Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Banks were the primary players in the financial services landscape. However, as a result of technological and entrepreneurial advancements, new business models have emerged, introducing new participants such as start-ups and technology firms into to the mix. This development has significantly altered how businesses and retail customers manage their finances. These new disruptive companies, as well as the components that contributed to it, are now commonly referred to as “Fintech”.
- blockchain
- fintech
- use-cases
- security
- privacy
- cryptography
- smart contract
1. Introduction
1.1. The Fintech Ecosystem
The Fintech ecosystem is composed of a diverse range of players who are all committed to innovating, increasing the competition in the financial sector, ultimately benefiting the welfare of clients and boosting economic productivity. In [1], Lee and Shin highlighted five distinct components of the Fintech ecosystem: Fintech startups, technology developers, government, financial stakeholders, and traditional financial institutions.
The last decade has witnessed several technological upheavals involving domains such as social media [2][3], artificial intelligence [4][5][6], big data and cloud computing [7][8], augmented/virtual reality [9][10], and most notably blockchain [11]. Based on the applications and innovation of Fintech [12], one can classify it into numerous verticals, including: payments and banking, investments and capital markets, lending, crowdfunding, insurance services and loyalty programs (as shown in Figure 1).
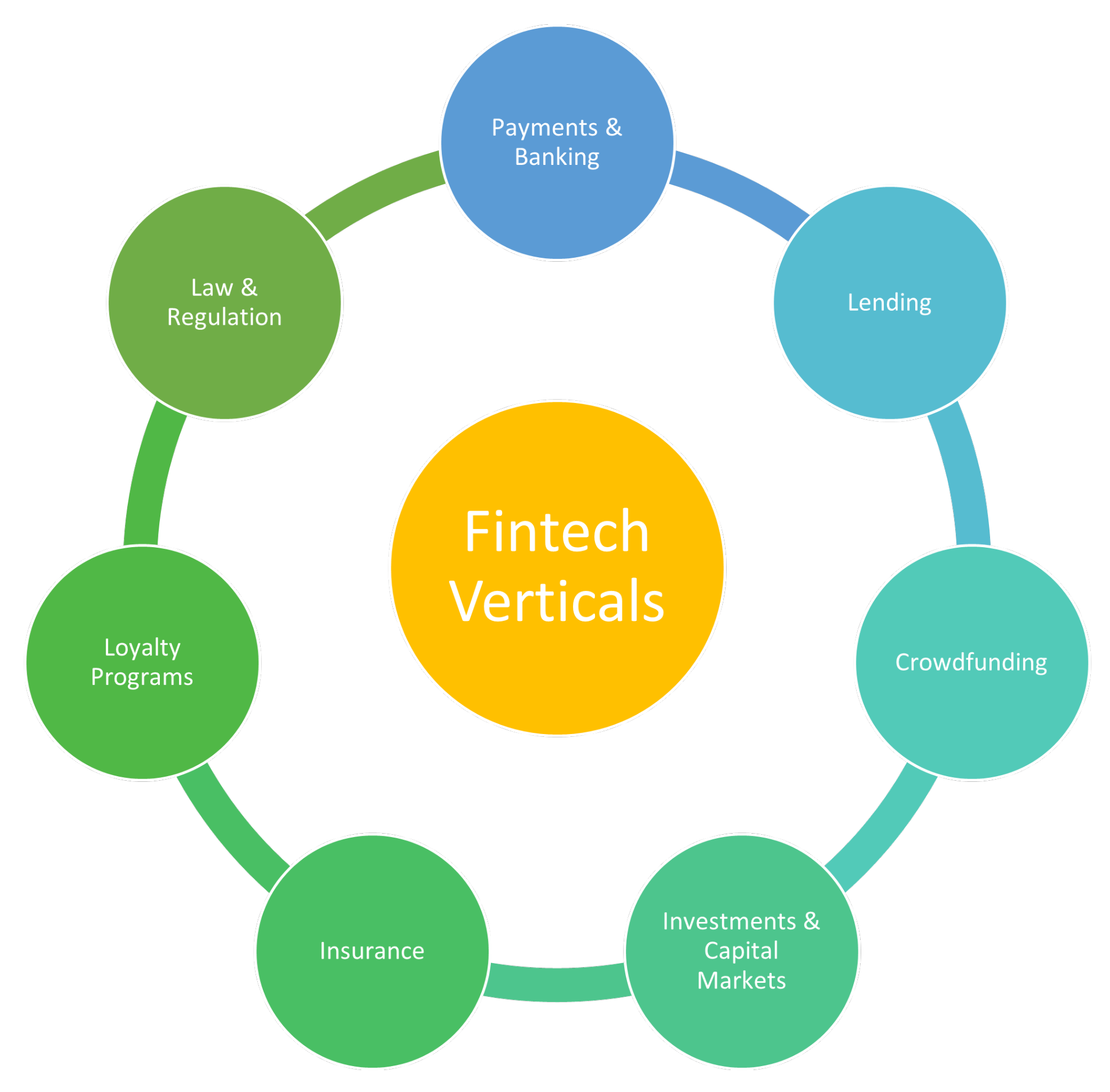
Figure 1. Fintech Verticals.
1.2. What Is Blockchain?
In 2008, the pseudonym Satoshi Nakamoto, who is the inventor of the cryptocurrency Bitcoin, published a white paper titled “Bitcoin: A Peer-to-Peer Electronic Cash System” [13]. The paper described in detail a payment system in which people would directly send/receive payments to/from each other. The technology illustrated a mechanism by which payments could be performed securely without any intermediary financial institution. Arguably, Bitcoin was the world’s first decentralized public ledger and it has since gained global status around the world.
The underlying technology standing behind the success of Bitcoin is the blockchain technology. This technology has also recently become a hot topic for researchers and been argued to be an even more revolutionizing phenomenon than Bitcoin.
Simplistically, the blockchain or distributed ledger technology(DLT) as defined in the Bitcoin whitepaper is a public, trusted and shared ledger, which is distributed to all participants in a community over a peer-to-peer network. In this community, people may or may not know each other, however, each member maintains his/her own copy of the information and all members must collectively validate any change on the blockchain. This removes the need for an intermediary third party. Blockchain is comprised by a continuously growing list of records called blocks that contain transactions. Blocks are protected from tampering by employing cryptographic hashes and consensus mechanisms. This allows the blockchain to be a transparent system of machines that originates and preserves the truth.
2. Blockchain Platforms in Fintech
2.1. How Blockchain Transforms Fintech Industry?
The Fintech industry in the last decade has seen a large number of transformations due to the disruption in various technologies like Artificial Intelligence, Cloud computing and Blockchain. Specifically with blockchain, the amount of disruption spans across all the Fintech verticals.
2.1.1. Disintermediation
Conventional banking methods involve dependency on intermediaries at all levels. Every transaction requires a counter-party in order to process. This causes bottlenecks and systems prone to single points of failure. Disintermediation refers to the reduction of the use of intermediaries between producers and consumers. The essence of blockchain is to induce decentralization into this fintech workflow in effect eliminating the middleman. In a blockchain network, there is no single entity that controls the transactions. Depending on the chosen consensus mechanism, the network as a whole agrees upon the state changes in a trustless manner.
2.1.2. Immutability and Transparency
A principal challenge in the Fintech industry is the lack of visibility to the consumers. Consider any sector like Trade Finance or Cross-border payments, the consumer is walking blind with no intuition as to the fees structure or the resources available for usage. Transparency acts as pillar that can bridge gap between the customer and financial institutions. Blockchain is powerful in increasing transparency as no one party controls the information processed in the network and cannot be manipulated at the whim of an entity. Every transaction that updates the state is recorded by either all the network participants or the involved parties depending on the choice of architecture.
2.1.3. Timeliness
Automation and instant execution of traditional contracts has been one of the focus areas for the past few years. Traditional financial contracts usually take 1–4 days for execution with the added manual intervention which can be as part of the remittance system or escrow or due to the requirement of physical presence for a signature. With the introduction of smart contracts, people are able to achieve instant transactions along with the substitution of the escrow and use of digital signatures.
2.1.4. Cost Optimization
Time can always be attributed to money. The cutting down of middlemen, making the process visible to all and reducing the time evolves into the introduction of new business models with upgraded cost structures. The benefits around cost can be ascribed to the reduced infrastructure costs, operation costs, documentation costs and transaction costs. Several studies [14][15] suggest that around 20 billion USD cost savings can be observed in areas of cross-border payments, trade finance and regulatory compliance.
2.1.5. Privacy and Security
Fintechs in general deal with highly-sensitive data related to both individuals and enterprises. Fraud, security breaches and cyber-attacks are the top threats to the rise of Fintech. With most of the Fintech services going online enterprises collect tremendous amounts of data about customers and insights. Protecting and providing this data to the relevant parties in a secure manner is also a challenge. With the usage of cryptographic primitives imbibed in the blockchain infrastructure, the ability to make any data accessible to the authorized individuals without any leakage is easier.
2.2. Classification of Blockchain Platforms
Consensus: A blockchain is a distributed ledger system maintained by a network of nodes. As ledger data are changed, each of these parties must agree on the authenticity of the revisions. Consensus mechanisms for blockchain networks are composed of a set of rules and principles that facilitate agreement [16]. Each blockchain network has its own consensus algorithm. There are two extensively utilized consensus algorithms across major blockchain networks. The first is proof of work (POW) [13], which is employed in both the Bitcoin and Ethereum networks at the moment. POW requires participants to mine blocks and attach them to the chain once they are confirmed as valid. These blocks must be provided in such a way that the block’s hash begins with a certain number of zeros. The count is determined by a difficulty level that varies according to the network’s congestion. As the difficulty of the block grows, the effort required to produce it can become exponentially more difficult. While proof of work enables an unbiased selection of miners, it comes with a slew of downsides. Specifically, the process of producing the block consumes a lot of energy, and the network is also vulnerable to 51 percent attacks [17]. Another extensively used algorithm is Proof of Stake (POS) [18]. Ethereum is expected to transition to a fully POS network in the last quarter of 2022. In POS, instead of miners, validators are chosen according on a consensus rule. By incorporating the network’s transactions, the chosen validator offers the block for the current round. Other validators in the network can monitor and certify the correctness of the present validator’s work. Even POS has drawbacks, such as the nothing at stake problem and long-range attack [19]. As a result, it is up to the network participants to decide which consensus to use based on the requirements of the product or platform.
Smart contracts: Smart contracts are rules that can be automatically enforced upon the fulfilment of specified criteria without the intervention of a third party. Each blockchain contains its own virtual computer, which each network participant must operate in order to analyse and process transactions. People can interface with the virtual machines using a low-level assembly language or a high-level language such as Solidity, which supports the Ethereum Virtual Machine (EVM). Thus, the support for smart contracts and the high-level language can also play a role in determining which blockchain network is most suited for a given use case.
Transaction Model: The transaction model defines the internal structure of the distributed ledger. This also influences how modifications to the ledger are stored in the ledger’s memory. There are two widely used transaction models: Unspent Transaction Outputs (UTXO) and account-based. Each transaction in the UTXO model results in the production of additional outputs. These outputs are the only ones that can be used in subsequent transactions. For instance, suppose Alice owes Bob 30 BTC in Bitcoin. She can use an existing output tag of 40 BTC to send 30 BTC to Bob. The transaction’s outputs would be a new output tag containing 30 BTC owned by Bob and 10 BTC held by Alice. Alice may use the ten bitcoins in any subsequent transactions. She is unable to use the earlier 40 BTC output tag because it is no longer valid. The same holds true for Bob. In contrast, the account model requires the system to keep a tree of accounts and their balances. Whenever a transaction between two accounts is issued, like in the preceding example, if the transaction is legitimate, meaning Alice has at least 30 BTC in her account balance and is permitted to handle the account, she can transfer it to Bob. On Bob’s side, he should have an account at the address specified by Alice in the transaction. In this situation, there is no need to track any output tags. However, each model offers a number of distinct advantages and downsides.
Governance: On-chain governance and off-chain governance are two distinct types of blockchain governance [20]. On-chain governance refers to the decentralised enforcement of protocol rules and smart contracts. In these instances, governance norms will be referred to as Decentralized Autonomous Organizations (DAOs) [21]. Off-chain governance, on the other hand, refers to the rules and decision-making processes followed by the protocol’s owners or the network’s members as a whole. Off-chain governance methods on public blockchains include discussions on social media, online forums, conferences, and other events. In particular, governance systems in enterprise scenarios should incorporate both off-chain and on-chain components.
Extensibility: Due to the fact that blockchain is being used in the Fintech ecosystem, it must demonstrate durability, upgradeability, and maintainability features. This is commonly referred to as extensibility. Since the inception of blockchain technology, the majority of networks have encountered a variety of challenges, both in terms of protocols and hacks. However, these same networks have overcome these obstacles. They have modernised the protocols. Issues with the codebase have been resolved. This capability is critical for a technology that is still in its infancy. Additionally, the presence of heterogeneous blockchains and DLT networks necessitates the establishment of communication between these systems. This interoperability situation adds complexity, yet it is a necessary condition for advancing the use of DLT in enterprise contexts.
Currency or Token: Numerous transactions are carried out on blockchains, which necessitates resource allocation by participants. In order to operate the network decentralised and equitably handle all transactions from all participants, the network must have incentive systems. These incentive mechanisms are reinforced by the use of either a system-wide native currency or a token that may be connected with ownership. Ether (ETH) is an example of a native currency, whereas ERC20 is an example of a token on the Ethereum network. The distinction is that actions within the virtual machine must be compensated in local currency, whilst certain apps are valued in ERC20.
Privacy: At all levels of the terrain, financial organisations are extremely concerned about privacy. With transparency being a primary purpose of blockchains, privacy is a critical concern. When it comes to financial services, privacy may be characterised in three ways from the user’s perspective [22], including: transactional confidentiality, user anonymity, and unlinkability. Transactional confidentiality implies that no information about user transactions may be released without prior consent. Any malicious assaults on the system as a whole must nonetheless protect the system against user data leakage. Secondly, user anonymity requires that except for the user and the participating party in a given transaction, no other entity in the network should be aware of any specifics of the transaction, including the sender and receiver’s identities. Finally, unlinkability implies that the inability of users to be associated with transactions. The ability to link a specific user to a transaction might result in the user’s anonymity being compromised and all transactions related with the user being disclosed.
Security: On the other side, security needs might be classified similarly to privacy requirements. At the system level, it is required that the distributed ledger should be immutable and reliable, that is, the ledger should be consistent among network participants. No contradictions should occur as a result of the reconciliation, clearing, and settlement processes. It is also required that the system must provide a high availability. The majority of transactions are intended to have low latency and to complete without causing system disruption. At the transactional level, the transaction integrity must be maintained throughout the ledger’s existence. In the Fintech sector, online transactions mostly include equity bonds, investments, and different high-risk assets. Thus, intentional falsification and forgery of transactions should be prohibited. Last but not least, preventing double-spending attacks on blockchain-based payment systems must be a desirable security feature.
Scalability: When it comes to blockchain performance, two critical variables are monitored: transaction throughput and confirmation delay. Centralized payment systems, such as banks, achieve a high level of optimization in terms of these two criteria. Whereas, blockchains confront significant issues in maintaining decentralisation. Scalability concerns extend deep into the system’s numerous levels. This might be due to consensus constraints, the ledger state’s structure, or reliance on external players, all of which result in confirmation delays. Thus, a project may be differentiated from others based on the solution chosen for a particular scalability challenge.
2.3. Comparison between Platforms
2.3.1. Bitcoin
Bitcoin [13] is the first public blockchain that does not require users any permission to join the network. The consensus mechanism is based on proof-of-work. Miners use energy to validate transactions and construct new blocks. Miners receive rewards in the form of local currency BTC for successfully mining valid blocks. Scripting languages enable the inclusion of complicated transactions that go beyond money. Scalability is a bottleneck of Bitcoin network. At the moment, it only supports around seven (7) transactions per second. To anonymize transactions, coin mixing or tumblers, and shadow addresses can be utilised [23]. Mixing is a term that refers to a service that jumbles bitcoins in private pools and distributes them to the appropriate recipient anonymously. The term “shadow address” refers to a feature built into the protocol that generates a new address for the sender with each transaction. Payments are the most often utilised use case for Bitcoin.
2.3.2. Ethereum
Ethereum [24] is yet another permissionless blockchain. Similar to Bitcoin, Ethereum currently uses the proof-of-work consensus mechanism to achieve an agreement among participants in the network. The primary distinction is the inclusion of smart contracts and the use of an account-based storage approach. On top of Ethereum, smart contracts may be developed using a variety of high-level programming languages such as Solidity. The network achieves a throughput of roughly 15 transactions per seconds, which is somewhat faster than bitcoin. On this network, decentralised applications (Dapps) are extremely easy to develop. At the time of writing, there have been almost 3000 Dapps developed on Ethereum (https://www.stateofthedapps.com/stats, accessed on 15 March 2022). The native currency is Ether (ETH). For privacy, Zero-Knowledge proof contracts can be used to create private transactions. In order to avoid a high energy consumption by the proof-of-work consensus mechanism, Ethereum is scheduled for an upgrade to proof-of-stake mechanism in 2022.
2.3.3. Cardano
The project, dubbed “Ethereum Killer”, orders and validates transactions using the Ouroboros protocol, a proof-of-stake consensus mechanism [25]. It employs a multi-layered approach, with the settlement layer in charge of currency conversion and the computation layer in charge of smart contract execution. As a result, the Cardano network may be easier to be upgraded compared to Bitcoin and Ethereum networks. For transactions, the network employs the UTXO concept. It is capable of scaling up to 257 transaction per second. For privacy, Cardano implemented Zero-Knowledge proofs, allowing private transactions. ADA is the network’s native currency, which is used to incentivize validators. Cardano’s road to acceptance is still long, since the network currently has just 62 decentralised applications (dapps), which is too small compared to Ethereum (https://cardanocrowd.com/dapps, accessed on 15 March 2022).
2.3.4. IOTA
Aimed at revolutionising the Internet of Things (IoT), IOTA [26] facilitates decentralised micro-payments between IoT devices. This network implements tangle, that is based on the Directed Acyclic Graph (DAG) data structure. There are no miners to validate transactions in the IOTA network, instead, it deploys a fast probabilistic consensus mechanism. Each node. issuing a new transaction, must approve two previous transactions. In the original design, IOTA also operates a coordinator node to achieve the consensus. It is thus criticized as a centralized network. It also did not offer smart contracts due to lack of absolute timestamp. Those issues were addressed in the IOTA’s newest version, launched in April 2021. The system enables smart contracts by supporting EVM, all Solidity contracts can thus be implemented on IOTA. The network is capable of around 1500 transactions per second. Coin mixing is a technique used to conceal transactions. IOTA is the native currency used for rewards and payments in the network.
2.3.5. Algorand
A public blockchain that employs a variation of the proof-of-stake consensus mechanism known as Pure proof-of-stake [27]. ALGO is the currency that is dispersed throughout the network’s validators. Payments-focused network capable of up to 1000 transactions per second with a five second finality. The Algorand network is built on a tiered structure, in which the first layer performs straightforward smart contracts pertaining to payments. The second layer is responsible for the execution of sophisticated smart contracts. The network was launched in 2019 and is funded by the Algorand Foundation, a non-profit organisation. Algorand is also planning to expand into the permissioned space with their enterprise blockchain platform.
2.3.6. Hyperledger Fabric
One of the most popular projects under the Hyperledger umbrella [28]. It is a permissioned distributed ledger that is well-suited for corporate use cases. Hyperledger Fabric enables the creation of smart contracts in the form of chaincode. Its design is very modular with many software components, minimizing the complexity of each component as well as the overall module-dependency network. The network does not have its own currency, and is able to perform approximately 3000 transactions per second. For privacy, Hyperledger Fabric establishes consortiums amongst members through the use of channels. There is also an option to have a private database contained within a node for the purpose of conducting private data transactions.
2.3.7. R3 Corda
The brainchild of the R3 Foundation [29], permits the creation of a privacy-focused permissioned blockchain in which organisations may deal directly with one another. This enables parties to conduct private transactions over the network. Similar to Bitcoin, it uses the UTXO concept for transactions. Additionally, legal contracts can be attached to transactions. Corda uses Kotlin, a cross-platform programming language to implement smart contracts. Due to the restriction on private transactions, throughput is limited to between 15 and 1678 transactions per second, depending on the participant structure. Corda implements two types of consensus mechanisms: transaction validity and transaction uniqueness. While the former requires contractual validity of the transaction and all its dependencies, the later prevents double-spends. In transaction validity, parties must first verify the relevant contract code and present all needed signatures. Otherwise, in transaction uniqueness, the parties must be assured that the transaction in issue is the sole consumer of all specified input. This procedure entails ensuring that no subsequent transaction consumes any of the agreed states.
2.3.8. Quorum
Quorum [30][31] is a private and permissioned network built on top of an Ethereum. It is based on the Go Ethereum client and utilises voting-based consensus. The unique feature of Quorum is that it can classify transactions as private or public based on an identity. As a result, the user initiating the transaction will have the option of making it private or public. One of Quorum’s key goals is to maximise the usage of existing technologies rather than reinventing the wheel. Due to the fact that it is a fork of Ethereum, it supports EVM and smart contracts. Consensys bought Quorum from its original owner, JPMorgan Chase, in 2020. Currently, the network supports around 900 transactions per second, depending on configuration and setup.
2.3.9. Multichain
Mutlichain [32] is a Bitcoin core fork. It was created to facilitate the establishment of both public and private blockchain networks. Multichain provides several configuration options for configuring the network. Its primary purpose, as implied by its name, is to link and interoperate with several chains. Multichain implements privacy using streams. Participants can establish streams between themselves in order to share confidential data. The performance may thus be affected by the network settings and the amount of streams produced. Due to the fact that it is built on Bitcoin core, this protocol does not yet enable smart contracts and the chain operates using the UTXO transaction paradigm. Round-robin selection of validators for mining is used. During the initial setup process, custom native assets can be developed. At the moment, the network has a throughput of roughly 1000 transactions per second.
2.3.10. Diem
Diem [33] is a private permissioned blockchain network that is established with a small number of validators. DiemBFT is the consensus technique for validator election. The network is controlled by an entity called Association, which operates as a central authority. The Association account is primarily responsible for managing network memberships and setup. Diem made a significant contribution with the Move smart contract language. It contains several intrinsic safety attributes and tools that were created to facilitate the creation of secure smart contracts from the start. The objective was to make payments simple and flexible. Diem is the network’s native currency. Except for the fact that the network is private, there are no intrinsic private transactions. According to a recent performance measurement on the testnet, Diem had a throughput of roughly 3 transactions per second, which is much slower than other blockchains. There has never been a mainnet from Diem till today. The project was formerly held by Meta before being acquired by Silvergate Capital (https://www.bloomberg.com/news/articles/2022-01-31/meta-backed-diem-association-confirms-asset-sale-to-silvergate, accessed on 15 March 2022). As a result, the project has been halted for an extended length of time with no updates.
3. Taxonomy of Use Cases
3.1. Digital Identity
Blockchain technology can be used to issue digital identity and credentials such as birth certificates, driver licences, etc. in a secure and verifiable way. Indeed, in the simplest identity model, the organization which provides services will issues a digital credential that its users can use to access its service. This identity model requires a trust between user and the organization, typically established through a password-based authentication. This is a centralized and insecure approach to online interactions, and although multi-factor schemes enhance the security, but they add friction that reduce user adoption and productivity.
3.2. Payments
Payments, especially cross-border payments between individuals and SMEs in developing countries are facing high cost and long delays. Typically, each cross-border transaction is conducted across a network of corresponding banks or money transfer providers without a central clearing system. Transaction fees are high due to charges from payor’s and payee’s institutions; inter-bank, cross-border transfer. There is a significant amount of overhead and negotiation that is required to set up and facilitate transactions across two legal jurisdictions that is partially solved if parties are willing to agree to use decentralised platforms like Ethereum as an intermediary.
3.3. Digital Currencies
The invention of digital currencies has brought about the pressure of innovation in the fields of Banking, Payments, and Investments. To be considered a currency by the definition in economics, it must meet the following requirements [34]: be a unit of account, a medium of trade, and a store of wealth. Digital currencies are a form of money that are expressed as a string of bits transmitted as a message via a network that validates the message’s validity using a variety of processes. Four classes of digital currencies exist: Cryptocurrencies, Stablecoins, Platform-based digital currencies(PBDC), and Central bank digital currencies(CBDC). Each variety has distinct benefits and drawbacks. To begin, cryptocurrencies are digital assets established on public and open blockchains that may be utilized similarly to traditional currency. There is no central authority in charge of currency supervision or regulation. The code is the law, and it establishes the laws governing the money. There are around 15,000 cryptocurrencies in existence as of December 2021, with a market valuation of $2.28 trillion USD [35].
3.4. Investing
3.4.1. Decentralised Exchanges
A critical challenge that cryptocurrencies faced early on was the issue of centralised exchanges. Many pointed out and rightly criticized that how could the technology which constantly touted its decentralisation could be truly called as such if it relied on centralised entities in order to purchase and sell. Thus many open discussions were held to solicit ideas from the community on how to build decentralised exchanges (DEXs). Overtime, it became abundantly clear that the issue was non-trivial. Some of the first iterations of DEXs resembled a mere replication of the traditional order book model [36] that most people who have a investment account would be familiar with. There would be two sides of the order book, a collection of bids of buyers willing to purchase a set amount at a set price, and a collection of asks of sellers willing to sell a set amount at a set price. An order would go through if either a buy or seller were willing to take the price set by the bids and asks. However, given the nature of transaction creation in the blockchain space, pending transactions would be totally transparent and be open to frontrunning, a typically illegal trading strategy that involves in exploiting and scalping the market to raise or decrease prices in the scalper’s favour to the disadvantage of an honest buyer or seller.
3.4.2. Decentralised Finance
Current consumers in the conventional financial ecosystem are unaware of the majority of accessible products and are unfamiliar with the laws governing these assets. Decentralized Finance (DeFi), often known as the lego of finance, provides the end user with the transparency, control, and accessibility that centralized finance lacks. Asset exchanges, loans, leveraged trading, decentralized governance, stablecoins, options, and derivatives are just a few of the items that fall under the DeFi umbrella. The previous subsection’s discussion of decentralized exchanges falls within the DeFi taxonomy as well.
3.5. Infrastructure/Value-Add Services
3.5.1. Decentralized Oracles
Blockchain networks are like closed circuits. All the data that smart contracts can be associated with is located and maintained by the nodes of the network. There is no way in-built into the protocol, as to how smart contracts can interact with external data as part of certain computations. Oracles are entities external to a blockchain network that can pipe information into the network.
3.5.2. Decentralized Storage
The internet generates massive amounts of data that is then served to the users from all over the world using multitude of services like cloud storage, peer-to-peer networks, intranet servers etc. When it comes to storage and retrieval of financial data it is crucial to maintain security, latency and availability at all times. Reliance on a centralized system will always have a backdoor through which an adversary can easily access and manipulate the data. Another evident issue with cloud storage is the concentration of few technology companies that have the capacity to build massive data centers. Due to this restriction, the cost around storage within these known servers increases with the space and availability requirements. Recently, with the inclusion of General Data Protection Regulation (GDPR) restrictions in some countries, the regulations around how and where to store the data are also changed. Data privacy is becoming a basic intuition needed when thinking about storage services.
Decentralized storage [37][38][39] is an option that can overcome the above mentioned constraints and is gaining momentum with the influx of blockchain use-cases. This enables trustless storage and allows for splitting the data and replicating the data across the world along multiple servers. These servers could be like a standalone user machine that is connected over a network with some pre-allocated hard disk space. The control of the data is not with the service provider anymore, rather with the user itself. Based on the persistence or incentive mechanisms used for data, different storage solutions have been proposed [40][41][42][43][44][45][46].
3.5.3. Node-as-a-Service
In the Fintech ecosystem, even in centralized infrastructure settings, cloud service providers such as Amazon, Azure, or Google are relied upon. They generally do not host servers on their own, as this entails a significant amount of engineering effort in terms of upkeep. In the blockchain scenario, the network is composed of several types of nodes based on the server’s capability. The majority of procedures fall into one of three categories: Archive Node—A node that maintains a history of data on the blockchain dating all the way back to the network’s genesis block. Full Node—A node that may purge data on a periodic basis and rely on the Archive node to verify the legacy data. Light Node—A client-facing node that does not store data but communicates with the Full Node to calculate and deliver blocks to the Full Node for storage. Light nodes keep extremely low data due to the fact that their infrastructure may consist of devices such as mobile phones. The user interface of any network of decentralized apps will communicate with the nodes to obtain data from the blockchain. Depending on the storage capacity, experience, and level of control required for the application, clients can either self-host or use a node-as-a-service (NaaS) provider. By utilizing a NaaS service, the duty for maintaining the node is eliminated. The client is not concerned about storage, bandwidth, or technical effort. Although customers of this type of service must never reveal their private keys. Users can interact with their data using an API given by the NaaS provider. Numerous services have existed since the concept of NaaS was born. Alchemy [47], Ankr [48], BlockDaemon [49], and Chainstack [50] are just a few of the most well-known applications in this domain. They offer a variety of service kinds depending on their business models.
4.6. Online Marketplaces and Supply Chains
3.6.1. Online Marketplaces
Historically, markets had four objectives: Match-making—the process of connecting buyers and sellers; transaction settlement—depending on the goods or services exchanged between a buyer and seller, settlement may include payment or the exchange of another good or service; service delivery—the end result of a transaction settlement is the delivery of the product to the buyer; and dispute resolution—the crux of marketplaces is to provide a mechanism for resolving disputes between buyers and sellers. Since the dawn of the internet, centralized marketplaces have existed. The majority of these businesses rely on reputation as their trust mechanism, which presents a significant barrier to entry for new merchants or consumers. Additionally, there are several middlemen who exert influence over the marketplaces and operate in the system’s favor. An example of this, is when an intermediary constantly connects with the highest bidding seller in order to benefit from the deal. Client privacy is not maintained in the centralized scenario as information is with a central entity. Payments could become a problem as well when interacting with sellers and buyers across border. Finally, there is the issue of terminating the marketplace, which is not difficult to do when everything is controlled by a small number of intermediaries.
3.6.2. Supply Chain Finance
The 2008 global financial crisis exposed numerous vulnerabilities in supply chains and associated capital management. During this time period, interest in Supply Chain Finance (SCF) began to grow. SCF [51] is the process of optimizing financial structures and processes within the supply chain ecosystem. The optimization process is primarily concerned with managing the working capital and liquidity associated with corporate institutions’ supply chain procedures. The basic flow of SCF is depicted in Figure 2, along with the parties involved. SCF enables risk management by facilitating the management of cash flows between customers, suppliers, and service providers.
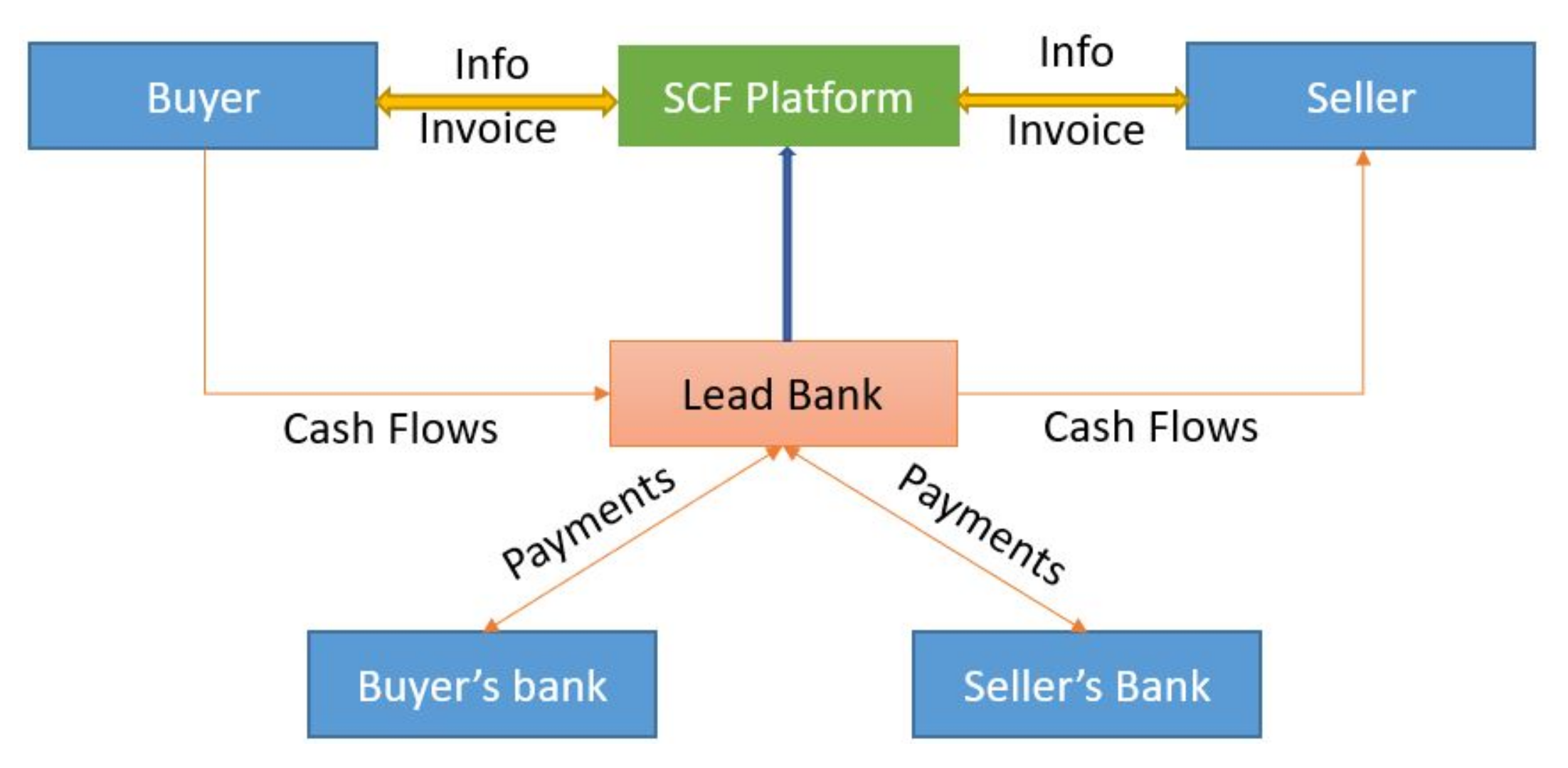
Figure 2. Workflow of SCF.
3.7. Corporate Governance
Corporate governance [52][53] is primarily concerned with the administration of an organization’s economic and social objectives. Engagement of stakeholders is critical in this scenario. Although corporate governance has existed for a long period of time, it continues to face numerous fundamental issues. To begin, businesses can profit from short-term fluctuations in share prices and accounting methods. Several instances include violations of ethics, lack of openness, and conflicts of interest. For shareholders, issues arise around accountability and ownership transfer, which are frequently associated with expensive costs. In terms of decision-making, present procedures rely heavily on manual processes, making it easier for actors to be persuaded and collude in order to commit systemic malpractices. This is where blockchain enters the fray. Blockchain has completely transformed the field of governance. Multiple governance mechanisms have been established at various levels of the blockchain architecture, which enables corporate governance structures to be executed on these platforms.
3.8. Crowdfunding
Crowdfunding is another area in which substantial sums of money are transferred. In general, crowdfunding [54] is the process through which an individual, a group of individuals, or an organization solicits cash for a specific cause via an internet platform. Michael Sullivan coined the word crowdsourcing for his fundavlog project (https://socialmediaweek.org/blog/2011/12/a-social-history-of-crowdfunding/, accessed on 25 February 2022). Globally, crowdsourcing generated approximately $5.5 billion USD in 2017 and $10.2 billion USD in 2018. According to the Global Crowdfunding market study 2022 (https://www.marketwatch.com/press-release/crowdfunding-market-by-growth-opportunities-2022—top-key-players-analysis-by-demand-status-industry-size-and-share-forecast-with-covid-19-impact-analysis-on-regional-trends-2024-2022-03-07), accessed on 25 February 2022, it is predicted to grow at a continuous rate of 18 percent, reaching $124.85 billion USD in revenue. According to the report, a significant driver is the rising use of social media platforms for free fund raising efforts and the increased accessibility to cash enabled by technological innovations such as blockchain. Numerous market models [55] have been employed throughout crowdfunding’s history.
This entry is adapted from the peer-reviewed paper 10.3390/cryptography6020018
References
- Lee, I.; Shin, Y.J. Fintech: Ecosystem, business models, investment decisions, and challenges. Bus. Horiz. 2018, 61, 35–46.
- Franco-Riquelme, J.N.; Rubalcaba, L. Innovation and SDGs through Social Media Analysis: Messages from FinTech Firms. J. Open Innov. Technol. Mark. Complex. 2021, 7, 165.
- Gomber, P.; Kauffman, R.J.; Parker, C.; Weber, B.W. On the fintech revolution: Interpreting the forces of innovation, disruption, and transformation in financial services. J. Manag. Inf. Syst. 2018, 35, 220–265.
- Jakšič, M.; Marinč, M. Relationship banking and information technology: The role of artificial intelligence and FinTech. Risk Manag. 2019, 21, 1–18.
- Belanche, D.; Casaló, L.V.; Flavián, C. Artificial Intelligence in FinTech: Understanding robo-advisors adoption among customers. Ind. Manag. Data Syst. 2019, 119, 1411–1430.
- Ashta, A.; Herrmann, H. Artificial intelligence and fintech: An overview of opportunities and risks for banking, investments, and microfinance. Strateg. Chang. 2021, 30, 211–222.
- Meng, S.; He, X.; Tian, X. Research on Fintech development issues based on embedded cloud computing and big data analysis. Microprocess. Microsystems 2021, 83, 103977.
- Trelewicz, J.Q. Big data and big money: The role of data in the financial sector. It Prof. 2017, 19, 8–10.
- Pant, S.K. Fintech: Emerging Trends. Telecom Bus. Rev. 2020, 13, 47–52.
- Tan, S.; Yang, Y.; Leopold, C.; Robeller, C.; Weber, U. Augmented Reality and Virtual Reality: New Tools for Architectural Visualization and Design. In Research Culture in Architecture; Walter De Gruyter: Berlin, Germany, 2019; pp. 301–310.
- Fernandez-Vazquez, S.; Rosillo, R.; De La Fuente, D.; Priore, P. Blockchain in FinTech: A mapping study. Sustainability 2019, 11, 6366.
- Imerman, M.B.; Fabozzi, F.J. Cashing in on innovation: A taxonomy of FinTech. J. Asset Manag. 2020, 21, 167–177.
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Technical Report. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 3 March 2022).
- Kfoury, B. The Role of Blockchain in Reducing the Cost of Financial Transactions in the Retail Industry. Technical Report. 2021. Available online: http://ceur-ws.org/Vol-2889/PAPER_02.pdf (accessed on 15 March 2022).
- Mori, T. Financial technology: Blockchain and securities settlement. J. Secur. Oper. Custody 2016, 8, 208–227.
- Zhang, C.; Wu, C.; Wang, X. Overview of Blockchain consensus mechanism. In Proceedings of the 2020 2nd International Conference on Big Data Engineering, Shanghai, China, 29–31 May 2020; pp. 7–12.
- Vukolić, M. The Quest for Scalable Blockchain Fabric: Proof-of-Work vs. BFT Replication. In Open Problems in Network Security. iNetSec 2015. Lecture Notes in Computer Science; Camenisch, J., Kesdoğan, D., Eds.; Springer: Cham, Switzerland, 2015; Volume 9591.
- Saleh, F. Blockchain without waste: Proof-of-stake. Rev. Financ. Stud. 2021, 34, 1156–1190.
- Nair, P.R.; Dorai, D.R. Evaluation of performance and security of proof of work and proof of stake using blockchain. In Proceedings of the 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Virtual, 4–6 February 2021; pp. 279–283.
- Reijers, W.; Wuisman, I.; Mannan, M.; De Filippi, P.; Wray, C.; Rae-Looi, V.; Cubillos Vélez, A.; Orgad, L. Now the Code Runs Itself: On-Chain and Off-Chain Governance of Blockchain Technologies. Topoi 2021, 40, 821–831.
- Chohan, U.W. The Decentralized Autonomous Organization and Governance Issues. 2017. Available online: https://ssrn.com/abstract=3082055 (accessed on 7 March 2022).
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. (CSUR) 2019, 52, 1–34.
- Chen, X.; Hasan, M.A.; Wu, X.; Skums, P.; Feizollahi, M.J.; Ouellet, M.; Sevigny, E.L.; Maimon, D.; Wu, Y. Characteristics of bitcoin transactions on cryptomarkets. In Proceedings of the International Conference on Security, Privacy and Anonymity in Computation, Communication and Storage, Atlanta, GA, USA, 14–17 July 2019; pp. 261–276.
- Wood, G. Ethereum: A Secure Decentralised Generalised Transaction Ledger; Technical Report; Ethereum & ETHCore: New York, NY, USA, 2016; Volume 151, pp. 1–32.
- Guides, T.S. Why Cardano ADA Deserves Your Attention—Cardano Cryptocurrency Strategy. 2018. Available online: https://tradingstrategyguides.com/cardano-cryptocurrency-strategy/ (accessed on 7 March 2022).
- Silvano, W.F.; Marcelino, R. Iota Tangle: A cryptocurrency to communicate Internet-of-Things data. Future Gener. Comput. Syst. 2020, 112, 307–319.
- Chen, J.; Micali, S. Algorand: A secure and efficient distributed ledger. Theor. Comput. Sci. 2019, 777, 155–183.
- Foundation, L. Hyperledger Fabric. 2015. Available online: https://hyperledger-fabric.readthedocs.io (accessed on 15 March 2022).
- Brown, R.G.; Carlyle, J.; Grigg, I.; Hearn, M. Corda: An introduction. R3 CEV 2016, 1, 14.
- Baliga, A.; Subhod, I.; Kamat, P.; Chatterjee, S. Performance evaluation of the quorum blockchain platform. arXiv 2018, arXiv:1809.03421.
- Consensys. Quorum Blockchain. 2022. Available online: https://github.com/ConsenSys/quorum (accessed on 15 March 2022).
- Greenspan, G. MultiChain Private Blockchain—White Paper. 2015. Available online: https://www.multichain.com/white-paper/ (accessed on 15 March 2022).
- Diem. Diem Blockchain. 2022. Available online: https://www.diem.com/en-us/ (accessed on 15 March 2022).
- Ali, R.; Barrdear, J.; Clews, R.; Southgate, J. The economics of digital currencies. Bank Engl. Q. Bull. 2014, 54, 276–286.
- Allen, F.; Gu, X.; Jagtiani, J. Fintech, Cryptocurrencies, and CBDC: Financial Structural Transformation in China. J. Int. Money Financ. 2022, 124, 102625.
- Liu, Y.; Vogel, S.; Zhang, Y. Electronic trading in OTC markets vs. centralized exchange. In Proceedings of the Finance Meeting EUROFIDAI-AFFI, Paris, France, 20 December 2018.
- Benisi, N.Z.; Aminian, M.; Javadi, B. Blockchain-based decentralized storage networks: A survey. J. Netw. Comput. Appl. 2020, 162, 102656.
- Casino, F.; Politou, E.; Alepis, E.; Patsakis, C. Immutability and decentralized storage: An analysis of emerging threats. IEEE Access 2019, 8, 4737–4744.
- Shah, M.; Shaikh, M.; Mishra, V.; Tuscano, G. Decentralized Cloud Storage Using Blockchain. In Proceedings of the 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI)(48184), Tirunelveli, India, 16–18 April 2020; pp. 384–389.
- Lakshman, A.; Malik, P. Cassandra: A decentralized structured storage system. ACM SIGOPS Oper. Syst. Rev. 2010, 44, 35–40.
- Vorick, D.; Champine, L. Sia: Simple decentralized storage. Retrieved May 2014, 8, 2018.
- Churyumov, A. Byteball: A Decentralized System for Storage and Transfer of Value. 2016. Available online: https://byteball.org/Byteball.pdf (accessed on 7 March 2022).
- Haeberlen, A.; Mislove, A.; Druschel, P. Glacier: Highly durable, decentralized storage despite massive correlated failures. In Proceedings of the 2nd Conference on Symposium on Networked Systems Design & Implementation, Boston, MA, USA, 2–4 May 2005; Volume 2, pp. 143–158.
- Wilkinson, S.; Lowry, J.; Boshevski, T. Metadisk a Blockchain-Based Decentralized File Storage Application; Technical Report, hal; Storj Labs Inc.: Atlanta, GA, USA, 2014; pp. 1–11. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.692.8781&rep=rep1&type=pdf (accessed on 7 March 2022).
- Ali, S.; Wang, G.; White, B.; Cottrell, R.L. A Blockchain-Based Decentralized Data Storage and Access Framework for PingER. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security And Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1303–1308.
- Ruj, S.; Rahman, M.S.; Basu, A.; Kiyomoto, S. BlockStore: A Secure Decentralized Storage Framework on Blockchain. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 1096–1103.
- Alchemy. 2022. Available online: https://www.alchemy.com/ (accessed on 7 March 2022).
- Ankr. 2022. Available online: https://www.ankr.com/ (accessed on 7 March 2022).
- BlockDaemon. 2022. Available online: https://blockdaemon.com/ (accessed on 7 March 2022).
- ChainStack. 2022. Available online: https://chainstack.com/ (accessed on 7 March 2022).
- Vousinas, G. Supply chain finance: Definition, modern aspects and research challenges ahead. In Supply Chain Finance: Risk Management, Resilience and Supplier Management; Tate, W., Bals, L., Ellram, L., Eds.; Kogan Page: London, UK, 2019; pp. 63–95. Available online: https://www.researchgate.net/publication/327981053_Supply_chain_finance_definition_modern_aspects_and_research_challenges_ahead (accessed on 7 March 2022).
- Singh, H.; Jain, G.; Munjal, A.; Rakesh, S. Blockchain technology in corporate governance: Disrupting chain reaction or not? Corp. Gov. Int. J. Bus. Soc. 2019, 20, 67–86.
- Yermack, D. Corporate governance and blockchains. Rev. Financ. 2017, 21, 7–31.
- Oguama, L. Fintech Credit Market—Crowdfunding: An Evaluation of Market Models. 20 September 2020. Available online: https://ssrn.com/abstract=3696044 (accessed on 7 March 2022).
- Shneor, R.; Zhao, L.; Flåten, B.T. (Eds.) Advances in Crowdfunding; Springer International Publishing: Berlin, Germany, 2020.
This entry is offline, you can click here to edit this entry!
