The Internet of Things (IoT) is a network of billions of interconnected devices embedded with sensors, software, and communication technologies. Wi-Fi is one of the main wireless communication technologies essential for establishing connections and facilitating communication in IoT environments. However, IoT networks are facing major security challenges due to various vulnerabilities, including de-authentication and disassociation DoS attacks that exploit IoT Wi-Fi network vulnerabilities. Traditional intrusion detection systems (IDSs) improved their cyberattack detection capabilities by adapting machine learning approaches, especially deep learning (DL). However, DL-based IDSs still need improvements in their accuracy, efficiency, and scalability to properly address the security challenges including de-authentication and disassociation DoS attacks tailored to suit IoT environments. The main purpose of this research was to overcome these limitations by designing a transfer learning (TL) and convolutional neural network (CNN)-based IDS for deauthentication and disassociation DoS attack detection with better overall accuracy compared to various current solutions. The distinctive contributions include a novel data pre-processing, and de-authentication/disassociation attack detection model accompanied by effective real-time data collection and parsing, analysis, and visualization to generate the dataset, namely, the Wi-Fi Association_Disassociation Dataset. To that end, a complete experimental setup and extensive research were carried out with performance evaluation through multiple metrics and the results reveal that the suggested model is more efficient and exhibits improved performance with an overall accuracy of 99.360% and a low false negative rate of 0.002. The findings from the intensive training and evaluation of the proposed model, and comparative analysis with existing models, show that this research allows improved early detection and prevention of de-authentication and disassociation attacks, resulting in an overall improved network security posture for all Wi-Fi-enabled real-world IoT infrastructures.
- de-authentication and disassociation attacks
- intrusion detection system
- convolutional neural network
- transfer learning
- IoT Wi-Fi networks
1. Introduction
2. Intrusion Detection System (IDS)
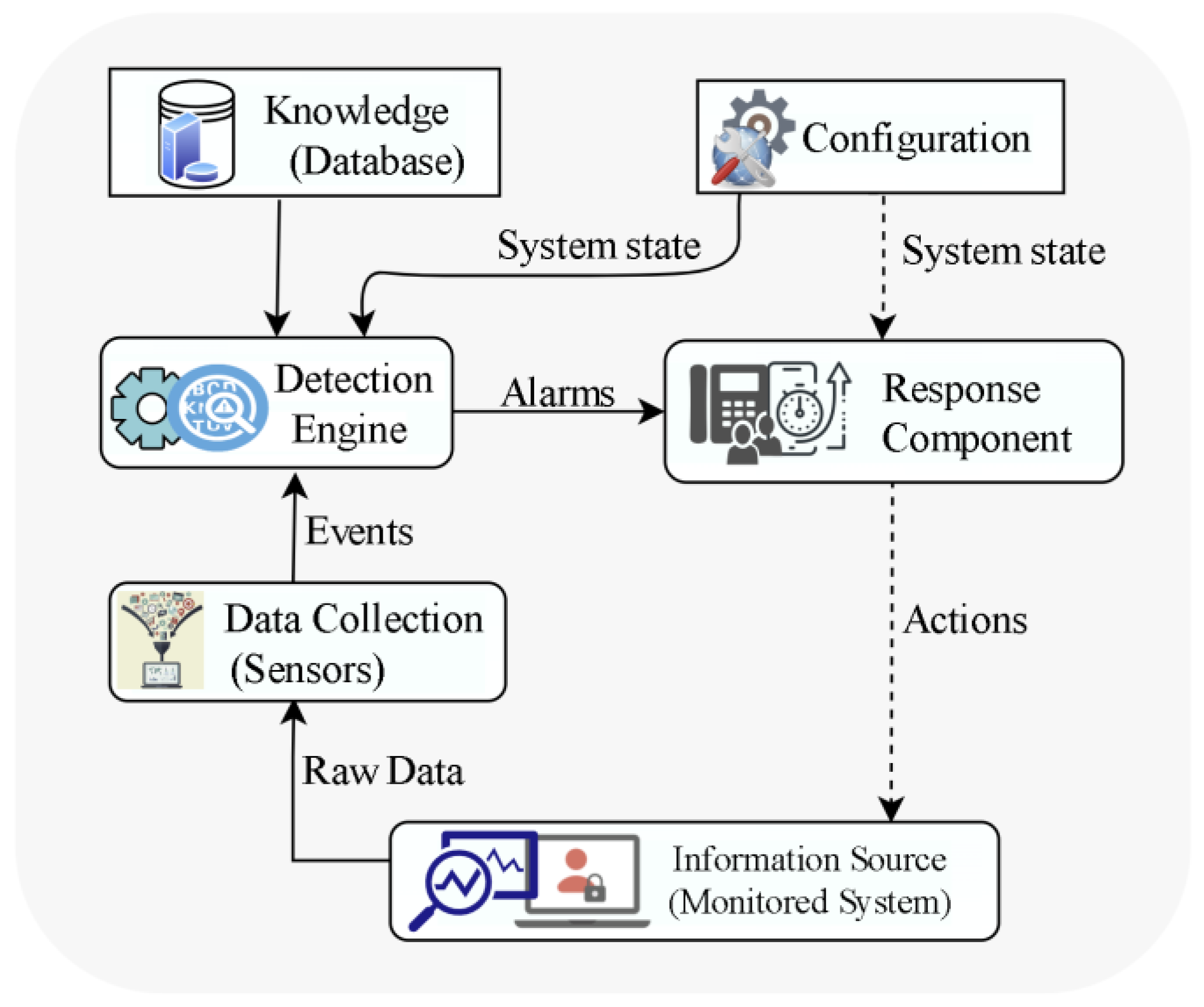
3. Machine and Deep Learning for IDS
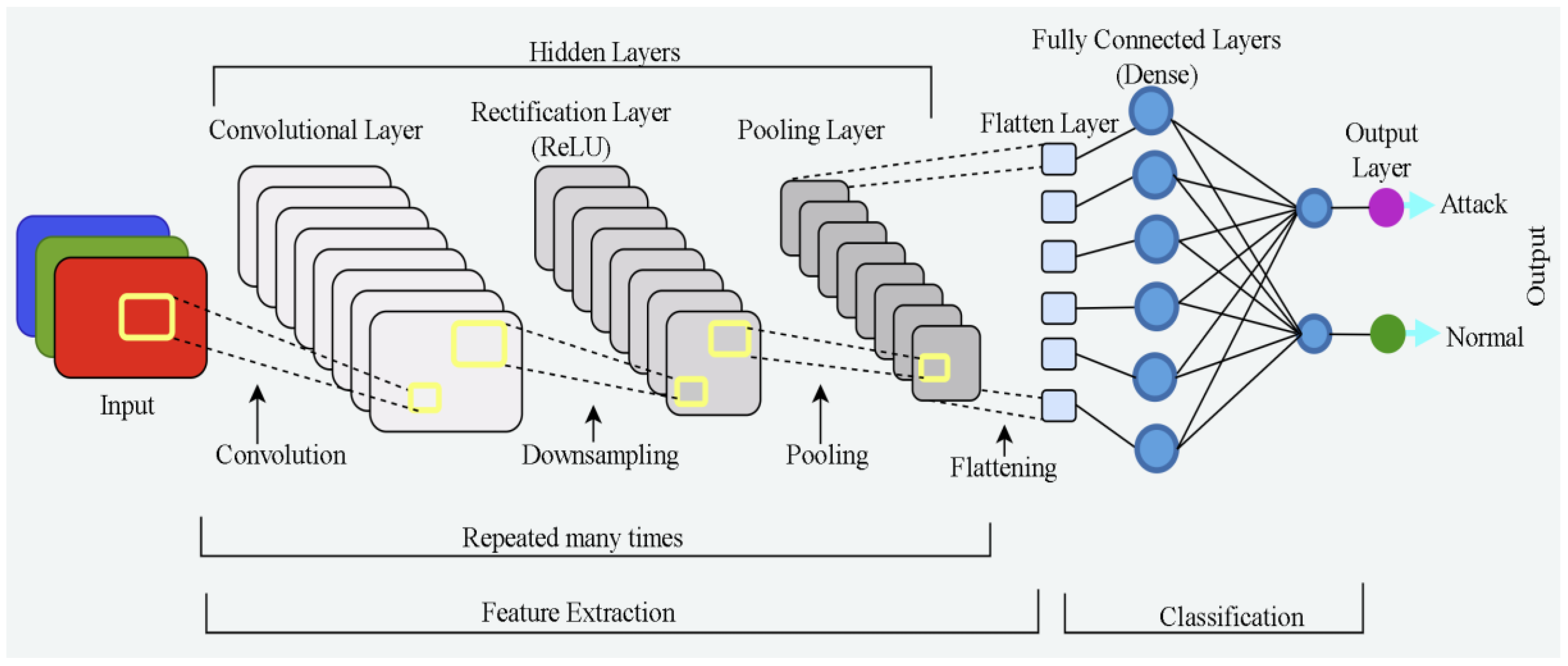
3.1. Convolutional Neural Networks
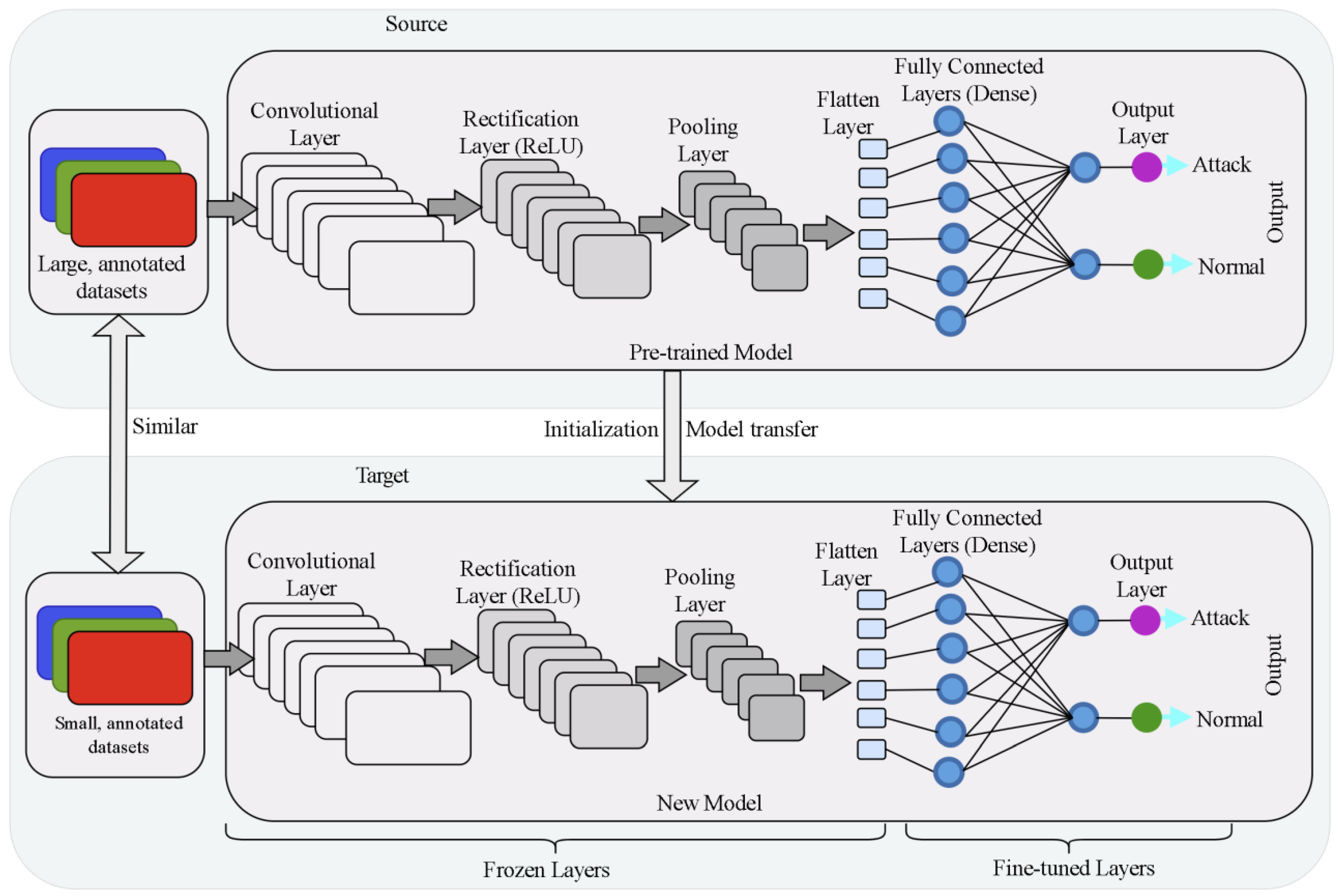
3.2. Transfer Learning
4. IoT and the Wi-Fi Protocol
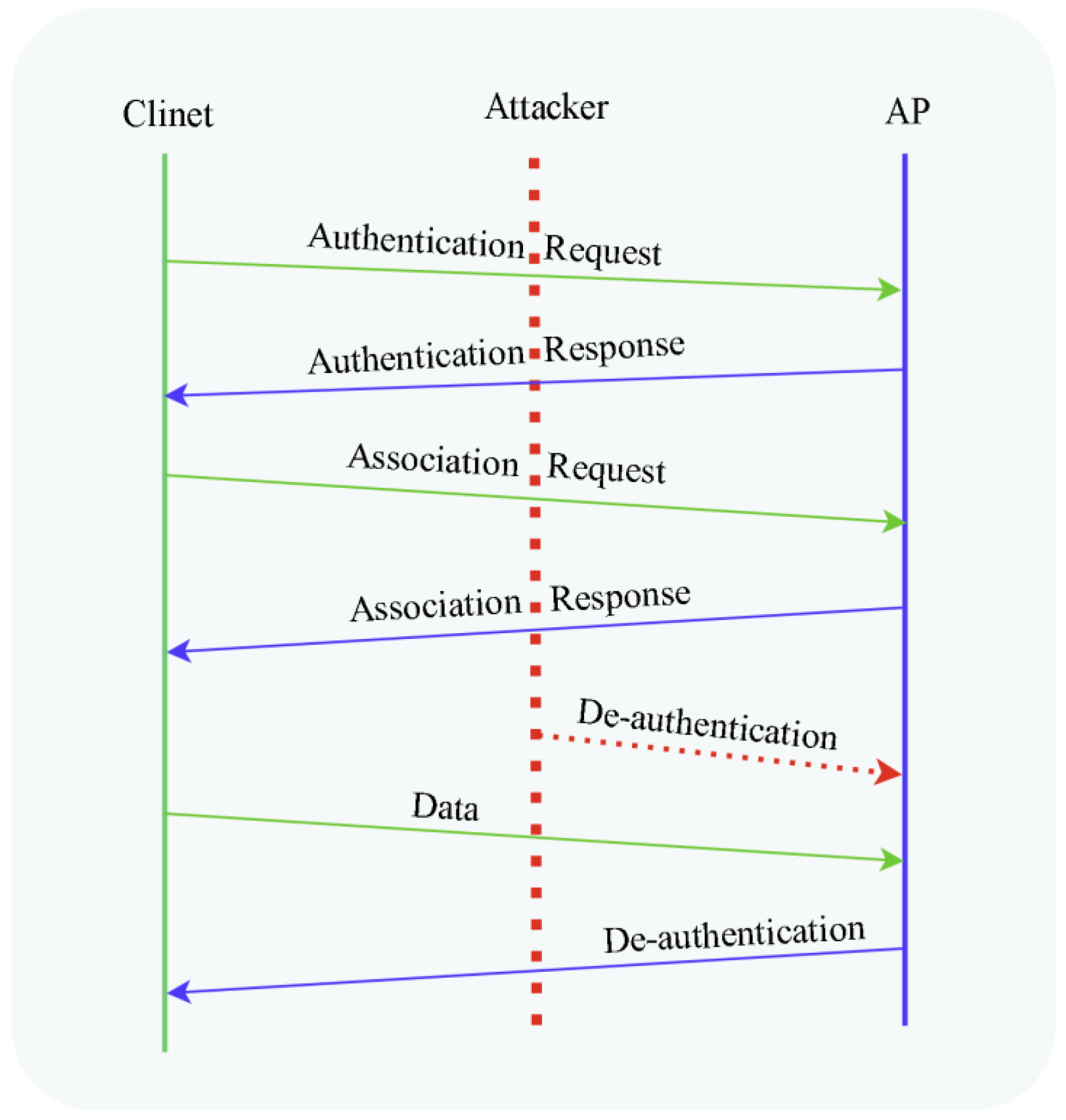
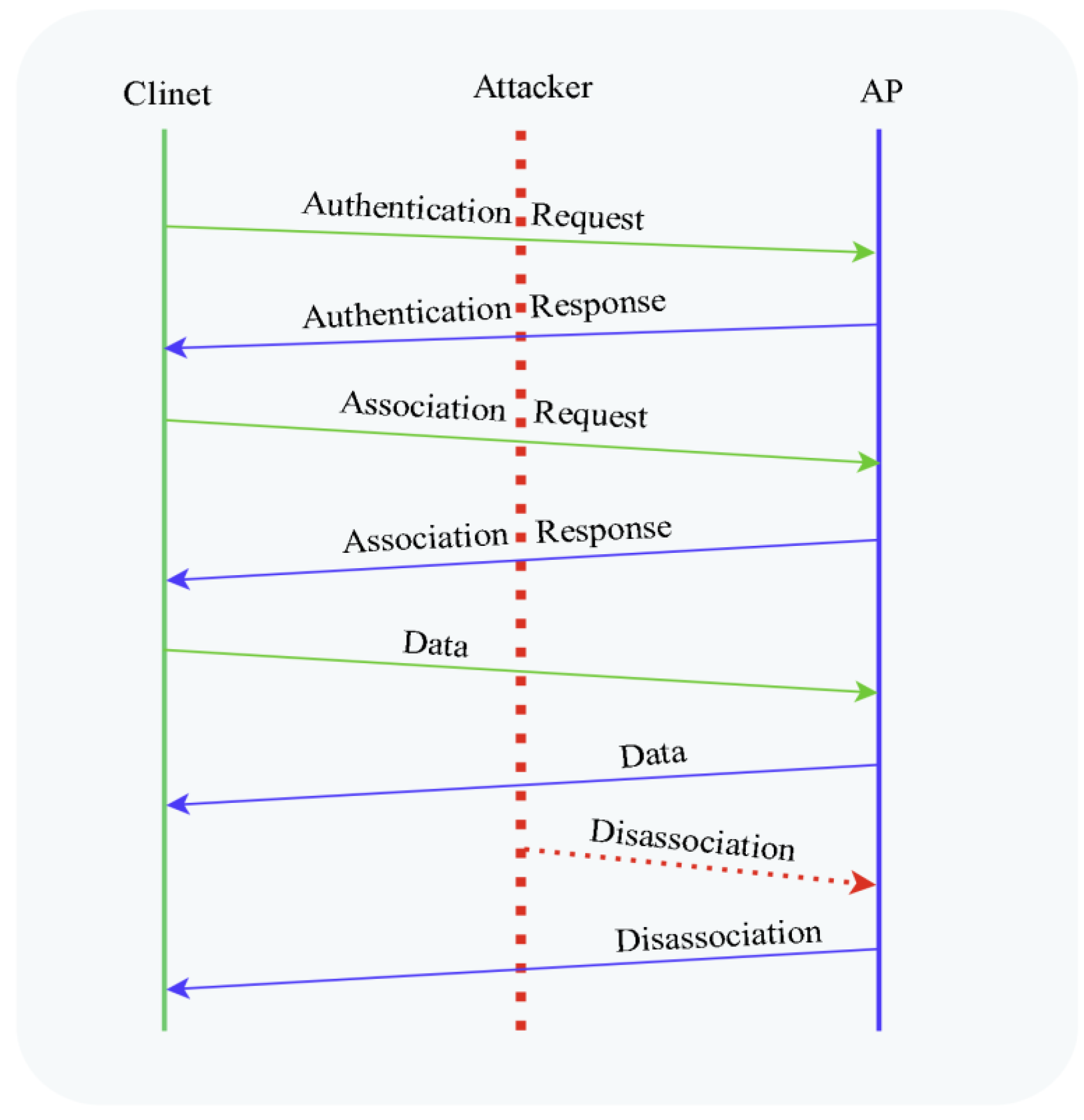
De-Authentication and Disassociation Attacks
5. De-Authentication DoS Attack
6. Disassociation DoS Attack
7. Log Collection and Parsing
8. Elastic Stack
This entry is adapted from the peer-reviewed paper 10.3390/electronics12173731
References
- IEEE 802.11-1997; IEEE Standard for Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- IEEE 802.11a-1999; IEEE Standard for Telecommunications and Information Exchange between Systems—LAN/MAN Specific Requirements—Part 11: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications: High Speed Physical Layer in the 5 GHz Band. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- 802.11g-2003; IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications: Further Higher Data Rate Extension in the 2.4 GHz Band. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- 802.11n-2009; IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC)and Physical Layer (PHY) Specifications Amendment 5: Enhancements for Higher Throughput. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- 802.11ac-2013; IEEE Standard for Information Technology—Telecommunications and Information Exchange between Systems–Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications—Amendment 4: Enhancements for Very High Throughput for Operation in Bands below 6 GHz. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- 802.11ai-2016; IEEE Standard for Information Technology—Telecommunications and Information Exchange between Systems—Local and Metropolitan Area Networks—Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 1: Fast Initial Link Setup. IEEE: Toulouse, France. Available online: https://standards.ieee.org (accessed on 12 May 2023).
- Gu, J.; Zhao, J.; Li, W. Research on WLAN Security Technology Based on IEEE 802.11. In Proceedings of the 2011 3rd International Conference on Advanced Computer Control, ICACC, Harbin, China, 18–20 January 2011; pp. 234–237.
- Juhász, K.; Póser, V.; Kozlovszky, M.; Bánáti, A. WiFi Vulnerability Caused by SSID Forgery in the IEEE 802.11 Protocol. In Proceedings of the SAMI 2019—IEEE 17th World Symposium on Applied Machine Intelligence and Informatics, Herlany, Slovakia, 24–26 January 2019; pp. 333–338.
- Yao, X.; Farha, F.; Li, R.; Psychoula, I.; Chen, L.; Ning, H. Security and Privacy Issues of Physical Objects in the IoT: Challenges and Opportunities. Digit. Commun. Netw. 2021, 7, 373–384.
- CVE Records for Deatuthentication and Disassociation Attacks. Available online: https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=deauthentication+attack (accessed on 28 June 2023).
- A. Reyes, A.; D. Vaca, F.; Castro Aguayo, G.A.; Niyaz, Q.; Devabhaktuni, V. A Machine Learning Based Two-Stage Wi-Fi Network Intrusion Detection System. Electronics 2020, 9, 1689.
- WPA3 Specification. Available online: https://www.wi-fi.org/downloads-public/WPA3%2BSpecification%2Bv3.1.pdf/35332 (accessed on 12 May 2023).
- IEEE Std 802.11ax-2021 (Amendment to IEEE Std 802.11-2020); IEEE Standard for Information Technology–Telecommunications and Information Exchange between Systems Local and Metropolitan Area Networks–Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 1: Enhancements for High-Efficiency WLAN. IEEE: Toulouse, France, 2021; pp. 1–767.
- Dalal, N.; Akhtar, N.; Gupta, A.; Karamchandani, N.; Kasbekar, G.S.; Parekh, J. A Wireless Intrusion Detection System for 802.11 WPA3 Networks. In Proceedings of the 2022 14th International Conference on COMmunication Systems & NETworkS (COMSNETS), Bangalore, India, 4–8 January 2022; Volume 3.
- Baras, K.; Moreira, A. Anomaly Detection in University Campus WiFi Zones. In Proceedings of the 2010 8th IEEE International Conference on Pervasive Computing and Communications Workshops, PERCOM Workshops 2010, Mannheim, Germany, 29 March–2 April 2010; pp. 202–207.
- Simbana, S.; Lopez, G.; Tipantuna, C.; Sanchez, F. Vulnerability Analysis Toolkit for IEEE 802.11 Wireless Networks: A Practical Approach. In Proceedings of the 3rd International Conference on Information Systems and Computer Science, INCISCOS, Quito, Ecuador, 13–15 November 2018; pp. 227–232.
- Seraphim, B.I.; Palit, S.; Srivastava, K.; Poovammal, E. A Survey on Machine Learning Techniques in Network Intrusion Detection System. In Proceedings of the 2018 4th International Conference on Computing Communication and Automation, ICCCA, Greater Noida, India, 14–15 December 2018; pp. 1–5.
- Satam, P.; Hariri, S. WIDS: An Anomaly Based Intrusion Detection System for Wi-Fi (IEEE 802.11) Protocol. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1077–1091.
- Yousefnezhad, N.; Malhi, A.; Främling, K. Security in Product Lifecycle of IoT Devices: A Survey. J. Netw. Comput. Appl. 2020, 171, 102779.
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A Survey of Intrusion Detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37.
- Danziger, M.; De Lima Neto, F.B. A Hybrid Approach for IEEE 802.11 Intrusion Detection Based on AIS, MAS and Naïve Bayes. In Proceedings of the 2010 10th International Conference on Hybrid Intelligent Systems, Atlanta, GA, USA, 23–25 August 2010; pp. 201–204.
- Thing, V.L.L. IEEE 802.11 Network Anomaly Detection and Attack Classification: A Deep Learning Approach. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6.
- Riyaz, B.; Ganapathy, S. A Deep Learning Approach for Effective Intrusion Detection in Wireless Networks Using CNN. Soft Comput. 2020, 24, 17265–17278.
- Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. Security Analysis of Network Anomalies Mitigation Schemes in IoT Networks. IEEE Access 2020, 8, 43355–43374.
- Sharma, N.; Jain, V.; Mishra, A. An Analysis of Convolutional Neural Networks for Image Classification. Procedia Comput. Sci. 2018, 132, 377–384.
- Narayana Rao, K.; Venkata Rao, K.; Pvgd, P.R. A Hybrid Intrusion Detection System Based on Sparse Autoencoder and Deep Neural Network. Comput. Commun. 2021, 180, 77–88.
- Lawrence, S.; Giles, C.L.; Tsoi, A.C.; Back, A.D. Face Recognition: A Convolutional Neural-Network Approach. IEEE Trans. Neural. Netw. 1997, 8, 98–113.
- Zhiqiang, W.; Jun, L. A Review of Object Detection Based on Convolutional Neural Network. In Proceedings of the 2017 36th Chinese Control Conference (CCC), Dalian, China, 26–28 July 2017; pp. 11104–11109.
- Chang, Y.; Yan, L.; Fang, H.; Zhong, S.; Liao, W. HSI-DeNet: Hyperspectral Image Restoration via Convolutional Neural Network. IEEE Trans. Geosci. Remote Sens. 2019, 57, 667–682.
- Devlin, J.; Cheng, H.; Fang, H.; Gupta, S.; Deng, L.; He, X.; Zweig, G.; Mitchell, M. Language Models for Image Captioning: The Quirks and What Works 2015. arXiv 2015, arXiv:1505.01809.
- Yang, J.; Li, J. Application of Deep Convolution Neural Network. In Proceedings of the 2017 14th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP), Chengdu, China, 15–17 December 2017; IEEE: Chengdu, China, 2017; pp. 229–232.
- Torfi, A.; Iranmanesh, S.M.; Nasrabadi, N.; Dawson, J. 3D Convolutional Neural Networks for Cross Audio-Visual Matching Recognition. IEEE Access 2017, 5, 22081–22091.
- Idrissi, I.; Azizi, M.; Moussaoui, O. Accelerating the Update of a DL-Based IDS for IoT Using Deep Transfer Learning. IJEECS 2021, 23, 1059.
- Pan, S.J.; Yang, Q. A Survey on Transfer Learning. IEEE Trans. Knowl. Data Eng. 2010, 22, 1345–1359.
- Global Economic Value of Wi-Fi_2021-2025—Wi-Fi Alliance. Available online: https://www.wi-fi.org/downloads-public/Global_Economic_Value_of_Wi-Fi_2021-2025_202109.pdf/37347 (accessed on 12 May 2023).
- Waliullah, M.; Moniruzzaman, A.B.M.; Rahman, M.S. An Experimental Study Analysis of Security Attacks at IEEE 802.11 Wireless Local Area Network. Int. J. Future Gener. Commun. Netw. 2015, 8, 9–18.
- Mahini, H.; Mousavirad, S.M. WiFi Intrusion Detection and Prevention Systems Analyzing: A Game Theoretical Perspective. Int. J. Wirel. Inf. Netw. 2020, 27, 77–88.
- Milliken, J.; Selis, V.; Yap, K.M.; Marshall, A. Impact of Metric Selection on Wireless Deauthentication Dos Attack Performance. IEEE Wirel. Commun. Lett. 2013, 2, 571–574.
- Tyagi, M.; Narvare, S.; Agrawal, C. A Survey of Different Dos Attacks on Wireless Network. Comput. Eng. Intell. Syst. 2018, 9, 23–32.
- Agrawal, A.; Dixit, A.; Shettar, N.; Kapadia, D.; Karlupia, R.; Agrawal, V.; Gupta, R. Delog: A Privacy Preserving Log Filtering Framework for Online Compute Platforms. arXiv 2019, arXiv:1902.04843v3.
