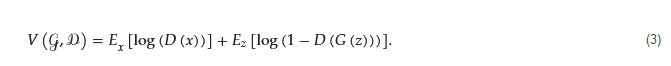The ransomware attacks threaten not only personal files but also critical infrastructure like smart grids, necessitating early detection before encryption occurs. Current methods, reliant on pre-encryption data, suffer from insufficient and rapidly outdated attack patterns, despite efforts to focus on select features. Such an approach assumes that the same features remain unchanged. This approach proves ineffective due to the polymorphic and metamorphic characteristics of ransomware, which generate unique attack patterns for each new target, particularly in the pre-encryption phase where evasiveness is prioritized.
1. Introduction
Like other cyberattacks, ransomware attacks target a variety of systems and networks, including Personal Computers (PCs), mobile devices, Wireless Sensor Networks (WSN), Vehicular Ad Hoc Networks (VANETs), and the Internet of Things (IoT) [
1,
2]. Several studies have been conducted to detect ransomware attacks [
3,
4,
5]. To detect crypto-ransomware early, the data collected during the pre-encryption phase of the crypto-ransomware lifecycle, before the encryption takes place is used [
6,
7]. The collected data are then used to train different machine learning algorithms to classify the programs into benign and ransomware [
8]. However, the lack of sufficient data during the early phases of the attack adversely affects the accuracy of the model due to insufficient attack patterns [
9].
Currently, ransomware attacks have targeted many Cyber Physical Systems (CPS), causing severe disruption of critical services and infrastructure [
10,
11]. In 2021, the US faced two significant CPS ransomware attacks on its critical infrastructure. The Colonial Pipeline, a major fuel supplier for the East Coast, experienced a cyberattack in May, leading to fuel shortages and panic buying in various states [
12]. Then, in June, JBS, the world’s top meat supplier, was attacked, prompting plant shutdowns in the US and Australia. This attack utilized the Ryuk ransomware, demanding millions in ransom. Colonial Pipeline and JBS suffered significant financial losses, paying ransoms of $4.4 million and $11 million, respectively [
12]. In October 2021, the Czech Republic’s major power company, CEZ, was attacked with RansomExx ransomware after an intrusion via Winnti malware, causing power outages. Earlier, in December 2020, a natural gas facility was targeted using the TrickBot malware variant, prompting a response from the Cybersecurity and Infrastructure Security Agency (CISA) [
10]. These attacks underline the severe consequences of ransomware on critical infrastructure, emphasizing the need for enhanced cybersecurity, and regular system updates, underscoring the significance of addressing vulnerabilities in CPS.
The insufficient attack patterns are the main obstacle that degrades the early detection accuracy of ransomware attacks. Although several studies tried to overcome data insufficiency by focusing on how to select a subset of features that represent the immature ransomware attack patterns. Such approach assumes that the significance of those features remains unchanged. This does not hold as the polymorphic and metamorphic nature of the attack makes the ransomware generate different patterns every time it receives a new target. This is especially true during the pre-encryption stage where the goal of ransomware is to be evasive. Hence, the features become quickly obsolete. GAN has the potential to overcome the data insufficiency problem by augmenting the real attack patterns with artificial, yet realistic data. However, the Minimax loss function used by GANS’s generator and discriminator is unable to estimate the distance between the probability distribution of real and artificial instances in the pre-encryption data of ransomware attacks.
2. Generative Adversarial Network for Ransomware Behavior Prediction
The major obstacle in the early detection of ransomware involves obtaining adequate data in the pre-encryption stage when the attack is still being set up and has not yet been executed [
1,
2]. Addressing this data shortage is crucial, as a sufficient dataset is needed for precise early detection. Data augmentation is often used in machine learning solutions and presents a promising way to tackle this scarcity of data, a problem commonly faced by malware and ransomware early detection systems. To our understanding, no existing studies specifically address data augmentation in the pre-encryption stage of ransomware attacks [
10]. Another challenge stems from the ever-changing nature of ransomware, which complicates the relevancy of features used for detection models [
14]. For example, an attack pattern seen in one ransomware variant at a specific time might be more relevant than the same pattern displayed by a different variant at another time. This indicates that the importance of features can vary depending on the ransomware variant and the timing of the attack. Despite this, current early detection methods often operate on the assumption that the importance of these features remains constant, leading to “behavioral drift.” This drift mostly results in detection systems becoming quickly outdated and less accurate over time.
The Generative Adversarial Network (GAN) has been widely used as an important component of deep neural networks [
15]. The GAN model has gained massive attention from researchers recently due to its prominent characteristics. It has two main rewards for machine learning based models: the generality and adversarial [
16]. It can generate new samples that can be used to prevent overfitting and, thus, improve machine learning performance. Moreover, it can be used to generate adversarial samples that can be used to improve the discriminability of the model. GAN use alternative training to estimate the density function over a data distribution using the Minimax algorithm [
17]. The Minimax game algorithm tries to minimize the maximum possible loss which results in multiple possibilities that can be used to generate new samples. In doing so, GAN projects the available simple distribution to a much more complex high-dimensional, real-world data distribution [
18]. GAN trains two adversarial networks called the generator and the discriminator. The generator is trained to map noise samples to synthetic samples with the goal is to generate new adversarial samples that can mislead the discriminator. Meanwhile, the discriminator trains to distinguish the real data samples from synthesized samples that were generated using the generator. GAN creates the new samples by making small changes to the original samples so as to deceive the detection model gain benefit of the nonlinear characteristics of neural networks and thus constructs a model that produces incorrect classification results.
Due to its prominent features, many researchers have applied the GAN algorithm to improve the classification performance of machine learning algorithms. Moti and Hashemi [
15] proposed a malware detection model for Internet of Things (IoT) using the Generative Adversarial Network technique and Convolutional Neural Network (CNN). CNN was used to extract high-level features while GAN was used to generate new malware samples to mitigate the limitations of availability of insufficient malware samples in IoT. Li and Zhou [
19] utilized GAN to develop a malware detection model-based adversarial example for the Android platform. Their proposed model called bi-objective GAN can generate evasive adversarial-example attacks able to fool the firewall and evade detection. Lu and Li [
20] used GAN to improve the classification accuracy of the malware detection by generating new samples that can mimic realistic-like malware samples as well as the realistic distribution of data. Zhang and Zhou [
17], proposed an improved Monte Carlo tree search (MCTS) algorithm for generating adversarial examples of cross-site scripting (XSS) attacks. A reward value is generated by the MCTS to rank the generated adversarial examples. The GAN algorithm was used to improve the detectability of adversarial examples. A GAN-based network was proposed to improve classification performance.
The following paragraph explains how GAN works. GAN formulates the adversarial problem as follows. Let 𝑋 denote the sample space, x is a benign sample, and 𝑔(𝑥)>0 denotes the classification function when the result is benign. The attacker aims to generate a malware sample 𝑥* that make 𝑔(𝑥*)>0. Thus, the aim of the attacker can be formulated as follows:
The GAN reduces the loss function value
𝑉 during the training of both generator
𝒢 and discriminator
𝒟 by solving the following optimization function:
This entry is adapted from the peer-reviewed paper 10.3390/fi15100318