Vehicular communication is a promising technology that has been announced as a main use-case of the fifth-generation cellular system (5G). Vehicle-to-everything (V2X) is the vehicular communication paradigm that enables the communications and interactions between vehicles and other network entities, e.g., road-side units (RSUs). This promising technology faces many challenges related to reliability, availability and security of the exchanged data.
1. Introduction
With the release of the fifth-generation cellular system (5G) and the current announced vision of the sixth-generation cellular system (6G), the demands for developing reliable vehicular communication systems have increased. This includes vehicle-to-everything (V2X) and vehicle-to-vehicle (V2V) technologies. V2X is the vehicular communication paradigm that enables the communications and interactions between vehicles and other network entities, e.g., road-side units (RSUs). V2X can be divided into four main types: vehicle–network interaction (V2N), vehicle-to-vehicle interaction (V2V), vehicle–infrastructure interaction (V2I) and vehicle–human interaction (V2P) [1]. The development of this sphere will increase the safety of road users, improve traffic flow and, consequently, reduce the negative impact on the environment.
The design and development of V2X systems face many challenges associated with the requirements, which include ultra-high availability, ultra-high reliability, ultra-low latency, high system flexibility and security. Moreover, the high mobility of such networks and the dense deployment of vehicles put high constraints on the design of these networks. Another important challenge is the lack of trust between the objects of the transport network that can negatively affect the activities and interaction, as well as leading to casualties, privacy violations and other irreversible consequences. In order to ensure the quality of services (QoS) and reduce the negative effects of the influence of unscrupulous participants in the transport interaction, blockchain is introduced to such networks at the exchange level between participants and RSUs.
Since blockchain achieves accountability and integrity between network participants, it has been introduced to secure vehicular networks communications. V2X networks have heterogeneous, massive sets of users; thus, introducing blockchain to such networks guarantees high system reliability and better information distribution. Using blockchain, the required privacy and security can be achieved for V2X networks by mitigating the link attack and detecting malicious nodes, since it can achieve a consensus without introducing a third-party
[2]. Using blockchain to rate a road user is also an effective solution for V2X systems, as rating a facility allows action to be taken against offenders and encourage decent users. This ensures that misbehavior messages that create risk or reduce the efficiency of the V2X system are reduced.
The development of blockchain-based V2X systems is a prerequisite for improving the dynamic requirements of V2X services and applications, as well as expanding the range of capabilities of the services provided. It is worth noting that the provision of V2X services requires the provision of various network characteristics, such as delay, jitter, loss rate and data rates
[3]. To provide and support the given service requirements, mobile edge computing (MEC) is introduced to V2X systems. MEC is cloud computing technology that moves from the centralization of massive data centers, to a distributed scheme of edge, limited, small data centers. It provides paths for data offloading, thus achieving various benefits in terms of latency, reliability, availability and flexibility.
2. V2X System Architecture When Integrating Blockchain Technology and MEC
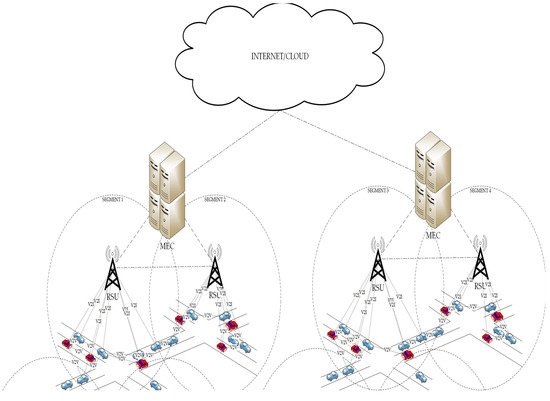
The proposed system architecture consists of roadside participants, several RSUs, distributed MEC units and the application server. Figure 1 presents the end-to-end system structure of the developed system. The V2X system participants, e.g., vehicles, pedestrians and cyclists, are the end-devices that periodically transmit and request traffic-related information.
Figure 1. The architecture of the proposed system.
RSUs are used to link services to V2X objects moving on/around the road and provide route information and updates. Each RSU provides the coverage to a group of vehicles, using the appropriate communication interface. Recently, V2X communications implemented using two main technologies, namely, 3GPP-based technology and dedicated short range communications (DSRC). IEEE 802.11p is the common DSRC that is widely used for V2X applications, while cellular vehicle-to-everything (C-V2X) is the alternative technology introduced by the 3GPP
[4].
Distributed MEC units are introduced at the edge of the access network, by connecting each RSU with an MEC unit. These edge units provide computing resources to roadside participants. Moreover, they implement the developed offloading scheme to manage the network traffic in an energy-efficient way.
3.1. V2X
In recent decades, the dedicated vehicle network has become a major network technology for the comfort and safety of drivers in vehicle environments. However, new applications and services require major changes in the underlying network models and calculations, which requires new road network planning
[5].
Thus, the emergence of critical messages and applications related to the safety of road users, which leads to high performance requirements and strict reliability of data transmission, should be noted. The transmitted messages can be divided into two categories, safety messages and general-purpose (non-safety-related) messages. For information about any emergency, vehicles can transmit or broadcast messages with high priority and high requirements. For information that is not an emergency, the requirements can be lowered. Based on the different requirements, V2X services can be divided into several basic types
[6][7].
Depending on the severity of the emergency, event messages are divided into different levels according to priority, where level 1 defines critical event messages with the highest priority, etc.
The primary goal of the vehicle network is to accurately disseminate information in a short time, with the required reliability and safety. There is a high risk that modern vehicles are subjected to cyber-attacks targeting vehicular communications
[8]. Due to inaccurate information sent by malicious vehicles, some important messages cannot be accurately disseminated in real time, resulting in damage to other traffic participants. Another problem could be the theft of important and sensitive information from traffic participants.
3.2. Application of Blockchain Technology between Road Users and RSUs
In the case of V2X, promising blockchain technology can be used to manage information trustworthiness, as event information would be stored in a publicly accessible blockchain. This technology can be applied in a variety of circumstances, such as the reliable transfer of information between network objects, the assessment of a road user’s rating and credibility with high node mobility.
Blockchain can solve major problems faced by V2X systems and provide security for the distribution of critical information. Using blockchain to reliably transmit information is important when transmitting and avoiding loss or distortion that could lead to negative consequences. Blockchain technology relies on rules and concepts to avoid these consequences. Due to the design of blockchain trust management, it can be successfully applied between nodes with decentralized systems.
Malicious nodes can infiltrate the network and spread false information on the network, causing the transport network to fail. Using blockchain to rate a road user is also an effective solution for use in the V2X system, as rating a facility would allow action to be taken against offenders and encourage decent users. This would ensure that misbehavior messages that create risk or reduce the efficiency of the V2X system are reduced.
3.3. Integration of Mobile Edge Computing (MEC) into the V2X System
Limited resources, a dynamic road user environment and long distances between cloud servers make it difficult to support computationally intensive services and cause problems such as additional latency, jitter and high power consumption
[9]. To solve these problems, the European Telecommunications Standards Institute, in 2014, proposed the use of mobile peripheral computing
[10]. Cloud-based models require the transmission and storage of V2X system object data in specialized data centers, which increases the likelihood of information leakage or loss and long latency, which can lead to accidents
[7]. In addition to this, the devices require additional services, such as computing and updating the user rating and network segment selection, which is a very time-consuming process; further, it becomes necessary to resort to mobile edge computing technology. When dealing with emergency event messages, the timeliness of the dissemination of messages is of paramount importance.
The loading pattern of RSUs and MEC depends on the corresponding traffic flow in that region. It is assumed that multiple RSUs share common edge server resources. To select segments and reduce service delays for excessive loads, it is necessary to expand the computational capacity of MEC. It is important to provide a balanced unloading scheme for different RSUs and to provide decision-making capacity for messages that require high reliability and system responsiveness.
This entry is adapted from the peer-reviewed paper 10.3390/electronics11020173