The Internet of Things (IoT) revitalizes the world with tremendous capabilities and potential to be utilized in vehicular networks. The Smart Transport Infrastructure (STI) era depends mainly on the IoT. Advanced machine learning (ML) techniques are being used to strengthen the STI smartness further. However, some decisions are very challenging due to the vast number of STI components and big data generated from STIs. Computation cost, communication overheads, and privacy issues are significant concerns for wide-scale ML adoption within STI. These issues can be addressed using Federated Learning (FL) and blockchain. FL can be used to address the issues of privacy preservation and handling big data generated in STI management and control. Blockchain is a distributed ledger that can store data while providing trust and integrity assurance. Blockchain can be a solution to data integrity and can add more security to the STI. While transmitting data, valuable information can be disclosed through the model parameters by reverse engineering. The disclosure of valuable data motivated researchers and developers to adopt known security and privacy defense methods, e.g., functional encryption and differential privacy, to FL.
- blockchain
- federated learning
- intelligence transportation system
- vehicular internet of things
1. Federated Learning and Blockchain for Security in Vehicular Networks
| Limitation of FL | Solution Provided by Blockchain-Enabled FL |
|---|---|
| FL is not suitable for the aggregating updates while selecting vehicles and maintain GM. |
Blockchain provides a solution to all these problems through its decentralized storage and further maintaining the FL model. Blockchain can be used to store GM. |
| High speed is required for the server to gather information and update vehicles (clients). |
|
| Express bandwidth is required. | |
| Skewing in GM can also be expected because of biasness. |
|
| FL cannot detect the internal attacks by malicious node while updates are gathered from every vehicle in a network causing GM unable to link up. |
2. Federated Learning and Blockchain for Privacy Preservation in Vehicular Networks
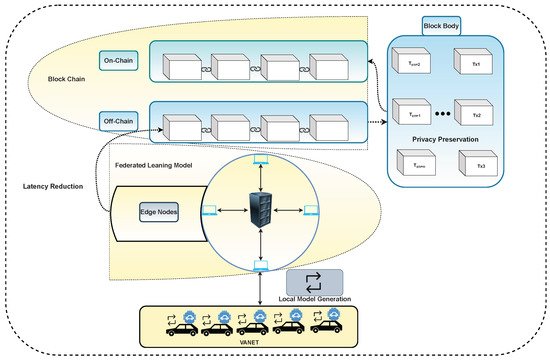
| Ref. | Contribution | Environment | Focused Area |
|---|---|---|---|
| [152] | In this research work, the author proposed a privacy reserving communication scheme based on VANET. The proposed framework meets the contextual and content privacy requirements. It used identity-based encryption and an elliptic curve cryptography scheme. | ITS | Security and Privacy |
| [153] | In this research work, the author proposed a contest-aware quantification technique to overcome security issues in VANET based on the Markov chain method. | VANET | Security |
| [154] | Based on wireless communication, the author presents a literature review of existing work related to VANET technology. The author also presents research directions and open issues for the integration of SDN with VANET. | SDN, IoT | Security |
| [155] | The proposed work addressed different privacy and security issues regarding VANET. The paper also presents the solutions to privacy and security issues. | VANET | Security and Privacy |
| [156] | The proposed work presented an overview of secure and smart communications using the IoT-based VANET technique to overcome traffic congestions in CPS, known as networks of IoV. | CPS, IoV | Security |
| [157] | The author made different clusters of vehicle packets of the specific cellular tower in an IoT environment. This process simplified communication, and VANET architecture reduces energy consumption and network delays. | IoT | Energy efficiency |
| [158] | The author proposed a lightweight end-to-end security solution for SDNV. The proposed objectives are achieved on two-level: RSU-based authentication technique and personal IDS. The lightweight security solution will also provide privacy. | SDNV | Energy |
| [159] | The author proposed a source location privacy preservation method based on smart energy for sustainable city roads. The proposed technique hides source location based on acceleration, distance, speed, and trust. | IoT | Energy and Privacy |
| [160] | The author proposed a new algorithm for multi-hop transmission called fuzzy clustering routing. The author also analyzed clustering limitations, which are performed through different algorithms. To transfer data, multi-hop routing was used. | IoT | Energy |
| [161] | This paper presented the different notions of blockchain and its usability in IoT networks. The author presented different privacy issues regarding the implementation of blockchain in IoT. The author presented FL usability in IoT networks, privacy risks, and taxonomy. | IoT | Privacy |
| [162] | Among different elements elaborate to manage a group of vehicles containing data, the author proposed a blockchain framework. The author integrates VPKI for blockchain to provide privacy and membership association. | VANET | Privacy |
| [163] | The author presented the fundamentals of IoT and blockchain. Then, the author presented a comprehensive literature review based on blockchain techniques for VIoT through the technical issues and problems. At the end of the paper, the authors present the future research direction regarding VIoT and blockchain. | VIoT | Energy and Privacy |
| [164] | The proposed research work analyzed and described existing supply chain, healthcare, VANET, and IoT access control through blockchain security methods. The author also presents a comprehensive survey regarding blockchain security. | IoT | Security and Privacy |
| [165] | The author proposed a new technique called FL-Block (blockchain FL) to overcome the existing issues in FL privacy. The local learning update is transferred to global learning using blockchain through this technique. | Fog computing | Privacy |
This entry is adapted from the peer-reviewed paper 10.3390/s22124394
