Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Vehicular ad hoc networks (VANETs) have become an essential part of the intelligent transportation system because they provide secure communication among vehicles, enhance vehicle safety, and improve the driving experience.
- vehicular ad hoc network
- security
- certificateless aggregate signature
1. Introduction
Vehicular ad hoc network (VANET) is an advanced version of the mobile ad hoc network (MANET), which was developed to enhance the safety, efficiency, and convenience of transportation [1]. VANET is a set of applications designed to offer new services connected to the traffic management system, designed to help various users to be better informed and use the transportation network to be safer, more connected, and significantly more intelligent. VANET can be established for monitoring and controlling traffic using the concept of vehicle-to-everything (V2X) communication, which includes vehicle to infrastructure (V2I), vehicle to sensor (V2S), vehicle to pedestrian (V2P), and Vehicle to Vehicle (V2V) communication [2][3]. The general architecture of a VANET is shown in Figure 1, which includes vehicles with built-in 5G-enabled onboard units (OBUs), 5G-enabled roadside units (RSUs), and trusted authorities (TAs). TA is a service provider, ensuring the safety of the VANET network and generating public and private keys for OBUs and RSUs [4]. In VANETs, each vehicle communicates through an OBU and broadcasts traffic-related information such as positions, speed, current time, traffic and road conditions to a nearby vehicle and an RSU [5].
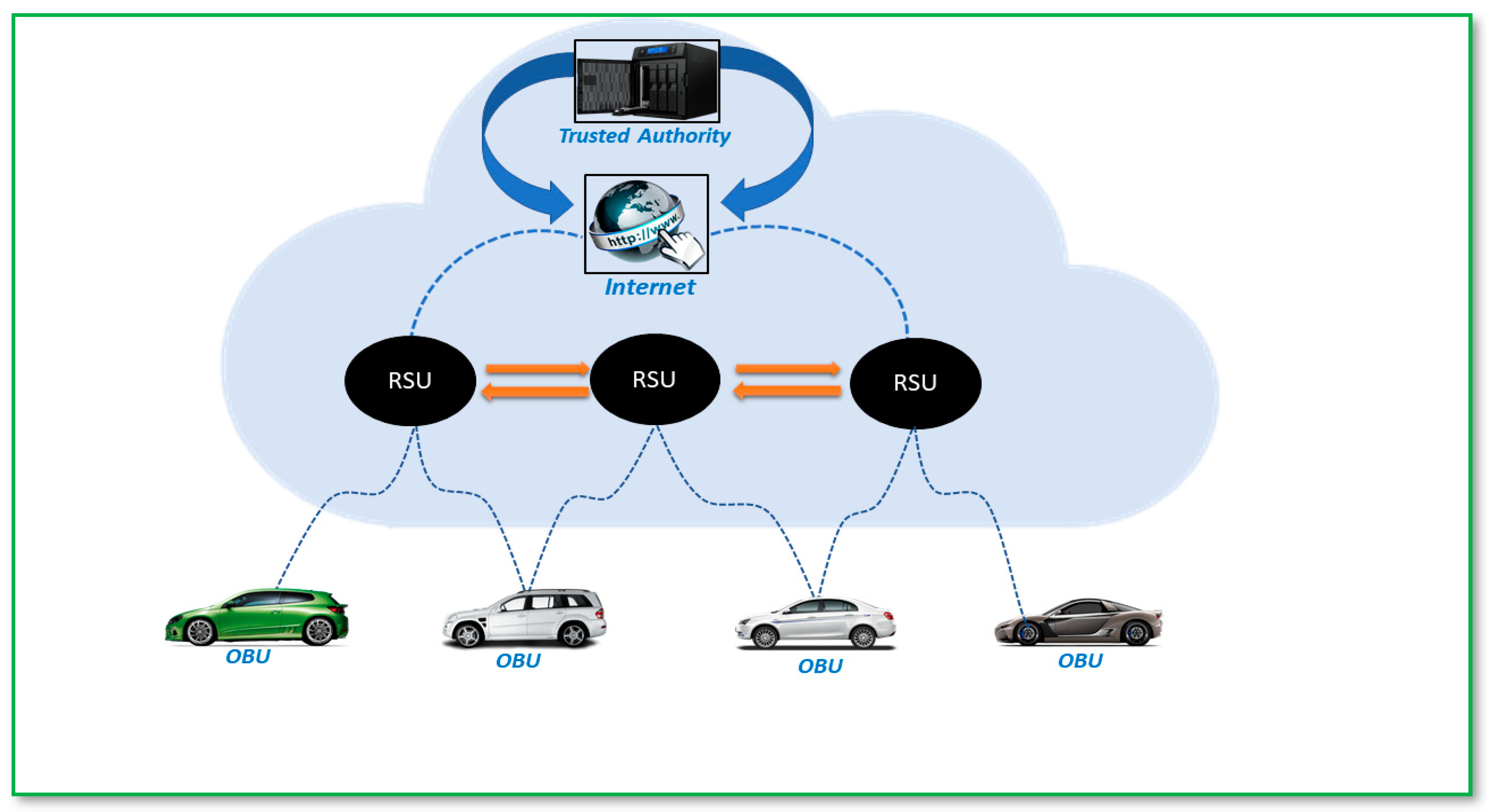
Figure 1. The general architecture of a VANET.
Despite all the attractive features offered by a VANET, there are significant challenges regarding its security and privacy when information is shared among vehicles through an open wireless channel. In a VANET system, an attacker can send bogus messages to the RSUs or other OBUs, which might cause disturbance on the roads, so it is necessary to verify the authenticity and integrity of the message [6]. Digital signature-based authentication techniques for VANETs have been built in various cryptographic frameworks, including public-key infrastructure (PKI), identity-based (ID), and certificateless cryptography.
In the standard implementation of public-key cryptography (PKC), each public key is required to produce a corresponding digital certificate [7]. Nevertheless, it not only involves certificate management but also contributes to an increase in the verification cost. To address the issues of certificate management, Shamir [8] came up with a novel technique in 1984 called ID-based public-key cryptography (ID-PKC). The public key consists of the user’s identity, such as phone number, e-mail address, etc., eliminating the need for a certificate. However, the private key is generated by the Key Generation Center (KGC), which might lead to a key escrow problem. To overcome the shortcomings of key management in traditional PKC and the key escrow problem in ID-PKC, Al-Riyami and Paterson [9] proposed Certificateless Public Key Cryptography (CL-PKC), which also requires the KGC to generate part of the user’s private key.
2. VANET Technology
A VANET is a communication technology that enables V2V and V2I communications via the Internet, which can be affected by several cyber-attacks. So, to avoid such circumstances, the best solution is authentication, in which the participating nodes in the VANET environment can authenticate each other before transferring data or information. To achieve authentication, the best approach is to use a digital signature, which allows a sender to sign data with his private key and deliver it to the recipient, who can then use the sender’s public key to verify the signature.
In a typical PKC-based signature, each user needs to produce a valid digital certificate that contains information about the identity of the certificate owner and the public key [7]. However, it not only requires certificate management but also contributes to an increase in the verification cost. To address certificate management issues, Shamir [8] proposed ID-PKC, in which the user’s identity is his public key, bypassing the need for certificates. However, the private keys are generated via the KGC, which might lead to a key escrow problem.
Al-Riyami and Paterson [9] proposed the idea of CL-PKC, in which the user’s private key is made up of a secret value and a partial private key. The user chooses his secret key, while the KGC generates the partial private key. Since the KGC cannot access the user’s complete private key without the user’s secret key, the user’s public key can be calculated from the secret value. Thus, the potential security issues associated with key escrow are eliminated. Secondly, the user’s public key can be calculated from the secret value, so a certificate is no longer needed. In other words, the CLS technique has the potential to address issues in both the classic signature method and the ID-based method. CLAS has the benefits of CLS and AS. In 2003, Boneh et al. [10] proposed the concept of CLAS, which can combine the signatures of n (n > 1) different messages signed by n other users into a single signature. The receiver only needs to check the aggregated signature instead of all the signatures, thereby reducing the computational cost of signature verification and the communication overhead of signature transmission to some extent.
The benefits of CLAS mentioned above have led to a lot of new research. Yum and Lee [11] proposed a CLAS scheme within the framework of the Random Oracle Model (ROM), but Hu et al. [12] discovered that Yum and Lee’s [11] scheme is vulnerable to public key replacement attacks. Deng et al. [13] designed and proved a secure practical CLAS scheme, although Kumar and Sharma [14] found that Deng et al. [13]’s scheme could guarantee unforgeability. A new certificateless signature system was presented by Horng et al. [15] for the use of V2I in a VANET’s communication. However, Ming and Shen [16] demonstrated that the scheme proposed by Horng et al. [15] was vulnerable to various attacks like replay attacks, modification attacks, impersonation attacks, and man-in-the-middle attacks and hence could not provide authentication and message integrity. Li et al. [17] addressed the limitation of Horng et al. [15]’s scheme and designed an improved CLAS scheme. However, the scheme has high computational and communicational costs since it uses bilinear pairing and point-to-point hash functions. Keitaro Hashimoto and Wakaha Ogata [18] came up with an open and small CLAS scheme in which the size of signatures stays the same, and any combination of signatures can be added together. However, the scheme is based on bilinear pairing, which necessitates higher computational and communicational costs. A highly effective AS scheme was developed by Malhi et al. [19] for privacy and authentication in VANETs. Cui et al. [20] developed an efficient CLAS scheme using ECC in vehicular sensor networks.
On the other hand, Kamil et al. [21] claimed that Cui et al.’s [20] scheme is unsafe against signature forgery attack. Du et al. [22] proposed an effective CLAS scheme without pairings for healthcare wireless sensor networks. However, the scheme is based on ECC, which results in a significant increase in both computational and communicational costs. To avoid the unpleasant certificate management problem of PKI and the key escrow problem of an ID-based framework, Gowri et al. [23] developed a CLAS-based authentication scheme for VANETS. However, Yang et al. [24] proved that Gowri et al.’s [23] scheme failed to achieve the desired security goals. Ye et al. [25] designed an improved certificateless authentication and AS scheme that may effectively counter coalition attacks. In the same year, Vallent et al. [26] developed a safe and efficient certificateless aggregation technique (ECLAS) for VANETs that might be used in a smart grid scenario. However, the [25][26] schemes are based on ECC to provide conditional privacy preservation, which leads to heavy computational costs and communication overhead.
A fully aggregated conditional privacy-preserving certificateless aggregate signature system (CPP-CLAS) was designed for VANETs by Yulei and Chen [27] in 2022. The proposed CPP-CLAS scheme uses ECC and general hash functions, which result in high computational costs and communication overhead. Another efficient pairing-free CLAS for secure VANET communication was introduced in the same year by Yibo et al. [28]. However, the [27][28] scheme was based on ECC, which has more computational costs and communication overhead.
In 2022, Cahyadi et al. [29] proposed a pairing-based CLAS authentication scheme to improve security, privacy, and efficiency in VANETs. However, it is found that the overall computation cost of the scheme is high due to massive pairing.
This entry is adapted from the peer-reviewed paper 10.3390/fi15080266
References
- Weber, J.S.; Neves, M.; Ferreto, T. VANET simulators: An updated review. J. Braz. Comput. Soc. 2021, 27, 8.
- Raut, C.M.; Devane, S.R. Intelligent transportation system for smartcity using VANET. In Proceedings of the 2017 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 6–8 April 2017; IEEE: Piscateville, NJ, USA; pp. 1602–1605.
- Ullah, I.; Khan, M.A.; Alsharif, M.H.; Nordin, R. An anonymous certificateless signcryption scheme for secure and efficient deployment of Internet of vehicles. Sustainability 2021, 13, 10891.
- Umar, M.; Islam, S.H.; Mahmood, K.; Ahmed, S.; Ghaffar, Z.; Saleem, M.A. Provable secure identity-based anonymous and privacy-preserving inter-vehicular authentication protocol for VANETS using PUF. IEEE Trans. Veh. Technol. 2021, 70, 12158–12167.
- Ullah, I.; Khan, M.A.; Khan, F.; Jan, M.A.; Srinivasan, R.; Mastorakis, S.; Hussain, S.; Khattak, H. An Efficient and Secure Multi-message and Multi-receiver Signcryption Scheme for Edge Enabled Internet of Vehicles. IEEE Internet Things J. 2021.
- Qu, F.; Wu, Z.; Wang, F.Y.; Cho, W. A security and privacy review of VANETs. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2985–2996.
- Khan, M.A.; Shah, H.; Rehman, S.U.; Kumar, N.; Ghazali, R.; Shehzad, D.; Ullah, I. Securing internet of drones with identity-based proxy signcryption. IEEE Access 2021, 9, 89133–89142.
- Shamir, A. Identity-based cryptosystems and signature schemes. In Advances in Cryptology: Proceedings of CRYPTO 84 4; Springer: Berlin/Heidelberg, Germany, 1985; pp. 47–53.
- Al-Riyami, S.S.; Paterson, K.G. Certificateless public key cryptography. In Asiacrypt; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2894, pp. 452–473.
- Boneh, D.; Gentry, C.; Lynn, B.; Shacham, H. Aggregate and verifiably encrypted signatures from bilinear maps. In Advances in Cryptology—EUROCRYPT 2003, Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Warsaw, Poland, 4–8 May 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 416–432.
- Yum, D.H.; Lee, P.J. Generic construction of certificateless signature. In Proceedings of the Information Security and Privacy: 9th Australasian Conference, ACISP 2004, Sydney, Australia, 13–15 July 2004; Springer: Berlin/Heidelberg, Germany; pp. 200–211.
- Hu, B.C.; Wong, D.S.; Zhang, Z.; Deng, X. Key replacement attack against a generic construction of certificateless signature. In ACISP; Springer: Berlin/Heidelberg, Germany, 2006; Volume 6, pp. 235–246.
- Deng, J.; Xu, C.; Wu, H.; Dong, L. A new certificateless signature with enhanced security and aggregation version. Concurr. Comput. Pract. Exp. 2016, 28, 1124–1133.
- Kumar, P.; Sharma, V. A comment on efficient certificateless aggregate signature scheme. In Proceedings of the 2017 International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, India, 5–6 May 2017; IEEE: Piscateville, NJ, USA; pp. 515–519.
- Horng, S.J.; Tzeng, S.F.; Huang, P.H.; Wang, X.; Li, T.; Khan, M.K. An efficient certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks. Inf. Sci. 2015, 317, 48–66.
- Ming, Y.; Shen, X. PCPA: A practical certificateless conditional privacy preserving authentication scheme for vehicular ad hoc networks. Sensors 2018, 18, 1573.
- Li, J.; Yuan, H.; Zhang, Y. Cryptanalysis and improvement of certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks. Cryptol. Eprint Arch. 2016. Available online: https://eprint.iacr.org/2016/692.pdf (accessed on 1 July 2023).
- Hashimoto, K.; Ogata, W. Unrestricted and compact certificateless aggregate signature scheme. Inf. Sci. 2019, 487, 97–114.
- Malhi, A.K.; Batra, S.; Pannu, H.S. An efficient privacy preserving authentication scheme for vehicular communications. Wirel. Pers. Commun. 2019, 106, 487–503.
- Cui, J.; Zhang, J.; Zhong, H.; Shi, R.; Xu, Y. An efficient certificateless aggregate signature without pairings for vehicular ad hoc networks. Inf. Sci. 2018, 451, 1–15.
- Kamil, I.A.; Ogundoyin, S.O. An improved certificateless aggregate signature scheme without bilinear pairings for vehicular ad hoc networks. J. Inf. Secur. Appl. 2019, 44, 184–200.
- Du, H.; Wen, Q.; Zhang, S. An efficient certificateless aggregate signature scheme without pairings for healthcare wireless sensor network. IEEE Access 2019, 7, 42683–42693.
- Thumbur, G.; Rao, G.S.; Reddy, P.V.; Gayathri, N.B.; Reddy, D.K.; Padmavathamma, M. Efficient and secure certificateless aggregate signature-based authentication scheme for vehicular ad hoc networks. IEEE Internet Things J. 2020, 8, 1908–1920.
- Yang, X.; Chen, A.; Wang, Z.; Du, X.; Wang, C. Cryptanalysis of an Efficient and Secure Certificateless Aggregate Signature-Based Authentication Scheme for Vehicular Ad Hoc Networks. Secur. Commun. Netw. 2022, 2022, 4472945.
- Ye, X.; Xu, G.; Cheng, X.; Li, Y.; Qin, Z. Certificateless-based anonymous authentication and aggregate signature scheme for vehicular ad hoc networks. Wirel. Commun. Mob. Comput. 2021, 2021, 6677137.
- Vallent, T.F.; Hanyurwimfura, D.; Mikeka, C. Efficient certificate-less aggregate signature scheme with conditional privacy-preservation for vehicular ad hoc networks enhanced smart grid system. Sensors 2021, 21, 2900.
- Chen, Y.; Chen, J. Cpp-clas: Efficient and conditional privacy-preserving certificateless aggregate signature scheme for vanets. IEEE Internet Things J. 2021, 9, 10354–10365.
- Han, Y.; Song, W.; Zhou, Z.; Wang, H.; Yuan, B. eCLAS: An efficient pairing-free certificateless aggregate signature for secure VANET communication. IEEE Syst. J. 2021, 16, 1637–1648.
- Cahyadi, E.F.; Su, T.W.; Yang, C.C.; Hwang, M.S. A certificateless aggregate signature scheme for security and privacy protection in VANET. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221080658.
This entry is offline, you can click here to edit this entry!
