Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Subjects:
Telecommunications
The Internet of Things (IoT) is an advanced technology that comprises numerous devices with carrying sensors to collect, send, and receive data. Due to its vast popularity and efficiency, it is employed in collecting crucial data for the health sector. As the sensors generate huge amounts of data, it is better for the data to be aggregated before being transmitting the data further. These sensors generate redundant data frequently and transmit the same values again and again unless there is no variation in the data.
- Internet of Things (IoT)
- fuzzy logic
- data aggregation
- healthcare
- FIS
- member functions
1. Introduction
The Internet of Things (IoT) is made up of smart devices that can communicate with each other by exchanging information [1]. These devices include multiple intelligent sensory elements and wearable smart devices, which are crucial for the development of the IoT [2]. The IoT has become an integral part of various fields such as healthcare, mining, buildings, cities, agriculture, transportation, industries, smart homes [3], smart surveillance [4,5], and automated systems [6]. Smart medical devices in healthcare can connect people and objects, making life easier and more convenient [7]. The Internet of Medical Things (IoMT) has become a crucial component of healthcare, offering intelligent services by collecting different types of data and transmitting them to cloud-based repositories [8,9]. The integration of the IoMT into smart healthcare has enabled seamless connectivity. As a result, developing an environmentally sustainable [10] solution to address the multiple challenges faced by the latest IoT-based smart healthcare strategies [11,12] is critical. Medical devices enable remote monitoring of patients, resulting in improved quality and efficiency of medical treatment.
Health information is collected from patients’ sensor devices and then transmitted to smart collectors in a secure manner in both normal and emergency situations [13]. Miniaturized devices play a crucial role in healthcare data collection, where security is quite critical [14] for efficient authentication [15]. Cyber–physical systems (CPSs) are utilized in social services, particularly in healthcare applications, as cost-effective solutions [16]. In health monitoring, the health-related data of patients are transmitted to the cyber world to allow for real-time processing and analysis of vast amounts of data [17]. In this scenario, enhanced computing frameworks are necessary to dynamically integrate both real-world and cyber aspects of medical cyber–physical systems [18]. IoT-enabled medical networks can manage complex communication to handle the processing of many users [19].
Fog computing architectures act as a middle layer between cloud servers and end users, providing data computation, storage services, and networking capabilities. The term “FoG server” was first introduced by Cisco [20]. The smart healthcare architecture [21] enables monitoring devices to communicate with patients and transmit data to a server remotely [22,23]. At the edge of the network, the smart healthcare architecture processes large amounts of data generated by numerous devices to reduce bandwidth and energy consumption. This reduces overhead on the cloud server and balances the load among multiple local fog nodes by integrating fog and the IoT [24]. Fog nodes may make intelligent decisions in emergency situations to efficiently handle critical health issues [25] with smart collector nodes [26]. The combination of fog computing and cloud computing can be an appropriate solution to overcome challenges in the IoT and healthcare systems [27,28].
Data aggregation is a critical technique used in the IoMT to collect health parameters from sensing devices and transmit them in a collective manner to reduce the transmission cost [29]. Furthermore, to optimize the data aggregation processes, mobile devices have been introduced as collector nodes [30]. For better collection and analysis of the data, fuzzy logic is employed. An efficient fuzzy-based healthcare data collection analysis mechanism is an approach that utilizes FL to analyze data. These data are gathered from wearable sensors, implanted devices, and some other resources. FL uses a mathematical framework to manage patient data and, in return, provides decisive information to healthcare professionals. This mechanism is needed in the healthcare sector because FL efficiently tackles huge, sophisticated, and varying patient data. It examines changes in patients’ data readings over time, assists doctors in making rational decisions timely to avoid health complications later on, and is cost-effective. These benefits cannot be attained with conventional methods. Robust security measures are demanded in IoMT systems to preserve patient data privacy and integrity [31,32].
Ensuring secure and privacy-preserved aggregated data is a crucial and mandatory aspect of both edge–node devices and fog nodes [33]. To maintain both data integrity [34] and to authenticate edge devices, authentication is also required using encryption-based measures [35]. Recent surveys add to the body of knowledge on aggregating healthcare data using IoT-based sensing devices [24,36] and the applications of fog computing [22,37]. However, these surveys do not address the security measures needed during the transmission of aggregated data. On the other hand, [27,35] considered security measures but did not extensively explore IoT scenarios. In [38,39,40], secure data collection and aggregation scenarios were explored but fog-assisted approaches were not considered.
2. Data Aggregation Using Artificial Intelligence Techniques
Kulkarni et al. highlighted the use of a computational intelligence (CI)-based algorithm. These CI-based algorithms deal efficiently with dynamic environment sand limited node energy. As CI-based solutions are not perfect under some conditions, artificial neural networks (ANNs), genetic algorithms (GAs), and particle swarm optimization (PSA) can be used [41]. In [42], swarm-intelligence-based schemes were elaborated that have improved network lifespan and use energy efficiently. Chen et al. presented the data aggregation ACO algorithm (DAACA) to utilize network energy efficiently, which is based on the ant colony optimization algorithm approach. The DAACA has features of both local and global pheromone methods. The different versions of DAACA assist in reducing computational and communicational overhead and increasing node life. The advantage of this scheme is that it features fault tolerance, low complexity, and higher flexibility [43].
Imitating the dynamic nature of a river, intelligent water drops (IWDs) are used in WSNs, where every drop shows a solution. This method is deployed after amendments in tree-based data aggregation to obtain optimal solutions [44]. To economically use energy in WSNs, an ant-colony-based optimization scheme called the minimum incremental dissemination tree (AMIDT) was introduced. This scheme consists of two main stages: in the first stage, an online tree is formed; during the second phase, a path- and reference-based heuristic is applied. AIMDT has reduced cost and energy utilization compared with existing schemes [45]. For different optimization issues, the ABC algorithm outperforms others in cases where nodes do not directly transmit data to the aggregator node or BS. Knowing the best traveling path of a mobile robot is important for reducing energy consumption. For this issue, the ABC algorithm performs better than greedy algorithms. The positive point of this scheme is that the retrieved results are very stable but cannot be implemented in the case of multiple robots [46]. As the number of sensors increases, the data they produce also increase, which is problematic for data mining techniques. To overcome this problem, a decentralized scheme using a WSN neural network was presented. A data technique was trained using data gathered from nodes in the network. The system performs well and was used for higher WSNs [47]. An optimum cluster was chosen using the shuffled frog algorithm. It showed better efficacy, fast searching, and optimal energy usage. CHs were selected based on the residual energy of WSN nodes [48]. The PSO method was used to aggregate data from complex and large networks. These methods assist in finding a better transmission path between nodes that lessens hop distances but increase hop counts. This method has lower energy consumption and is suitable for the dynamic nature of the environment [49].
The F-LEACH scheme was presented to extend the network life span and economical energy utilization. Selecting an appropriate cluster head improves network performance. For this purpose, the FIS function was used to determine cluster heads in the network. FIS considers the distance of nodes from the base station and residual energy level; a node with a low distance from the BS and high energy has a high probability of being selected as the cluster head. If N nodes are in the network and the total clusters are K, there are approximately N/K clusters in the network. One of them is a CH node, while others are ordinary nodes. The proposed scheme has fewer dead nodes, improved residual energy, and improved work performance up to 5–20% [50].
Abid et al. designed a scheme that deals with the problem of efficient data aggregation and transmission in time-constrained wireless sensor networks. For the aggregation of data, multilevel clustering was used, in which a structure-free approach was considered. In this clustering, nodes are divided into large clusters during first-phase clustering. Each group has one cluster head (CH) collecting member data. The CH node needs more energy to work efficiently, so it is important to check the energy level of nodes from time to time and select the CH node intelligently. For this purpose, the event-driven cluster head election (EDC) algorithm was used in which node residual energy is checked against threshold energy E0 and checking the CF bit. If the current CH fulfills both conditions, no change occurs. Otherwise, a node near the present CH is selected as the next CH to reduce energy wastage. The proposed scheme was simulated using NS-2, and the results proved that the proposed method achieved better aggregation gain and lower delay. The drawback of the process is that if the energy level of primary CH dissipates, the communication of the whole network is affected [51]. Singh et al. proposed an energy-efficient scheme to overcome the probability of transmitting redundant data and balanced energy utilization. For clustering, four main parameters were considered in the fitness function: the energy level of the node, density near CH, Euclidean distance of the CH and the sensor nodes calculated usinf Equation (1) [52], and distance from CH to BS.
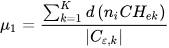 where 𝜇1 denotes the maximum Euclidean distance among nodes and the respective CHCH, while 𝐶bejk represents the total nodes lying in the communication range of egg e of a cluster named k. to calculate the total amount of energy of nodes lies in a network; Equation (2) [52] is used.
where 𝜇1 denotes the maximum Euclidean distance among nodes and the respective CHCH, while 𝐶bejk represents the total nodes lying in the communication range of egg e of a cluster named k. to calculate the total amount of energy of nodes lies in a network; Equation (2) [52] is used.
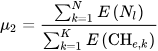
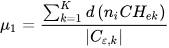
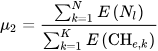
Using a fitness function, 20%20% of the nodes are considered for CHCH, and after calculating their cost, the best host nest is obtained. 𝜇1 denotes the maximum Euclidean distance among nodes and their respective CHCH; Equation (3) [52] is used to calculate cost C. The value of 𝜆 is considered as 0.5. The lower value obtained by 𝜇1 and 𝜇2 assists in reducing the intracluster distance, which ultimately helps with the selection of ideal CHCH.
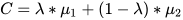
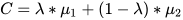
Vasim et al. presented a scheme emphasizing prolonging network life while efficiently consuming energy. The proposed method consists of four important phases. In phase 1, node mobility is monitored using the distance formula. Mobility dissipates energy quickly, so the node having low mobility is selected to minimize utilization. For determining CH, the AE-LEACH algorithm is implemented in the next phase, which uses residual energy, and distances from BS are used. A threshold value is calculated for all the nodes that lie in the range of zero or one. A certain node works as a head if the computed value exceeds the capacity. The CH broadcasts messages in the network; all nodes that reply to that message become cluster group members. Member nodes transmit data to the CH, which are sent to the BS after performing aggregations. The particle filter algorithm estimates the targets’ next state in the third phase. In the last step, the Gini index is used to check the even consumption of energy level. NS-2 evaluates the proposed scheme and provides better results in network lifetime, energy utilization, and residual energy. The benefit of this scheme is that the CH is not fixed and changes frequently, reducing the burden on the node playing the role of CH. The drawback of this technique is that the case of malicious nodes is not handled efficiently [53].
Amutha presented a hybrid scheme that caters to both cases when the sink node is static and moveable. In both scenarios, the CH is selected by checking some circumstances, including residual energy, node density, distance factor, and node centrality. The node centrality is a new parameter that has yet to be included in previous studies, which leads to selecting the optimal CH; the members a short distance from the CH and high energy are clustered under that head. For the static case, static sink nodes (SSNs) are placed in left, right, and center in an area of interest (AOI) to check the CH’s energy level and effective path. In the second case, the mobile sink (MS) node moves randomly to collect data. The mobility model was introduced to resolve the hot-spot problem in a later approach. The simulation was conducted using NS-2; for different metrics, it showed better energy consumption and data delivery, low delay, and higher throughput than former schemes. The advantage of this scheme is that in the case of a static sink node, all possible directions for calculating the optimal path to disseminate aggregated data to SN are considered. The problem in the case of MS is that it works well only for short-range communication but not long-range communication [54].
Yan et al. proposed using game theory to cluster sensor nodes and reduce energy consumption in wireless sensor networks (WSNs). Each sensor node is viewed as a player node and uses its current state (active or passive) to cluster them. GEC introduces the transition of active nodes into a sleeping state and vice versa when required and introduces penalty principles to control energy violations caused by selfish or greedy nodes in the network. These penalties aim to reduce the energy consumption of communicating nodes in the network [55]. The benefit of this scheme is that it provides reliable performance even in harsh environments. The drawback of this scheme is that it is not suitable for heterogeneous WSNs. To reduce energy consumption in a heterogeneous WSN environment, Bhushan et al. presented a fuzzy-attribute-based joint integrated scheduling and tree formation technique, which intelligently selects different parents for different types of nodes. Two phases were defined: control phase and data phase. In the control phase, nodes choose lots and parents, and they have information about the number and type of data packets and the type of packet that the node itself has generated. In the second phase, nodes are created, and data are transmitted. For each outgoing data packet, a different parent can be chosen per its type. To fuzzify the system, min–max normalization is used to scale the weights. These weights act as membership functions, having small consequences with a straight connection to a node having a high probability of being selected as the parent for data aggregation and transmission to an SN. For packet t, a neighbor of type t is chosen; if it is present, data are forwarded to it. Otherwise, having the node’s neighbor of type t, data are forwarded to it. In case no such scenario occurs, the node with the fewest dynamic nodes is considered the parent node. For checking the performance of the proposed schemed FAJIT, a simulation was performed and compared with DICA and DICA_EXTENSION under different metrics. The results showed that FAJIT performs better than the previous two schemes. The benefit of this scheme is that it is considered a heterogeneous environment for sustaining energy levels. The drawback of the method is that complications increase when deploying it for large networks [40].
In [56], the author proposed a scheme for collecting data in which sensors are deployed. After that, clustering is performed, and data are saved into a repository. To cluster uncategorized data, the K-means clustering method is used. The proposed scheme, fuzzy-logic-based data aggregation (FLDA), uses fuzzy logic. Afterward, fuzzification and defuzzification are applied to obtain a discrete output to aggregate the most appropriate data, decreasing the volume of duplicate data. The proposed scheme was simulated in a MATLAB MATLAB 2018b environment, and the results showed that FLDA achieved better data persistency, higher network lifetime, and reduced energy utilization. The drawback of the scheme is that it works better under specified assumptions that cannot always be achieved as the density of nodes increases.
By considering the hot-spot or energy hole issue in WSNs, Ssert et al. presented a technique that uses energy economically. The proposed method, two-tier distributed fuzzy-logic-based protocol (TTDFP), is categorized into two tiers. In the primary tier, fuzzy logic is used to select CHs for unequal clustering via the process of the probabilistic model. In the second tier, the routing path is chosen. The cluster head generates the Min value, which is assigned as one. The fuzzy logic is applied if the min value increases and becomes >1. The proposed scheme was simulated with MATLAB, and the results showed that TTDFP achieved a higher ratio of the alive node’s residual energy until the last round. The advantage of this proposed distributed scheme is that the hot-spot problem is resolved. It balances and economically consumes power, which ultimately increases network lifespan. The limitation of the proposed method is that no procedure is initialized to lessen the load on the CH [57].
The grid clustering method was introduced to efficiently aggregate data from nodes by utilizing an economical amount of energy. The whole area is divided into grids, and a CH is selected for each. The entire network acts as an environment, and the CH works as an agent. The nodes with a short distance and good link quality are more likely to be selected as aggregator nodes. Afterward, the sink node is placed occasionally in areas where a low amount of energy is used. For this purpose, the fruit fly optimization algorithm is used. MATLAB was used for simulation and generating results considering important metrics such as PLR, energy utilization, and throughput. The benefit of this scheme is that it reduces latency and enhances node lifetime by minimizing energy consumption. The drawback of the method is that complications arise, and performance degrades in the case of dense WSN [58]. To maintain efficient data aggregation in heterogeneous networks, the scheme uses fuzzy logic scheduling, which takes two inputs: the residual energy of a node and the overlapping range of a node and the nodes in its vicinity. The output of the system is a suitable data rate. In the second stage, the binary tree of a CH is created, and the BS is responsible for implementing the dragonfly algorithm to create an aggregated tree. Afterward, high-priority nodes are placed as left and right children. If two nodes have the same priority level, in this case, the node with low priority is considered first. When the tree is completed, it is evaluated based on a fitness function. The fitness function is calculated using Equation (4) [23].
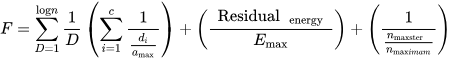
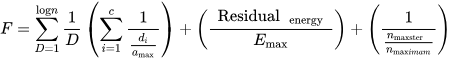
This equation checks factors including distance to the sink node, residual energy of CHCH, and the number of CMs. Then, it evaluates the constructed tree based on the abovementioned terms and selects the best tree. D shows the depth of the present aggregated tree, n is the total CHCH in the network, c is the CHCH in a current tree, d is the distance between CHCH and SN,𝒢5 is the maximum distance between CH and SN, 𝐸max is the ultimate energy level of CHs, the 𝑛−cluster is the total CM in a cluster ii, and 𝑛maximum shows the entire CM in the group. The proposed scheme was simulated using NS, performing better than existing schemes. The benefit of this scheme is that it provides better data packet transmission because of a suitable aggregation tree that was not considered in previous methods. The drawback of this technique is that the CH has to bear a higher load that eventually consumes more energy [59]. This protocol introduces a multipath for aggregated data to transmit crucial healthcare data to medical servers (MS) and reduce delay. The incoming data are divided into normal and emergency data. When biosensors send readings, if the generated data are beyond the normal range, it sets the threshold value as one. This sort of data are termed emergency data and are transmitted to cluster heads from the best routes with the lowest congestion rate. On the other hand, normal data are transferred from ordinary routes. Fuzzy logic is employed to rank the data. The scheme has a lower packet loss rate, and critical data are transmitted to the MS effectively, but the security perspective needs to be addressed [60]. To resolve the hotspot problem in WBANs, a temperature-aware scheme was presented, which considers the temperature of nodes before selecting the CH. The clustering is performed for data aggregation based on fuzzy logic. The fuzzy logic considers route breakage, residual energy, and nodes having the same neighbors. Similar nodes lie in the same cluster and aggregate data efficiently. The proposed scheme consumes low power while transmitting data to the coordinator, but complexity increases in high-level heterogeneous environments [61]. To understand the health situation of patients, the K-edge mechanism was introduced in a heterogeneous health-sector environment. In the initial phase, fuzzy logic is used to know the heart condition of patients. Then, a CNN mechanism is employed to determine the respiratory condition of patients. By using multianalysis and Mamdani fuzzy output, the patient’s condition is evaluated. The K-edge implementation provides better results regarding patient condition. The results demonstrated an accuracy of 98.68% for respiratory conditions and was suitable for performance in resource-restricted environments [62]. In another method, to increase the efficacy of data transmission in the WBAN context, the aggregation node dynamically selects the aggregation frame. The data are classified into seven user priorities (UPs): UP7 has the highest priority, and UP0 has the lowest priority. The data are transferred to queues and sent to the central hub, where they are transmitted to the main server. Queue 0 contains emergency data, which are dispatched without delay. At the same time, aggregation occurs at Queues 1 and 2. For selecting an aggregation frame, the DQN algorithm is used. The hub node offloads the tasks and sends them to the medical server [63].
3. Schemes Dealing with Data-Aggregation-Based Delay
During this aggregate process, hurdles like high energy consumption and delays occur, reducing network efficiency. An optimal partial aggregation (OPA) scheme was presented to resolve this issue. In this scheme, a node with a higher lifetime is considered an aggregator. A multiswarm fruit fly optimization algorithm (MFOA) is used to extend the aggregator node’s lifespan. Subsequently, an enhanced version of time to task (ToT) is used to reduce the delay issue in the aggregation of data. To find the quickest path to send data from source to destination, a nondominated sorting gravitational searching algorithm (NSGSA) is used. For simulation, an NS-2 simulator was used. The results showed that OPA has a longer network life span, low delay, and high throughput, and utilizes resources efficiently compared with previous techniques [64].
Game theory and an ant-colony-based data gathering technique (GTAC-DG) scheme were introduced to maintain the energy level of nodes to improve system performance for a long time. In the first level, the game theory idea is applied, in which all nodes in a network act as players, and nodes with high residual energy and load have a high probability of becoming rendezvous points (RPs), while other nodes become candidates. During the second stage, the best optimum path is selected. An enhanced version of ant colony optimization determines an appropriate trajectory for the mobile sink to reach the RPs. RPs having a high load are given significant importance to visit by the MS during data collection. The proposed scheme was simulated in MATLAB 2018b. This scheme has better network life and economic resource consumption and fewer dead nodes than former schemes. The drawback of this scheme is that implementing both algorithms increases computation overhead and makes it costly to deploy [65].
This entry is adapted from the peer-reviewed paper 10.3390/s23187799
This entry is offline, you can click here to edit this entry!
