The technological advancements in the smart inverter technology were handled, comprehensively keeping the distribution level end user in mind. Since the smart inverter constitutes the most significant aspect of power conversion, control and regulation and acts as the interface between the utility and consumer, the vulnerabilities of the same when subjected to cyber attacks are highlighted in detail. Communication also forms a vital aspect as it is bi-directional (between the utility and consumer and vice-versa) in a smart grid platform. Therefore, the different standards of communication and rules along with the co-ordination aspects are elucidated in detail. The topological configuration of smart inverters under wired and wireless topologies are also handled, to give a better understanding with respect to the choice and selection of the same, keeping the end-user perspective in mind. Security being the key area of concern, the different types of cyber attacks that are prevalent and can be detected and identified is explained in detail. In addition, the role of the synchrophasor technology in state estimation, monitoring and detection of faults is demonstrated. Considering, the solar PV-based DER as an end-use application, the importance of newer technologies related to IoT and block chain with respect to the cyber security aspects of the smart grid is brought forth. This domain is of continuing importance and concern and still has several challenges to overcome. Keeping this in mind, the existing gaps and future directions are also presented.
1. Introduction
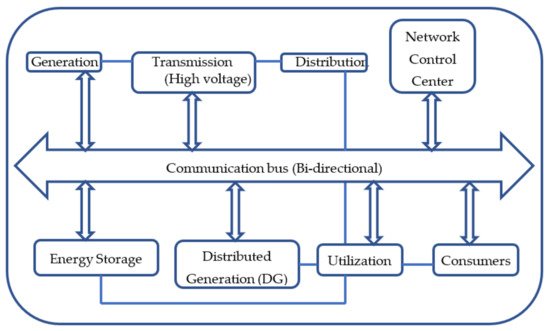
Smart grids are a revolutionary step toward a reliable, efficient and secure means of power transfer and delivery to the consumers. Technology evolution of smart grid has tried to amalgamate the information technology (IT) domain with the conventional grid structure. Smart grid architecture relies heavily on digital information and controls and also incorporates dynamic optimization of grid operations and resources. It also encourages the use of distributed resources and generation which includes renewable. The purpose of making the grid smart is to enforce greater responsibility toward energy use, energy consumption and efficiency. Keeping consistent with the concept, smart technologies (for the purpose of grid optimization, metering, communications as well as distributed automation) and smart appliances are integrated in the grid architecture. There is also considerable research on employing peak-shaving and energy storage technologies such as the plug-in hybrid and electric vehicles, thermal storage etc. Microgrids are an important subset of smart grids. While the former is confined to a smaller scale and operates independent of the larger utility grid, the latter operates at a larger utility level. Generally, microgrids are community based whereas smart grids are designed for the entire power system (from the generation to distribution stages). The block diagram representation of a smart grid is shown in Figure 1. The microgrid usually comprises multiple distributed generators (DGs) such as solar and wind along with linear and non-linear loads.
Figure 1. Schematic of a Smart Grid.
2. Standard Cyber Security Protocols
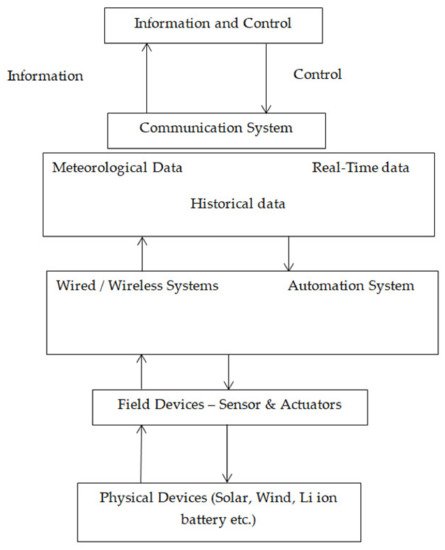
Figure 1 shows a typical smart microgrid with cyber secure systems in which power electronic converters are used in Nejabatkhah, Farzam, et al.
[1]. The cyber secure model consists of four important layers discussed below.
Figure 1. Typical smart microgrid with cyber secure systems.
The physical power system layer consists of power electronic converters, transformers, etc. To implement the control decisions, sensor and actuator layers are used. The devices are used to measure voltage, frequency and to check the circuit breaker status. For enabling communication between different layers, communication layer is used.
As stated earlier, the communication can be either wired or wireless. The management layer is the central control layer and maintains the microgrid under varied conditions. This layer gathers the data from the measurement layer and generates control signals to the microgrid. These control signals are sent to the actuators for performing necessary actions.
To control the physical system, cyber security collects, transmits and processes the data. The flow of data should be based on certain secure protocols that are reliable and efficient. Certain cyber secure protocols are described below.
2.1. AMI System Security Requirements (AMI-SEC)
To develop a strong rule for the initial AMI (Advanced Metering Infrastructure) in a smart grid, UCA International Users Group (UCAIug) was implemented. This protocol can be used for a home area network, meter management and forecasting system.
2.2. NERC CIP
This was established for setting up safe operation of bulk electric systems in North America. This protocol involves nine standards and forty-five requirements. This protocol provides emphasis on identification of critical cyber asset, controls and security management systems.
2.3. GB/T 22239
This is setup for information security technology in China. For the information system, it contains five security protection abilities to protect from hackers and reinstate to the previous state.
2.4. NISTIR 7628
This was proposed by the National Institute of Standards and Technology Interagency Report (NISITR). The guideline consists of more than six hundred pages with three volumes. This information helps many organizations in terms of information support (vehicle charging stations).
2.5. ISO/IEC 27001 and 27002
In regard to security testing, compliance with security policies this protocol is used to ensure that the execution of hardware and software controls is precise. To all smart grid components, this protocol can be used.
2.6. NIST SP 800-82
In regard to security of the industrial control system that is used world-wide, this protocol is used. The validation and certification of security controls if implemented in the right manner are maintained. Vulnerability and penetration testing standards are provided by this protocol.
3. Classifications in Cyber Attacks
Different types of cyber attacks are: (a) attack on data availability; (b) attack on data integrity; (c) attack on confidential data.
3.1. Attack on Data Availability
During islanded mode and in transients, the behavior of the power electronic converters is important. A secure smart grid should make sure that the data should be available during these periods. The attacks made during these instances are called attack on data availability. Initiation of the attack can be from either one point or multiple points, by sending malicious packets to the host or by exceeding the routers’ processing capacity, network bandwidth, or servers.
3.2. Attack on Data Integrity
By manipulating the measurements in the communication network, these attacks are made. This leads to the imbalance in voltage and frequency, and synchronization with the grid does not happen. Hence, under all operating conditions, the data should be accurate and trustworthy. False data injection (FDI) is the best example for attack on data integrity. These are also referred to as stealth attacks. In such attacks, the hackers enter the communication layer and system operators will be unaware of such attacks.
3.3. Attack on Confidential Data
The confidential data should be available only for authorized personals. Although this attack does not cause much effect on the smart grid, hackers access user data (identity and usage of power)
3.4. Types of Cyber Attacks
In smart microgrids the concept of outer supervisory control and inner primary control is followed. The supervisory control manages the overall operation effectively and efficiently and generates the control signals by receiving the information from power electronic converter. These control signals reach the inner control layer and perform necessary actions. The hackers target the steady state and the transient operations of the microgrid.
3.5. Cyber Attacks on State Estimation
Voltage and phase angle measurements and state estimation are used to decide the system operation. The state estimation also helps in an efficient and effective operation. The state estimation plays a major role in monitoring and controlling the smart grid. The estimated states are used for estimating the load flow, stability analysis, load forecasting and location pricing. Any attack by the hackers on the states will cause devastating effects on the performance and operation of the smart grid
State estimation can be classified as AC and DC state estimations. DC state estimations have studied more than AC, as analytical models are simple.
3.6. Cyber Attacks on Protection Schemes
The protection scheme is one of the most important components in a microgrid. This scheme should work during grid-connected and islanded mode of operation. The relay setting is made based on the type of operation and current level. This is based on standards provided by IEC (International Electrotechnical Commission) 61850. Hackers change the setting of the relay, leading to disastrous effects. Hence, a secure, reliable, and fast communication network-enabled protection scheme should be provided.
3.7. Cyber Attacks on Voltage Control
The power electronics interfaced distributed generations and diesel generators govern the voltage in a smart grid. The system voltage and the reactive power-measured control system provide the reference values for generation of power. Hackers attack the reference data and voltage regulation is impacted.
This entry is adapted from the peer-reviewed paper 10.3390/app11188780