Autonomous vehicles (AV) are game-changing innovations that promise a safer, more convenient, and environmentally friendly mode of transportation than traditional vehicles.
- autonomous vehicles
- vehicular technology
- artificial intelligence
- federated learning
- deep learning
- machine learning
- cloud computing
1. Introduction
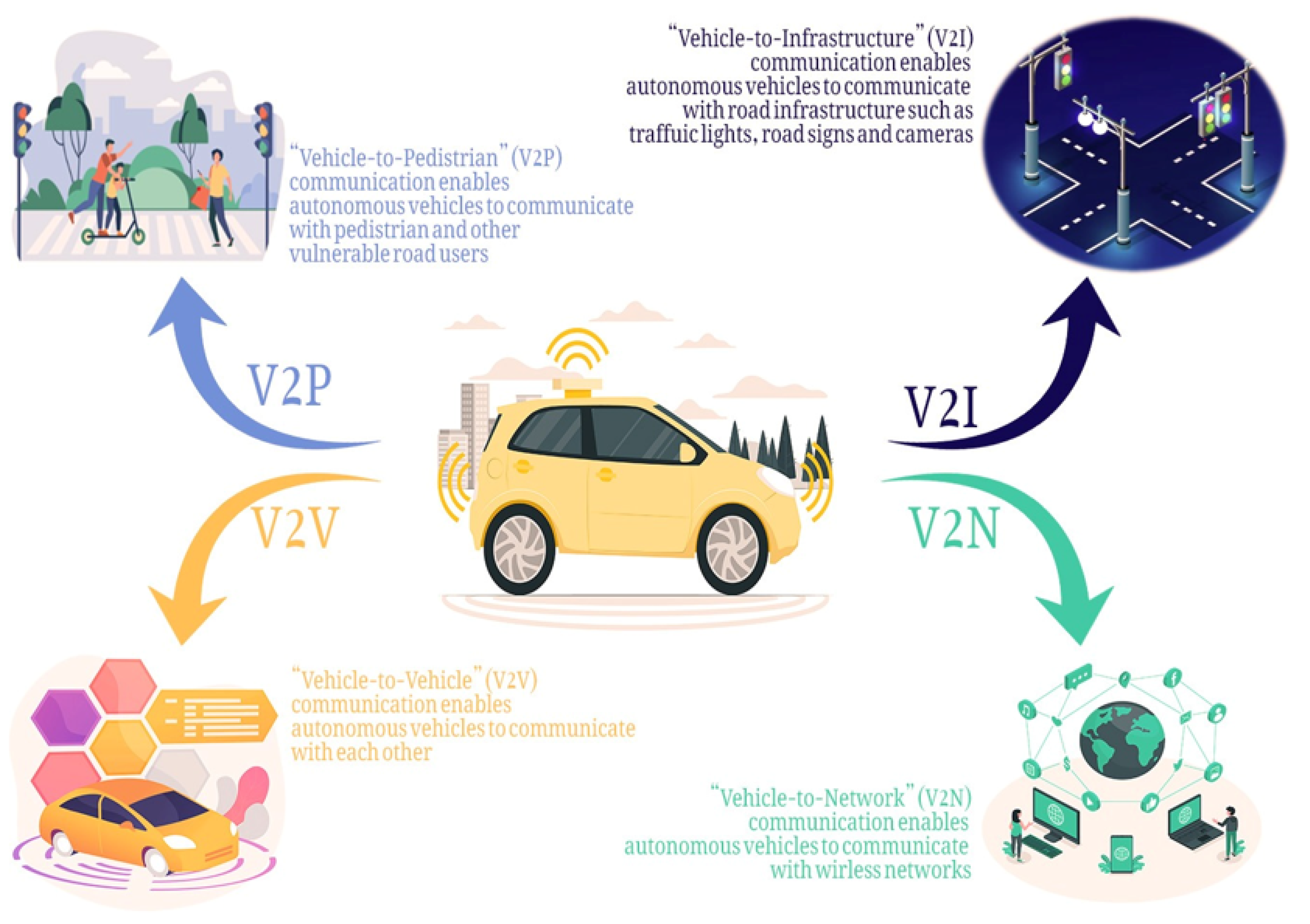
2. Infrastructure and Ad Hoc Autonomous Vehicle
Autonomous vehicles can be classified into two categories based on the usage of infrastructure they use infrastructure-based autonomous vehicles and Ad hoc (infrastructure-less) autonomous vehicles. Infrastructure-based autonomous vehicles rely on physical infrastructure such as roads, traffic signals, and mapping systems. They use Global Positioning System (GPS), LiDAR, RADAR, cameras, and other sensors to navigate, but also require a well-maintained network of roads, signs, and signals to ensure safe and efficient operation [5]. Infrastructure-based autonomous vehicles are autonomous vehicles that rely on physical infrastructure such as roads, traffic signals, and mapping systems to operate. These vehicles use GPS, LiDAR, RADAR, cameras, and other sensors to navigate and make decisions. Still, they also require a well-maintained network of roads, signs, and signals to ensure safe and efficient operation. Some key features and benefits of infrastructure-based autonomous vehicles include [6]:
- 1.
-
Improved Safety: By relying on physical infrastructure, infrastructure-based autonomous vehicles can use safety features such as traffic signals, road markings, and signs to make driving decisions and reduce the risk of accidents.
- 2.
-
Increased Efficiency: Infrastructure-based autonomous vehicles can optimize their routes based on real-time traffic data and use dedicated autonomous vehicle lanes to reduce congestion and improve overall traffic flow.
- 3.
-
Improved User Experience: Infrastructure-based autonomous vehicles can provide a more comfortable and convenient riding experience, using amenities such as rest stops, charging stations, and service facilities along the way. However, there are also some limitations to infrastructure-based autonomous vehicles [7], such as:
- •
-
Cost: Implementing the necessary physical infrastructure can be expensive, and maintaining it can also be a high ongoing cost.
- •
-
Limited Operating Environments: Infrastructure-based autonomous vehicles are limited to operating in areas with well-defined roads and traffic signals and may not be suitable for rural or off-road environments.
- •
-
Dependence on Human Intervention: While infrastructure-based autonomous vehicles can use physical infrastructure to make driving decisions, they may still require human intervention in certain scenarios, such as system failure or road closure.
2.1. Technologies
-
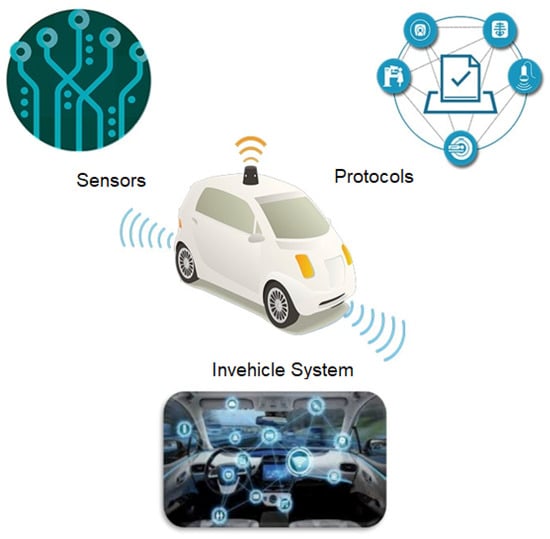
Sensors: To observe and comprehend their environment, autonomous cars use a range of sensors, including cameras, LiDAR, radar, and ultrasonic sensors. These sensors give the vehicle information about its surroundings, such as the location, mobility of other cars, pedestrians, and obstacles [10].
-
Computer Vision: Computer vision algorithms are used to process and analyze the data collected by the vehicle’s sensors. These algorithms help the vehicle to identify and track objects in its environment, as well as to understand their movement and behavior.
-
Artificial Intelligence (AI) and Machine Learning: Algorithms based on machine learning and artificial intelligence are utilized to make choices and direct the vehicle’s activities. For example, they can be used to determine the vehicle’s best path to follow, predict the behavior of other road users, and react to unexpected events.
-
GPS and Maps: GPS and high-definition maps are used to provide the vehicle with information about its location and help it navigate and avoid obstacles [11].
-
Communication Systems: Autonomous vehicles use a variety of communication systems, such as cellular networks, dedicated short-range communication (DSRC), and Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) communication, to exchange information with other vehicles, road infrastructure, and the cloud.
-
Actuation Systems: Autonomous vehicles use actuation systems, such as electric motors, hydraulic actuators, and pneumatic systems, to control the vehicle’s movement and perform tasks such as steering, accelerating, and braking.
-
Power and Energy Management Systems: Autonomous vehicles use power and energy management systems, such as batteries, fuel cells, and regenerative braking, to provide the vehicle with the energy needed to operate and optimize its energy efficiency.
2.2. Routing
-
Traffic Conditions: The vehicle uses real-time traffic data to avoid congested areas and to select the fastest and most efficient route.
-
Road Infrastructure: The vehicle considers the physical layout of the road network, including the presence of intersections, toll booths, and other road features when selecting a route.
-
Obstacles: The vehicle uses its sensors to detect and avoid obstacles, such as other vehicles, pedestrians, and road work that may be present along the route.
-
Safety: The vehicle considers the safety of its passengers and other road users when selecting a route. For example, it may avoid routes with a high incidence of accidents or with poor road conditions.
-
Energy Efficiency: The vehicle considers the energy consumption of different routes and selects the route that minimizes energy usage.
2.3. Data Dissemination
3. Autonomous Vehicles in Smart Cities in a Nutshell
3.1. Public Adoption

3.1.1. Technological Adoption
3.1.2. Consumer Trust
3.1.3. Infrastructure Adoption
3.2. Planning the Driverless City
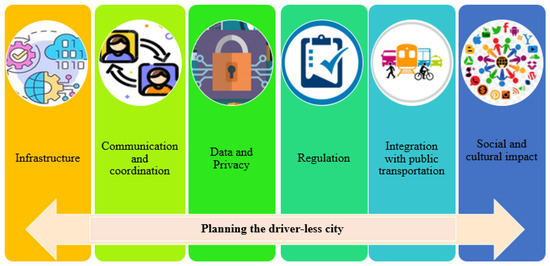
3.2.1. Infrastructure
3.2.2. Communication and Coordination
3.2.3. Data and Privacy
3.2.4. Regulation
3.2.5. Integration with Public Transportation
3.2.6. Social and Cultural Impact
3.3. Traffic Management
3.4. Environmental Impact and Public Health
4. Emerging Technologies
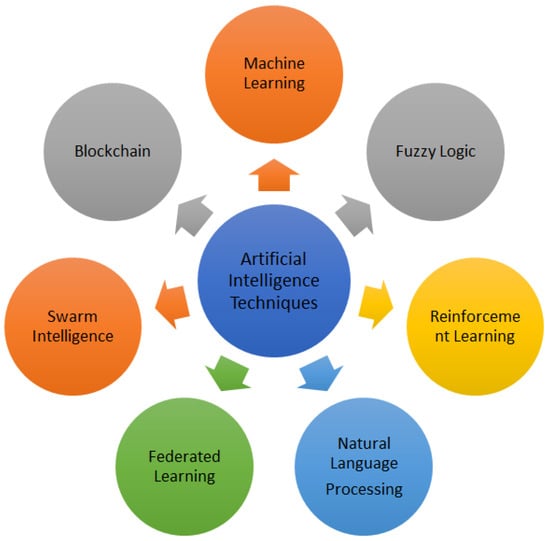
4.1. Artificial Intelligence Techniques
-
Machine learning (ML) is utilized for anomaly detection, route optimization, and traffic prediction [34].
-
Reinforcement learning (RL) is a technique for dynamic route planning and adaptive traffic control.
-
Artificial neural networks (ANN) are used to identify, classify, and communicate about vehicles.
-
Fuzzy logic is used to make safety-critical decisions like emergency braking.
-
The use of genetic algorithms (GA) to improve network communication and energy efficiency.
-
Swarm intelligence—utilized in platooning of vehicles for cooperative communication.
-
Natural language processing (NLP)—utilized for hands-free operation and other human-vehicle interactions. Figure 4 shows the graphical representation of AI techniques.
4.2. Cloud Computing
4.3. Solar Power Electric Vehicles
5. Cyber Attacks and Management
5.1. Cyber Attacks
5.2. Attacks Management
GPS: To prevent GPS-targeted attacks, a variety of defenses have been deployed. For instance, the false signals differ visually from those transmitted by satellites. Attacks that consider the signal’s power, the time between broadcasts, and the signal clock information could be detected using this method [43]. Ref. [44] utilized the receiver’s correlation function distortions to evaluate the GPS signal’s accuracy. Investigate the direction of arrival (DoA), which uses an antenna array to thwart attacks because the DoA of GPS signals would disclose a different carry phase than spoofing signals. Other methods use GPS broadcasts to embed cryptographic algorithms for assault defense. Encrypt GPS L1 P(Y) code to see if a spoofing attempt is being made.
LiDAR: Changing the way LiDAR transmits and receives light is one possible technique. If the adversary intends to carry out the attack effectively, they must coordinate the false laser with the LiDAR laser. Defensive strategies for LiDAR have been shown in Figure 6. The LiDAR laser can prevent an assailant by repeatedly firing laser pulses in one direction, say three times. As LiDAR can only receive lasers from a fixed angle while rotating, limiting the impact of attacks by reducing the receiving angle is possible; however, doing so also lowers LiDAR’s sensitivity.
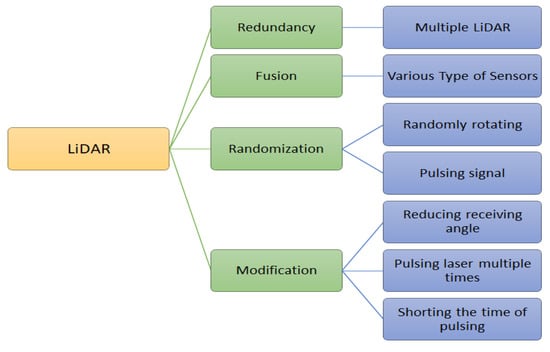
5.2.2. Defence Approaches for In-Vehicle Systems
5.2.3. Defence Approaches for In-Vehicle Protocols
5.3. Traditional Security Devices
5.4. Threat Modeling Approaches
5.5. Authentication Schemes
5.6. Over-The-Air (OTA) Updates
5.7. Zero-Trust Architecture
6. Forensics Approaches
6.1. Forensic Tools
6.2. Forensics Standards for Autonomous Vehicles
6.3. Forensics Challenges in Autonomous Vehicles
7. Simulators
7.1. CARLA
-
A sizable, intricate urban area including streets, buildings, traffic lights, and other elements typical of cities.
-
Realistic lighting and weather conditions, including varying day lengths, seasons, and weather phenomena like snow, rain, and fog [67].
-
Support for various sensors, including LiDAR, radar, and cameras, which may be set up to imitate various sensor kinds and noise levels.
-
A scenario system that is flexible and adaptable, enabling developers to generate and test a variety of situations, including various traffic densities, driving behaviors, and weather conditions.
-
A Python API that makes it simple for developers to build custom agents and behaviors and control and interact with the simulation [68].
-
Support for the Open DRIVE format enables simulation developers to import actual road networks.
-
Support for the Unreal Engine enables physics-based interactions between agents and realistic graphics.
7.2. Apollo
-
The Apollo Simulator is a physics-based, highly realistic simulator that may be used to test and create autonomous vehicle systems. It supports several sensors, including LiDAR, radar, and cameras, and contains a variety of realistic landscapes [69].
-
Perception is a module collection that analyzes sensor data and identifies environmental items such as lane markers, traffic lights, and other cars.
-
Planning is a collection of modules for creating plans for the vehicle’s motion, such as trajectory and path planning.
-
Control, A group of modules that carry out instructions and manage the vehicle’s motion, including low-level steering, throttle, and braking controllers [70].
-
HD Map is a high-definition map that can give the car precise information about its surroundings, such as the road’s geometry, lane markings, and traffic lights.
-
Cybersecurity is a collection of modules to protect autonomous vehicle systems against cyberattacks.
-
Cloud-based services is a group of cloud-based services that can be used to remotely access the car and store and exchange data [19].
7.3. AirSim
-
Realistic settings is an AirSim that offers a range of settings, such as urban, rural, and natural settings, which can be utilized to assess the effectiveness of autonomous systems in various contexts [71].
-
AirSim supports cameras, LiDAR, and GPS sensors, which can be set up to simulate various sensor kinds and noise levels.
-
Interactions that are based on physics: AirSim models the physics of flight, including wind, turbulence, and other elements that may have an impact on how well aerial vehicles perform.
-
AirSim enables programmers to design and test various scenarios, including weather, illumination, and traffic density conditions [72].
-
AirSim offers a Python API that makes it simple for developers to build, manage, and interact with the simulation [73].
-
AirSim allows testing of fleet-based or swarm-based systems by simulating many vehicles simultaneously.
7.4. Gazebo
-
Gazebo models 3D physics-based simulations such as robotic system dynamics, including the impact of gravity, friction, and collisions.
-
It features a range of settings, including urban, rural, and natural ones, which can be used to assess how well robotic systems function in various contexts [74].
-
It features support for cameras, LiDAR, and GPS sensors, which may be customized to imitate a variety of sensor kinds and noise levels.
-
With Gazebo, developers can design and test a variety of situations, such as those with varying weather, lighting, and traffic volumes.
-
It has C++, Python, and MATLAB APIs that make it simple for developers to build, manage, and interact with the simulation [75].
-
Simulating numerous robots at once is supported by Gazebo, which makes it possible to test swarm- or fleet-based systems.
-
Gazebo offers a plugin architecture that enables programmers to design unique plugins to provide new features or alter the simulation’s behavior.
7.5. SUMO
-
SUMO replicates individual vehicle movement on the road network while considering traffic lights, signs, and other traffic regulations.
-
It contains a range of settings, such as urban, suburban, and rural settings, which can be utilized to test the effectiveness of traffic systems in various contexts [76].
-
Simulating a wide range of traffic scenarios with support for diverse vehicle kinds, traffic densities, and traffic patterns is possible with SUMO.
-
It offers C++, Python, and Java APIs that make it simple for developers to build, manage, and interact with the simulation [77].
-
It is capable of simulating a variety of forms of transportation, including trains, buses, bicycles, and pedestrians, in addition to automobiles and buses.
-
SUMO has a plugin architecture that enables programmers to build unique plugins to include new features or alter the simulation’s behavior.
8. International Standards and Guidelines
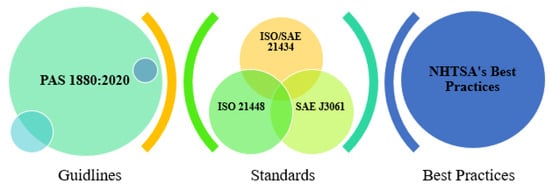
8.1. Guidelines for Improving AVs Security
-
Protect the software and hardware components by ensuring that every piece of hardware and software has been properly tested for vulnerabilities and developed with security in mind.
-
Encrypt all data: To avoid unauthorized access or theft, any data sent through the vehicle or kept there should be encrypted.
-
Watch over and restrict access: Establish rigorous access restrictions and keep a close eye on all communications going to and coming from the vehicle. Update software frequently: Update the software frequently to repair flaws and enhance security features.
-
Implement cybersecurity measures: To identify and stop cyberattacks, employ cybersecurity measures such as firewalls and intrusion detection systems [82].
-
Conduct penetration testing: To find and fix system vulnerabilities, conduct penetration testing regularly.
-
Plan for response and recovery: Create a thorough response strategy that addresses reporting events and restoring systems during a security breach.
-
Users should be informed about the value of security and the best practices for operating the vehicle safely and securely.
8.2. Guidelines for End Users
-
Before using the vehicle, familiarize yourself with the operating instructions and safety precautions by reading the manual.
-
Recognize the vehicle’s limitations: Autonomous vehicles are not fault-proof and are still susceptible to errors. Be conscious of the vehicle’s capabilities and limitations at all times.
-
Know when to take control: In some circumstances, autonomous vehicles may ask you to take the wheel. Knowing when and how to drive safely while doing so is crucial [83].
-
Always buckles up: Even if you are not driving, buckle up when you ride in an autonomous car.
-
Update the vehicle’s software frequently to guarantee that you have access to the most recent security and safety features.
-
Avoid attempting to modify or meddle with the vehicle’s systems because doing so could harm the vehicle’s performance and safety [82].
-
Inform the manufacturer or your local authorities immediately if you experience any problems or issues with the car.
-
Prepare for crises by becoming familiar with your vehicle’s emergency protocols and being ready to act if necessary [84].
9. Conclusions
This entry is adapted from the peer-reviewed paper 10.3390/technologies11050117
References
- Kim, S.; Shrestha, R. Security and Privacy in Intelligent Autonomous Vehicles. In Automotive Cyber Security; Springer: Berlin/Heidelberg, Germany, 2020; pp. 35–66.
- Saab, S.S.; Shen, D.; Orabi, M.; Kors, D.; Jaafar, R.H. Iterative learning control: Practical implementation and automation. IEEE Trans. Ind. Electron. 2021, 69, 1858–1866.
- Anita, E.M.; Jenefa, J. A survey on authentication schemes of VANETs. In Proceedings of the 2016 International Conference on Information Communication and Embedded Systems (ICICES), Chennai, India, 25–26 February 2016; pp. 1–7.
- Cui, J.; Liew, L.S.; Sabaliauskaite, G.; Zhou, F. A review on safety failures, security attacks, and available countermeasures for autonomous vehicles. Ad Hoc Netw. 2019, 90, 101823.
- Wuthishuwong, C.; Traechtler, A. Vehicle to infrastructure based safe trajectory planning for Autonomous Intersection Management. In Proceedings of the 2013 13th international conference on ITS telecommunications (ITST), Tampere, Finland, 5–7 November 2013; pp. 175–180.
- Agrawal, S.; Elger, G. Concept of infrastructure based environment perception for in2lab test field for automated driving. In Proceedings of the 2021 IEEE International Smart Cities Conference (ISC2), Manchester, UK, 7–10 September 2021; pp. 1–4.
- Liu, S.; Yu, B.; Tang, J.; Zhu, Y.; Liu, X. Communication challenges in infrastructure-vehicle cooperative autonomous driving: A field deployment perspective. IEEE Wirel. Commun. 2022, 29, 126–131.
- Akabane, A.T.; Immich, R.; Bittencourt, L.F.; Madeira, E.R.; Villas, L.A. Towards a distributed and infrastructure-less vehicular traffic management system. Comput. Commun. 2020, 151, 306–319.
- Lim, K.; Tuladhar, K.M. LIDAR: Lidar information based dynamic V2V authentication for roadside infrastructure-less vehicular networks. In Proceedings of the 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–6.
- Campbell, S.; O’Mahony, N.; Krpalcova, L.; Riordan, D.; Walsh, J.; Murphy, A.; Ryan, C. Sensor technology in autonomous vehicles: A review. In Proceedings of the 2018 29th Irish Signals and Systems Conference (ISSC), Belfast, UK, 21–22 June 2018; pp. 1–4.
- Olaverri-Monreal, C. Autonomous vehicles and smart mobility related technologies. Infocommun. J. 2016, 8, 17–24.
- Rossi, F.; Zhang, R.; Hindy, Y.; Pavone, M. Routing autonomous vehicles in congested transportation networks: Structural properties and coordination algorithms. Auton. Robot. 2018, 42, 1427–1442.
- Abbas, A.; Krichen, M.; Alroobaea, R.; Malebary, S.; Tariq, U.; Jalil Piran, M. An opportunistic data dissemination for autonomous vehicles communication. Soft Comput. 2021, 25, 11899–11912.
- Ahmed, M.L.; Iqbal, R.; Karyotis, C.; Palade, V.; Amin, S.A. Predicting the public adoption of connected and autonomous vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 23, 1680–1688.
- Acheampong, R.A.; Cugurullo, F. Capturing the behavioural determinants behind the adoption of autonomous vehicles: Conceptual frameworks and measurement models to predict public transport, sharing and ownership trends of self-driving cars. Transp. Res. Part F Traffic Psychol. Behav. 2019, 62, 349–375.
- Golbabaei, F.; Yigitcanlar, T.; Paz, A.; Bunker, J. Individual predictors of autonomous vehicle public acceptance and intention to use: A systematic review of the literature. J. Open Innov. Technol. Mark. Complex. 2020, 6, 106.
- Lavasani, M.; Jin, X.; Du, Y. Market penetration model for autonomous vehicles on the basis of earlier technology adoption experience. Transp. Res. Rec. 2016, 2597, 67–74.
- Choi, J.K.; Ji, Y.G. Investigating the importance of trust on adopting an autonomous vehicle. Int. J. Hum.-Comput. Interact. 2015, 31, 692–702.
- Garcia, D.; Kreutzer, C.; Badillo-Urquiola, K.; Mouloua, M. Measuring trust of autonomous vehicles: A development and validation study. In Proceedings of the HCI International 2015-Posters’ Extended Abstracts: International Conference, HCI International 2015, Los Angeles, CA, USA, 2–7 August 2015; Proceedings, Part II 17. Springer: Berlin/Heidelberg, Germany, 2015; pp. 610–615.
- Dirsehan, T.; Can, C. Examination of trust and sustainability concerns in autonomous vehicle adoption. Technol. Soc. 2020, 63, 101361.
- Legacy, C.; Ashmore, D.; Scheurer, J.; Stone, J.; Curtis, C. Planning the driverless city. Transp. Rev. 2019, 39, 84–102.
- Shatu, F.; Kamruzzaman, M. Planning for active transport in driverless cities: A conceptual framework and research agenda. J. Transp. Health 2022, 25, 101364.
- Fox, S.J. Planning for density in a driverless world. NEULJ 2017, 9, 151.
- González-González, E.; Cordera, R.; Stead, D.; Nogués, S. Envisioning the driverless city using backcasting and Q-methodology. Cities 2023, 133, 104159.
- Wagner, P. Traffic control and traffic management in a transportation system with autonomous vehicles. Auton. Driving Tech. Leg. Soc. Asp. 2016, 301–316.
- Gora, P. Simulation-based traffic management system for connected and autonomous vehicles. In Road Vehicle Automation 4; Springer: Berlin/Heidelberg, Germany, 2018; pp. 257–266.
- Kopelias, P.; Demiridi, E.; Vogiatzis, K.; Skabardonis, A.; Zafiropoulou, V. Connected & autonomous vehicles–Environmental impacts–A review. Sci. Total Environ. 2020, 712, 135237.
- Rojas-Rueda, D.; Nieuwenhuijsen, M.; Khreis, H. Autonomous vehicles and public health: Literature review. J. Transp. Health 2017, 5, S13.
- Basma, H.; Halaby, H.; Radwan, A.B.; Mansour, C. Design of optimal rule-based controller for plug-in series hybrid electric vehicle. In Proceedings of the 32nd International Conference on Efficiency, Cost, Optimization, Simulation and Environmental Impact of Energy Systems, Wroclaw, Poland, 23–28 June 2019.
- Kontar, W.; Ahn, S.; Hicks, A. Autonomous vehicle adoption: Use phase environmental implications. Environ. Res. Lett. 2021, 16, 064010.
- Khoury, J.; Khoury, J.; Zouein, G.; Arnaout, J.P. A practical decentralized access protocol for autonomous vehicles at isolated under-saturated intersections. J. Intell. Transp. Syst. 2019, 23, 427–440.
- Rojas-Rueda, D.; Nieuwenhuijsen, M.J.; Khreis, H.; Frumkin, H. Autonomous vehicles and public health. Annu. Rev. Public Health 2020, 41, 329–345.
- Mchergui, A.; Moulahi, T.; Zeadally, S. Survey on artificial intelligence (AI) techniques for vehicular ad hoc networks (VANETs). Veh. Commun. 2022, 34, 100403.
- Javed, A.R.; Usman, M.; Rehman, S.U.; Khan, M.U.; Haghighi, M.S. Anomaly detection in automated vehicles using multistage attention-based convolutional neural network. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4291–4300.
- Yaqoob, I.; Khan, L.U.; Kazmi, S.A.; Imran, M.; Guizani, N.; Hong, C.S. Autonomous driving cars in smart cities: Recent advances, requirements, and challenges. IEEE Netw. 2019, 34, 174–181.
- Liu, S.; Liu, L.; Tang, J.; Yu, B.; Wang, Y.; Shi, W. Edge computing for autonomous driving: Opportunities and challenges. Proc. IEEE 2019, 107, 1697–1716.
- Masood, A.; Lakew, D.S.; Cho, S. Security and privacy challenges in connected vehicular cloud computing. IEEE Commun. Surv. Tutor. 2020, 22, 2725–2764.
- Xia, X.; Meng, Z.; Han, X.; Li, H.; Tsukiji, T.; Xu, R.; Zheng, Z.; Ma, J. An Automated Driving Systems Data Acquisition and Analytics Platform. Transp. Res. Part C Emerg. Technol. 2023, 151, 104120.
- Meng, Z.; Xia, X.; Xu, R.; Liu, W.; Ma, J. Hydro-3D: Hybrid Object Detection and Tracking for Cooperative Perception Using 3D Lidar. IEEE Trans. Intell. Veh. 2023.
- Sami, H.; Mourad, A.; Otrok, H.; Bentahar, J. Fscaler: Automatic resource scaling of containers in fog clusters using reinforcement learning. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020; pp. 1824–1829.
- Shahzad, A.; Gherbi, A.; Zhang, K. Enabling Fog–Blockchain Computing for Autonomous-Vehicle-Parking System: A Solution to Reinforce IoT–Cloud Platform for Future Smart Parking. Sensors 2022, 22, 4849.
- Javed, A.R.; Hassan, M.A.; Shahzad, F.; Ahmed, W.; Singh, S.; Baker, T.; Gadekallu, T.R. Integration of blockchain technology and federated learning in vehicular (iot) networks: A comprehensive survey. Sensors 2022, 22, 4394.
- Psiaki, M.L.; Powell, S.P.; O’Hanlon, B.W. GNSS spoofing detection using high-frequency antenna motion and carrier-phase data. In Proceedings of the 26th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2013), Nashville, TN, USA, 16–20 September 2013; pp. 2949–2991.
- Wesson, K.D.; Gross, J.N.; Humphreys, T.E.; Evans, B.L. GNSS signal authentication via power and distortion monitoring. IEEE Trans. Aerosp. Electron. Syst. 2017, 54, 739–754.
- Lim, K.; Islam, T.; Kim, H.; Joung, J. A Sybil attack detection scheme based on ADAS sensors for vehicular networks. In Proceedings of the 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; pp. 1–5.
- Zhou, M.; Qin, Z.; Lin, X.; Hu, S.; Wang, Q.; Ren, K. Hidden voice commands: Attacks and defenses on the VCS of autonomous driving cars. IEEE Wirel. Commun. 2019, 26, 128–133.
- Cao, Y.; Xiao, C.; Cyr, B.; Zhou, Y.; Park, W.; Rampazzi, S.; Chen, Q.A.; Fu, K.; Mao, Z.M. Adversarial sensor attack on lidar-based perception in autonomous driving. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 2267–2281.
- Sheehan, B.; Murphy, F.; Mullins, M.; Ryan, C. Connected and autonomous vehicles: A cyber-risk classification framework. Transp. Res. Part A Policy Pract. 2019, 124, 523–536.
- Saber, O.; Mazri, T. Security of Autonomous Vehicles: 5g Iov (internet of Vehicles) Environment. Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2022, 48, 157–163.
- Hasan, M.K.; Islam, S.; Gadekallu, T.R.; Ismail, A.F.; Amanlou, S.; Abdullah, S.N.H.S. Novel EBBDSA based Resource Allocation Technique for Interference Mitigation in 5G Heterogeneous Network. Comput. Commun. 2023, 209, 320–330.
- Sajid, F.; Javed, A.R.; Basharat, A.; Kryvinska, N.; Afzal, A.; Rizwan, M. An efficient deep learning framework for distracted driver detection. IEEE Access 2021, 9, 169270–169280.
- Ma, Z.; Schmittner, C. Threat modeling for automotive security analysis. Adv. Sci. Technol. Lett. 2016, 139, 333–339.
- Mohammed, A.Z.; Man, Y.; Gerdes, R.; Li, M.; Celik, Z.B. Physical layer data manipulation attacks on the can bus. In Proceedings of the Intl. Workshop on Automotive and Autonomous Vehicle Security (AutoSec), Online, 24–28 April 2022.
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.H.; Kim, H.K. Cybersecurity for autonomous vehicles: Review of attacks and defense. Comput. Secur. 2021, 103, 102150.
- Manvi, S.S.; Tangade, S. A survey on authentication schemes in VANETs for secured communication. Veh. Commun. 2017, 9, 19–30.
- Du, X.; Htet, K.K.K.; Tan, K.K. Development of a genetic-algorithm-based nonlinear model predictive control scheme on velocity and steering of autonomous vehicles. IEEE Trans. Ind. Electron. 2016, 63, 6970–6977.
- Khatun, M.; Glaß, M.; Jung, R. An approach of scenario-based threat analysis and risk assessment over-the-air updates for an autonomous vehicle. In Proceedings of the 2021 7th International Conference on Automation, Robotics and Applications (ICARA), Prague, Czech Republic, 4–6 February 2021; pp. 122–127.
- Qureshi, A.; Marvi, M.; Shamsi, J.A.; Aijaz, A. eUF: A framework for detecting over-the-air malicious updates in autonomous vehicles. J. King Saud-Univ.-Comput. Inf. Sci. 2021, 34, 5456–5467.
- Kondaveety, V.B.; Lamkuche, H.; Prasad, S. A zero trust architecture for next generation automobiles. AIP Conf. Proc. 2022, 2519, 030088.
- Alipour, M.A.; Ghasemshirazi, S.; Shirvani, G. Enabling a Zero Trust Architecture in a 5G-enabled Smart Grid. arXiv 2022, arXiv:2210.01739.
- Lian, Z.; Zeng, Q.; Wang, W.; Gadekallu, T.R.; Su, C. Blockchain-based two-stage federated learning with non-IID data in IoMT system. IEEE Trans. Comput. Soc. Syst. 2022, 10, 1701–1710.
- Alexakos, C.; Katsini, C.; Votis, K.; Lalas, A.; Tzovaras, D.; Serpanos, D. Enabling digital forensics readiness for internet of vehicles. Transp. Res. Procedia 2021, 52, 339–346.
- Yang, G.; Xue, Y.; Meng, L.; Wang, P.; Shi, Y.; Yang, Q.; Dong, Q. Survey on autonomous vehicle simulation platforms. In Proceedings of the 2021 8th International Conference on Dependable Systems and Their Applications (DSA), Yinchuan, China, 5–6 August 2021; pp. 692–699.
- Elyas, M.; Maynard, S.B.; Ahmad, A.; Lonie, A. Towards a systemic framework for digital forensic readiness. J. Comput. Inf. Syst. 2014, 54, 97–105.
- Sun, Y.; Wu, L.; Wu, S.; Li, S.; Zhang, T.; Zhang, L.; Xu, J.; Xiong, Y.; Cui, X. Attacks and countermeasures in the internet of vehicles. Ann. Telecommun. 2017, 72, 283–295.
- Sharma, P.; Gillanders, J. Cybersecurity and Forensics in Connected Autonomous Vehicles: A Review of the State-of-the-Art. IEEE Access 2022, 10, 108979–108996.
- Vivan, G.P.; Goberville, N.; Asher, Z.D.; Brown, N.; Rojas, J.F. No Cost Autonomous Vehicle Advancements in CARLA through ROS; SAE International: Warrendale, PA, USA, 2021.
- Pérez-Gil, Ó.; Barea, R.; López-Guillén, E.; Bergasa, L.M.; Gomez-Huelamo, C.; Gutiérrez, R.; Diaz-Diaz, A. Deep reinforcement learning based control for Autonomous Vehicles in CARLA. Multimed. Tools Appl. 2022, 81, 3553–3576.
- Bojarski, M.; Del Testa, D.; Dworakowski, D.; Firner, B.; Flepp, B.; Goyal, P.; Zhang, X. End to end learning for self-driving cars. arXiv 2016, arXiv:1604.07316.
- Dai, F.; Chen, M.; Wei, X.; Wang, H. Swarm intelligence-inspired autonomous flocking control in UAV networks. IEEE Access 2019, 7, 61786–61796.
- Shah, S.; Dey, D.; Lovett, C.; Kapoor, A. Airsim: High-fidelity visual and physical simulation for autonomous vehicles. In Proceedings of the Field and Service Robotics: Results of the 11th International Conference; Springer: Berlin/Heidelberg, Germany, 2018; pp. 621–635.
- Bondi, E.; Dey, D.; Kapoor, A.; Piavis, J.; Shah, S.; Fang, F.; Dilkina, B.; Hannaford, R.; Iyer, A.; Joppa, L.; et al. Airsim-w: A simulation environment for wildlife conservation with uavs. In Proceedings of the 1st ACM SIGCAS Conference on Computing and Sustainable Societies, Menlo Park and San Jose, CA, USA, 20–22 June 2018; pp. 1–12.
- Yao, S.; Zhang, J.; Hu, Z.; Wang, Y.; Zhou, X. Autonomous-driving vehicle test technology based on virtual reality. J. Eng. 2018, 2018, 1768–1771.
- Koenig, N.; Howard, A. Design and use paradigms for gazebo, an open-source multi-robot simulator. In Proceedings of the 2004 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS)(IEEE Cat. No. 04CH37566), Sendai, Japan, 28 September–2 October 2004; Volume 3, pp. 2149–2154.
- Furrer, F.; Burri, M.; Achtelik, M.; Siegwart, R. Rotors—a modular gazebo mav simulator framework. Robot. Oper. Syst. (Ros) Complet. Ref. 2016, 1, 595–625.
- Krajzewicz, D. Traffic simulation with SUMO–simulation of urban mobility. Fundam. Traffic Simul. 2010, 145, 269–293.
- Krajzewicz, D.; Erdmann, J.; Behrisch, M.; Bieker, L. Recent development and applications of SUMO-Simulation of Urban MObility. Int. J. Adv. Syst. Meas. 2012, 5.
- Schmittner, C.; Griessnig, G.; Ma, Z. Status of the Development of ISO/SAE 21434. In Proceedings of the Systems, Software and Services Process Improvement: 25th European Conference, EuroSPI 2018, Bilbao, Spain, 5–7 September 2018; Proceedings 25. Springer: Berlin/Heidelberg, Germany, 2018; pp. 504–513.
- Martin, J.; Carter, A. Nhtsa cybersecurity research. In Proceedings of the 25th International Technical Conference on the Enhanced Safety of Vehicles (ESV) National Highway Traffic Safety Administration, Washington, DC, USA, 5 June 2017.
- Schmittner, C.; Ma, Z.; Reyes, C.; Dillinger, O.; Puschner, P. Using SAE J3061 for automotive security requirement engineering. In Proceedings of the Computer Safety, Reliability, and Security: SAFECOMP 2016 Workshops, ASSURE, DECSoS, SASSUR, and TIPS, Trondheim, Norway, 20 September 2016; Proceedings 35. Springer: Berlin/Heidelberg, Germany, 2016; pp. 157–170.
- Udayakumar, P. Manage and Secure AVS. In Design and Deploy Azure VMware Solutions: Build and Run VMware Workloads Natively on Microsoft Azure; Springer: Berlin/Heidelberg, Germany, 2022; pp. 341–387.
- Anderson, J.M.; Nidhi, K.; Stanley, K.D.; Sorensen, P.; Samaras, C.; Oluwatola, O.A. Autonomous Vehicle Technology: A Guide for Policymakers; Rand Corporation: Santa Monica, CA, USA, 2014.
- Abu Bakar, A.I.; Abas, M.A.; Muhamad Said, M.F.; Tengku Azhar, T.A. Synthesis of autonomous vehicle guideline for public road-testing sustainability. Sustainability 2022, 14, 1456.
- Mohsin, A.H.; Zaidan, A.; Zaidan, B.; Albahri, O.; Ariffin, S.A.B.; Alemran, A.; Enaizan, O.; Shareef, A.H.; Jasim, A.N.; Jalood, N.; et al. Finger vein biometrics: Taxonomy analysis, open challenges, future directions, and recommended solution for decentralised network architectures. IEEE Access 2020, 8, 9821–9845.
