Centralized networks can host ubiquitous interconnected objects using Internet of Things (IoT) platforms. It is also possible to implement decentralized peer-to-peer solutions using blockchain technology, including smart homes and connected cars. However, both models have limitations regarding their ability to provide privacy and security due to limited resources, centralization management, and scalability, cost, and response time. The diversity of IoT network nodes is expected to result in different throughputs and rates. Centralized networks control and improve the performance of a large number of IoT devices. However, centralizing systems suffer from a number of disadvantages. A third party often has to manipulate the data collected by central cloud storage, which could lead to information leaks that could compromise the user’s privacy.
1. IoT Authentication and Authorization
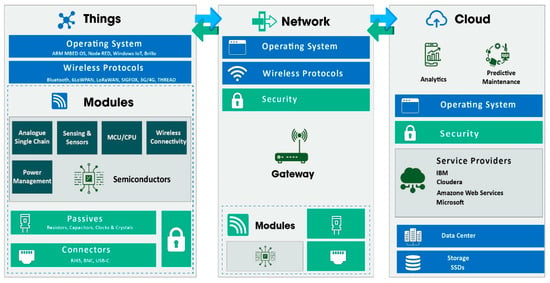
The term “Internet of Things” refers to the connectivity of “smart” devices, including digital and mechanical machinery, goods, and people. These “smart” gadgets are able to exchange data via a network without the involvement of a human being. The typical Internet of Things system is depicted in Figure 1. Applications of the Internet of Things on a larger scale include, among other things, smart cities, smart homes, and smart healthcare systems. The typical IoT system is composed of: (i) IoT sensors and devices such as smart vehicles, smart electronics equipment, and smart home appliances. (ii) Networks, communication protocols, and 4G and 5G technologies. (iii) Communication and processing protocols (iv) Storage resources such as the cloud.
Figure 1. The IoT architecture and its distribution.
To access IoT applications, devices must be authenticated and authorized. In terms of network security, these measures are crucial [
9]. A relevant authentication procedure is needed for establishing secure communication between IoT devices. An IoT network typically uses public key infrastructure to control the authentication and authorization of devices and nodes [
10]. The high volume of requests greatly exacerbates the authority center’s workload, resulting in considerable delays [
11]. Several new mechanisms have been suggested to improve this situation. Ref. [
12] proposes a method for authentication and privacy using IP-Sec with TLS. Nonetheless, due to its high computing requirements, such a mechanism is inefficient for connected devices with limited computational resources.
IoT researchers [
13] found a way to provide an access management system based on blockchain technology. A Proof of Concept (PoC) algorithm is a consensus-based method implemented instead of a centralized management server in the suggested approach. By utilizing Ethereum blockchain technology to verify the entity’s identity [
14], it presents IoT controlling access in a secure manner that addresses issues of delegating access rights. In a previous paper [
15], blockchain structures (BCS) are proposed as IoT verification methods using layers, intersections, and self-organization. Security performance is assessed based on the efficiency of storage, responsiveness, and validity. Based on the blockchain, ref. [
16] proposes an IoT security and authentication method. By using this method, single points of failure can be avoided.
2. The Blockchain and IoT Environment
In 2008, a well-known crypto currency called Bitcoin developed and utilized blockchain technology for the first time [
17]. It is a decentralized ledger technology with a peer-to-peer networking foundation.
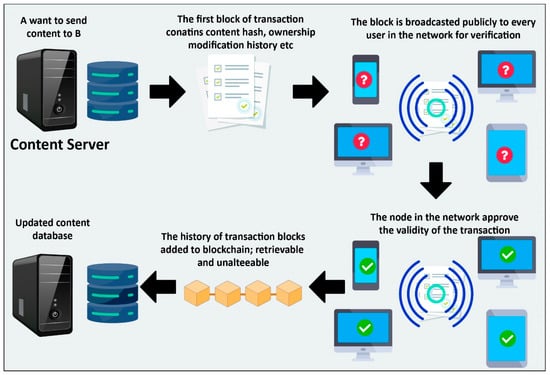
Figure 2 depicts the workings of a typical blockchain paradigm. In this approach, each node in the blockchain network updates its copy of the ledger. The Internet of Things (IoT) devices can be made more secure, private, and reliable by using blockchain technology for encrypted communication.
Figure 2. The working mechanism of a typical blockchain.
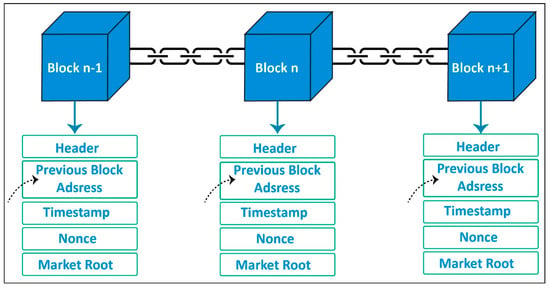
Conventional centralized systems rely on a single point of control and are hence open to attacks. On the other hand, blockchain is decentralized, meaning no organization has complete authority over the network. Lowering the single points of failure and potential attack routes can improve the security of IoT connectivity. Blockchain also offers an unchangeable, tamper-proof ledger in which data can be safely recorded. As seen in Figure 3, a chain of blocks that is impossible to tamper with without being noticed is created by connecting each data block to the one before it using cryptographic hashes. This guarantees the accuracy of the data transmitted between IoT devices.
Figure 3. Data connectivity via chain of blocks inside blockchain.
Blockchain-based identity and authentication management allow for secure device authentication. Each IoT device can have a distinct digital identity that is kept on the blockchain and can be used to confirm the validity of the device and its data. The conditions of the agreement are explicitly contained in the smart contract’s code, which is a self-executing contract. Smart contracts can be applied to the Internet of Things to automate processes based on predetermined criteria. To ensure secure and predictable behavior, a smart contract can specify, for instance, that a particular action carried out by an IoT device should only be conducted if certain criteria are met. Thanks to the secure data sharing, multiple parties can share data in a regulated, secure manner. The risk of data breaches and illegal access is decreased since IoT devices can share data directly with authorized parties without the use of middlemen.
3. Secure IoT Frameworks Based on Blockchain
A new method of addressing privacy and security challenges associated with the IoT has been developed using blockchain; [
18] presents several strategies for preserving privacy within blockchain-based IoT systems. Several strategies to implement differential privacy include encryption, anonymization, private contracts, and mixing.
Study [
19] looks at blockchain and IoT applications and discusses how the technology can address security concerns.
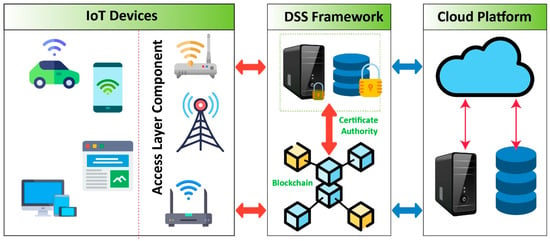
Figure 4 shows the secure IoT framework with blockchain implementation, as the IoT is challenged by insufficient standardization, the limited capacity of cloud servers, low manipulation potential, and costs [
4]. As a way to facilitate IoT device privacy and security, lightweight scalable blockchain is described in [
20]. By implementing a blockchain with robust computing performance, decentralization and privacy protection are achieved due to the implementation of an overlay network. IoT networks and blockchain should be integrated to address their challenges [
21]. A redesigned consensus mechanism called Proof of Block and Trade is proposed. It aims to speed up the validation of trades and blocks by reducing computation time. An IoT device’s memory requirements are reduced by developing a distributed ledger. The authors of [
3] propose a blockchain-based model that uses lightweight scalable blockchain (LSB) to modify the consensus algorithm, reducing the deployment complexity of Proof of Work. Ref. [
22] explains how blockchain-based frameworks can be utilized to address problems such as confidentiality, trust, resilience, and autonomy. Blockchain implementation can be assessed using an IoT and edge computing decision structure with the framework. Ref. [
23] proposes a context-sensitive data allocation mechanism for blockchain-enabled IoT systems. For each data request, the authors compute the rating of allocation (RoA) score using a fuzzy logic mechanism. This paper investigates the efficiency of blockchain systems and fog architectures.
Figure 4. Secure IoT framework with blockchain implementation.
4. Blockchain Security Model for 5G-Enabled IoT Networks
In [
24], a blockchain-based solution for automated certificate revocation in 5G IoT networks is proposed. The system utilizes blockchain technology to ensure the security and privacy of IoT devices and data by providing a reliable and efficient certificate revocation mechanism. The proposed system uses smart contracts and consensus mechanisms to automate the certificate revocation process and maintain the system’s integrity.
A blockchain-based remote data integrity checking scheme (RDIC) for IoT devices in 5G networks is proposed in [
25]. The proposed scheme utilizes a blockchain to maintain the integrity of the data collected by IoT devices in the network. The system employs a challenge–response protocol and smart contracts to automate the data checking process and ensure the authenticity of the data. The proposed scheme addresses the security and privacy issues associated with data collection and sharing in IoT networks. Another paper proposes a blockchain-based data dissemination scheme for 5G-enabled softwarized UAV networks [
26]. The proposed scheme utilizes blockchain technology to provide secure and reliable data dissemination between UAVs and other entities in the network. The system employs a consensus mechanism and smart contracts to automate the data dissemination process and maintain the integrity of the system. The proposed scheme is designed to address the security and privacy issues associated with data dissemination in UAV networks.
5. Permissioned Blockchain in IoT
It is possible to achieve the benefits of a trust-free environment, which is also flexible, scalable, and confidential, without the need for centralized authority through the use of Hyperledger Fabric (HLF) [
27]. Hyperledger Fabric is an open-source blockchain platform developed by the Linux Foundation. It provides a modular and highly flexible framework for building permissioned blockchain networks, making it suitable for various enterprise applications. Hyperledger Fabric offers features like confidentiality, scalability, and flexibility in terms of consensus algorithms and smart contract languages. It is designed to support consortium networks where multiple organizations collaborate while preserving data privacy and security. In the HLF framework, consensus algorithms are open architectures. This allows you to modify the configuration and increase performance. An authorization framework based on the HLF framework is proposed in [
28] for an IoT network. There is some consideration of IoT-driven data collection and its standard features in [
29]. In order to address the management issues of big data generated by the IoT, this research proposes the management of big data on a blockchain through a permissioned, decentralized trust management protocol (BlockBDM).
6. Level-Based IoT Blockchain
According to [
17], a platform is proposed to make smart city communication more secure using blockchain. An IoT and blockchain especially suited for medical use have been proposed in paper [
30]. With decentralized multi-layer IoT networks, the solution solves the computation and complexity challenges associated with blockchain implementation. To implement the smart city, a blockchain and SDN-based hybrid network architecture is proposed in [
31]. A core network and edge network are proposed as parts of the proposed architecture to improve efficiencies. Both the strengths of centralized and distributed networks are inherited by this model. In [
32], the authors present an enhanced privacy and data security framework based on blockchain technologies. Multi-layer management aims to improve response times and utilization. In this framework, mobile agents can perform a hash function, implement encryption, implement aggregation, and decrypt data. As a result, mobile agents are transferred from blockchains to IoTs to complete their tasks. An IoT blockchain framework based on a hierarchical two-tier system is proposed in [
33] for the IoT car rental system that uses blockchain technology to enhance and measure its scalability. In [
34], a cloud-based multi-layer architecture that utilizes blockchain is proposed to facilitate the monitoring and management of the Internet of Underwater Things (IoUT). Using selected residual energy super nodes, clusters and groups of sensor nodes are formed. The Bloom filter is used to track super nodes and nodes. In order to communicate, gateways deploy a standard secret key, which is distinct from the super node’s secret key. As a result, the routed data are stored in the blockchain ledger.
This entry is adapted from the peer-reviewed paper 10.3390/electronics12204314