Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Subjects:
Computer Science, Information Systems
Anonymity forms the basis of decentralized ecosystems, leading to an increase in criminal activities such as money laundering and illegal currency trading. Especially in blockchain-based metaverse services, activities such as preventing sexual crimes and verifying the identity of adults are becoming essential. Therefore, avatar authentication and the KYC (Know Your Customer) process have become crucial elements.
- blockchain
- smart contract
- avatar
- KYC
- user authentication
- DID
- NFT
- SBT
- ZKP
1. Introduction
The emergence of cryptocurrency using blockchain technology provides decentralization and innovative opportunities for the financial system, but at the same time, it causes many problems. In particular, it is raising concerns about the safety and regulation of the financial system. The most serious problems are AML (Anti-Money Laundering) and CFT (Counter-Financing of Terrorism). According to Chainalysis, USD 23.8 billion worth of cryptocurrency, a 68% increase compared to the previous year, was laundered in 2022 [1]. In addition, due to the borderless nature of cryptocurrency, unlimited foreign exchange transactions are possible and lead to capital flight, which can affect the sustainability of the national economy [2]. Due to the anonymity provided by cryptocurrency, it is not easy to verify the real identity of cryptocurrency users. As a result, concerns about the reliability and safety of financial transactions using cryptocurrency are being raised, and user authentication and KYC (Know Your Customer) processes are essential to solve this problem.
In particular, user authentication is becoming an increasingly vital element even in the metaverse environment that epitomizes Web3, operating through blockchain technology. In this case, there is a drawback of managing all users’ personal information on the server, which includes issues such as manipulating game item acquisition. Indeed, in May 2020, there was an incident where the personal information of 100 million active users of Roblox was compromised due to a hacking incident [3]. However, in the case of decentralized metaverse systems (e.g., Decentraland [4] and Sandbox [5]) that utilize blockchain, users log in using crypto wallet software (e.g., Metamask (version 11.2.0)) to map with avatars in the metaverse, and provide services through the ownership of NFTs present in their wallets. This is because crypto wallet software relies on verifying the possession of specific items rather than issuing NFTs based on the user’s identity, making it an inadequate method for identity authentication. Even if an NFT authenticated the user, the information could still be publicly visible on the blockchain, potentially leading to privacy issues.
User authentication is essential not only in metaverse environments but also in the majority of Web3 applications. In the field of finance, centralized exchanges already implement KYC procedures to verify users’ identities. Moreover, regulations like the Travel Rule [6] for anti-money laundering efforts require VASPs (Virtual Asset Service Providers) to collect and transmit information, such as the sender’s and receiver’s names, account numbers, addresses, and more. This mandatory reporting helps to mitigate the risks associated with money laundering and terrorist financing. Therefore, the FATF (Financial Action Task Force) emphasizes the importance of identity authentication to the extent that, through its first set of VASPs guidelines released in June 2019, it recommends that countries advocate for the enforcement of the Travel Rule. Similarly, decentralized exchanges also make various efforts to verify users’ identities. Among them, tbdex [7] is developing a decentralized protocol for exchanging fiat currency and cryptocurrencies. They are utilizing DID (Decentralized Identity) credentials [8] to authenticate users’ identities as part of their protocol development process.
As such, it is important for identity authentication to determine the identity of the user associated with the wallet address. Vitalik Buterin, the creator of Ethereum, proposed the concept of the SBT (Soul Bound Token) [9], which issues non-transferable NFTs to represent users’ identities, offering a proposal for identity verification and validation within decentralized societies. The world’s largest cryptocurrency exchange, Binance, has issued a form of identity token called the BABT (Binance Account Bound Token) [10], a form of SBTs. These tokens are issued to users who have completed Binance’s KYC process, enabling them to participate in various projects based on the BNB chain and receive rewards accordingly. On the other hand, in order to proceed with user identity management using the SBT, it is essential to verify that the actual wallet user wishes to be issued an SBT.
In the blockchain ecosystem, it is common to verify a user’s identity using DID and an SBT. However, DID verification needs to be conducted in the off-chain environment outside of the blockchain, and users have to submit credentials every time they want to prove their identity, which is a drawback. On the other hand, using an SBT, identity verification can occur on-chain within the blockchain environment based on the possession of an SBT. However, to issue an SBT, users need to provide their private information to the SBT issuer, raising concerns about privacy protection.
2. DID
DID is an identity information system used within a trust-distributed framework without centralized registration mechanisms. It is a technology based on distributed ledgers that enable individuals to autonomously manage proof of identity and control the scope and recipients of identity information submissions.
As shown in Figure 1, the part that represents user information is called a claim. These claims are collected, signed by the issuer, and sent to the holder in the form of credentials. The holder then stores the credentials and, when they want to reveal specific information, they add the information and their own signature and send it to the verifier, allowing the user’s information to be verified. For example, if an accommodation facility requires age verification, a national ID card presented to staff will reveal all personal information, such as address, social security number, and name, not just date of birth. However, by using DID, it is possible to prove something like “19 years or older” without revealing the exact age. DID technology has gained significant attention because it uses the principles of Self-Sovereign Identity (SSI), which allows users to store and manage authentication data while providing only the information necessary for identity verification [11]. In the medical field, methods for face-to-face consultations and personal health devices (PHDs) have been proposed for individual health management [12,13]. As these online services require user authentication, research using DID for personal information protection is being conducted to address issues related to sensitive medical information in electronic health records [12]. In the era of data economy, DID technology is widely used in many authentication services for reasons such as data sovereignty and personal information protection. However, there is a drawback in using DID in Web3 systems.
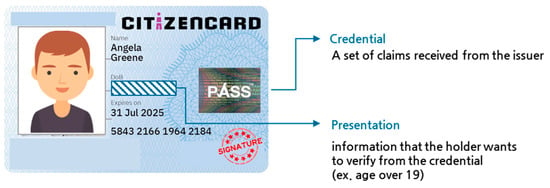
Figure 1. Components of DID.
3. NFT
NFT stands for “Non-Fungible Token”, representing a unique and irreplaceable token. Each NFT has a distinct identifier, which encapsulates its unique attributes and ownership information. This data is uploaded to the blockchain, making forgery or tampering difficult. NFTs grew based on the ERC-721 [14] standard in Ethereum [15]. Ethereum is a decentralized platform built on blockchain technology, best known for its smart contract capabilities [16]. Smart contracts are encoded segments of the EVM (Ethereum Virtual Machine) bytecode, which is a Turing-complete programming language.
Within the blockchain’s on-chain environment, there is an “ownerOf” function that indicates the owner’s address and a “tokenURI” function that contains a URL to a JSON file with various attributes, including the image of the NFT. The actual information of NFTs is stored off-chain, either on IPFS or a server. Utilizing this feature, verifying the ownership and data information of a specific NFT by using its ID (tokenID) on the blockchain is possible. As shown in Figure 2, NFT marketplaces provide a user interface that allows for easy viewing of NFT information based on the data uploaded to the blockchain. NFTs are primarily used to represent ownership of digital content, such as digital art, music, videos, and game items. Therefore, it provides the advantage of protecting the owner’s copyright from the work and transparently managing the rights of digital assets. Currently, blockchain-based metaverse services that support NFT transactions operate as shown in Figure 3.
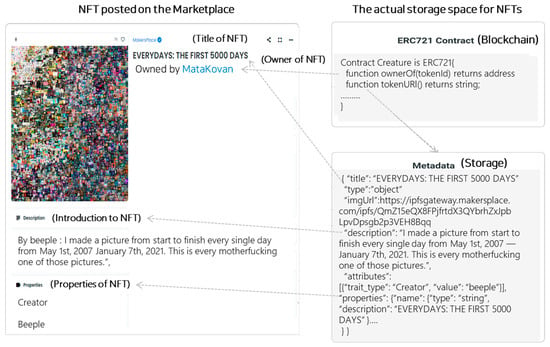
Figure 2. Composition of NFT.
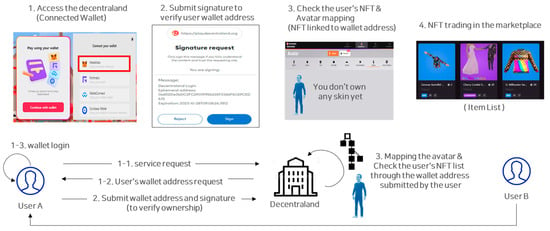
Figure 3. Login procedure in metaverse service using digital wallet.
First, the user must log in to a digital wallet program such as Metamask and go through the process of verifying the signature value to verify the user’s wallet address. After that, the wallet address and the corresponding avatar are mapped 1:1. In this way, the blockchain wallet address supported by the metaverse can be expanded into an ID concept that allows avatars to log in. In addition, in Decentraland, users who are 19 years of age or older need a costume of an ice breaker character issued as an NFT to participate in hold’em poker. User authentication is carried out whether or not a specific NFT is possessed. However, NFTs are unsuitable for creating user identities as NFTs because the owner can transfer ownership.
4. SBT
In May 2022, the co-founders of Ethereum, Vitalik Buterin, economist Glen Weyl, and lawyer Puja Ohlhaver, published a paper titled “Decentralized Societies: Finding the Soul of Web3.0”, which introduced the concept of an SBT. The paper proposed the development of a new type of cryptographic token called a “Soul Bound Token”. These tokens are designed to represent individual identities in a decentralized digital world. It introduced the concept that these tokens could serve as the foundation for creating a decentralized society (DeSoc) like the metaverse by making it impossible to transfer or trade them, unlike the traditional NFT. Utilizing an SBT, various aspects of an individual’s identity, such as employment, volunteer work, educational history, qualifications, medical records, criminal records, membership status, and affiliations, can be securely established by creating non-transferable NFT badge forms. These badges are then mapped to the user’s digital wallet address, ensuring the preservation of their identity. Currently, the SBT is creating various ERC standards (ERC-5192 [17], ERC-5727 [18], and ERC-6454 [19]). Generally, the minimum functions and interfaces with non-transferable characteristics are being defined.
Many services are attempting to implement identity verification systems using the SBT. In [20], a Dapp was developed to issue and verify COVID-19 vaccination certificates in the form of an SBT. In [21], a Dapp was developed to provide digital certificates in the education sector using an SBT. In [22], various cases of SBT use in the Web3 domain were listed, confirming its potential to replace the existing ownership-guaranteeing NFTs. Thus, the emergence of the SBT has led to significant advances in user identity verification systems within the blockchain.
5. ZKP
ZKP is a crucial cryptographic concept that provides a means for a prover to demonstrate the truth of a statement to a verifier without divulging any details about the statement, except for its validity. This cryptographic process entails a series of interactive exchanges between the prover and verifier. During these interactions, the prover seeks to authenticate the statement by sharing specific information while preserving the confidentiality and privacy of the statement itself. Through these exchanges, the verifier can securely confirm the veracity of the prover’s claim without compromising the underlying information. A typical ZKP framework comprises three distinct phases [23]:
-
Witness Phase: in the initial stage, the prover formulates a proof based on the statement and transmits it to the verifier.
-
Challenge Phase: subsequently, the verifier formulates a challenge based on the proof received and forwards it to the prover.
-
Response Phase: finally, the prover tackles the challenge and sends the response back to the verifier.
ZKP is a fundamental tool in modern cryptography, gaining significant attention due to its ability to address critical security and privacy challenges. It finds application in various domains, including digital identity [24], blind signatures [25], and attribute verification [26]. ZKP offers a potent cryptographic technique that enhances privacy, security, and efficiency in blockchain applications. There are numerous applications for implementing ZKP in the blockchain context, such as enabling anonymous transactions [27], facilitating secure voting systems [28,29], and improving supply chain management [30].
This entry is adapted from the peer-reviewed paper 10.3390/math11204387
This entry is offline, you can click here to edit this entry!
