Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is an old version of this entry, which may differ significantly from the current revision.
Subjects:
Computer Science, Cybernetics
As an Internet of Things (IoT) technological key enabler, Wireless Sensor Networks (WSNs) are prone to different kinds of cyberattacks. WSNs have unique characteristics, and have several limitations which complicate the design of effective attack prevention and detection techniques.
- Internet of Things
- wireless sensor networks
- security
1. Introduction
Wireless Sensor Networks are the backbone that enables Internet of Things (IoT) at low cost and low power [1]. These networks have been considered for a wide range of applications, such as military, environmental, healthcare, and civilian, despite being vulnerable to attacks [2]. Indeed, Wireless Sensor Networks (WSNs) result in major concerns in terms of security. Concerns include the use of devices which have resource constraints in terms of energy, the adopted wireless broadcasting channels, the involvement of multi-hop relays, the dynamic network topology, variable medium-to-large network scales, heterogeneous sensor node fabrication, and most importantly, the different routing protocols employed. Securing WSNs is relevant to securing IoT [3], as the latter comprises one or more WSNs, which implies that developing prevention, detection, and mitigation security solutions for WSNs are essential for establishing secure and reliable IoT systems.
Classical WSN security techniques, such as spread spectrum, cryptography, and key management [4,5], may not efficiently detect attacks, and can demand sophisticated software and hardware changes, rendering these solutions insufficient to address WSN security concerns, as WSN devices constrain the network’s power, storage, computational, and communication capabilities [6]. There has been growing interest in novel security paradigms, with cybersecurity companies investing as much as USD 119 billion to solve these problems [7]. This has led to newly evolved means aimed at strengthening WSN security against possible cyberattacks via Machine Learning (ML) and Blockchain (BC) [8].
2. Existing Surveys on ML and BC in WSN
In this regard, a few previous surveys have focused on presenting state-of-the-art ML and BC techniques for WSN cybersecurity. Key surveys tackling WSN security are tabulated in Table 1, which highlights the different subtopics covered, including ML, BC, attack taxonomy, and ML–BC integration, among others. The surveyed sources were collected from popular academic databases, such as IEEE Xplore, Elsevier, and Scopus, as per the most recent citation provided by Google Scholar, and are detailed in Figure 1.
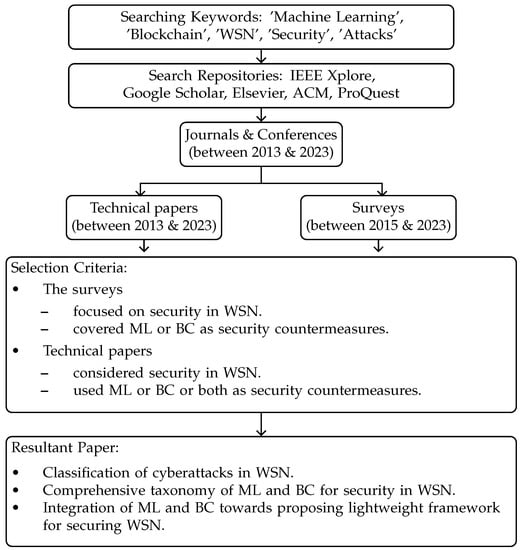
Figure 1. Paper collection criteria flowchart.
Table 1 reveals that research work on ML techniques is the primary subject of existing survey papers in the literature. A number of surveys that were published between 2012 and 2017, such as [16], did not examine WSN-related ML techniques, instead jointly discussing methods adopted in both IoT and WSN. On the other hand, surveys similar to [16,17,18,19] focused primarily on WSN. The authors of [19] considered only Denial of Service (DoS) attacks over the five TCP/IP layers. The authors of [17] provided a generalized and comprehensive review of ML techniques adopted to support WSNs against their inherent limitations, including security. The paper specifically focused on ML methods used to detect outlying and misleading measurements. The authors of [14] discussed the different types of attacks targeting WSNs and associated proposed ML solutions. Protecting WSNs using several ML methods was discussed in [16]. The authors of [20] explored using ML techniques with WSNs, including anomaly detection, with a focus on Deep learning (DL) techniques. A different research direction was analyzed in [20,21], where the authors focused on a specific type of WSN. The authors of [20] presented ML learning techniques targeting advanced WSN systems, and [21] reviewed ML techniques to secure industrial WSN systems. The authors of [22] reviewed ML algorithms and considered using software-defined networking (SDN) as a solution that can help enhance the node efficiency, creating a new foundation for using ML schemes to secure WSNs.
Considering BC techniques, several reviews have been conducted on securing IoT through the use of BC, such as [7,23,24,25,26,27,28,29,30]; however, Ref. [31] is the only article addressing BC for mitigating cyberattacks in WSNs. The study concluded that integrating BC techniques within WSNs has limitations, as BC is demanding in terms of both energy and computational complexity and is not expandable.
3. WSN Security Requirements
The most important WSN security requirements include integrity, availability, scalability, non-repudiation, mutual authentication, confidentiality, and data freshness, defined in turn as follows:
-
Integrity: transmitted messages cannot be tampered with due to illegal actions when moving from one node to the other.
-
Availability: legitimate (and authenticated) nodes can effectively access the network/provided services.
-
Scalability: the network should be able to cope with increases in size and to adapt to the dynamic addition and removal of various nodes, and node functionalities must be incorporated with sensor nodes for every service without affecting the network’s security level.
-
Mutual Authentication: the identities of any pair of nodes engaged in communication must be recognized before they interact.
-
Non-repudiation: the nodes cannot deny the implemented operations or alter the messages they send.
-
Confidentiality: the privacy of sensitive data transmitted over the network medium must be preserved by ensuring that any intruder or other neighboring network intercepting the communication channels cannot obtain any confidential information.
4. WSN Design Challenges and Unique Characteristics
WSN security solution design is highly affected by the unique features of these networks that make them more susceptible to cyberattacks than other technologies. This is primarily due to their challenging underlying infrastructure, which consists of a collection of sensor nodes utilizing scarce resources. The basic building blocks of a sensor node consist of four main units, namely, processing, sensing, communication, and power [31], as shown in Figure 2. The processing unit is the central unit, containing a processor or micro-controller that controls the sensor’s activities and executes the communication protocols; however, it has limited storage memory. The processing unit is connected to the sensing unit by an Analog to Digital Converter (ADC). The sensing device captures surrounding data, which are then converted into an electrical signal by the ADC. The communication unit typically supports data exchange between the sensor and the other network elements using a transceiver. Finally, the power unit provides the electrical energy required by the other units using limited-lifespan batteries. Optional sensor hardware additions include power generation and mobilization units [35]. Certain nodes may include a location-finding unit for positional localization in reference to the node’s neighbors. These special characteristics must be identified before they can be used in the design and development of more secure networks. The following points describe the dominant design considerations in WSNs in detail, which are further highlighted in Figure 3.
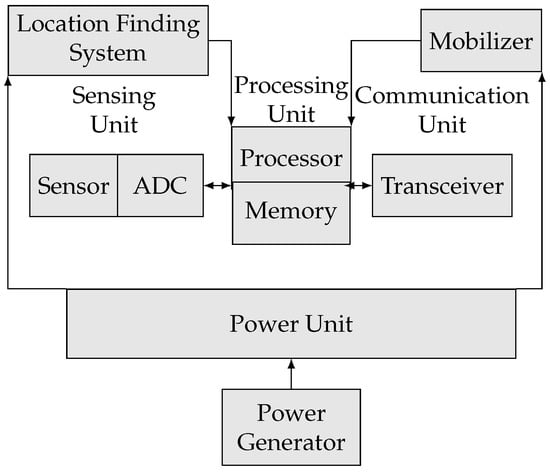
Figure 2. Illustration of sensor node building blocks.
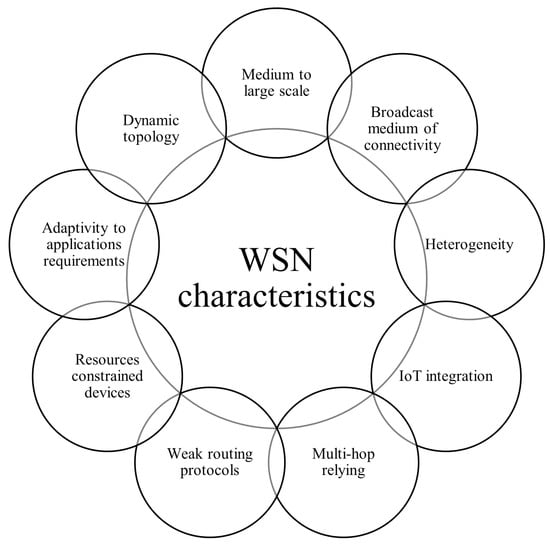
Figure 3. Unique characteristics of WSNs.
-
WSNs can be used in a wide range of applications with different security requirements; however, they must be able to ensure privacy, confidentiality, integrity, freshness, and authentication.
-
Sensor nodes must be heterogeneous in terms of fabrication and energy-saving strategies, such as sleep, idle, and wake-up modes, which dictates the need to provide different underlying network architectures for the different heterogeneous applications.
-
WSNs have many appealing applications, creating a need for different levels of secure functionalities and service requirements, such as secure node selection, data aggregation [36], localization, and routing.
-
Resource-constrained devices have limited memory, power, and transmitting bandwidth. For example, TelosB [37] is an ultra-low-power sensor with a a 16 bit processor and 8 MHz RISC microcontroller with only 10 Kb RAM, 48 Kb program memory, and 1024 Kb flash storage. The required total space for a typical code, such as TinyOS, which is the de facto standard operating system for wireless sensors, is approximately 4 Kb [38]. Therefore, any implemented security algorithm within the network must not be computationally demanding beyond these limitations.
-
Security algorithms must be able to manage unsupervised sensors, which could be exposed to physical attack by demolishing the hardware or to attackers equipping sensors with extra hardware to perform hidden or malicious functions prior to their being deployed in the network area.
-
Determining the adopted broadcast dynamic channel used as a wireless communication medium is challenging, as it is unattended and might be affected by collision and interference issues. WSN communication links are usually based on the 802.15.4 standard, and can be implemented via the use of other technologies as well, such as Bluetooth, ZigBee, PLC, WiFi, 4G, and 5G.
-
The lack of fixed physical infrastructure is a significant design challenge due to the rapidly changing connectivity between nodes.
-
A dynamic underlying network topology results from node failure, deployment of new nodes, possible variations in node position (which is especially the case under harsh environmental conditions), node mobility. The resulting flexibility in terms of link connectivity presents a design challenge for security algorithms, which must be able to adapt to network node variations in order to obtain the extra measure of protection provided by monitoring of corrupted nodes.
-
WSN routing protocols have weaknesses, including malicious routing information injection, alteration, or spoofing, which might lead to network disruptions such as creation of routing loops, broadcasting of fake error messages to partition the network, attracting or repelling network traffic from particular nodes, extending or shortening route paths, and increasing end-to-end latency. These issues are likely to complicate the design of security routing techniques [39].
-
Medium- to large-scale networks of hundreds or thousands of nodes deployed randomly or uniformly throughout the network field presents a challenge when designing security algorithms that are sufficiently flexible to support different security-level requirements.
-
The scalability of WSNs implies handling large amounts of data that may have inconsistent, noisy, erroneous, redundant, and missing values, which requires designing intelligent security approaches that can correctly interpret data to drive intelligent decision-making.
-
Data transmission over multi-hop relaying creates a significant threat, as relays could be eavesdroppers [40], and communicated data may be breached, tampered with, or forged.
-
Time synchronization is an issue, as nodes are independently controlled in the field. Local clocks should be coordinated to avoid synchronization uncertainties, which could cause sensed data to become ambiguous and unreliable.
-
Unexpected and unusual sensor behavior patterns may arise during WSN deployment in unpredictable and hazardous environments, potentially changing the entire historical pattern of the sensed data.
These characteristics render a completely secure WSN system almost impossible to establish, unlike its counterpart networks. The characteristics of WSN systems limit the available security options, including those similar to heavyweight classical security approaches such as spread spectrum, cryptography, and key management at either the device level or the overall network level. These options are demanding in terms of the resources required to protect the network. As existing security solutions for WSNs are insufficient due to these networks’ unique characteristics, it is difficult to create lightweight and effective security mechanisms that can enable optimization of node resource usage while supporting network scalability and without compromising security, allow for a dynamic network topology with different possible configurations and node localization, and integrate heterogeneous hardware and software platforms for sensors to allow them to detect malfunctioning or faulty nodes.
5. Cyberattacks in WSN Contexts
Cyberattacks are the greatest challenge facing communication networks worldwide. The threat of cyberattacks affects any network’s connectivity, availability, reliability, and confidentiality, limiting its efficient use. Mitigating this challenge is essential, especially because the frequency and the nature of attacks have increased tremendously over time [41]. For this reason, cyberattacks targeting WSNs have been the focus of several recent studies in the literature [4,42,43,44,45,46]. Cyberattacks occur when good nodes are communicating over a communication link and intruder or eavesdropper nodes interfere with or disturb that link. This malicious activity usually aims to obtain, alter, or prevent the flow of data within the network using different means; therefore, this activity should be prevented, detected, and mitigated in order to maintain a reliable communication channel [47]. Malicious acts targeting WSNs have been classified in the literature in different ways: the first classification divides attacks into active or passive attacks; the second classification is based on the physical location of the attack relative to the network’s physical position, using this distinction to divide attacks into inside or outside attacks; and the third classification is based on the disrupted stack Open Systems Interconnection (OSI) layer, dividing attacks into physical layer, data link layer, and network layer attacks [42,48].
Active attacks threaten network integrity and reduce availability by continuously attempting to modify the content of the network packets or flooding the victim nodes with surplus packets. The different types of active attacks are based on the underlying stack layer disrupted by the attack, as shown in Figure 4 [42,48]. Attacks such as link jamming, physical tampering, or node replication are hardware-oriented attacks that affect the node’s physical layer. These attacks are more likely to occur when the sensor is exposed to a harsh environment or open to an adversary; therefore, they are unlikely to occur when the sensor node is placed in a secure indoor location. Other attacks, such as collision, exhaustion, and unfairness, are executed against the Media Access Control (MAC) protocol at the data link layer. These attacks cause collisions that result in packet re-transmission; therefore, copies of the same packets must traverse the network, overwhelming the communication channel and wasting limited sensors energy. The most common attacks, such as sinkhole, wormhole, blackhole, selective forwarding (grayhole), ‘Hello’ flooding, sybil, spoofing, and altered or replayed routing information attacks, all interrupt the network layer. These attacks prevent proper packet delivery to the destination through methods such as taking advantage of the multi-hop routing protocol, in which any node routes passing through malicious nodes are unable to deliver packets or are intentionally redirected to incorrect nodes. Examples of attacks impacting the functionality of the transport layer include session hijacking, flooding, and de-synchronization attacks. For example, flooding results in node failure, as the attacker consumes node resources by sending multiple connection requests. Attacks that target the application layer include selective forwarding, deluge, and clock skewing. The most difficult to detect among these attacks is selective forwarding, as the attacker does not block packet forwarding entirely, and only drops or alters some of the received packets from selected nodes. Deluge allows the sensor nodes to be reprogrammed remotely, and clock skewing disrupts those sensors that require synchronization for successful communication. Unlike active attacks, passive attacks do not affect network integrity, instead compromising network confidentiality. These attacks sniff and read unauthorized messages through the communication channels between nodes without disrupting their communication or interrupting network processes. Passive attacks may make the network more vulnerable to other kinds of attacks, such as camouflaged adversaries, physical tampering, eavesdropping, and traffic analysis.
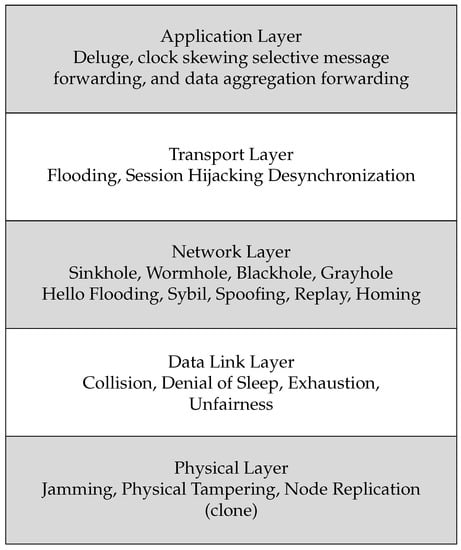
Figure 4. Active attack classification according to OSI stack layer.
Internal attacks are initiated from within the network’s physical boundaries. These attacks control and utilize other network nodes to execute malicious acts. An inside attack can obtain the network transmission key or other network information from the transmitted packets within the network, then use this information to attack the entire network. A typical example of an internal attack is when an attacker takes advantage of a dump security implementation at an unsecured sensor node or a non-updated device’s firmware, which allows the attacker to turn sensing devices into malicious nodes. The attacker then utilizes the node’s network connectivity with other nodes to extract network data using eavesdropping, interfering, or misrouting. External attacks are initiated from beyond the network boundaries; therefore, they cannot obtain network information, such as node identification numbers or transmission keys, making attack recognition easier [48]. In addition, external attackers require powerful wireless transceivers to listen to data packets inside the network in order to accomplish malicious activities such as eavesdropping, replay, injection, and interference. Figure 5 depicts scenarios for external and internal attacks targeting a WSN.
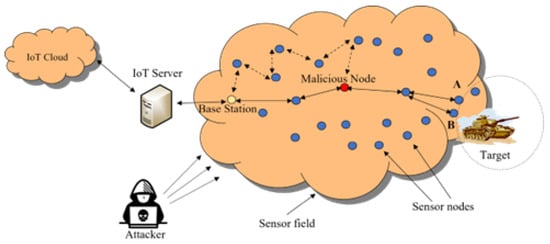
Figure 5. Internal and external cyberattack scenarios in WSN contexts.
In terms of OSI layers, the physical and network layers experience the most threatening attacks. The physical layer possesses a broadcasting channel and a dynamic topology, which allows attackers to easily listen to or sniff the communication channel and establish attacks. While, the network layer has a weak routing protocol that attackers can exploit to execute malicious acts. Another form of attack can be initiated over several WSN stack layers; such attacks across multiple layers include DoS and Man-in-the-middle (MITM) attacks [38]. DoS attacks are numerous, and include jamming and node tampering at the physical layer, collision, exhaustion, denial of sleep, unfairness at the data link layer, homing, blackhole, grayhole, wormhole, sinkhole, spoofing, ‘Hello’ flooding, TDMA scheduling, sybil, and replay attacks at the network layer, as well as flooding and desynchronization at the transport layer [56]. MITM attacks work as a relay between two victims [6]; this type of attack can be passive, where the attacker eavesdrops or intercepts the data traveling on the network between two legitimate nodes without altering the data, such as eavesdropping at the physical layer, or it can be active, where the attacker can delay, drop, or modify the content of a packet, such as a replay attack at the network layer [57].
6. Architecture of WSN vs. Architecture of IDS
Intrusions are similar to attacks in that they aim to disturb the network’s normal operation or obtain access to the network’s information. The IDS is the network’s line of defense, designed to detect violations and tell the controller, or BS, to react appropriately.
6.1. Naive or Flat-Based WSN Architecture for Centralized IDS
In a centralized architecture, better known as a Naive WSN architecture, a central BS collects all the information sensed by all network nodes and forwards the collected information to the cloud IoT server. Similarly, in a centralized IDSs, the BS acts as a global reference that performs computationally demanding tasks to monitor and filter data traffic to facilitate attack detection. Several studies have considered executing the IDS at both the BS level and at the remote server level connected to the IoT cloud, which is called a multi-layer IDS scenario. This approach has multiple limitations, including attack detection latency, considerable communication overhead, and high energy consumption. Latency occurs when data traffic analysis is delayed until the information reaches the BS. Communication overhead is caused by the need to transmit all sensed information to the central BS over the communication link, increasing energy consumption as the node’s distance relative to the central unit increases [58]. Due to these limitations, centralized IDS architectures are typically used only in very small networks.
6.2. Naive or Flat-Based WSN Architecture for Stand-Alone IDS
The opposite philosophy to centralized IDS is stand-alone IDS, which is a node-centric architecture. Each node individually uses an IDS detection model to detect any possible attack locally without needing to exchange any information with the adjacent nodes or a central BS unit. This approach does not exhibit latency when detecting node attacks or introducing communication overhead; however, energy consumption at the node level is higher than in a centralized IDS, and the nodes have lower battery life.
6.3. Naive or Flat-Based WSN Architecture for Distributed or Cooperative IDS
This approach assumes that each node has its own local IDS model to monitor the data traffic, then involves all network nodes in deciding whether an intrusion is present in the network based on the detected indicators. If a locally measured indicator is weak or inconclusive, the involved node can initiate a cooperative global intrusion detection procedure in which all network nodes cooperatively participate in reaching a global decision. Otherwise, if an intrusion is locally detected with sufficient evidence, the involved node can independently alert the rest of the nodes to the presence of a violation in the network. This approach reduces false attack stimulus events, which relate to scenarios in which a violation alarm is triggered even though no real threat is in progress within the network. In this approach, node power consumption is higher and node battery life is lower than the stand-alone IDS due to the an additional optional cooperative procedure.
6.4. Naive or Flat WSN Architecture for Agent-Based IDS
Agent-based IDS involves installing the detection model in a selected subset of sensor nodes, which are called Monitor Nodes (MNs), to reduce the detection overhead faced by the stand-alone and distributed approaches. In tis approach, selected nodes perform detection in addition to their normal sensing, communication, and routing activities in the case of flat WSN architecture. Agents’ tasks are relocated to another predefined subset of nodes after a certain period of time or when performing a specific mission, which improves IDS detection efficiency and increases network lifetime. Agent-based IDS is especially suitable for WSNs, as nodes near the BS can be excluded from communicating all of their samples when developing the reference ML model at the BS because they do not contribute much to the determination of hypersphere of the developed ML model. Agent-based IDS is typically preferred over centralized IDS architecture, especially for networks with geographically dispersed nodes, as in a centralized approach the nodes consume more power when transmitting their data to the central location.
6.5. Hierarchical WSN Architecture for Distributed or Cooperative IDS
A WSN’s hierarchical architecture is a variation of centralized architecture, which can be implemented as cluster-based or tree-based. In a cluster-based architecture all sensor nodes are partitioned into clusters, whereas in a tree-based architecture the nodes are partitioned into trees according to their topographical area. The nodes in a tree-based architecture are organized into a routing tree rooted at the BS. Cluster-based architectures can be static or dynamic. In static clustering the sensors are divided proactively into several clusters at the time of network deployment, while in dynamic clustering the formation of clusters is triggered reactively by detecting the event of interest. In a distributed IDS, the detection model is placed in every sensor network node, allowing nodes to collaborate in order to detect possible intrusions. The clear advantage of implementing a combined hierarchical and distributed architecture is that the communication overhead is significantly lower than in other approaches, as both hierarchical and distributed architectures involve less communication exchange between nodes [58]. A disadvantage of this approach is the need for each network node to have sufficient energy, processing, and storage capacity. Studies have considered using multi-layer instead of distributed IDS, with heterogeneous detection models placed only at the BS and CHs.
7. Types of IDS
IDS-based mechanisms are effective and lightweight solutions for detecting abnormal behavior in WSN sensor nodes. An IDS requires an IDS agent or detector node that analyses the network traffic to detect a abnormal behavior. Intrusion detection at the IDS agent level involves three phases: collection, processing, and action. Network data traffic is collected during a specific time period, then this collected information is processed according to a particular detection mechanism. Detection approaches can be classified as misuse-based, anomaly-based, and specification-based detection. In misuse-based or signature-based detection, the system searches for specific patterns or signatures to identify and detect an intrusion. This approach easily detects known attacks, but cannot detect new or unknown attacks. In specification-based detection, a set of rules or specifications have been set as a reference for normal system operation; any deviation from these specifications triggers an abnormal behavior alert, allowing the system to take proper preventive actions accordingly. This approach has a low false positive rate; however, developing the required specifications is very time-consuming. Anomaly-based detection systems learn the normal behavior profile from normal network traffic and create a reference model accordingly. This model is then used to detect any deviation from the learned pattern or behavior exceeding a certain estimated threshold for use in identifying intrusions [32].
Anomaly-based detection is adaptive, and can detect new and unknown attacks efficiently; however, it has a higher false positive rate compared to previous approaches, as any deviation from the normal behavior profile is considered an attack even though it might be due to normal activity of an unlearned profile or a faulty node producing abnormal activities [15]. Especially in critical infrastructure applications, these types of anomalies are just as harmful as those caused by intruders, and should be identified by the developed reference model [32]. Anomaly-based detection is practical, flexible, computationally feasible, bandwidth (BW) and both spectrally and memory efficient [21]; therefore, it is widely used to secure WSNs. For this reason, the focus of this survey is on anomaly-based detection.
Anomaly-based detection techniques are classified into statistical and ML approaches. The stochastic network behavior in normal conditions is measured during a specific time window and is used to establish a baseline for future detection of patterns that are different from normal traffic [58]. However, the approach continuously generates other reference profiles with a given score for comparison to the reference profile during traffic monitoring. In this approach, the IDS is able to detect an anomalous occurrence if the score is above a certain threshold. On the other hand, ML approaches use classification algorithms to detect intrusions and malicious activities. ML classification algorithms build models capable of classifying packets to distinguish between normal and abnormal packets through training. The model is installed at the sensor level, and can classify upcoming packets after training. The advantage of ML is the ability of models to learn from experience without being explicitly reprogrammed, allowing them to be improved automatically [15,59].
This entry is adapted from the peer-reviewed paper 10.3390/fi15060200
This entry is offline, you can click here to edit this entry!
