Due to the excellent compression performance of JPEG, many schemes based on JPEG have been developed for the encryption and compression of digital images. According to the positioning of the encryption within the compression process, they can be classified into three categories: encryption before compression, joint compression and encryption, and compression before encryption. Encryption before compression means that the image is encrypted before JPEG compression. Typical methods include permutation encryption and some chaos-based encryption schemes that directly operate on the original image
- remote sensing image transmission
- image encryption
- JPEG
1. Introduction
Image encryption is an important method to ensure the security of image transmission. Currently, a wide range of image encryption methods have been developed and are available. These methods use various encryption technologies to ensure security and privacy, such as multimedia scrambling [1], wave perturbation [2], reversible cellular automata [3], bitplane-based image encryption [4], and chaos-based image encryption algorithms [5][6][7][8]. These image encryption algorithms can transform the original image into an incomprehensible distortion form, ensuring the security of the image during storage and transmission. However, with the continuous growth of the size of image files, the method of directly encrypting images will consume extensive computing resources. This problem will become more obvious when encrypting remote sensing images because of their larger amount of data. Since the countries along the “Belt and Road” are developing countries with limited computing resources, it is necessary to design a joint encryption and compression scheme to reduce the computational burden of these countries.
2. Encryption and Compression Schemes Based on JPEG
2.1. JPEG
2.1.1. Preprocessing
2.1.2. Discrete Cosine Transform, Quantization, and Zigzag Scanning
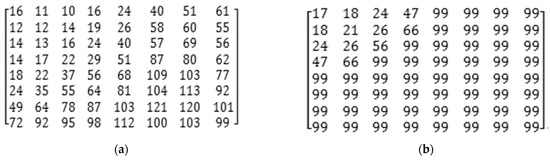
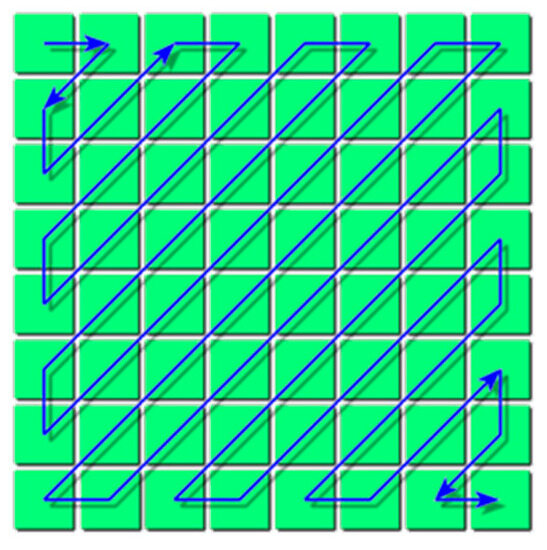
2.1.3. Entropy Encoding
2.2. Encryption and Compression Schemes Based on JPEG
This entry is adapted from the peer-reviewed paper 10.3390/s23177600
References
- Li, C.; Lin, D.; Feng, B.; Lu, J.; Hao, F. Cryptanalysis of a Chaotic Image Encryption Algorithm Based on Information Entropy. IEEE Access 2018, 6, 75834–75842.
- Wu, Y.; Zhou, Y.; Agaian, S.; Noonan, J.P. A symmetric image cipher using wave perturbations. Signal Process. 2014, 102, 122–131.
- Wang, X.; Luan, D. A novel image encryption algorithm using chaos and reversible cellular automata. Commun. Nonlinear Sci. Numer. Simul. 2013, 18, 3075–3085.
- Cao, W.; Zhou, Y.; Chen, C.L.P.; Xia, L. Medical image encryption using edge maps. Signal Process. 2017, 132, 96–109.
- Zhu, H.; Zhao, Y.; Song, Y. 2D Logistic-modulated-Sine-coupling-Logistic chaotic map For Image Encryption. IEEE Access 2019, 7, 14081–14098.
- Zhu, H.; Qi, W.; Ge, J.; Liu, Y. Analyzing Devaney Chaos of a Sine–Cosine Compound Function System. Int. J. Bifurc. Chaos 2018, 28, 1850176.
- Zhu, H.; Zhang, X.; Yu, H.; Zhao, C.; Zhu, Z. An image encryption algorithm based on compound homogeneous hyper-chaotic system. Nonlinear Dyn. 2017, 89, 61–79.
- Hanif, M.; Iqbal, N.; Ur Rahman, F.; Khan, M.A.; Ghazal, T.M.; Abbas, S.; Ahmad, M.; Al Hamadi, H.; Yeun, C.Y. A Novel Grayscale Image Encryption Scheme Based on the Block-Level Swapping of Pixels and the Chaotic System. Sensors 2022, 22, 6243.
- Zhou, J.; Liu, X.; Au, O.C. On the design of an efficient encryption-then-compression system. In Proceedings of the 2013 IEEE International Conference on Acoustics, Speech and Signal Processing, Vancouver, BC, Canada, 26–31 May 2013; pp. 2872–2876.
- Wallace, G.K. The JPEG still picture compression standard. Commun. ACM 1991, 34, 30–44.
- He, J.; Huang, S.; Tang, S.; Huang, J. JPEG Image Encryption with Improved Format Compatibility and File Size Preservation. IEEE Trans. Multimedia 2018, 20, 2645–2658.
- Li, P.; Lo, K.T. Survey on JPEG compatible joint image compression and encryption algorithms. IET Signal Process. 2020, 14, 475–488.
- Gan, Z.; Chai, X.; Han, D.; Chen, Y. A chaotic image encryption algorithm based on 3-D bit-plane permutation. Neural Comput. Appl. 2018, 31, 7111–7130.
- Chai, X.; Gan, Z.; Yuan, K.; Chen, Y.; Liu, X. A novel image encryption scheme based on DNA sequence operations and chaotic systems. Neural Comput. Appl. 2019, 31, 219–237.
- Kurihara, K.; Shiota, S.; Kiya, H. An encryption-then-compression system for JPEG standard. In Proceedings of the 2015 Picture Coding Symposium (PCS), Cairns, Australia, 31 May–3 June 2015; pp. 119–123.
- Chuman, T.; Sirichotedumrong, W.; Kiya, H. Encryption-then-Compression Systems using Grayscale-based Image Encryption for JPEG Images. IEEE Trans. Inf. Forensics Secur. 2018, 14, 1515–1525.
- Korshunov, P.; Ebrahimi, T. Scrambling-based tool for secure protection of JPEG images. In Proceedings of the IEEE International Conference on Image Processing (ICIP), Paris, France, 27–30 October 2014; pp. 3423–3425.
- Li, S.; Zhang, Y. Quantized DCT coefficient category address encryption for JPEG image. KSII Trans. Internet Inf. Syst. (TIIS) 2016, 10, 1790–1806.
- Puteaux, P.; Wang, Z.; Zhang, X.; Puech, W. Hierarchical High Capacity Data Hiding in JPEG Crypto-compressed Images. In Proceedings of the 2020 28th European Signal Processing Conference (EUSIPCO), Amsterdam, The Netherlands, 18–21 January 2021; pp. 725–729.
- Ong, S.; Wong, K.; Qi, X.; Tanaka, K. Beyond format-compliant encryption for JPEG image. Signal Process. Image Commun. 2015, 31, 47–60.
- Qian, Z.; Zhou, H.; Zhang, X.; Zhang, W. Separable Reversible Data Hiding in Encrypted JPEG Bitstreams. IEEE Trans. Dependable Secur. Comput. 2016, 15, 1055–1067.
- Liang, H.; Zhang, X.; Cheng, H. Huffman-code based retrieval for encrypted JPEG images. J. Vis. Commun. Image Represent. 2019, 61, 149–156.
- He, K.; Bidan, C.; Le Guelvouit, G.; Feron, C. Robust and secure image encryption schemes during JPEG compression process. Electron. Imaging 2016, 28, 1–7.
- Cheng, H.; Zhang, X.; Yu, J.; Zhang, Y. Encrypted JPEG image retrieval using block-wise feature comparison. J. Vis. Commun. Image Represent. 2016, 40, 111–117.
- Zhang, D.; Zhang, F. Chaotic encryption and decryption of JPEG image. Opt. —Int. J. Light Electron Opt. 2014, 125, 717–720.
- Zhang, X.; Cheng, H. Histogram-based retrieval for encrypted JPEG images. In Proceedings of the 2014 IEEE China Summit & International Conference on Signal and Information Processing (ChinaSIP), Xi’an, China, 9–13 July 2014; pp. 446–449.
- Socek, D.; Kalva, H.; Magliveras, S.S.; Marques, O.; Culibrk, D.; Furht, B. New approaches to encryption and steganography for digital videos. Multimed. Syst. 2007, 13, 191–204.
- Cao, W.; Leng, X.; Yu, T.; Gu, X.; Liu, Q. A Joint Encryption and Compression Algorithm for Multiband Remote Sensing Image Transmission. Sensors 2023, 23, 7600. https://doi.org/10.3390/s23177600
