1. Introduction
Despite being introduced ten years ago, the concept of zero trust is still in its early stages as an emerging network security concept. This section attempts to study zero trust from the perspective of trust and explores the representative literature on trust in cybersecurity, the concept and principles of zero trust, and its achievements. Finally, a table is provided to showcase the relevant literature.
1.1. Trust in Cybersecurity
The concept of trust predates cybersecurity and has been discussed and analysed by sociologists for many decades. Rousseau et al. [
12] define trust as “a psychological state comprising the intention to accept vulnerability based upon positive expectations of the intentions or behaviour of another”.
Although this generally accepted definition captures an inter-disciplinary perspective, it does not fully capture the dynamics and varied subtleties of trust. Thus, there is no universally accepted scholarly definition of trust. The implications and classification of trust in cybersecurity has always been determined by the context. According to Govindan et al. [
13], trust can be reflected in reliability, utility, availability, reputation, risk, confidence, quality of services, and other concepts. However, none of these concepts accurately capture trust. For example, although some security professionals regard trust as a security metric or an evaluation methodology [
14], others consider it as a relationship between entities [
15]. The focus and security requirements of different scenarios impact trust, imbuing it with ambiguity. Thus, scholarly attention has shifted from the definition of trust to the classification.
With complexity and ambiguity, trust is classified based on the context. In safety culture, Burns et al. [
16] divided trust into explicit and implicit trust. Explicit trust is derived from the clear standard that people use, relevant information obtained, and existing laws and regulations to objectively and fairly judge the credibility of others. This improves safety by sacrificing practicality. Implicit trust, on the other hand, derives from people’s subjective perception of the trustworthiness of others based on emotions and experiences. This sacrifices a certain amount of security for improved practicality. According to Dunning et al. [
17], trust is constructed based on people’s ethical norms, rather than established societal norms, whose influence dwindles, as mutual trust between two parties deepens. From the perspective of the weight change of explicit and implicit trust, with the deepening of mutual trust between two parties, the objective explicit trust determined by societal norms will gradually be weaker than the subjective implicit trust accumulated through multiple interactions; the increase in the influence of implicit trust will further promote the conclusion of subsequent transactions. Thus, trust comprises objective explicit trust and subjective implicit trust, and the weight of the two directly affects the safety and practicality of trust in actual use.
In cybersecurity, there are more refined trust classifications. Govindan et al. [
13] classified trust as a risk factor, belief, subjective probability, or transitivity. For mobile ad hoc networks, trust is more of a subjective assessment. The reliability and accuracy of the received information should be assessed in a given context. Trust can reflect the belief, confidence, or expectations of the target node’s future activity/behaviour and the mutual relationship between the nodes that behave in a trustworthy manner with each other. Pearson et al. [
18] surmised that both persistent trust and dynamic trust are required in cloud computing. The major difference between persistent and dynamic trust is the length of the trust life cycle. Persistent trust is derived from long-term underlying properties or infrastructure; dynamic trust, on the other hand, exists briefly in specific states, contexts, or for single information. Thus, the reliability of the former is more dependent on the long-term existing mechanisms of society or industry, and the latter is closer to trusted computing availed by modern computer technology. However, these definitions and classifications of trust always rely on the traditional perimeter to divide trusted and untrusted zones. The gradual disappearance of the traditional perimeter poses a challenge that impels a new security solution.
1.2. What Is Zero Trust
Prior to zero trust, the default assumption among security professionals was that all the data and transactions inside the perimeter were always trusted [
19]. However, risks, such as penetration attacks, malicious insiders, and loss of data, degrade trust. Trust for malicious insiders is degraded by the system only after the target resource is obtained. Owing to this, critical resources are always under threat, even within the secure perimeter. Furthermore, in current authentication and authorization methods, malicious insiders retain permissions until the trust is re-evaluated. To address the flaws of the traditional perimeter, zero trust addresses insider threats in an internal network using deperimeterization [
3]. It describes a transition that reduces or even eliminates the perimeter and secures the system using a continuous approach that verifies each device, user, transaction, and even data flow, during the entire access process. Thus, it assumes the stance of “never trust, always verify”. However, there is no specific and universal definition of trust. Most scholars regard it as a cybersecurity paradigm related to identity authorization, fine-grained access control, and secure communication that focuses on combining existing technologies. Others consider zero trust a cybersecurity paradigm focused on resource protection and have attempted to summarize it as several abstract definitions and architectures that eliminate implicit trust from a more fundamental perspective [
9]. In general, zero trust is concerned with the use of technology for the comprehensive, accurate, and real-time control of security systems.
Owing to the growing sophistication of AI, it is being introducing into security systems. For zero trust, AI, as a human analogue, is becoming one-sided, in terms of assessing security using technical metrics alone. Tidjon et al. [
20] attempted to understand the factors influencing the trustworthiness of an AI system. By compiling and summarizing the literature, transparency was found to be the most adopted principle. Theoretically, trustworthiness can be judged based on the 12 attributes of transparency: privacy, fairness, security, safety, responsibility, accountability, explainability, well-being, human rights, inclusiveness, and sustainability. This finding illustrates the need for researchers on zero trust to introduce human-related factors to further enhance security, in addition to the constant enhancement of technology. Regardless of how advanced AI technology becomes, it must ultimately be used only when humans trust it. This, in turn, is one reason why the definition of zero trust is controversial.
Therefore, although there is no unified definition of zero trust, existing research has provided an understanding of its core principle. Based on the works of Kindervag [
21], ACT-ICA [
19], NIST ZTA [
9], the National Security Agency [
22], and J. Garbis et al. [
23], the following deductions are made:
-
Separation of trust from location. This principle is one of the basic premises for achieving zero trust. The biggest difference between zero trust and traditional security perimeters is whether the location determines the trust in the access behaviour. Zero trust dispels the credibility of the internal trusted network set by the traditional security perimeter based on the resource location, and is premised on the belief that location can no longer fully guarantee trust in the current network environment. Furthermore, the network security situation, such as the long-term hostility of the network and existence of internal and external threats, makes the trust gained by the location unable to guarantee the security of critical resources in the network. The separation of trust from the location that is the core of zero trust can invalidate the trust determined by location, thereby reducing the scope of the influence of implicit trust in internal trusted networks, and ultimately achieving the goal of resisting threats from internal and external networks simultaneously. However, it should be noted that that trust is not solely determined by location, as zero trust does not completely negate the influence of the location on trust judgment; rather, it is simply one of other collectible elements as an equal condition for judging trust.
-
The principle of least privilege. The formulation of least-privilege policies is essential to achieve frequent and fine-grained authentication and authorisation. All requested permissions must be restricted to a specific entity under access and only given the minimum permissions for the current operation. This is similar to the principle of the least privilege in the access control. It is necessary to enumerate all possible access conditions and avoid conflicts among policies by comparing a series of elements related to access such as subjects, resources, and context. At the same time, the principle of the least privilege can also reduce the scale of risks caused by the abuse of power and minimize the scope of threats. Additionally, dynamic security policies must be used to maintain the necessary flexibility in dynamic contexts. Therefore, the scale of zero trust security policies is often determined based on the complexity of the deployment scenario.
-
All data and services as resources. Zero trust expands resource coverage and protects critical resources from damage. Logically, the access can be regarded as the operation of the subject in a specific environment, aiming to protect against existing attacks. However, once services involving data flow and computation are damaged, access security will also be affected, and protection against attacks cannot resist unknown attacks. Therefore, all data and services included in the zero trust access process are regarded as resources that are as important as the object or device being accessed, and critical resources are specifically protected.
-
Continuous monitoring and evaluation. No entity is inherently trustworthy; thus, all entities should be monitored. The monitoring proposed here does not monitor only specific threat behaviors or characteristics as before, it monitors all states of all entities (data flow, devices, services, files) related to the access. A robust continuous monitoring system can collect environmental information as much as possible and provides reliable data for safety assessment. As the observable information increases, the credibility of the security analysis results obtained by the assessment system would increase, thereby reducing the probability of threats caused by the trust.
Zero trust is a cybersecurity paradigm, holistic model, systematic approach, and set of guiding principles. Although it can be interpreted in many ways in different scenarios, its principles are constant. Researchers have always realized zero trust in applications and devices, authentication and access control, and network architecture. From these perspectives, zero trust and its deployment can be analysed intuitively.
1.3. Zero Trust Achievement
Zero trust is a cybersecurity paradigm wherein no user, transaction, or network traffic is trusted, unless verified [
24]. Based on these principles, it can be guaranteed mainly through four aspects: authentication, access control, continuous monitoring, and evaluation [
25]. These components are closely combined to realize the final security system. Currently, there are a few zero trust approaches in academic and industrial research, and these achievements can help scholars understand how to achieve zero trust.
To address the security risks of the distributed denial of service attacks and sniffing attacks owing to unauthorised access to infrastructure, CSA follows a “need-to-know” model, and proposes SDP as a security model/framework that dynamically protects modern networks [
8,
26,
27]. Further, the CSA proposes that the premise of a traditional enterprise network architecture is to create an internal network demarcated from the outside world by a fixed perimeter. The architecture consists of a series of firewall functions that block external users and allow internal users to exit. However, the traditional fixed-perimeter model is rapidly becoming obsolete. Bring-your-own-devices and phishing attacks have resulted in untrusted access, and the location of the perimeter has been changed by software-as-a-service and infrastructure-as-a-service. This is similar to the internal threat issues that zero trust attempts to fix, and the researchers regard SDP as an approach to zero trust. SDP, which differs from a traditional system, affords visibility to everyone but allows connectivity on a “need-to-know” basis by adding several point control systems. In a real system, SDPs replace physical appliances with logical components that operate under the control of an application owner. This implies that it transfers the responsibility of granting trust to the requester from the application designer and then to the resource owner.
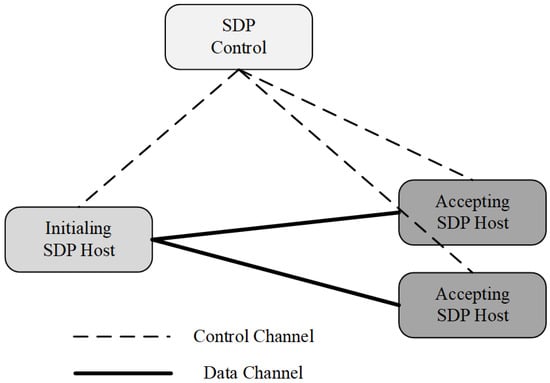
The architecture of the SDP consists of two components: SDP hosts and SDP controllers. SDP hosts can initiate or accept connections. These actions are managed through an interaction with the SDP controller via a secure control channel (see
Figure 3). Thus, the control and data planes are separated to realise a completely scalable system. In this architecture, the SDP controller undertakes the task of performing authentication before access and controls the opening and closing of the data channels between hosts. Thus, SDP can effectively defend against remote hypervisor attacks, denial of service attacks, virtual machine hopping, and port scanning [
28]. Five separate security layers compose and support the SDP architecture: single packet authentication (SPA), mutual transport layer security (mTLS), device validation (DV), dynamic firewalls, and application binding (AppB). Among them, the SPA is the basic component for maintaining secure authentication and valid traffic before the connection between the parties of the transaction. The SPA requires that the first packet be cryptographically sent from the initiating host to the SDP controller, where the host’s authorisation is verified before granting it access. Subsequently, the SPA is sent by the host to the gateway to help it determine the authorised host’s traffic and reject all other traffic. With these components and technologies, the SDP can effectively defend against attacks from insiders and protect critical resources.
Figure 3. The architecture of the SDP.
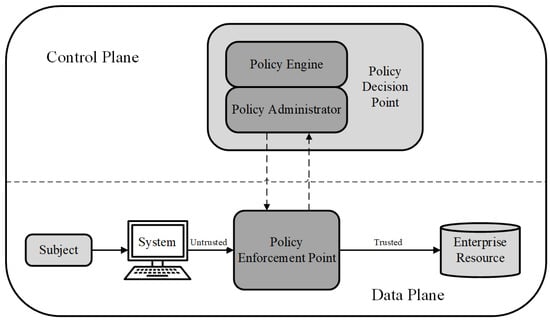
The zero trust architecture (ZTA) was first proposed by NIST in 2020 [
9]. Compared to the SDP, the ZTA is a systematic security architecture that contains technologies such as SDP, access control, and multi-factor authentication. This supports the logical component of ZTA (see
Figure 4) that separates the control and data planes. The policy decision point (PDP) is the core of the control plane and is responsible for authentication and authorisation. It grants access based on trust that satisfies the security policies of the system. The policy enforcement point (PEP) is the core of the data plane responsible for transporting the trust from the PDP to the current access of the subject and permits the connection between the subject and enterprise resources. By demarcating the control and data planes, the ZTA can effectively integrate the related technologies and modularly add them into the architecture.
Figure 4. The logical components of ZTA.
Syed et al. [
29] analysed and collated the basic principles and related technologies of the ZTA. They also derived seven directions for zero trust: lightweight and scalable continuous authentication techniques, fine-grained context-based access, data encryption under resource constraints, microsegmentation techniques to cope with single points of failure, threat-aware systems that integrate heterogeneous data sources and monitoring logs, reliable automated trust assessment knowledge systems, and application-level access control enforcement procedures. As can be observed, the implementation of zero trust relies on the combination of multiple technologies.
To accelerate the deployment and implementation of zero trust, the NIST categorises the mainstream technologies for it into three topics from a technical perspective, namely SDP, identity and access management (IAM), and micro-segmentation (MSG), which together are known as “SIM”. IAM acts as a web service to ensure the secure access to resources by controlling the authentication and authorisation. As an application technology predating ZTA, IAM systems have already been offered by many organisations such as AWS [
30], SailPoint [
31], IBM [
32], Oracle [
33], RSA [
34], and Core Security [
35]. MSG, on the other hand, is a network security technology that is concerned with the isolation of horizontal traffic in the network [
36]. By dividing all the services within a data centre into several tiny network nodes according to specific rules, MSG can enforce the access control on these nodes through dynamic policies, thereby achieving logical segmentation. From the perspective of zero trust deployment, SDP provides the technical foundation at the network data level, IAM provides a viable management method for continuous authentication and fine-grained access control, and MSG delineates the logical areas of business data. With these technologies as its foundation, zero trust has progressed rapidly in a short period.
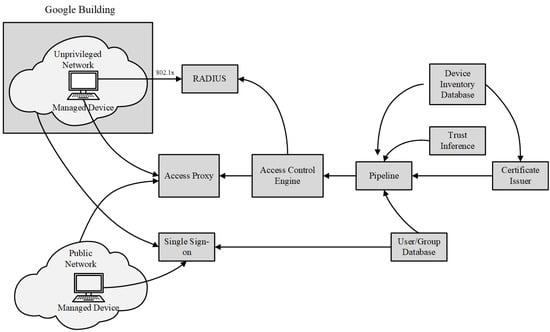
BeyondCorp, proposed by Google for its enterprise security, is also recognised as a valid solution for zero trust. Based on the assumption that an internal network is fraught with as much danger as the public Internet, BeyondCorp is a new security model that dispenses with a privileged corporate network [
5,
6,
7]. It requires that all access to enterprise resources be fully authenticated, authorised, and encrypted based on the device state and user credentials. According to the fine-grained access to different parts of enterprise resources, the user experiences of local and remote access to enterprise resources are identical. The major components of BeyondCorp are shown in
Figure 5. To remove trust from the network, BeyondCorp defines and deploys an unprivileged network that closely resembles an external network, which is still within a private address space controlled by Google itself. Furthermore, BeyondCorp uses a strictly managed access control list (ACL) with the information of all the client devices related to Google. The ACL controls access between different parts of Google’s network using the access control engine.
Figure 5. BeyondCorp components and access flow.
As a critical technology in networks, the security of Docker deployments is noteworthy. Leahy et al. [
37] investigated the security state of Docker containers deployed by default on Linux from a containerisation perspective and proposed a zero trust container architecture (ZTCA). The ZTCA builds on the strategic ideas and principles of the ZTA and successfully demonstrates that the zero trust principle can censor and secure a wide range of Docker use cases to ensure the security of Docker deployment. This demonstrates that the relevant security principles at the core of zero trust can not only theoretically secure systems, but also provide security enhancements to existing technologies. However, the proposed framework has the same limitations as the other security frameworks. It is complex to deploy and requires a high level of security personnel, which are common problems faced by existing zero trust frameworks. Therefore, simplifying the design process, while ensuring security, is critical for future zero trust research.
Taking a comprehensive look at various zero trust architectures, it can be observed that zero trust architecture is a holistic solution that encompasses the entire life cycle of a network. It covers aspects such as identity authentication, access control, data protection, network security, application security, and threat monitoring. By integrating these technologies into the architecture, zero trust achieves its security objectives. From a trust perspective, it is the trust established through these aspects that ensures the overall security of the zero trust architecture.
In the context of identity authentication, trust is derived from the verification of the legitimacy of the requesting entity, and it serves as a fundamental consideration when establishing a zero trust architecture. Whether it is traditional user authentication mechanisms or more context-aware and continuous identity authentication methods, as well as device authentication mechanisms that focus on digital identity, these identity authentication technologies hold the same significance within the zero trust architecture. Security practitioners of zero trust need to selectively apply appropriate technologies based on specific scenarios and business requirements.
In the realm of access control, trust originates from the effective granting and restriction of permissions to entities during access, which forms the fundamental guarantee for the principle of least privilege in zero trust. Identity-based, role-based, attribute-based, intent-based, and risk-based access control mechanisms, which provide assistance in access granularity, permission granting, and policy management, are all crucial considerations for the design and implementation of a zero trust architecture. These mechanisms should be taken into account by zero trust security researchers. Regarding data protection, trust relies on the reliability of encryption algorithms, and the implementation of a zero trust architecture necessitates the selection of suitable solutions based on specific security requirements, data formats, and computational resources of the given scenario.
In terms of network security, trust is built upon the effectiveness of network segmentation, which is an essential aspect that needs to be determined prior to deploying a zero trust architecture. Different segmentation strategies will influence the choice of specific technologies in other areas, ultimately impacting the flexibility of the zero trust architecture.
Application security and threat monitoring, on the other hand, further mitigate uncertainties introduced by human factors within a zero trust architecture. By promptly detecting and responding to abnormal events, these practices help reduce security risks.
All of these zero trust architectures seek to separate data and control to a great extent and achieve the security requirements of zero trust through the joint management of different control components. However, it is important to note that the ultimate goal of zero trust is to protect against insider threats that existing security models cannot protect against, which requires it to be deployed in a realistic manner to validate theoretical and methodological feasibility and reliability. In addition, research on insider threats is an area on which zero trust researchers need to focus. Only a comprehensive understanding of insider threats can render zero trust research results usable and feasible for solving practical problems.
2. Application
The IT landscape is empowered by a connected world that is more susceptible to malicious activity owing to its connectedness, user diversity, wealth of devices, and globally distributed applications and services. The complexity of the current and emerging Cloud and IoT has exposed the lack of effectiveness of traditional security perimeters. These issues can be addressed separately by fine-grained access control, continuous authentication, log audition, and network microsegmentation. As a cybersecurity paradigm combining these technologies, zero trust can address the issues of the traditional security perimeter and can be applied to Cloud and IoT. This section introduces partial zero trust solutions for Cloud and IoT scenarios and analyses the focus areas in these two contexts. Additionally, the last section provides an overview table of the relevant literature.
2.1. Application of Zero Trust in the Cloud Environment
The benefits of clouds include virtual computing technology, a powerful storage capacity, and good system scalability. This makes them more familiar and valuable to enterprises and scholars. With the increasing scale and complexity of in-cloud environments in recent years, insider attacks against clouds have increased significantly. However, most clouds still adopt a traditional perimeter defence, which leaves them without effective defences against insider threats, especially data loss, theft, and destruction caused by lateral attacks in the cloud. The proposal of zero trust provides a new solution to these issues, and scholars have introduced zero trust in cloud environments with appropriate adaptations to the original technology [
38,
39,
40,
41].
The traditional security perimeter simply divides a network into an internal trusted network and an external untrusted network. This prevents the perimeter from defending against insider threats in the internal network and creates risks for the critical resources. For this purpose, Huang et al. [
38] proposed a framework for analysing trust relations in the cloud. The trust mechanism comprises cloud service trust, service provider trust, cloud broker trust, cloud auditor trust, and societal trust. This fine-grained segmentation enables trust to be applied on a smaller scale.
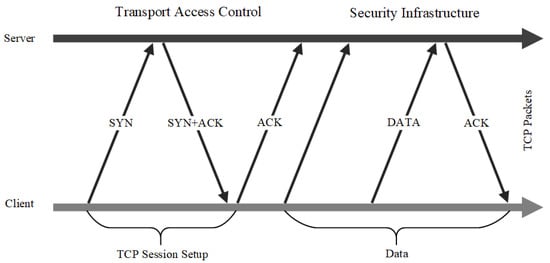
Considering that the best security practices adopting network segmentation in traditional data centres are not well suited to cloud computing environments, C. DeCusatis et al. [
39] proposed a zero trust cloud network segmentation method achieved by transport access control (TAC) and first packet authentication. They combined both approaches into a single unified defence to realize zero trust in the cloud environment. Each network session must be independently authenticated at the transport layer before any access to the network or protected servers is granted. In addition, explicit trust is established by generating a network identity token attached to the first packet of a TCP connection before the data traffic of sessions between the client and server (see
Figure 6). However, this approach to security is predicated on modifications to the transport layer protocol, which imposes a significant overhead on cloud service providers that have already deployed operations.
Figure 6. TAC approach of Transport Layer.
Owing to the emerging microservices of the cloud, attacks can propagate laterally within the data centre by exploiting cross-service dependencies. Thus, Zaheer et al. [
40] proposed shifting the perimeter from network endpoints to workflows. They assumed that the infrastructure provider and information from the trusted infrastructure were trustworthy. Based on this assumption, they proposed an extended Berkeley Packet Filter that could track the context of a microservice workflow. Thus, the perimeter of the workflows could be changed by detecting the workflow data and the context of the provider. This method implements zero trust for applications and enhances security in a microservice cloud environment.
Zolotukhin et al. [
42] used the defence idea of the SDP to deploy deep learning components on top of the software-defined networking (SDN) and network function virtualization (NFV) controllers in the SDN and NFV technologies, thus enabling the real-time detection of network states and dynamic adjustment of security policies. However, the practicality of the approach was not effectively proven, as the researchers used artificially generated network traffic data. By empowering network security management components with intelligence through reinforcement learning algorithms, the components could no longer be limited to static and unchanging security policies, which is in line with the reality of dynamically changing network environments and security requirements.
Comparing the zero trust solutions in cloud scenarios reveals that the focus is primarily on addressing the interactions between large-scale data and services in the cloud, efficient network segmentation within the cloud, and the design of effective trust evaluation and auditing mechanisms. These three requirements highlight the key considerations for zero trust in cloud scenarios: ensuring secure communication for large-scale interactions, enabling dynamic network construction, and establishing explicit trust relationships. From a trust perspective, the interactions between services in the cloud outweigh those between individuals and services. This implies that establishing and maintaining trust relationships between services is of paramount importance for zero trust in the cloud. Additionally, the extensive interactions in the cloud generate a significant amount of recordable data. Leveraging information theory concepts such as information entropy, source coding, and channel coding can provide additional insights into the state of the cloud, enabling more comprehensive network intelligence and enhancing communication reliability and transmission rates.
In addition to the security components in the cloud, humans are also a source of risk with which zero trust is concerned. Sarkar et al. [
43] surveyed several implementations of a zero-trust-based cloud-network model. Different methods and applications for authenticating and authorising key services used in a trust-based cloud network were examined; it was found that there were various problems in moving from existing system architectures to a ZTA for deploying zero trust in a cloud environment. Among these, the most obvious impediment was humans. Zero trust focuses on more granular data than other security architectures and, therefore, may also carry the risk of compromising privacy. Cloud is the dominant storage and management environment in business today, and zero trust cannot be accepted by the general public, regardless of how secure it is, if a user or organisation discovers that the privacy of their data on the cloud has been compromised. Therefore, to deploy zero trust in the cloud, the architecture and approach must be designed for data privacy.
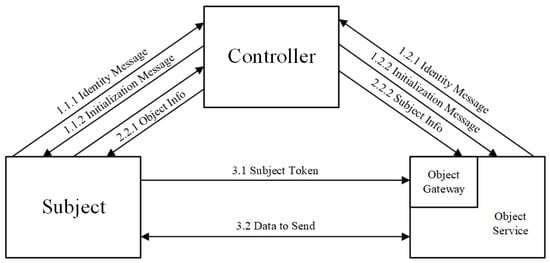
Although these zero trust solutions can provide a better protection for resources in the cloud, there are still some shortcomings. First, most of the existing zero trust solutions adopt a three-element architecture in which the control and data planes, that is, the subject, controller, and object, are separated (see Figure 7). The controller serves as the central node for the authentication and access control, and its ports are completely open to the entire network. Once the controller has a single point of failure or is attacked, the execution efficiency of the entire zero trust solution is significantly reduced, and its security is affected. If a distributed controller is used, the consistency of information between the controllers becomes a key feature that affects the accuracy of the execution result. Although the strong consistency technology of the blockchain can be used to ensure the synchronisation of information between the various controllers, the performance and time overhead caused by the blockchain will become an important factor affecting the availability of the program. Therefore, zero trust solutions in the cloud environment must be developed for specific needs at the expense of certain indicators, in exchange for the improvement of other indicators.
Figure 7. Basic zero trust architecture.
2.2. Application of Zero Trust in the IoT Environment
The IoT is an Internet system that integrates various sensors and objects to communicate with one another without human intervention. Security and privacy issues have become increasingly evident with the large-scale deployment of IoT [
44]. Unknown devices and traffic can exacerbate the spread of vulnerabilities between interconnected devices in sensitive locations with access to potentially harmful actuation capabilities [
45]. With the rise of AI and machine learning technology, IoT technology has gradually improved, becoming one of the development trends in society. However, the large number of devices moving in and out of the IoT makes it difficult to deploy a fixed perimeter, and device management has become increasingly complicated. With the deepening of research, scholars believe that zero trust, with the requirement that all devices must be verified, whether they are inside or outside, can address these issues, thus ensuring the security of the entire IoT.
With its advantages of distributed databases, smart contracts, consensus, and immutability, blockchain has become a popular technology for achieving zero trust in IoT. Samaniego et al. [
46] proposed Amatista, a blockchain-based middleware, and applied it to achieve hierarchical zero trust management in IoT. This is a novel zero trust hierarchical mining process that allows different levels of trust, to validate infrastructure and transactions. The shift from a centralised to a distributed approach for trust management and mining enables the deployment of zero trust in the IoT environment. Dhar et al. [
47] proposed a peer-to-peer blockchain network framework that operates in parallel with a zero-trust-based security architecture. Components, such as the segmentation gateway, microcore, perimeter (MCAP), and management server are connected to the blockchain. It addresses the security concerns of risk-based MCAPs and cryptographically secures storage and transmission. Zhao et al. [
48] introduced blockchain as an authentication scheme for IoT devices, making it possible to switch smart devices from an untrusted state to a trusted state. They all leverage the distribution and immutability of blockchain to deploy zero trust in the IoT.
Researchers have further explored the relationship between zero trust and blockchain through studies from both theoretical and application perspectives. Alevizos et al. [
49] conducted a comparative analysis of the traditional perimeter-based model and zero trust model, and explored its potential use for endpoints based on blockchain foundations. Their study showed the capability of endpoint integrity testing, demonstrating that the blockchain technology is indeed capable of supporting endpoint authentication for ZTA. However, it should be noted that the biggest impediment to the application of blockchain technology to zero trust is the significant overhead associated with the technology itself. The fine-grained authentication and access control necessary for zero trust affect the usability of blockchains in real-world scenarios. From this perspective, to apply blockchain technology to zero trust, research might be predicated on two ideas: one is to simplify the consensus algorithm and data structure in the blockchain to accommodate the constrained endpoint resources, and the other is to use multiple endpoint clusters to increase the computing power of blockchain nodes.
To use blockchain technology to achieve zero trust for IoT, researchers are also attempting to optimize existing ZTAs and zero trust technologies. Palmo et al. [
50] found that ensuring the reliability of IoT itself is critical when embedding IoT devices into SDPs. In this regard, they analysed the federation evaluation method of the IoT gateway, federation evaluation method of identity provider (IdP) and federation evaluation method of certification authority. From a qualitative evaluation perspective, it was determined that the IdP federal evaluation method had the least overhead and was the easiest to administer and install. However, for the application of zero trust in IoT, the existing research lacks validation in simulated or actual IoT environments. A purely qualitative evaluation can only prove the feasibility of the method from a theoretical perspective, not its effectiveness and usability in reality.
How zero trust can be deployed in the IoT environment under 5G is also a current research priority. Valero et al. [
51] proposed a new security and trust framework for 5G multidomain scenarios and validated zero trust principles in distributed multistakeholder environments. The security and trust levels of multi-stakeholder 5G networks are improved through trust and intra-domain and inter-domain modules. This hierarchical approach to security rules allows individual stakeholders in a 5G network to focus more on their own security-related matters, thus avoiding unnecessary overheads. However, the dynamic nature of stakeholders cannot be ignored. How this security and trust framework automatically adjusts when stakeholders change is the next critical issue to consider. At the same time, the trustworthiness of the AI approach used in the security and trust framework is also a difficult issue in zero trust research.
Li et al. [
52] also provided an outlook on the security of future industrial IoT, resulting in a blockchain-based zero trust architecture for future IoT. To cope with the complexity and performance requirements of 5G-IoT systems, they proposed specific frameworks to achieve the zero trust authentication of devices/users/applications. However, 5G-IoT poses significantly more security issues than traditional IoT, particularly heterogeneity and interoperability. Zero trust research under 5G-IoT could mitigate the lightweight requirements and focus on how to provide a set of architectures with compatibility, scalability, and different granularity of the access control.
Some scholars believe that zero trust can address the issue of power IoT security. The power IoT has a massive terminal access and facilitates efficient information sharing, while addressing the problem of increasingly blurred grid boundaries. Chen et al. [
53] proposed the use of blockchain to enhance the security of data interaction and achieve a high-level protection of data circulation in all the links of the power network. They used blockchain as a computing paradigm and collaboration model to establish trust at a low cost in an untrusted competitive environment. Based on the ZTA, Xiaojian et al. [
54] proposed a power IoT security protection architecture for network boundary and channel security protection, business application security function design, and mobile terminal software security protection. They used a central policy library to manage dynamic access-control authorisation strategies. In addition, they reduced the granularity of access to a single operation on a single device. These studies proved that zero-trust-related technologies can effectively address security issues in IoT environments.
In contrast to the close relationship between zero trust solutions and services in cloud scenarios, zero trust solutions in the IoT focus more on integrating with blockchain technology and addressing the requirements of different real-world scenarios. In terms of blockchain integration, the emphasis of zero trust solutions lies in leveraging the distributed nature of blockchain to achieve multi-level trust management and designing device authentication schemes based on information consistency. However, the incorporation of zero trust’s fine-grained identity and access control introduces significant overhead, which also affects its integration with blockchain. In addressing the requirements of different real-world scenarios, there are diverse demands on data interaction, communication methods, data management, and scalability in zero trust solutions due to the dynamic nature of 5G networks, the complexity of industrial IoT, and the security and reliability of smart grids. While existing zero trust solutions in IoT and blockchain are already capable of achieving some functionalities, the inherent limitations of IoT still pose challenges to the design and implementation of zero trust solutions.
To further deploy zero trust in IoT environments, future researchers should focus on the following three issues. The first is the deployment of zero trust technologies under resource constraints. Current zero trust technologies tend to prioritise security over lightweighting, but most IoT devices cannot afford the computational overhead (such as deep learning) that significantly exceeds the computation required by their own business. Therefore, lightweight deployment is the first issue to be addressed in zero trust deployments under IoT. The next issue is how to cope with the impact of changing device dynamics on zero trust deployments. In reality, the movement of IoT devices can have an impact on factors such as transmission rate and network topology, thus changing the state of zero trust deployment. Finally, the interoperability of heterogeneous devices is an issue. There are many different types of IoT devices with differences in device models, message formats, and transmission methods. One of the key principles of zero trust security is data monitoring and management. This heterogeneity can hinder the deployment of zero trust in the IoT. An architecture or protocol that supports the interconnection of heterogeneous devices can significantly facilitate the deployment of zero trust in IoT.
This entry is adapted from the peer-reviewed paper 10.3390/e25121595