The Internet of Things (IoT) plays a vital role in interconnecting physical and virtual objects that are embedded with sensors, software, and other technologies intending to connect and exchange data with devices and systems around the globe over the Internet. With a multitude of features to offer, IoT is a boon to mankind, but just as two sides of a coin, the technology, with its lack of securing information, may result in a big bane. It is estimated that by the year 2030, there will be nearly 25.44 billion IoT devices connected worldwide.
- Internet of Things
- security
- threats
- privacy
- vulnerabilities
- Blockchain
1. Introduction
We live in a time when technology is an essential requirement for all humans, and the evidence is the increased dependence on technology in almost every aspect of our lives. Today’s world is evolving with the rapidly growing Internet of Things (IoT)-based application [1]. The rise of the IoT has been a glorious phenomenon in recent years. The physical and virtual objects implanted with sensors, software, and other technologies are interlinked together in IoT [2]. It envisages communicating and sharing data with other devices and systems worldwide over the Internet. Further, IoT is like an array of network-enabled devices that exclude traditional computers such as laptops and servers.
To implement IoT, the traditional technology had to undergo some major modifications. For example, to convert an isolated device into a transmitting device, there is a need to increase small computing devices’ memory and processing capacity while dramatically reducing their size [6]. Further, the creation of various lightweight, secure protocols for communication between different IoT devices is equally important. The improvements to the conventional networks to help the operation of the IoT ecosystem have their own set of consequences. However, the unprecedented growth of interconnected devices has crippled the IoT ecosystem. Consequently, there exists enough scope for threats and attacks in IoT-based applications.
The Global Vice President at New Net Technologies (NNT), Dirk Schrader, stated that IoT-based computers have become the crown jewels of cybercriminals. He also said that less than 42% of businesses can detect insecure IoT devices. Hence, for researchers to develop well-grounded solutions to trace and avert these threats, they must first understand the threats and attacks to make the IoT environment safe, secure, and reliable. There are three significant aspects to consider while examining the IoT from a security perspective. To begin with, there are a massive number of smart devices, possibly billions. This suggests that the IoT would be the most complex man-made system ever in terms of the number of entities involved [7]. Second, they are essentially heterogeneous, with respect to the functionality, protocol stacks, radios, operating systems (some objects do not even have one), energy sources, identities, and so on [8]. Third, each smart object is owned by a company or a person, and it is managed by the same or a different company or individual. Millions of businesses and individuals are in control of a subset of the smart objects in their management domains. From the standpoint of protection, privacy, and trust, how this control is technically upheld is a critical issue.
The state-of-the-art survey on various aspects of IoT, including security, privacy, and robustness, has been presented in [11] by Chen et al. The authors focused on specific issues of IoT interface positioning and localization. The development of lightweight block cipher algorithms has been proposed to be used in devices for data encryption and decryption [12]. A desktop review and qualitative analysis have been performed by Gamudani et al. in [13] to compute performance analysis of attacks. Cryptographic approaches have been discussed in [14] as a method of ensuring long-term security approaches. Different layer architectures of IoT and security issues associated with them have been discussed with possible countermeasures using Blockchain (BC) in [15]. The survey on security aspects of IoT has been presented by Alaba et al. in [16], covering the scope of security countermeasures in some other allied paradigms, including Machine-to-Machine (M2M), Cyber-Physical System (CPS), and Wireless Sensor Networks (WSNs). In [17], Abomhara et al. discussed various applications of IoT and the security threats related to them, including vulnerabilities, intruders, and some other attacks. The threats concerning security and privacy in IoT architecture have been presented without counter measuring techniques by Kozlov et al. in [18].
2. IOT Vulnerability
3. Taxonomy of Threats and Attacks in IoT
-
Unstructured threats: These are made up mainly of novice people who use the readily available hacking software.
-
Structured threats: People aware of system vulnerabilities and can comprehend, build, and exploit code and scripts are known as structured risks.
-
Advanced Persistent Threats (APT): A coordinated assault is an example of advanced persistent threats. APT is a sophisticated network attack that seeks to steal data from high-value information in industries such as manufacturing, banking, and national defense [112].
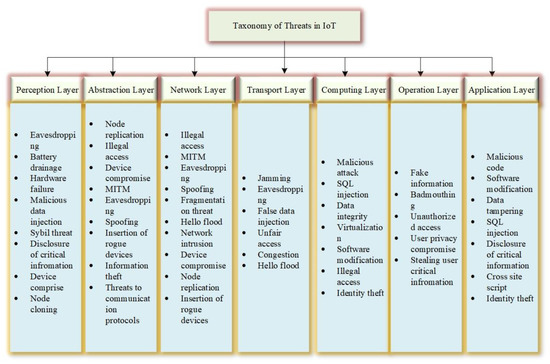
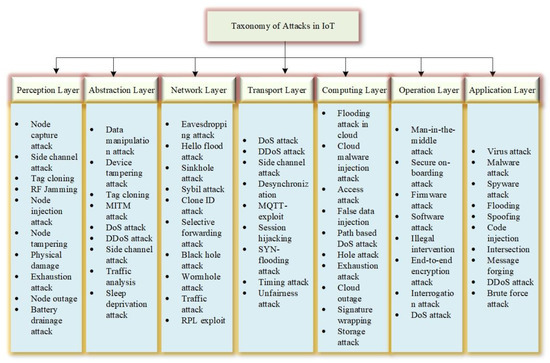
4. Security Goals and Roadmap in IoT
-
Confidentiality: Confidentiality is an important security feature in the Internet of Things, but it is not always required, for example, in cases where data are exchanged with the public. In the vast majority of situations and cases, sensitive data must not be disclosed or read by unauthorized persons [180]. Sensitive information about patient data, company information, and possibly military information, as well as security accreditations, should all be kept private from unauthorized users. Confidentiality should be granted such that the information gathered or distributed is safe and only accessible to approved users. Data collected by a computer or a sensor should not be sent to other devices unless they are properly encrypted. To prevent malicious actors from accessing the collected data, only encrypted messages should be sent to neighboring devices. A data encryption system transforms each bit of data into ciphertext, followed by a two-step verification process in which two devices/components permit access only if the authentication test is passed by both the devices, and a biometric verification in which the user is uniquely identifiable and biometric authentication in which the person can be identified by his or her fingerprints.
-
Integrity: Integrity should be offered to ensure data validity. Data integrity is critical since data recipients must be able to verify whether data obtained from other devices are authentic. In most cases, integrity is a necessary security property for IoT users to receive reliable services [181]. Different IoT systems have different levels of trustworthiness. As an example, because of data sensitivities, a patient observation framework would have high trustworthiness testing against arbitrary mistakes. It is integrated into the network to protect cybercrimes data in the communication process so that data manipulation cannot be carried out without the danger detected by the device. Two error detection methods are used to ensure data integrity in the inspection and cyclic redundancy search. For continuous data sync for backup purposes, a version control system is used.
-
Authentication and authorization: Authenticity is related to credibility, and it means that each system in the network should be able to recognize and authenticate other devices. Since the IoT is made up of so many devices, it is critical to be able to recognize them; otherwise, malicious devices might use spoofing to target IoT networks. Due to the design of IoT settings, the possible communication between the device and device (M2M) is exacerbated by the problem of authentication in IoT connectivity. Different authentication criteria in different systems require different solutions. Some solutions, such as bank card or bank device authentication, require a high level of reliability. However, others will need to be foreign, such as e-Passport, while others will need to be local. Only approved entities (any authenticated entity) can conduct such network operations using the authorization property [182].
-
Availability: The primary aim of every IoT protection system is to make data available to users promptly. The consumer should be able to obtain data from the resources right away, not only in usual circumstances but also in emergencies. Firewalls are installed in the network to protect against attacks on services such as denial-of-service attacks, which prevent data from reaching the end-user [183].
-
Accountability: Accountability provides redundancy and responsibility for some activities, tasks, and the preparation of the execution of network security policies while designing security strategies to be used in a safe network [184]. Accountability cannot prevent attacks on its own, but it does help ensure that other security measures are functioning properly. Integrity and confidentiality, for example, can be rendered worthless if they are not subjected to transparency. Often, in a disapproved event, an entity’s behavior can also be traced through an accountability system, which can help determine the inside story of what occurred and who was ultimately responsible.
5. Conclusions
The introduction of smart computing devices using IoT has made day-to-day lives more convenient. Data analytics, automation, and smart devices have all benefited from the introduction of IoT into human life. Nevertheless, the unprecedented growth in IoT has also been crippled with many vulnerabilities and challenges. Further, the IoT’s heterogeneous design expands the attack surface and adds new challenges to an already vulnerable IoT network. The successful compromise of the system’s security may have fatal consequences for users. The overall security of the device must be considered to ensure that critical vulnerabilities are mitigated. Policies and protocols must be enforced as much as possible to deter threats and attacks. In this paper, we have presented a most comprehensive survey on IoT from the perspective of security threats and attacks. Further, modern threats and attacks on the emerging IoT infrastructure, security flaws, and countermeasures are discussed in this paper. In addition, a roadmap of using ubiquitous technologies, viz., BC, FC, EC, and ML, for enhancing security in IoT are comprehensively discussed in this paper.However, due to IoT devices’ heterogeneous existence and limitations, any resolution would be ineffective and obsolete. Consequently, due to the evolving nature of technology, it is estimated that more countermeasures and vulnerabilities will be revealed in the near future. As future work, the authors are working on ML and IoT integration to enhance IoT-based applications’ security under dynamically varying conditions.
This entry is adapted from the peer-reviewed paper 10.3390/su13169463
