Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Subjects:
Computer Science, Cybernetics
The Internet of Things (IoT) is expanding rapidly and is becoming increasingly crucial to how we live our daily lives. Internet protocol addresses can be used by IoT nodes for connecting to the Internet. Intrusion detection systems (IDSs) guarantee both the security posture and defense against intrusions of IoT devices.
- intrusion detection system (IDS)
- Internet of Things (IoT)
- network security
- cyber security
1. Introduction
The Internet of Things (IoT) is expanding rapidly and is becoming increasingly crucial to how we live our daily lives. Internet protocol addresses can be used by IoT nodes for connecting to the Internet [1,2]. These self-configured intelligent nodes are creating advances in several innovative applications, including automation of processes, home control, smart transportation, information data analysis, etc. Based on the analysts’ reports, it was evident that there will eventually be a society with more interconnected devices than people on the earth. According to the expected population of 8.3 billion, the international data corporation (IDC) anticipated that there would be 42 billion connected IoT gadgets generating 80 Zetta Bytes (ZB) of data in 2025 [3,4]. The extensive use of the Internet makes network security an unavoidable concern. Due to the Internet of Things’ potential applications in various human activities, various IoT-related studies have recently attracted interest in the academic community and industry [5]. With the decline in sensor prices, the rise of remote storage services, and the popularity of big data, the IoT is seen as a viable solution to raise people’s quality of life.
Nevertheless, incorporating physical items with the Internet exposes most of our regular activities to security risks [6,7]. When different types of devices are connected to a network, it is clear that the simple availability of these resources raises IoT, which in turn helps new applications grow in popularity. Security issues [8] arise when heterogeneous nodes in IoT systems are coupled to a sophisticated network architecture. The main difficulty is maintaining security in IoT nodes with limited resources. Furthermore, various attacks could be launched against these IoT nodes [9,10]. IDSs are a simple yet effective security tools for guaranteeing adequate network security in any IoT-integrated environment. The typical structure of an IDS model is shown in Figure 1.
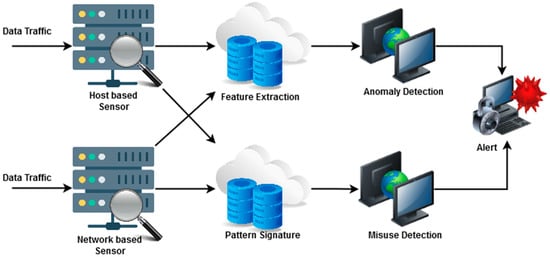
Figure 1. A visual structure of a typical intrusion detection system (IDS) model.
Typically, the process of identifying actions carried out by intruders over computer systems is known as intrusion detection. These behaviors, also called assaults, are meant to gain illicit access to a computing system [11]. An internal or external intrusion may occur. Users who have some level of authorized access within the network and want to increase their access rights to abuse prohibited privileges are known as internal invaders [12]. Users who are not part of the intended network and attempt to obtain illicit access to system data are known as external intruders. Numerous studies [13] are being conducted to determine the ideal variables and outcomes for identifying signs of intrusion in IoT environments. Concerns about dangers to data security are escalating as IoT expands [14]. Due to multiple components, such as the IoT devices’ weaknesses, these vulnerabilities can be exploited by malware, denial-of-service intrusion attempts, and other threats. It is vital to take more substantial precautions to prevent these occurrences, enabling system developers and IoT device manufacturers to enhance their security mitigation techniques. All potential risks and vulnerabilities that are created explicitly for IoT architectures must be found.
Current solutions for IoT systems [15] need to be revised due to the unique characteristics of IoT that have an impact on the development of intrusion detection systems (IDSs), notwithstanding the maturity of IDS technology for traditional networks. More studies concentrate on the understanding of risks that are deemed necessary in this context in order to limit potential threats, and obstacles in the security of IoT systems, such as privacy and security, are being encountered and have to be handled and prevented.
2. A Novel Range-Optimized Attention Convolutional Scattered Technique for Intrusion Detection in IoT Networks
This section looks at some recent research findings pertinent to IoT network security and intrusion detection approaches. Based on the performance outcomes, it also examines the benefits and drawbacks of the current systems.
Da Costa et al. [18] presented a comprehensive review examining several machine learning techniques for detecting intrusions from IoT networks. This review’s focus is on various machine learning and evolutionary computation-based processes. This article aims to enlighten readers on the state of the field’s literature and serve as a new resource for academics looking into IoT security challenges. The work includes several innovative approaches to intrusion detection and network security in digital environments. Although these methods aim to increase intrusion detection recognition rates, it is believed that the false positive rate continues to pose an issue that must be dealt with across all research studies.
Islam et al. [19] intended to spot the different types of IoT threats by using a set of machine learning and deep learning algorithms, including support vector machine (SVM), decision tree (DT), random forest (RF), long short-term memory (LSTM), and deep belief network (DBN). Data analysis-based strategies are used in this study since they are quicker to implement than alternative methods and more effective for addressing events that are not yet known to have resulted from known attacks. The framework’s primary goal is to create an intelligent, safe, and reliable IoT system that can identify its vulnerabilities, act as a safeguarding barrier for severe cyberattacks, and recover itself. This article suggests a learning-based methodology that can detect and guarantee the system’s security under unusual circumstances. Nimbalkar et al. [20] investigated the different feature selection techniques for developing an effective intrusion detection system (IDS) to protect IoT networks. Using an information gain (IG) and gain ratio (GR) selection models reduces the total count of features to 50%, which is provided to the JRip classifier for accurate detection. Moreover, the authors aim to generate a compact dataset after completing the data preprocessing operations. In addition, the accuracy of the suggested classifier is validated with and without IG and GR feature selection techniques. This study’s results indicate that the classifier’s accuracy is significantly increased with these feature reduction techniques.
Hindy et al. [21] conducted a detailed case study to investigate the different machine learning techniques used for intrusion detection and classification. In this work, the MQTT-IoT-IDS 2020 dataset has been used as the primary source for processing, where the uni-directional and bi-directional features are considered for an efficient classification. Alsaedi et al. [22] utilized the data-driven approaches for detecting intrusions from IoT and IIoT networks using the telemetry ToN-IoT dataset. The authors aim to develop a new dataset for protecting large-scale networks from recent cyber threats. Moreover, it investigated some of the famous and emerging datasets used in this field for ensuring security, which are listed in Table 1.
Table 1. List of online available datasets used for IoT security.
| No. | Datasets | Different Attack Scenarios | Heterogeneity of IoT Data Sources | Number of Instances | Number of Features |
|---|---|---|---|---|---|
| 1 | KDD’99 | No | No | 494,021 | 41 |
| 2 | NSL-KDD | No | No | 125,973 | 42 |
| 3 | UNSW-NB 15 | Yes | No | 2,540,000 | 49 |
| 4 | LWSNDR | No | No | 48,000 | 29 |
| 5 | ISCX | Yes | No | 15,570 | 45 |
| 6 | AWID | Yes | No | 458,691 | 155 |
| 7 | UNSW-IoT trace | No | No | 1,000,000 | 8 |
| 8 | BoT-IoT | Yes | No | 56,800 | 116 |
| 9 | T-IIoT | Yes | Yes | 50,000 | 52 |
Zhou et al. [23] deployed a graph neural network (GNN)-based intrusion detection methodology for IoT systems. Here, the hierarchical adversarial attack (HAA) generation algorithm has been developed to detect unknown attacks more accurately. In addition, the random walk with restart (RWR) technique is also deployed to identify the vulnerable nodes from the network by computing the priority level. This study uses the open-source UNSW-SOSR 2019 dataset to investigate the suggested model by comparing it with some of the baseline techniques. However, this mechanism consumes more time to predict the solution, which could be the major drawback of this work. Wahab et al. [24] introduced an online deep learning approach for spotting intrusion from IoT networks. In this study, the data drift detection technique has been used to identify the intrusion data streams by analyzing the variance of features. The suggested method ensures sustainable performance with effective intrusion detection solutions. The advantage of this mechanism was that it supports both drift detection and adoption for intrusion identification and recognition. Yet, the suggested deep neural network technique has high computational and time complexity.
Kan et al. [25] utilized an adaptive particle swarm optimization (PSO) technique incorporated with CNN algorithm for identifying network intrusions from IoT systems. Also, it focuses on the development of a multi-type of intrusion detection model with improved prediction probability and reliability. Moreover, the highest probability prediction is carried out using cross-entropy loss function. The suggested APSO-CNN intrusion detection results are estimated according to the training loss and accuracy measures.
Abdalgawad et al. [26] implemented a bi-directional generative adversarial network (Bi-GAN) model for spotting cyberattacks from the IoT 23 dataset. In this study, the adversarial autoencoder has been used along with the Bi-GAN model for spotting a variety of attacks from the network. In addition, a 10-fold cross-validation strategy is used to test and validate the performance and outcomes of the suggested mechanism. According to the study results, it is noted that the generative deep learning techniques provide high accuracy with better detection performance.
Kumar et al. [27] developed a distributed intrusion detection system for spotting DDoS attacks from IoT networks. Typically, a security mechanism must handle large amounts of data generated by IoT devices in a distributed way and apply the proper statistical methods in a viable architecture. Shukla et al. [28] applied an artificial intelligence (AI)-based intrusion detection methodology for IoT security. The work examined the usage of several machine learning methods inside IoT. It also highlighted how crucial it is to select the right data for a model [29]. There is also a discussion of the naive Bayesian network intrusion detection technique. Most notably, it looked at how crucial it is to prepare IoT system events for classification, and it examined the consequences of utilizing a hidden naive Bayes multi-classifier, discovering that it outperformed the standard model. According to the AI paradigm [30], every single node in the IoT network has an internal AI process that is only in charge of that node. This method can be scaled because the total number of sessions grows according to the number of analyzed nodes. In [31], the authors introduce a hierarchical fog computing-based architecture for Industry 5.0’s smart energy-supplying systems. It efficiently handles data-intensive analysis from IIoT devices, outperforming traditional cloud computing, and ensures data security through attribute-based encryption (ABE).
Albasheer et al. [32] looked at network intrusion detection systems (NIDS) and the problems they have, such as a lot of false positives, different ways to deal with alert correlation, and insights into network security. Researchers in [33] introduced an AI-driven cross-platform VPN system for detecting and categorizing attack risks. They demonstrated the efficiency of an extended gradient boosting (XgBoost)-based AI algorithm in preventing cyberattacks and integrating with a Cassandra big data system. In [34], researchers proposed an on-the-move intrusion detection system (OMIDS) for electric vehicle networks, showing high classification accuracy for various threats. In [35], the authors explored the potential of supervised machine learning for IDS, achieving high classification performance. In [36], the authors introduced “IntruDTree”, a machine learning-based intrusion detection system designed for the IoT.
According to Table 2, it shows that some strategies can lower the false positive rate, but in doing so, they also require more training and labeling. However, some methods reverse the process, reducing the false positive rate at the expense of high computational costs for both training and testing. Such a problem is highly pertinent to intrusion detection because real-time detection is an important consideration.
Table 2. A table summarizing the state-of-the-art studies from the literature review, including the approach, key contributions, and limitations of each study.
| Reference | Approach | Key Contributions | Limitations |
|---|---|---|---|
| Da Costa et al. [18] | Review of machine learning techniques for IoT intrusion detection | Comprehensive review of IoT intrusion detection techniques | High false positive rate across research studies |
| Islam et al. [19] | Use of machine learning and deep learning algorithms for IoT threat detection | Focus on quick implementation and effective handling of unknown events | Limited discussion on computational efficiency |
| Nimbalkar et al. [20] | Feature selection techniques for enhancing IDS in IoT networks | Effective reduction of feature count for accurate detection | Limited discussion on scalability for large datasets |
| Hindy et al. [21] | Case study on machine learning techniques for intrusion detection | Focus on MQTT-IoT-IDS 2020 dataset and bi-directional features | No explicit mention of limitations in the provided text |
| Alsaedi et al. [22] | Data-driven approaches for IoT and IIoT intrusion detection | Development of new dataset for IoT intrusion detection | Limited information on performance evaluation |
| Zhou et al. [23] | GNN-based intrusion detection using HAA and RWR techniques | Innovative use of GNN for unknown attack detection | Increased time consumption for predictions |
| Wahab et al. [24] | Online deep learning approach with data drift detection | Detection of intrusion data streams with drift detection | High computational and time complexity |
| Kan et al. [25] | Adaptive PSO-CNN model for multi-type intrusion detection | Incorporation of PSO with CNN for improved reliability | Limited details on how cross-entropy loss is implemented |
| Abdalgawad et al. [26] | Bi-GAN model for detecting cyberattacks in IoT networks | Effective use of Bi-GAN and generative deep learning | No specific limitations provided in the text |
| Kumar et al. [27] | Distributed intrusion detection for DDoS attacks in IoT | Development of distributed intrusion detection system | Limited details on the specific methodology used |
| Shukla et al. [28] | AI-based intrusion detection in IoT with focus on data selection | Examination of various machine learning methods in IoT | No explicit discussion of limitations in the provided text |
This entry is adapted from the peer-reviewed paper 10.3390/s23198044
This entry is offline, you can click here to edit this entry!
