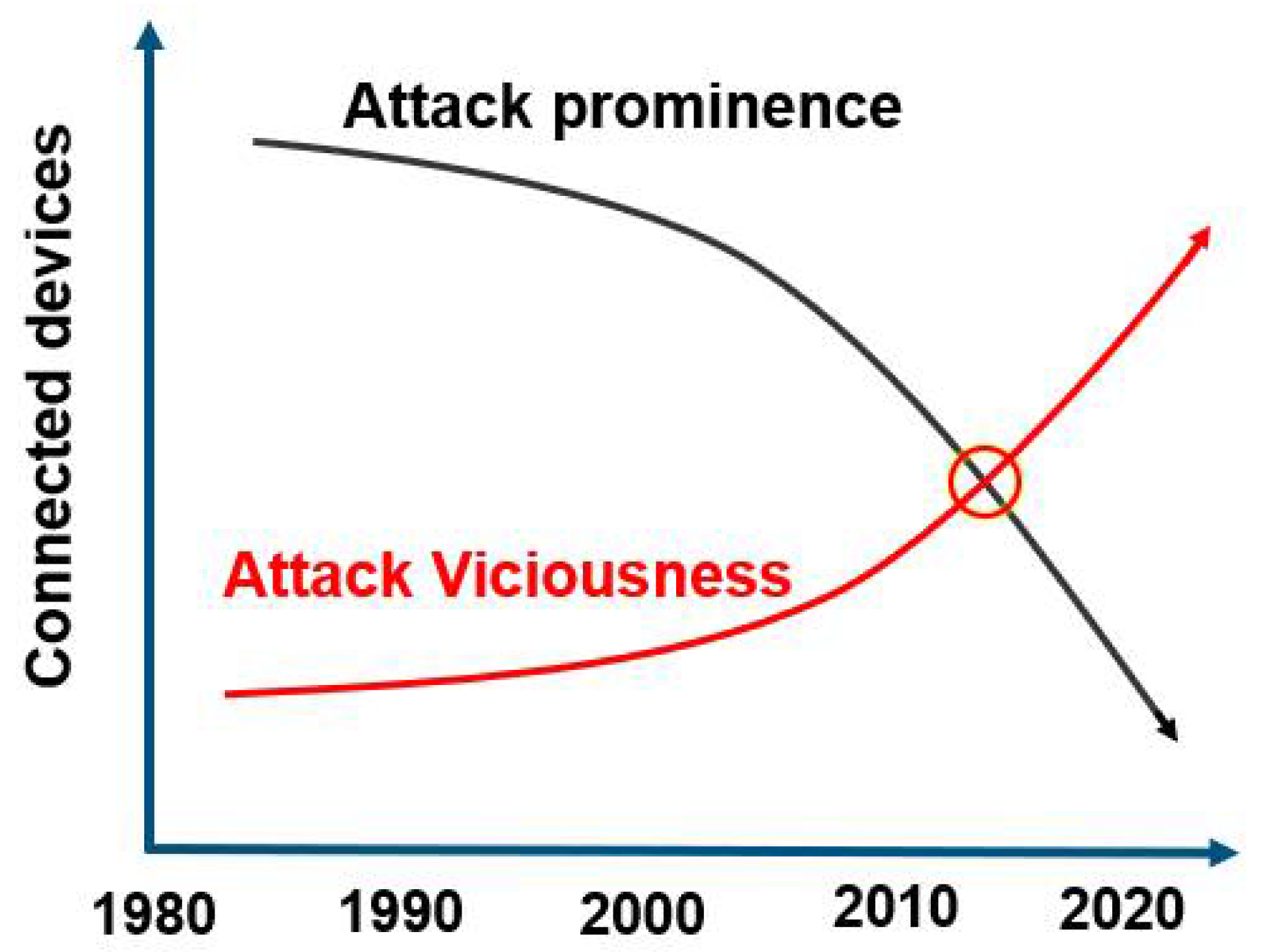
2. Cyber-Threats
2.1. Forms of Attack
2.2. Past and Present Threats
3. Importance of Cybersecurity in Manufacturing and Construction
3.1. Manufacturing
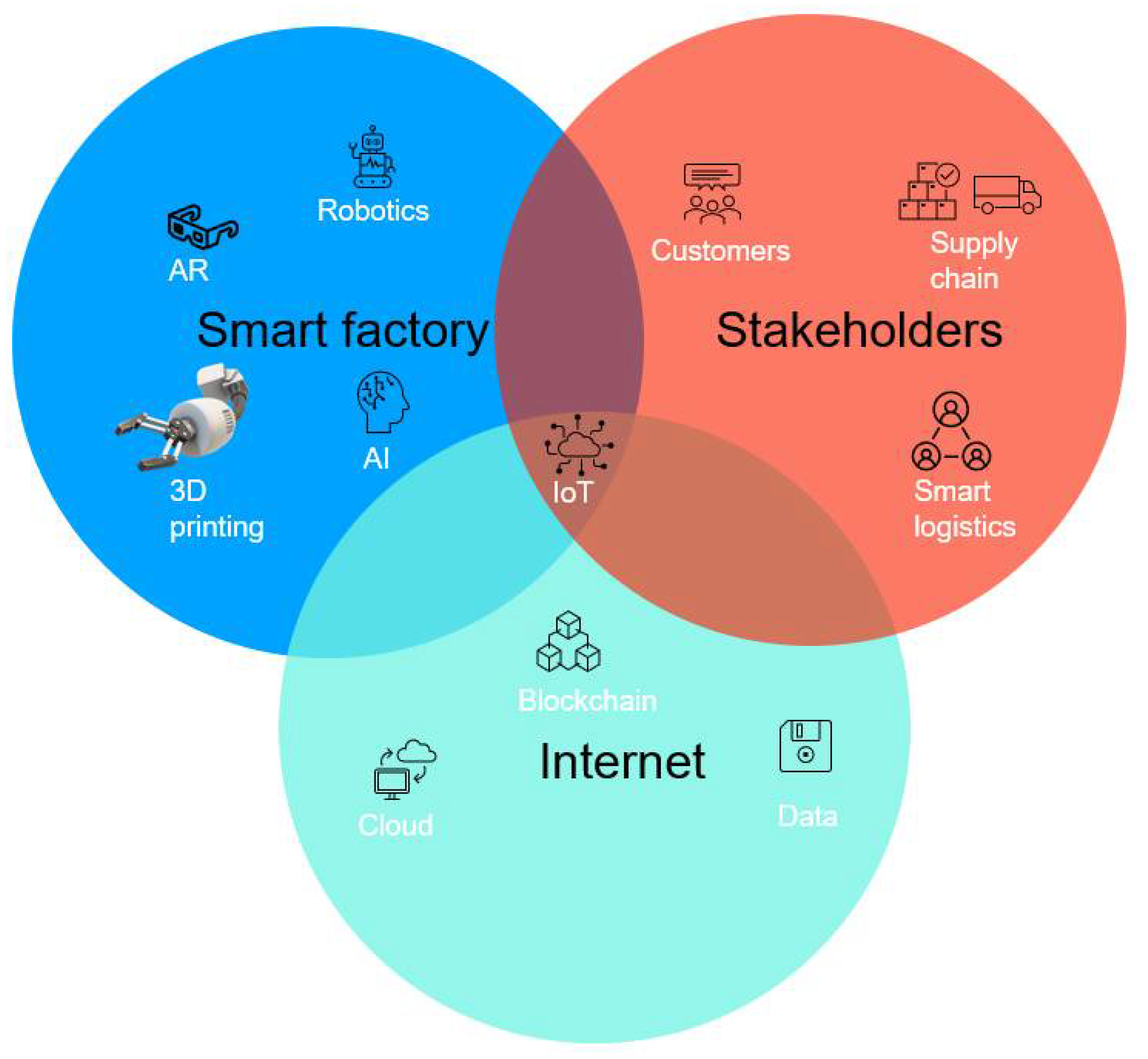
3.2. Off-Site Construction
OSC combines the aspects of remote manufacturing and construction, enabling site work to progress with the prefabrication of building elements simultaneously. This is facilitated by multiple Industry 4.0 technologies, such as cloud services, sensors, GPS, and networks that involve the exchange of information in close to real time between different stakeholders.
One of the most extensively adopted technologies in OSC, more than any other digital technology, is BIM, which constitutes about 70% of 113 conducted research studies [15]. It has five main attributes (visualization, coordination, simulation, optimization, and plotting ability) that enable the digital simulation and modelling of a construction project during its entire lifecycle. This technology provides a pathway for the digitalization of OSC, and the key elements of this digitalization can be categorized as follows: digital data and access, automation, and connectivity.
In digital data and access, information is collected, processed, and analyzed to obtain new perspectives related to the value chain and giving information to be shared between stakeholders on a network. Stakeholders are enabled to operate electronic procurements and material accounts, leading to automation that engenders independent and self-ordering operations [16].
IoT in OSC has been used to perform supply chain supervision to track real-time work progression. Benefits have been realized regarding time savings, cost savings, and more efficient information sharing. However, studies have shown that the management of such complex systems experiences delays due to unstable networks and complex data handling [23].
OSC is not only a clump of participants and equipment; with the adoption of IR4 technologies and digitalization of this industry, it has grown into a hyper-connected web of participants throughout an entire project life cycle. Hence, securing the cyber-physical interactions from the conceptual stages is paramount.
4. Targetable Entities and Vulnerabilities
4.1.1. Prefabricated Module Production and Preparation
4.1.2. Transportation Design and Planning
4.1.3. Onsite Assembly
5. Cybersecurity Frameworks and Management
5.1. Cybersecurity Management Framework for Cloud-Based BIM Model
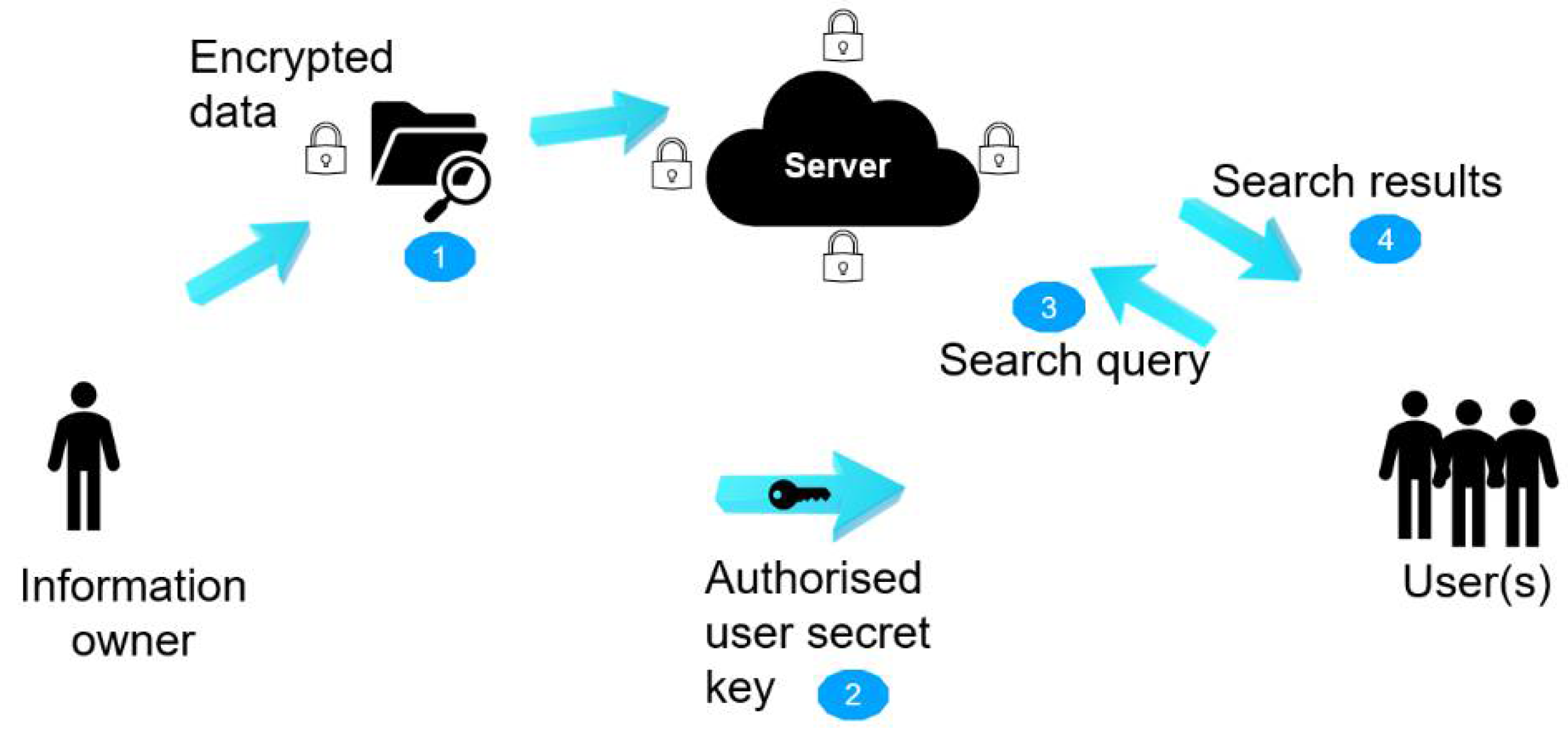
-
Access management.
-
Information protection.
-
Governance approach.
-
Security practices and policies.
-
Protected collaboration in BIM–cloud integration.
5.2. National Institute of Standards and Technology Framework
5.3. Security-Minded BIM in PAS 1192-5 and ISO 19650-5
5.4. The Institute of Engineering Technology (IET) Code of Practice for Cybersecurity in the Built Environment (Cop-CSBE)
5.5. Core Cybersecurity Framework for Construction
5.6. Management
This entry is adapted from the peer-reviewed paper 10.3390/app12105037
References
- Mullet, V.; Sondi, P.; Ramat, E. A Review of Cybersecurity Guidelines for Manufacturing Factories in Industry 4.0. IEEE Access 2021, 9, 23235–23263.
- Bai, C.; Dallasega, P.; Orzes, G.; Sarkis, J. Industry 4.0 technologies assessment: A sustainability perspective. Int. J. Prod. Econ. 2020, 229, 107776.
- Kebande, V.R. Industrial internet of things (IIoT) forensics: The forgotten concept in the race towards industry 4.0. Forensic Sci. Int. Rep. 2022, 5, 100257.
- Zabidin, N.S.; Belayutham, S.; Ibrahim, K.I. A bibliometric and scientometric mapping of Industry 4.0 in construction. J. Inf. Technol. Constr. 2020, 25, 287–307.
- Kozlovska, M.; Klosova, D.; Strukova, Z. Impact of Industry 4.0 Platform on the Formation of Construction 4.0 Concept: A Literature Review. Sustainability 2021, 13, 2683.
- Oesterreich, T.D.; Teuteberg, F. Understanding the implications of digitisation and automation in the context of Industry 4.0: A triangulation approach and elements of a research agenda for the construction industry. Comput. Ind. 2016, 83, 121–139.
- Ani, U.P.D.; He, H.; Tiwari, A. Review of cybersecurity issues in industrial critical infrastructure: Manufacturing in perspective. J. Cyber Secur. Technol. 2016, 1, 32–74.
- Mantha, B.R.; de Soto, B.G. Cyber Security Challenges and Vulnerability Assessment in the Construction Industry. In Proceedings of the Creative Construction Conference, Budapest, Hungary, 29 June–2 July 2019.
- Maskuriy, R.; Selamat, A.; Maresova, P.; Krejcar, O. Olalekan Industry 4.0 for the Construction Industry: Review of Management Perspective. Economies 2019, 7, 68.
- Amin, M. A Survey of Financial Losses Due to Malware. In Proceedings of the Second International Conference on Information and Communication Technology for Competitive Strategies, Udaipur, India, 4 March 2016.
- Hansen, R.L. The Computer Virus Eradication Act of 1989: The War against Computer Crime Continues Comment. Softw. LJ 1989, 3, 717–754.
- Matkeviciene, R. Review: Cybercrime-Vandalising Information Society. Available online: http://informationr.net/ir/reviews/revs053.html (accessed on 29 March 2022).
- Kamal, S.U.M.; Ali, R.J.A.; Alani, H.K.; Abdulmajed, E.S. Survey and brief history on malware in network security case study: Viruses, worms and bots. ARPN J. Eng. Appl. Sci. 2016, 11, 16.
- Hwang, B.-G.; Shan, M.; Looi, K.-Y. Key constraints and mitigation strategies for prefabricated prefinished volumetric construction. J. Clean. Prod. 2018, 183, 183–193.
- Wang, M.; Wang, C.C.; Sepasgozar, S.; Zlatanova, S. A Systematic Review of Digital Technology Adoption in Off-Site Construction: Current Status and Future Direction towards Industry 4.0. Buildings 2020, 10, 204.
- Alaloul, W.S.; Liew, M.S.; Zawawi, N.A.W.A.; Mohammed, B.S. Industry Revolution IR 4.0: Future Opportunities and Challenges in Construction Industry. MATEC Web Conf. 2018, 203, 02010.
- Fenner, A.E.; Zoloedova, V.; Kibert, C.J. Conference Report 2017: State-of-the-Art of Modular Construction. In Proceedings of the Rinker School of Construction Management University of Florida, Gainesville, FL, USA, 28 October 2017.
- Machado, T.J.X.; Gouveia, L.B. Covid-19 effects on cybersecurity issues. Int. J. Adv. Eng. Res. Sci. 2021, 8, 222–229.
- Pasco, J.; Lei, Z.; Aranas, C. Additive Manufacturing in Off-Site Construction: Review and Future Directions. Buildings 2022, 12, 53.
- Conti Ransomware|CISA’. Available online: https://www.cisa.gov/uscert/ncas/alerts/aa21-265a (accessed on 8 April 2022).
- Wells, L.J.; Camelio, J.A.; Williams, C.; White, J. Cyber-physical security challenges in manufacturing systems. Manuf. Lett. 2014, 2, 74–77.
- Corallo, A.; Lazoi, M.; Lezzi, M.; Luperto, A. Cybersecurity awareness in the context of the Industrial Internet of Things: A systematic literature review. Comput. Ind. 2022, 137, 103614.
- Zhong, R.Y.; Peng, Y.; Xue, F.; Fang, J.; Zou, W.; Luo, H.; Ng, S.T.; Lu, W.; Shen, G.Q.P.; Huang, G.Q. Prefabricated construction enabled by the Internet-of-Things. Autom. Constr. 2017, 76, 59–70.
- Yaacoub, J.-P.A.; Salman, O.; Noura, H.N.; Kaaniche, N.; Chehab, A.; Malli, M. Cyber-physical systems security: Limitations, issues and future trends. Microprocess. Microsyst. 2020, 77, 103201.
- Zhai, Y.; Chen, K.; Zhou, J.X.; Cao, J.; Lyu, Z.; Jin, X.; Shen, G.Q.; Lu, W.; Huang, G.Q. An Internet of Things-enabled BIM platform for modular integrated construction: A case study in Hong Kong. Adv. Eng. Inform. 2019, 42, 100997.
- Niu, Y.; Lu, W.; Chen, K.; Huang, G.G.; Anumba, C.J. Smart Construction Objects. J. Comput. Civ. Eng. 2016, 30, 04015070.
- Junior, M.L.; Filho, M.G. Variations of the kanban system: Literature review and classification. Int. J. Prod. Econ. 2010, 125, 13–21.
- Mutis, I.; Paramashivam, A. Cybersecurity Management Framework for a Cloud-Based BIM Model. In Advances in Informatics and Computing in Civil and Construction Engineering; Springer: Cham, Switzerland, 2019; Volume 125, pp. 325–333.
- NIST CSWP 04162018; Framework for Improving Critical Infrastructure Cybersecurity. Version 1.1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018.
- Pender-Bey, G. The Parkerian Hexad; Information Security Program; Lewis University: Romeoville, IL, USA, 2019; p. 31.
- Reid, R.C.; Gilbert, A.H. Using the Parkerian Hexad to Introduce Security in an Information Literacy Class. In Proceedings of the 2010 Information Security Curriculum Development Conference, Kennesaw, GA, USA, 1–3 October 2010; pp. 45–47.
- Carlson, T. Information Security Management: Understanding ISO 17799; Lucent Technologies World Services: New Providence, NJ, USA, 2001; p. 18.
- Boyes, H. Resilience and Cyber Security of Technology in the Built Environment; Institution of Engineering and Technology: London, UK, 2013.
- Boyes, H.; Hallaq, B.; Cunningham, J.; Watson, T. The industrial internet of things (IIoT): An analysis framework. Comput. Ind. 2018, 101, 1–12.
- Boyes, H. Security, Privacy, and the Built Environment. IT Prof. 2015, 17, 25–31.
- Turk, Ž.; de Soto, B.G.; Mantha, B.R.; Maciel, A.; Georgescu, A. A systemic framework for addressing cybersecurity in construction. Autom. Constr. 2021, 133, 103988.
- Gammack, J.; Hobbs, V.J.; Pigott, D. The Book of Informatics; Thomson: Toronto, ON, Canada, 2007.
- Tiwari, A.; Batra, U. Blockchain Enabled Reparations in Smart Buildings Cyber Physical System. Def. Sci. J. 2021, 71, 491–498.
- Turk, Ž. Ten questions concerning building information modelling. Build. Environ. 2016, 107, 274–284.
- Redmond, A.; Hore, A.; Alshawi, M.; West, R. Exploring how information exchanges can be enhanced through Cloud BIM. Autom. Constr. 2012, 24, 175–183.
- Thomas, L.W.; McDaniel, J.B. Legal Issues Surrounding the Use of Digital Intellectual Property on Design and Construction Projects, No. 58; National Academies Press: Washingdon, DC, USA, 2013.
- Turk, Ž.; Klinc, R. Potentials of Blockchain Technology for Construction Management. Procedia Eng. 2017, 196, 638–645.
- Ammous, S. Blockchain Technology: What Is It Good for? SSRN Scholarly Paper ID 2832751; Social Science Research Network: Rochester, NY, USA, 2016.
