Sensor networks provide services to a broad range of applications ranging from intelligence service surveillance to weather forecasting. While most of the sensor networks are terrestrial, Underwater Sensor Networks (USN) are an emerging area. One of the unavoidable and increasing challenges for modern USN technology is tolerating faults, i.e., accepting that hardware is imperfect, and coping with it. Fault Tolerance tends to have more impact in underwater than in terrestrial environment as the latter is generally more forgiving. Moreover, reaching the malfunctioning devices for replacement and maintenance under water is harder and more costly.
- underwater sensor network
- fault tolerance
- cross-layer fault tolerance
- fault management
1. Introduction
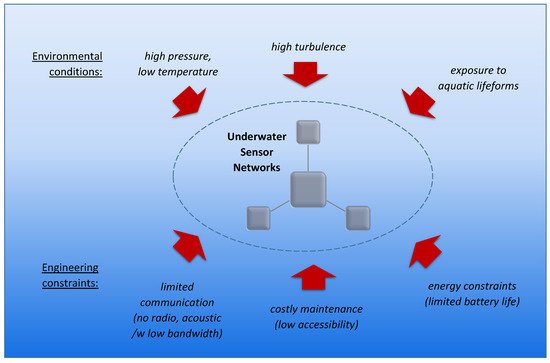
Underwater Sensor Networks (USNs) have become widespread and are being deployed in a wide range of applications ranging from harbor security to monitoring underwater pipelines and fish farms. Due to the fact that USNs often operate in an extremely harsh environment, and many of their applications are safety-critical, it is imperative to develop techniques enabling these networks to tolerate faults. Moreover, USNs face many challenges that are not present in terrestrial networks, such as virtual inapplicability of the wireless radio communication under water and limitations of the acoustic means, for example.
2. Specifics of Underwater Sensor Networks
3. Taxonomy of Faults and Fault Tolerance Tasks
In the following, we present the taxonomy of the sources of faults, as well as of the Fault Tolerance tasks. The objective of describing and representing these taxonomies is to categorize the articles for the current survey.
3.1. Sources of Faults
3.2. Fault Tolerance Tasks
The objective of the current section is to define a taxonomy of Fault Tolerance tasks to help categorize the identified papers. The Fault Tolerance tasks are based on more general Fault Tolerance principles from References [18][19]. Figure 2. shows the taxonomy of Fault Tolerance tasks applicable in USNs and how they affect each other. While the design and initial deployment of USNs contribute to Fault Prevention and Prediction abilities, data collecting techniques at the run-time contribute also to Fault Detection and Fault Recovery stages of the system, all of which are going to be discussed in the current paper.
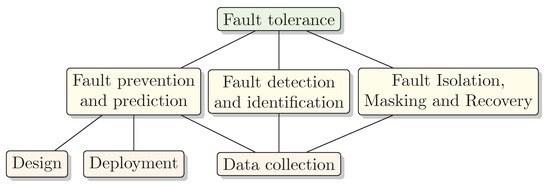
The techniques under consideration can be categorized into the following groups:
-
Fault Prediction and PreventionThis task is about both preventing a fault to happen, as well as about proactive fault avoidance. Sensor networks can prevent certain faults from happening by design and/or deployment aspects. A disadvantage of fault prevention is a potentially increased system complexity. Fault avoidance, in turn, includes manufacturing testing and verification, which have a high cost often exceeding that of the entire design process.
-
Fault Detection and IdentificationOne of the central parts of Fault Tolerance is Fault Detection and Fault Identification of affected components which can, for instance, be performed by utilizing data collection with ping messages. Without Fault Identification, for instance, sensor node and network faults may be hard to distinguish. A disadvantage of Fault Detection and Fault Identification may be additional energy requirements and network congestion.
-
Fault Isolation, Masking, and RecoveryIsolation, masking, and recovery are different techniques for repairing a fault, minimizing the effect of a fault, or avoiding it to turn to system failure. Identified faults can be isolated, masked, and sensor network recovered, for instance, redirecting traffic through healthy backup components. Fault Recovery can ensure overall system operation even when components degrade. The downside may be the cost of adding components to ensure redundancy.
The overview of fault tolerant techniques presented in the following section follows the above-described taxonomy.
4. Overview of Techniques by Fault Tolerance Tasks
4.1. Fault Prevention and Prediction
4.1.1. Design of the Sensor Network
4.1.2. Sensor Network Deployment
4.1.3. Data Collection
4.1.4. UWSN Testing Frameworks
4.2. Fault Detection and Identification
4.3. Fault Isolation, Masking and Recovery
Subsequent to Fault Detection, Fault Identification, and Fault Diagnosis, a fault handling stage can be entered [38] to prevent further data corruption and system deterioration. The fault handling consists of Fault Isolation, Masking, and Recovery. Fault handling can hide the fault occurrence from other components by applying Fault Masking; the key techniques for such masking are informational, time, and physical redundancy [18]. Proposed masking technique For Underwater Vehicles is Triple Modular Redundancy (TMPR) [48], which is also one of the most commonly used Fault Masking techniques. Isolating a faulty component from the others can be facilitated by using virtualization [18]. In large scale distributed systems, frozen virtual images of healthy services have been used as checkpoints [49] for rolling back in case of a fault occurrence.
Fault Recovery ensures that the fault does not propagate to visible results, for instance, by rolling back to a previous healthy state (checkpointing) or re-trying failed operations (time redundancy). Some of the techniques for Fault Recovery can be Reconfiguration, which is changing the system’s state so that the same or similar error is prevented from occurring again, and Adaptation, which is re-optimizing the system, for instance, after Reconfiguration task [19].
In Sensor Networks, different approaches for Fault Recovery have been used, that have different resource overheads, energy-efficiencies, scalabilities and network types. For both network and node Fault Recovery in wireless sensor networks, Mitra et al. (2016) [50] compares techniques, such as checkpoint-based recovery (CRAFT), agent-based recovery (ABSR), fault node recovery (FNR), cluster-based and hierarchical fault management (CHFM), and Failure Node Detection and Recovery algorithm (FNDRA). While some of those are specific to terrestrial wireless usage, some principles (e.g., checkpointing, etc.) can also be used in wired and/or underwater environments. To reduce the network bandwidth requirements, checkpoint backup can be mobile to nearby nodes [51] and used for recovering from fault situations.
In network protocols, Fault Masking and Fault Recovery are handled by error control schemes that are commonly categorized into the following three groups [1]:
-
Automatic Repeat Request (ARQ)—re-transmission of corrupted data is asked;
-
Forward Error Correction (FEC)—data corruption can be detected and corrected by the receiving end; and
-
Hybrid ARQ (HARQ)—a combination of FEC and ARQ.
The cross-layer approach benefits Fault Recovery significantly since single-layer redundancy, such as hardware redundancy and application checkpointing, have very high costs, and latency between fault occurrence and detection makes the recovery difficult [19].
This entry is adapted from the peer-reviewed paper 10.3390/s21093264
References
- Domingo, M.C.; Vuran, M.C. Cross-layer analysis of error control in underwater wireless sensor networks. Comput. Commun. 2012, 35, 2162–2172.
- Domingo, M.C. A topology reorganization scheme for reliable communication in underwater wireless sensor networks affected by shadow zones. Sensors 2009, 9, 8684–8708.
- Zenia, N.Z.; Aseeri, M.; Ahmed, M.R.; Chowdhury, Z.I.; Shamim Kaiser, M. Energy-efficiency and reliability in MAC and routing protocols for underwater wireless sensor network: A survey. J. Netw. Comput. Appl. 2016, 71, 72–85.
- Xu, J.; Li, K.; Min, G. Reliable and energy-efficient multipath communications in underwater sensor networks. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1326–1335.
- Lal, C.; Petroccia, R.; Conti, M.; Alves, J. Secure underwater acoustic networks: Current and future research directions. In Proceedings of the 2016 IEEE Third Underwater Communications and Networking Conference (UComms), Lerici, Italy, 30 August–1 September 2016.
- Das, A.P.; Thampi, S.M. Fault-resilient localization for underwater sensor networks. Ad Hoc Netw. 2017, 55, 132–142.
- Mohamed, N.; Jawhar, I.; Al-Jaroodi, J.; Zhang, L. Sensor network architectures for monitoring underwater pipelines. Sensors 2011, 11, 10738–10764.
- Kumar, S.; Balamurugan, B. Fault tolerant cloud systems. In Encyclopedia of Information Science and Technology, 4th ed.; Khosrow-Pour, D.B.A., Ed.; IGI Global: Hershey, PA, USA, 2018.
- Wilfredo, T.; Torres-Pomales, W. Software Fault Tolerance: A Tutorial; Technical Report October; NASA: Washington, DC, USA, 2000.
- Khan, M.Z. Fault Management in Wireless Sensor Networks. GESJ Comput. Sci. Telecommun. 2013, 1, 3–17.
- Paradis, L.; Han, Q. A survey of fault management in wireless sensor networks. J. Netw. Syst. Manag. 2007, 15, 171–190.
- Henkel, J.; Hedrich, L.; Herkersdorf, A.; Kapitza, R.; Lohmann, D.; Marwedel, P.; Platzner, M.; Rosenstiel, W.; Schlichtmann, U.; Spinczyk, O.; et al. Design and architectures for dependable embedded systems. In Proceedings of the Seventh IEEE/ACM/IFIP International Conference on Hardware/Software Codesign and System Synthesis, Taipei, Taiwan, 9–14 October 2011; ACM Press: New York, NY, USA, 2011; p. 69.
- Georgakos, G.; Schlichtmann, U.; Schneider, R.; Chakraborty, S. Reliability challenges for electric vehicles. In Proceedings of the 50th Annual Design Automation Conference, Austin, TX, USA, 29 May–7 June 2013; ACM Press: New York, NY, USA, 2013; p. 1.
- Lorenz, D.; Barke, M.; Schlichtmann, U. Efficiently analyzing the impact of aging effects on large integrated circuits. Microelectron. Reliab. 2012, 52, 1546–1552.
- Sauli, Z.; Retnasamy, V.; Taniselass, S.; Shapri, A.H.; Hatta, R.M.; Aziz, M.H. Polymer core BGA vertical stress loading analysis. Proc. Int. Conf. Comput. Intell. Model. Simul. 2012, 129, 148–151.
- Rehman, S. Reliable Software for Unreliable Hardware—A Cross-Layer Approach. Ph.D. Thesis, Karlsruhe Institute of Technology (KIT), Karlsruhe, Germany, 2015.
- Kaaniche, M.; Laprie, J.C.; Blanquart, J.P. Dependability engineering of complex computing systems. In Proceedings of the Sixth IEEE International Conference on Engineering of Complex Computer Systems 2000, Tokyo, Japan, 11–14 September 2000; pp. 36–46.
- Tanenbaum, A.S.; Van Steen, M. Distributed Systems: Principles and Paradigms; Prentice-Hall: Upper Saddle River, NJ, USA, 2007.
- Carter, N.P.; Naeimi, H.; Gardner, D.S. Design techniques for cross-layer resilience. In Proceedings of the 2010 Design, Automation & Test in Europe Conference & Exhibition (DATE 2010), Dresden, Germany, 8–12 March 2010; pp. 1023–1028.
- Singh, S.P.; Sharma, S.C. A survey on cluster based routing protocols in wireless sensor networks. Procedia Comput. Sci. 2015, 45, 687–695.
- Sofi, S.A.; Mir, R.N. Natural algorithm based adaptive architecture for underwater wireless sensor networks. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017; pp. 2343–2346.
- Tyagi, S.; Kumar, N. A systematic review on clustering and routing techniques based upon LEACH protocol for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 623–645.
- Noh, Y.; Lee, U.; Lee, S.; Wang, P.; Vieira, L.F.; Cui, J.H.; Gerla, M.; Kim, K. HydroCast: Pressure routing for underwater sensor networks. IEEE Trans. Veh. Technol. 2016, 65, 333–347.
- Asim, M.; Mokhtar, H.; Merabti, M. A fault management architecture for wireless sensor network. In Proceedings of the 2008 International Wireless Communications and Mobile Computing Conference, Crete, Greece, 6–8 August 2008; pp. 779–785.
- Jiang, S. State-of-the-Art Medium Access Control (MAC) Protocols for Underwater Acoustic Networks: A Survey Based on a MAC Reference Model. IEEE Commun. Surv. Tutor. 2018, 20, 96–131.
- Wu, C.H.; Lee, K.C.; Chung, Y.C. A Delaunay Triangulation based method for wireless sensor network deployment. Comput. Commun. 2007, 30, 2744–2752.
- Isler, V.; Kannan, S.; Daniilidis, K. Sampling based sensor-network deployment. In Proceedings of the 2004 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), Sendai, Japan, 28 September–2 October 2004; pp. 1780–1785.
- Dong, M.; Li, H.; Li, Y.; Deng, Y.; Yin, R. Fault-tolerant topology with lifetime optimization for underwater wireless sensor networks. Sadhana Acad. Proc. Eng. Sci. 2020, 45.
- Cheng, Z.; Perillo, M.; Heinzelman, W.B. General network lifetime and cost models for evaluating sensor network deployment strategies. IEEE Trans. Mob. Comput. 2008, 7, 484–497.
- Bhuvana, V.P.; Preissl, C.; Tonello, A.M.; Huemer, M. Multi-Sensor Information Filtering with Information-Based Sensor Selection and Outlier Rejection. IEEE Sens. J. 2018, 18, 2442–2452.
- Goyal, N.; Dave, M.; Verma, A.K. Data aggregation in underwater wireless sensor network: Recent approaches and issues. J. King Saud Univ. Comput. Inf. Sci. 2017.
- Goyal, N.; Dave, M.; Verma, A.K. A novel fault detection and recovery technique for cluster-based underwater wireless sensor networks. Int. J. Commun. Syst. 2018, 31, 1–14.
- Kohnstamm, J.; Madhub, D. Mauritius Declaration. In Proceedings of the 36th International Conference of Data Protection & Privacy Commissioners, Balaclava, Mauritius, 14 October 2014; pp. 1–2.
- Campagnaro, F.; Francescon, R.; Guerra, F.; Favaro, F.; Casari, P.; Diamant, R.; Zorzi, M. The DESERT underwater framework v2: Improved capabilities and extension tools. In Proceedings of the 2016 IEEE Third Underwater Communications and Networking Conference (UComms), Lerici, Italy, 30 August–1 September 2016.
- Petrioli, C.; Petroccia, R.; Potter, J.R.; Spaccini, D. The SUNSET framework for simulation, emulation and at-sea testing of underwater wireless sensor networks. Ad Hoc Netw. 2015, 34, 224–238.
- Petroccia, R.; Spaccini, D. Comparing the SUNSET and DESERT frameworks for in field experiments in underwater acoustic networks. In OCEANS 2013 MTS/IEEE Bergen: The Challenges of the Northern Dimension; IEEE: Bergen, Norway, 2013.
- Ateniese, G.; Capossele, A.; Gjanci, P.; Petrioli, C.; Spaccini, D. SecFUN: Security framework for underwater acoustic sensor networks. In MTS/IEEE OCEANS 2015—Genova: Discovering Sustainable Ocean Energy for a New World; IEEE: Genova, Italy, 2015.
- Liu, T.H.; Yi, S.C.; Wang, X.W. A fault management protocol for low-energy and efficient Wireless sensor networks. J. Inf. Hiding Multimed. Signal Process. 2013, 4, 34–45.
- Case, J.D.; Fedor, M.; Schoffstall, M.L.; Davin, J. RFC1157: Simple Network Management Protocol (SNMP). Technical Report, RFC Editor. 1990.
- Gunawi, H.S.; Do, T.; Hellerstein, J.M.; Stoica, I.; Borthakur, D.; Robbins, J. Failure as a service (faas): A cloud service for large-scale, online failure drills. In Technical Report No. UCB/EECS-2011-87; University of California: Berkeley, CA, USA, 2011.
- Intel. Intelligent Platform Management Interface. 2004. Available online: (accessed on 6 May 2021).
- Napolitano, M.R.; Neppach, C.; Casdorph, V.; Naylor, S.; Innocenti, M.; Silvestri, G. Neural-network-based scheme for sensor failure detection, identification, and accommodation. J. Guid. Control. Dyn. 1995, 18, 1280–1286.
- Neti, C.; Schneider, M.H.; Young, E.D. Maximally Fault Tolerant Neural Networks. IEEE Trans. Neural Netw. 1992, 3, 14–23.
- Benincasa, G.; D’Aniello, G.; De Maio, C.; Loia, V.; Orciuoli, F. Towards perception-oriented situation awareness systems. Adv. Intell. Syst. Comput. 2014, 322, 813–824.
- Compton, M.; Barnaghi, P.; Bermudez, L.; García-Castro, R.; Corcho, O.; Cox, S.; Graybeal, J.; Hauswirth, M.; Henson, C.; Herzog, A.; et al. The SSN ontology of the W3C semantic sensor network incubator group. J. Web Semant. 2012, 17, 25–32.
- D’Aniello, G.; Gaeta, A.; Orciuoli, F. Artificial bees for improving resilience in a sensor middleware for Situational Awareness. In Proceedings of the 2015 Conference on Technologies and Applications of Artificial Intelligence, Tainan, Taiwan, 20–22 November 2015; pp. 300–307.
- Fadel, E.; Gungor, V.C.; Nassef, L.; Akkari, N.; Abbas Malik, M.G.; Almasri, S.; Akyildiz, I.F. A survey on wireless sensor networks for smart grid. Comput. Commun. 2015, 71, 22–33.
- Alansary, K.A.; Daoud, R.M.; Amer, H.H.; Elsayed, H.M. Networked control system architecture for autonomous underwater vehicles with redundant sensors. In Proceedings of the 2019 11th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Pitesti, Romania, 27–29 June 2019; pp. 2019–2022.
- Cristea, V.; Dobre, C.; Pop, F.; Stratan, C.; Costan, A.; Leordeanu, C.; Tirsa, E. A dependability layer for large-scale distributed systems. Int. J. Grid Util. Comput. 2011, 2, 109.
- Mitra, S. Comparative study of fault recovery techniques in wireless sensor network. In Proceedings of the 2016 IEEE International WIE Conference on Electrical and Computer Engineering (WIECON-ECE), Pune, India, 19–21 December 2016; pp. 19–21.
- Salera, I.; Agbaria, A.; Eltoweissy, M. Fault-tolerant mobile sink in networked sensor systems. In Proceedings of the 2006 2nd IEEE Workshop on Wireless Mesh Networks, Reston, VA, USA, 25–28 September 2007; pp. 106–108.
