With the inclusion of communication networks and smart metering devices, the attack surface has increased in microgrids, making them vulnerable to various cyber-attacks. The negative impact of such attacks may render the microgrids out-of-service, and the attacks may propagate throughout the network due to the absence of efficient mitigation approaches. AI-based techniques are being employed to tackle such data-driven cyber-attacks due to their exceptional pattern recognition and learning capabilities. AI-based methods for cyber-attack detection and mitigation that address the cyber-attacks in microgrids are summarized.
- cyber-attacks
- microgrids
- artificial intelligence
- detection
- neural networks
1. Introduction

| Location | Target | Type | Impact |
|---|---|---|---|
| North America (2003) | Network failures in control room operating system | Denial of service | Blackout across multiple regions |
| Korea Hydro and Nuclear Power (2014) | Unauthorized access to critical information | Potential loss of confidential information and designs | Compromised security and safety of plant and personnel |
| Ukraine (2015) | BackEnergy malware in control room computers | Denial of service, False data injection | Blackout across multiple substations |
| Kyiv (2016) | Industroyer malware targeting industrial control systems | Denial of service, Issuing false control commands | Power outage to at least one-fifth of Kyiv |
| Middle East petrochemical plant (2017) | Safety system of the plant | Potential denial of services and life loss | Plant shut down |
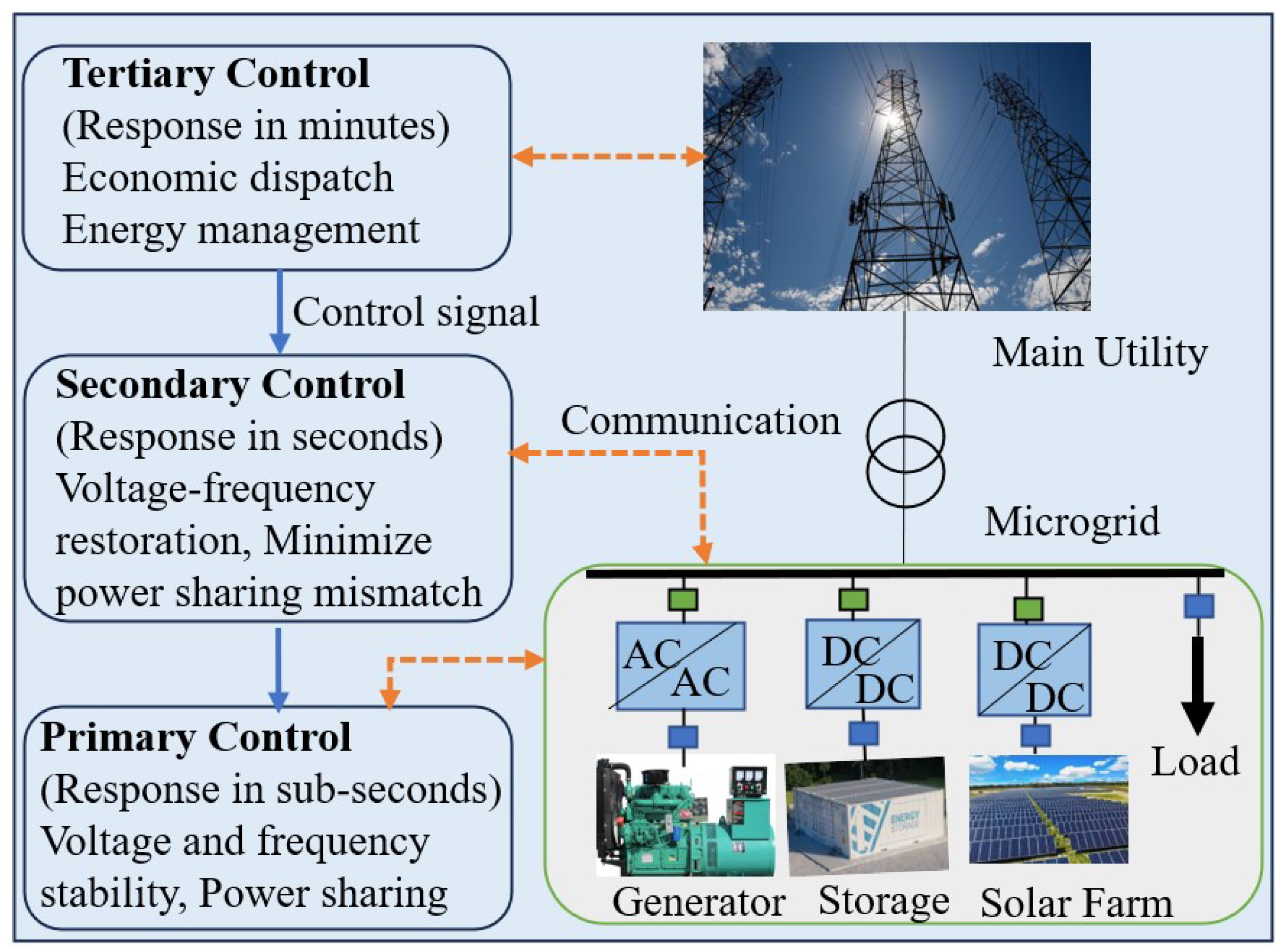
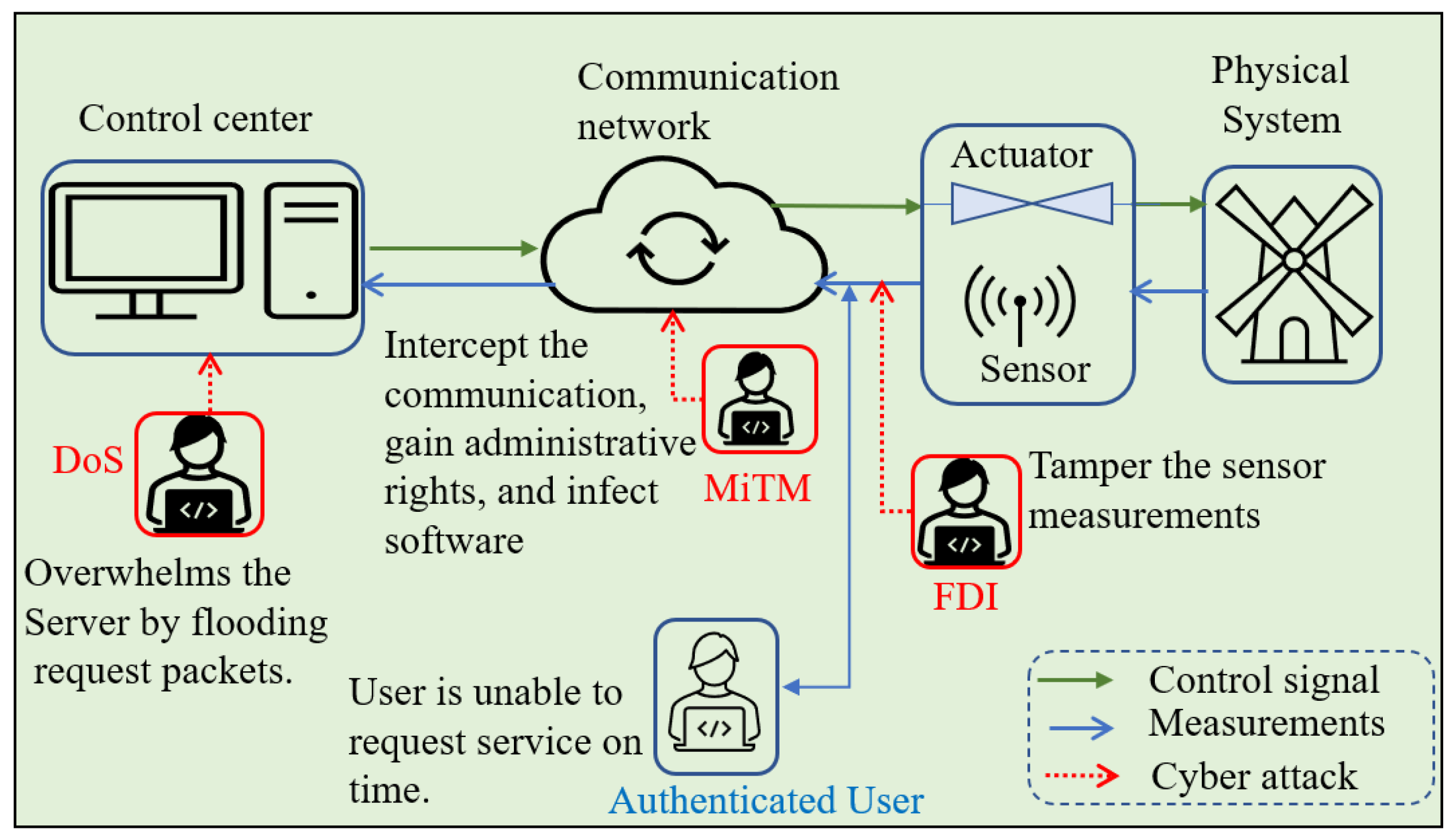
2. Types of Cyber-Attacks in Microgrids
3. AI-Based Cyber-Attack Detection
4. AI-Based Cyber-Attack Mitigation
This entry is adapted from the peer-reviewed paper 10.3390/en16227644
References
- Nassif, A.B.; Ericson, S.; Abbey, C.; Jeffers, R.; Hotchkiss, E.; Bahramirad, S. Valuing Resilience Benefits of Microgrids for an Interconnected Island Distribution System. Electronics 2022, 11, 4206.
- Aghmadi, A.; Hussein, H.; Polara, K.H.; Mohammed, O. A Comprehensive Review of Architecture, Communication, and Cybersecurity in Networked Microgrid Systems. Inventions 2023, 8, 84.
- de la Cruz, J.; Wu, Y.; Candelo-Becerra, J.E.; Vásquez, J.C.; Guerrero, J.M. A review of networked microgrid protection: Architectures, challenges, solutions, and future trends. CSEE J. Power Energy Syst. 2023.
- Bazmohammadi, N.; Madary, A.; Vasquez, J.C.; Mohammadi, H.B.; Khan, B.; Wu, Y.; Guerrero, J.M. Microgrid digital twins: Concepts, applications, and future trends. IEEE Access 2021, 10, 2284–2302.
- Espina, E.; Llanos, J.; Burgos-Mellado, C.; Cardenas-Dobson, R.; Martinez-Gomez, M.; Saez, D. Distributed control strategies for microgrids: An overview. IEEE Access 2020, 8, 193412–193448.
- Nasirian, V.; Moayedi, S.; Davoudi, A.; Lewis, F.L. Distributed cooperative control of DC microgrids. IEEE Trans. Power Electron. 2014, 30, 2288–2303.
- Morstyn, T.; Hredzak, B.; Agelidis, V.G. Distributed cooperative control of microgrid storage. IEEE Trans. Power Syst. 2014, 30, 2780–2789.
- Mustafa, A.; Poudel, B.; Bidram, A.; Modares, H. Detection and mitigation of data manipulation attacks in AC microgrids. IEEE Trans. Smart Grid 2019, 11, 2588–2603.
- Beg, O.A.; Nguyen, L.V.; Johnson, T.T.; Davoudi, A. Signal temporal logic-based attack detection in DC microgrids. IEEE Trans. Smart Grid 2018, 10, 3585–3595.
- Khan, A.A.; Beg, O.A. Cyber Vulnerabilities of Modern Power Systems. In Power Systems Cybersecurity: Methods, Concepts, and Best Practices; Haes Alhelou, H., Hatziargyriou, N., Dong, Z.Y., Eds.; Springer International Publishing: Cham, Switzerland, 2023; pp. 47–66.
- Bhusal, N.; Abdelmalak, M.; Kamruzzaman, M.; Benidris, M. Power system resilience: Current practices, challenges, and future directions. IEEE Access 2020, 8, 18064–18086.
- Ribas Monteiro, L.F.; Rodrigues, Y.R.; Zambroni de Souza, A. Cybersecurity in Cyber–Physical Power Systems. Energies 2023, 16, 4556.
- Nejabatkhah, F.; Li, Y.W.; Liang, H.; Reza Ahrabi, R. Cyber-security of smart microgrids: A survey. Energies 2020, 14, 27.
- Tan, S.; Wu, Y.; Xie, P.; Guerrero, J.M.; Vasquez, J.C.; Abusorrah, A. New challenges in the design of microgrid systems: Communication networks, cyberattacks, and resilience. IEEE Electrif. Mag. 2020, 8, 98–106.
- Tan, S.; Xie, P.; Guerrero, J.M.; Vasquez, J.C. False data injection cyber-attacks detection for multiple DC microgrid clusters. Appl. Energy 2022, 310, 118425.
- Venkatachary, S.K.; Prasad, J.; Samikannu, R. Cybersecurity and cyber terrorism-in energy sector—A review. J. Cyber Secur. Technol. 2018, 2, 111–130.
- Suprabhath Koduru, S.; Machina, V.S.P.; Madichetty, S. Cyber Attacks in Cyber-Physical Microgrid Systems: A Comprehensive Review. Energies 2023, 16, 4573.
- Krause, T.; Ernst, R.; Klaer, B.; Hacker, I.; Henze, M. Cybersecurity in power grids: Challenges and opportunities. Sensors 2021, 21, 6225.
- MITRE ATT&CK Matrix for Enterprise. Available online: https://attack.mitre.org/ (accessed on 10 November 2023).
- Ramotsoela, D.T.; Hancke, G.P.; Abu-Mahfouz, A.M. Practical Challenges of Attack Detection in Microgrids Using Machine Learning. J. Sens. Actuator Netw. 2023, 12, 7.
- Karanfil, M.; Rebbah, D.E.; Debbabi, M.; Kassouf, M.; Ghafouri, M.; Youssef, E.N.S.; Hanna, A. Detection of Microgrid Cyberattacks Using Network and System Management. IEEE Trans. Smart Grid 2023, 14, 2390–2405.
- Pinto, S.J.; Siano, P.; Parente, M. Review of Cybersecurity Analysis in Smart Distribution Systems and Future Directions for Using Unsupervised Learning Methods for Cyber Detection. Energies 2023, 16, 1651.
- Ortega-Fernandez, I.; Liberati, F. A Review of Denial of Service Attack and Mitigation in the Smart Grid Using Reinforcement Learning. Energies 2023, 16, 635.
- Kim, Y.; Hakak, S.; Ghorbani, A. Smart grid security: Attacks and defence techniques. IET Smart Grid 2023, 6, 103–123.
- Sahoo, S.; Blaabjerg, F.; Dragicevic, T. (Eds.) Cyber Security for Microgrids; IEEE: New York, NY, USA, 2022.
- Leng, M.; Sahoo, S.; Blaabjerg, F.; Molinas, M. Projections of Cyberattacks on Stability of DC Microgrids—Modeling Principles and Solution. IEEE Trans. Power Electron. 2022, 37, 11774–11786.
- Jamali, M.; Sadabadi, M.S.; Davari, M.; Sahoo, S.; Blaabjerg, F. Resilient Cooperative Secondary Control of Islanded AC Microgrids Utilizing Inverter-Based Resources Against State-Dependent False Data Injection Attacks. IEEE Trans. Power Electron. 2023, 1–12.
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting cybersecurity attacks in internet of things using artificial intelligence methods: A systematic literature review. Electronics 2022, 11, 198.
- Trivedi, R.; Khadem, S. Implementation of artificial intelligence techniques in microgrid control environment: Current progress and future scopes. Energy AI 2022, 8, 100147.
- Nair, D.R.; Nair, M.G.; Thakur, T. A smart microgrid system with artificial intelligence for power-sharing and power quality improvement. Energies 2022, 15, 5409.
- Wu, T.; Wang, J. Artificial intelligence for operation and control: The case of microgrids. Electr. J. 2021, 34, 106890.
- Lv, L.; Wu, Z.; Zhang, L.; Gupta, B.B.; Tian, Z. An Edge-AI Based Forecasting Approach for Improving Smart Microgrid Efficiency. IEEE Trans. Ind. Inform. 2022, 18, 7946–7954.
- Zhao, S.; Blaabjerg, F.; Wang, H. An Overview of Artificial Intelligence Applications for Power Electronics. IEEE Trans. Power Electron. 2021, 36, 4633–4658.
- Dewangan, F.; Abdelaziz, A.Y.; Biswal, M. Load Forecasting Models in Smart Grid Using Smart Meter Information: A Review. Energies 2023, 16, 1404.
- Poti, K.D.; Naidoo, R.M.; Mbungu, N.T.; Bansal, R.C. Intelligent solar photovoltaic power forecasting. Energy Rep. 2023, 9, 343–352.
- Yang, Y.; Guo, L.; Li, X.; Li, J.; Liu, W.; He, H. A data-driven detection strategy of false data in cooperative DC microgrids. In Proceedings of the IECON 2021—47th Annual Conference of the IEEE Industrial Electronics Society, Toronto, ON, Canada, 13–16 October 2021; pp. 1–6.
- Banda, M.K.; Koduru, S.S.; Machina, V.S.P.; Madichetty, S. A Deep Learning Based Cyber Attack Detection and Mitigation Scheme in Synchronous Buck Converter. In Proceedings of the 2022 IEEE International Conference on Power Electronics, Drives and Energy Systems (PEDES), Jaipur, India, 14–17 December 2022; pp. 1–6.
- Suprabhath, K.; Prasad, M.V.S.; Chetty, S.; Mishra, S. A deep learning based cyber attack detection scheme in DC microgrid systems. CPSS Trans. Power Electron. Appl. 2023, 8, 2.
- Siniosoglou, I.; Radoglou-Grammatikis, P.; Efstathopoulos, G.; Fouliras, P.; Sarigiannidis, P. A unified deep learning anomaly detection and classification approach for smart grid environments. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1137–1151.
- Panthi, M. Anomaly detection in smart grids using machine learning techniques. In Proceedings of the 2020 First International Conference on Power, Control and Computing Technologies (ICPC2T), Raipur, India, 3–5 January 2020; pp. 220–222.
- Glauner, P. Big Data-Driven Detection of False Data Injection Attacks in Smart Meters. IEEE Access 2021, 9, 144313–144326.
- Basati, A.; Guerrero, J.M.; Vasquez, J.C.; Bazmohammadi, N.; Golestan, S. A Data-Driven Framework for FDI Attack Detection and Mitigation in DC Microgrids. Energies 2022, 15, 8539.
- Abazari, A.; Zadsar, M.; Ghafouri, M.; Atallah, R.; Assi, C. A data mining/anfis and adaptive control for detection and mitigation of attacks on dc mgs. IEEE Trans. Smart Grid 2022, 14, 2406–2422.
- Khan, A.A.; Beg, O.A.; Jin, Y.F.; Ahmed, S. An Explainable Intelligent Framework for Anomaly Mitigation in Cyber-Physical Inverter-based Systems. IEEE Access 2023, 11, 65382–65394.
- Tian, E.; Wu, Z.; Xie, X. Codesign of FDI Attacks Detection, Isolation, and Mitigation for Complex Microgrid Systems: An HBF-NN-Based Approach. IEEE Trans. Neural Netw. Learn. Syst. 2022.
- Habibi, M.R.; Sahoo, S.; Rivera, S.; Dragičević, T.; Blaabjerg, F. Decentralized coordinated cyberattack detection and mitigation strategy in DC microgrids based on artificial neural networks. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 9, 4629–4638.
- Zhang, N.; Sun, Q.; Yang, L.; Li, Y. Event-Triggered Distributed Hybrid Control Scheme for the Integrated Energy System. IEEE Trans. Ind. Inform. 2022, 18, 835–846.
- Yang, L.; Li, X.; Sun, M.; Sun, C. Hybrid Policy-Based Reinforcement Learning of Adaptive Energy Management for the Energy Transmission-Constrained Island Group. IEEE Trans. Ind. Inform. 2023, 19, 10751–10762.
- AlSkaif, T.; Crespo-Vazquez, J.L.; Sekuloski, M.; van Leeuwen, G.; Catalão, J.P.S. Blockchain-Based Fully Peer-to-Peer Energy Trading Strategies for Residential Energy Systems. IEEE Trans. Ind. Inform. 2022, 18, 231–241.
- Cui, S.; Wang, Y.W.; Shi, Y.; Xiao, J.W. A new and fair peer-to-peer energy sharing framework for energy buildings. IEEE Trans. Smart Grid 2020, 11, 3817–3826.
- Lopez-Garcia, T.B.; Coronado-Mendoza, A.; Domínguez-Navarro, J.A. Artificial neural networks in microgrids: A review. Eng. Appl. Artif. Intell. 2020, 95, 103894.
- Singh, N.K.; Mahajan, V. Analysis and evaluation of cyber-attack impact on critical power system infrastructure. Smart Sci. 2021, 9, 1–13.
- Pour, M.M.; Anzalchi, A.; Sarwat, A. A review on cyber security issues and mitigation methods in smart grid systems. In Proceedings of the SoutheastCon 2017, Concord, NC, USA, 30 March–2 April 2017; pp. 1–4.
- Zhang, Z.; Ning, H.; Shi, F.; Farha, F.; Xu, Y.; Xu, J.; Zhang, F.; Choo, K.K.R. Artificial intelligence in cyber security: Research advances, challenges, and opportunities. Artif. Intell. Rev. 2022, 55, 1029–1053.
- Zhang, Y.; Liu, J.; Shen, W. A Review of Ensemble Learning Algorithms Used in Remote Sensing Applications. Appl. Sci. 2022, 12, 8654.
- Mienye, I.D.; Sun, Y. A Survey of Ensemble Learning: Concepts, Algorithms, Applications, and Prospects. IEEE Access 2022, 10, 99129–99149.
- Harrou, F.; Taghezouit, B.; Khadraoui, S.; Dairi, A.; Sun, Y.; Hadj Arab, A. Ensemble Learning Techniques-Based Monitoring Charts for Fault Detection in Photovoltaic Systems. Energies 2022, 15, 6716.
- Arman, A.; Krishnan, V.V.G.; Srivastava, A.; Wu, Y.; Sindhu, S. Cyber physical security analytics for transactive energy systems using ensemble machine learning. In Proceedings of the 2018 North American Power Symposium (NAPS), Fargo, ND, USA, 9–11 September 2018; pp. 1–6.
- Goyel, H.; Swarup, K.S. Data Integrity Attack Detection Using Ensemble-Based Learning for Cyber–Physical Power Systems. IEEE Trans. Smart Grid 2023, 14, 1198–1209.
- Liu, S.; You, S.; Yin, H.; Lin, Z.; Liu, Y.; Yao, W.; Sundaresh, L. Model-Free Data Authentication for Cyber Security in Power Systems. IEEE Trans. Smart Grid 2020, 11, 4565–4568.
- Toker, O.; Khalghani, M.R. Cyber Anomaly Detection Design for Microgrids using an Artificial Intelligent-Based Method. In Proceedings of the 2022 North American Power Symposium (NAPS), Salt Lake City, UT, USA, 9–11 October 2022; pp. 1–5.
- Dehghani, M.; Niknam, T.; Ghiasi, M.; Bayati, N.; Savaghebi, M. Cyber-Attack Detection in DC Microgrids Based on Deep Machine Learning and Wavelet Singular Values Approach. Electronics 2021, 10, 1914.
- Dehghani, M.; Kavousi-Fard, A.; Dabbaghjamanesh, M.; Avatefipour, O. Deep learning based method for false data injection attack detection in AC smart islands. IET Gener. Transm. Distrib. 2020, 14, 5756–5765.
- Mao, J. Data-Driven Cyberattack Detection for Microgrids. Master’s Thesis, KTH School of Electrical Engineering and Computer Science, Stockholm, Sweden, 2022.
- Reda, H.T.; Anwar, A.; Mahmood, A.; Chilamkurti, N. Data-driven approach for state prediction and detection of false data injection attacks in smart grid. J. Mod. Power Syst. Clean Energy 2022, 11, 455–467.
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. Detection of false data injection cyber-attacks in DC microgrids based on recurrent neural networks. IEEE J. Emerg. Sel. Top. Power Electron. 2020, 9, 5294–5310.
- Kwon, S.; Yoo, H.; Shon, T. IEEE 1815.1-based power system security with bidirectional RNN-based network anomalous attack detection for cyber-physical system. IEEE Access 2020, 8, 77572–77586.
- Qiu, W.; Tang, Q.; Wang, Y.; Zhan, L.; Liu, Y.; Yao, W. Multi-view convolutional neural network for data spoofing cyber-attack detection in distribution synchrophasors. IEEE Trans. Smart Grid 2020, 11, 3457–3468.
- Naderi, E.; Asrari, A. Toward detecting cyberattacks targeting modern power grids: A deep learning framework. In Proceedings of the 2022 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 6–9 June 2022; pp. 357–363.
- He, Q.; Shah, P.; Zhao, X. Resilient operation of DC microgrid against FDI attack: A GRU based framework. Int. J. Electr. Power Energy Syst. 2023, 145, 108586.
- Khan, A.A.; Beg, O.A.; Alamaniotis, M.; Ahmed, S. Intelligent anomaly identification in cyber-physical inverter-based systems. Electric Power Syst. Res. 2021, 193, 107024.
- Wan, Y.; Dragičević, T. Data-driven cyber-attack detection of intelligent attacks in islanded dc microgrids. IEEE Trans. Power Electron. 2022, 70, 4293–4299.
- Sourav, S.; Biswas, P.P.; Chen, B.; Mashima, D. Detecting Hidden Attackers in Photovoltaic Systems Using Machine Learning. In Proceedings of the 2022 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Singapore, 25–28 October 2022; pp. 360–366.
- Li, F.; Xie, R.; Yang, B.; Guo, L.; Ma, P.; Shi, J.; Ye, J.; Song, W. Detection and identification of cyber and physical attacks on distribution power grids with pvs: An online high-dimensional data-driven approach. IEEE J. Emerg. Sel. Top. Power Electron. 2019, 10, 1282–1291.
- Hakim, M.S.S.; Karegar, H.K. Detection of False Data Injection Attacks Using Cross Wavelet Transform and Machine Learning. In Proceedings of the 2021 11th Smart Grid Conference (SGC), Tabriz, Iran, 7–9 December 2021; pp. 1–5.
- Qiu, W.; Tang, Q.; Zhu, K.; Yao, W.; Ma, J.; Liu, Y. Cyber spoofing detection for grid distributed synchrophasor using dynamic dual-kernel SVM. IEEE Trans. Smart Grid 2020, 12, 2732–2735.
- Ahmed, S.; Lee, Y.; Hyun, S.H.; Koo, I. Unsupervised machine learning-based detection of covert data integrity assault in smart grid networks utilizing isolation forest. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2765–2777.
- Chen, Y.; Qi, D.; Dong, H.; Li, C.; Li, Z.; Zhang, J. A FDI attack-resilient distributed secondary control strategy for islanded microgrids. IEEE Trans. Smart Grid 2020, 12, 1929–1938.
- Ye, J.; Giani, A.; Elasser, A.; Mazumder, S.K.; Farnell, C.; Mantooth, H.A.; Kim, T.; Liu, J.; Chen, B.; Seo, G.S.; et al. A review of cyber–physical security for photovoltaic systems. IEEE J. Emerg. Sel. Top. Power Electron. 2021, 10, 4879–4901.
- Gaggero, G.B.; Girdinio, P.; Marchese, M. Advancements and research trends in microgrids cybersecurity. Appl. Sci. 2021, 11, 7363.
- Rana, M.M.; Li, L.; Su, S.W. Cyber attack protection and control of microgrids. IEEE/CAA J. Autom. Sin. 2017, 5, 602–609.
- Sahoo, S.; Yang, Y.; Blaabjerg, F. Resilient synchronization strategy for AC microgrids under cyber attacks. IEEE Trans. Power Electron. 2020, 36, 73–77.
- Sahoo, S.; Dragičević, T.; Blaabjerg, F. Multilayer resilience paradigm against cyber attacks in DC microgrids. IEEE Trans. Power Electron. 2020, 36, 2522–2532.
- Zhang, J.; Sahoo, S.; Peng, J.C.H.; Blaabjerg, F. Mitigating concurrent false data injection attacks in cooperative dc microgrids. IEEE Trans. Power Electron. 2021, 36, 9637–9647.
- Mishra, S.; Anderson, K.; Miller, B.; Boyer, K.; Warren, A. Microgrid resilience: A holistic approach for assessing threats, identifying vulnerabilities, and designing corresponding mitigation strategies. Appl. Energy 2020, 264, 114726.
- Naderi, E.; Asrari, A. Experimental Validation of a Remedial Action via Hardware-in-the-loop System Against Cyberattacks Targeting a Lab-scale PV/Wind Microgrid. IEEE Trans. Smart Grid 2023, 14, 4060–4072.
- Danilczyk, W.; Sun, Y.; He, H. ANGEL: An intelligent digital twin framework for microgrid security. In Proceedings of the 2019 North American Power Symposium (NAPS), Wichita, KS, USA, 13–15 October 2019; pp. 1–6.
- Zeng, H.; Zhao, Y.; Wang, T.; Zhang, J. Defense Strategy against False Data Injection Attacks in Ship DC Microgrids. J. Mar. Sci. Eng. 2022, 10, 1930.
- Habibi, M.R.; Dragicevic, T.; Blaabjerg, F. Secure control of dc microgrids under cyber-attacks based on recurrent neural networks. In Proceedings of the 2020 IEEE 11th International Symposium on Power Electronics for Distributed Generation Systems (PEDG), Dubrovnik, Croatia, 28 September–1 October 2020; pp. 517–521.
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. False data injection cyber-attacks mitigation in parallel DC/DC converters based on artificial neural networks. IEEE Trans. Circuits Syst. II Express Briefs 2020, 68, 717–721.
- Habibi, M.R.; Baghaee, H.R.; Blaabjerg, F.; Dragičević, T. Secure control of DC microgrids for instant detection and mitigation of cyber-attacks based on artificial intelligence. IEEE Syst. J. 2021, 16, 2580–2591.
- Habibi, M.R.; Baghaee, H.R.; Blaabjerg, F.; Dragičević, T. Secure MPC/ANN-based false data injection cyber-attack detection and mitigation in DC microgrids. IEEE Syst. J. 2021, 16, 1487–1498.
- Abianeh, A.J.; Wan, Y.; Ferdowsi, F.; Mijatovic, N.; Dragičević, T. Vulnerability identification and remediation of fdi attacks in islanded dc microgrids using multiagent reinforcement learning. IEEE Trans. Power Electron. 2021, 37, 6359–6370.
