Please note this is an old version of this entry, which may differ significantly from the current revision.
Subjects:
Computer Science, Information Systems
Unlike traditional industrial systems that operate in isolation or with limited connectivity, IIoT systems enable seamless communication between devices and systems, both within a single industrial facility and across multiple sites or locations. This interconnectedness allows for the exchange of data and information, facilitating the integration of operational technology (OT) with information technology (IT) systems.
- identity privacy
- location privacy
- footprint privacy
- multidimensional privacy
1. Introduction
Conventional corporate structures, within a society where humans and robots need to collaborate, create obstacles that squander energy, devalue information, and limit knowledge transfer. At this point, the IIoT is transforming how businesses and, by extension, the manufacturing industry, operate [1]. The IIoT is relevant to ubiquitous connectivity, enabling objects, machines, and devices to exchange data autonomously across networks, eliminating the need for human intervention. This connectivity has brought about remarkable progress in industrial organizations, seamlessly merging the physical and digital realms and driving transformative changes in the economy and modern business practices. With the aid of sensors, businesses can effectively monitor performance and address areas that require improvement, thereby enhancing both the manufacturing process and the overall customer experience and ultimately adding value at every production stage [2].
2. IIoT and Privacy-Preserving Architectures
Unlike traditional industrial systems that operate in isolation or with limited connectivity, IIoT systems enable seamless communication between devices and systems, both within a single industrial facility and across multiple sites or locations. This interconnectedness allows for the exchange of data and information, facilitating the integration of operational technology (OT) with information technology (IT) systems [12].
The IIoT leverages technologies such as cloud computing, big data analytics, machine learning, and artificial intelligence to process and derive insights from the vast amount of data generated by industrial devices and systems. These technologies enable predictive maintenance, remote monitoring, intelligent automation, and optimization of industrial processes.
The applications of the IIoT are diverse and can be found in various industries, including manufacturing, energy and utilities, transportation, agriculture, healthcare, and more. Examples of IIoT implementations include smart factories, connected supply chains, remote asset management, predictive maintenance, and energy management systems.
Any edge device (sensors, readers, gateways) can transfer local data to cloud systems by using any available communication system for real-time analysis. However, if they are not incorporating AI applications, their use can be considered passive, as they cannot utilize the data in real-time.
AI plays a crucial role in leveraging data in real-time by enabling efficient processing, analysis, and decision-making. Also, AI empowers organizations to harness the power of real-time data by enabling efficient processing, analysis, and decision-making. By leveraging AI algorithms and techniques, organizations can extract insights, make predictions, automate processes, and provide personalized experiences in real-time, thereby gaining a competitive edge and driving innovation. It must be noted that real-time data processing focuses on the timely processing and analysis of data as it is generated, enabling organizations to make immediate decisions or take prompt actions. Intelligent automation, on the other hand, leverages AI and automation technologies to automate tasks and processes, reducing human effort and improving efficiency. Together, they can enhance operational agility, optimize decision-making, and drive intelligent actions based on real-time data.
On the other hand, this closer networking of the digital world of machines creates the potential for profound changes in global industry and many areas of private and social life. Based on all this, it is necessary to present tomorrow’s trends in everything related to IIoT technology applications [13].
-
Growth of IIoT applications [14]. Manufacturing automation continues to grow, with the number of companies choosing to automate and implement the IIoT soaring to new levels due to the impact of the COVID-19 pandemic. Machine learning and robotics are two applications that increase automation. Machine learning increasingly automates manufacturing processes, so less human intervention is required, while the increasing number of human jobs being taken over by robotics results in fewer people in the workplace. Organizations need to ensure that proper security protocols are in place to safeguard data privacy and prevent unauthorized access.
-
The wireless revolution. Only some IIoT applications have access to local sockets [15]. “Local socket” refers to a communication endpoint or interface that allows processes running on the same device or within the same local network to communicate with each other. Local sockets in IIoT architectures can provide privacy in industrial environments by enabling secure and private communication between processes and applications running on the same device or within the same local network. By utilizing local sockets, data can be exchanged and coordinated within the confines of the device or local network, reducing the risk of unauthorized access or interception from external sources. This local communication ensures that sensitive data stays within the trusted boundaries of the industrial environment, enhancing privacy and preventing potential security breaches. Additionally, with the advent of advanced IIoT wireless technologies like 5G, organizations can further enhance network isolation and security, creating dedicated and isolated network environments that offer heightened privacy, control, and protection for sensitive data through features such as Network Slicing, Enhanced Security Mechanisms, Private 5G Networks, and Network Function Virtualization (NFV). Secure and private communication between processes and applications within the industrial environment helps maintain data privacy and prevents potential security breaches.
-
Adoption of Virtual Reality (VR) [16] for remote operations has become dominant for industrial applications regarding training and commissioning. Devices that combine a screen, camera, and microphone have become more sophisticated, and machine suppliers more often collaborate with their customers or service engineers through VR. The ability to commission machines remotely has made companies realize that being on-site is only sometimes necessary. The machine supplier can work with the customer through an augmented reality headset, such as a HoloLens. The customer sees virtual reality instructions and maintenance data to perform the necessary tasks, while the machine supplier receives a live feed of what the customer sees. As companies employ VR for training, maintenance, and collaboration purposes, it is crucial to ensure that privacy safeguards are in place to protect sensitive information shared through these immersive technologies.
-
Use of machine data to improve customer relations [17,18]. Connected machines have opened new ways to use machine data and improve customer relationships. The above statement highlights the impact of interconnected devices and the data they generate on enhancing customer relationships. Specifically, connected machines and the data they generate enable organizations to leverage the machine data in various ways, leading to improved customer relationships. By utilizing machine data for proactive maintenance, predictive analytics, customized offerings, and enhanced support, organizations can deliver better customer experiences, increase customer satisfaction, and strengthen their relationships with the customers. It is not only interesting for large companies but also for smaller companies to make use of their data. Due to the increase in connected machines, the number of companies with access to critical machine data has also increased tremendously. It is a big challenge for many companies to discover new possibilities. The use of data is not only essential to improve and optimize companies’ machines but also to create a better long-term relationship with customers. Machine data can, for example, be used to prevent equipment failures by predicting and performing machine maintenance before a fault occurs. In this way, machine downtime can ultimately be reduced [19]. Ensuring data security and using anonymization techniques when analyzing and utilizing machine data can help protect customer privacy.
-
Machine learning [20]. Machine learning is a branch of AΙ, where systems must be able to learn automatically and improve from experience without being programmed by humans. Applying machine learning can be difficult because preprocessing to label and normalize many data takes time. Unsupervised learning or self-learning methodologies create higher-scale automation [21]. This means that human intervention is no longer needed since the data from the device is automatically sent to the algorithm. Thus, machine learning detects patterns of normal usage; therefore, after some time, it also tracks unusual patterns. For example, a machine creates several terns, but when a part of the machine fails, new patterns are created with donations from the usual pattern. When such a situation occurs, machinery suppliers receive a notification so they know that maintenance is required [22,23]. Implementing data privacy and security measures during data preprocessing, model training, and inference stages is crucial to maintaining privacy while benefiting from machine learning techniques.
-
“Smart” packaging [24]. Using direct materials with built-in connections, intelligent packaging delivers advanced benefits for industries. A fundamental feature of smart packaging is enabling customers to interact with it and collect data for more efficient product handling. Smart packaging may include video recipes and other demonstrations that explain the product’s use. ICT and packaging interact in several ways, including sensors, Quick Response (Q.R.) codes, and augmented/virtual/mixed reality possibilities. The objective is to increase the customer value and data collection via intelligent monitoring to optimize the operations and improve efficiency [25]. Ensuring transparent data collection practices, obtaining informed consent, and implementing robust security measures helps to protect customer privacy and build trust.
As can be easily seen, the development of the IIoT is a big step in realizing Industry 4.0 and the upcoming Industry 5.0, as it promotes the large-scale automation and optimization of processes related to intelligent sensors (e.g., configuration, high-volume handling of data, decision-making, etc.). But this involves significant technical difficulties due to the industrial wireless networks’ large scale and complex structure. In addition, recording and transmitting large amounts of data creates severe security and privacy concerns, as some may contain sensitive industry and personal information [26].
Privacy and security in the IIoT scenario are presented in Figure 1 [27].
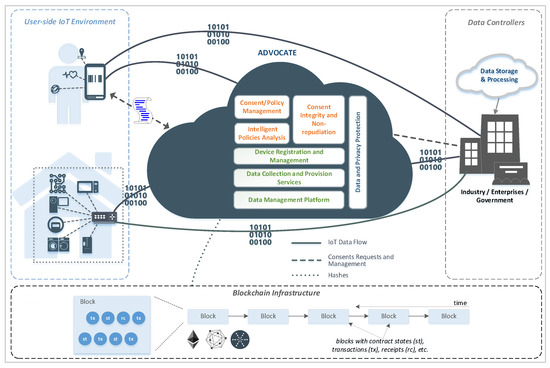
Figure 1. Privacy and security in the IoT/IIoT using ADVOCATE architecture [27].
The ADVOCATE approach aims to address data privacy and consent management in various user environments, such as smart homes, patient health monitoring systems, and activity monitoring sensors. It utilizes a portable device, like a mobile phone, to create a user-friendly interface for data subjects to interact with and manage their personal data disposal policy and consent.
The architecture proposed by ADVOCATE focuses on three specific ecosystems: smart cities, industry, and healthcare. These environments often involve a wide range of sensors and devices that collect data about individuals. By using the ADVOCATE approach, data controllers can interact with data subjects through the portable device to obtain their consent for the data processing activities.
In addition, in the industrial sector, the ADVOCATE approach is applied to ensure that data subjects have a say in how their personal data is processed within industrial environments. This is particularly important considering the sensitive nature of data involved in manufacturing processes, trade secrets, and industrial control systems. By using a portable device, individuals can easily manage their consent preferences and ensure that their personal data is handled appropriately.
It must be noted that ADVOCATE is an ideal industry privacy paradigm by providing a user-centric and customizable framework for managing consent, data disposal policies, and privacy preferences. It helps industries comply with privacy regulations, address industry-specific privacy concerns, and empower individuals to have control over their personal data in industrial environments.
Architectures that protect privacy are promising solutions to the IIoT ecosystem. Privacy-preserving architectures refer to the design and implementation of systems that prioritize the protection and preservation of user privacy. These architectures are particularly relevant in today’s digital age, where vast amounts of personal data are collected, processed, and shared. The following are some commonly employed privacy-preserving architectures [26]:
-
Privacy by Design (PbD) [28]: Privacy by Design is a framework that promotes privacy considerations throughout the entire system development lifecycle. It involves embedding privacy features and measures into the architecture, ensuring that privacy is a core principle from the initial design stages. PbD can certainly be applied in IIoT environments. By integrating privacy considerations into the design and development of IIoT systems, organizations can ensure that privacy is a fundamental aspect of their architecture and processes.
-
Differential Privacy [29]: Differential privacy is a technique that aims to protect individual privacy while still allowing useful information to be extracted from datasets. It adds noise or perturbation to the data to prevent the identification of specific individuals while preserving the overall statistical properties of the dataset. Differential privacy can be challenging to implement in IIoT environments due to the decentralized and diverse nature of the data sources. However, with careful design and data aggregation techniques, it is possible to apply differential privacy principles in certain IIoT use cases where data privacy is crucial.
-
Federated Learning [30]: Federated learning is an approach where machine learning models are trained on decentralized data without transferring the data to a central server. This architecture allows for collaborative model training while keeping the data on individual devices, thereby maintaining privacy. Federated learning can be well-suited for IIoT environments, as it allows collaborative model training while keeping the data on individual devices or local servers. This approach preserves privacy by minimizing data transfer and centralization.
-
Homomorphic Encryption [31]: Homomorphic encryption enables computation on encrypted data without decrypting it. It allows data to be processed securely in an encrypted state, preserving privacy during computation. Homomorphic encryption can be complex to implement in resource-constrained IIoT devices and systems due to its computational overhead. However, advancements in hardware and cryptographic techniques may make it more feasible for specific IIoT use cases where privacy-preserving computations are necessary.
-
Zero-Knowledge Proofs [32]: Zero-knowledge proofs are cryptographic protocols that allow one party to prove the validity of certain information to another party without revealing the actual information. This approach enables the verification of data or statements without exposing the underlying sensitive data. Zero-knowledge proofs can be challenging to implement in IIoT environments due to the limited computational capabilities and communication constraints of IIoT devices. However, they can be applied in certain scenarios where privacy-preserving authentication or verification is required.
-
Data Minimization [33]: Data minimization involves collecting and retaining only the necessary data for a specific purpose, reducing the exposure of personal information. By limiting the amount of data collected, processed, and stored, privacy risks are reduced. Data minimization is highly relevant and applicable in IIoT environments. Limiting the collection, processing, and retention of personal data to what is strictly necessary helps reduce privacy risks and ensures compliance with privacy regulations.
-
User-centric Identity and Access Management (IAM) [34]: User-centric IAM puts individuals in control of their personal information. It allows users to manage their own identity and control the sharing of their personal data, ensuring privacy preferences are respected. User-centric IAM may have limited applicability in IIoT environments since the concept of individual users may not always align with the industrial setting. However, similar principles can be applied to manage access, authentication, and authorization of IIoT devices and systems, ensuring that privacy preferences are respected.
These privacy-preserving architectures aim to strike a balance between the need to collect and process data for functional purposes while respecting individual privacy rights. By incorporating privacy-enhancing technologies and principles, these architectures help mitigate privacy risks and build trust between users and service providers.
Blockchain technology offers several privacy-preserving architectures that aim to protect sensitive data while leveraging the benefits of a decentralized and immutable ledger. Here are some key privacy-preserving architectures in blockchain [35]:
-
Confidential Transactions [36]: Confidential transactions use cryptographic techniques to obfuscate transaction details while still maintaining the integrity of the blockchain. This allows for the concealment of transaction amounts and participant identities, enhancing privacy.
-
Zero-Knowledge Proofs [37]: Zero-knowledge proofs (ZKPs) enable the verification of certain statements or computations without revealing the underlying data. ZKPs can be utilized in blockchain to prove the validity of transactions or smart contract conditions without disclosing the sensitive information involved.
-
Ring Signatures [38]: Ring signatures allow for the anonymous signing of a transaction on behalf of a group. In a blockchain context, a ring signature enables a participant to sign a transaction without revealing their specific identity, making it difficult to determine the actual signer.
-
Stealth Addresses [39]: Stealth addresses provide privacy in transactions by creating a one-time destination address for each transaction. This prevents the direct association between a sender’s address and the recipient’s address, enhancing privacy.
-
Homomorphic Encryption [40]: Homomorphic encryption enables computations to be performed on encrypted data without decrypting it. By applying this technique to blockchain, sensitive data can be stored and processed in an encrypted state, preserving privacy.
-
Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge (zk-SNARKs) [41]: zk-SNARKs allow for the verification of computations without revealing the inputs or intermediate steps. This technology can be used in blockchain to prove the validity of a computation, such as verifying a smart contract, while keeping the inputs confidential.
-
Permissioned/Private Blockchains [42]: Permissioned or private blockchains restrict participation and access to a select group of known entities. These blockchains provide enhanced privacy as they limit the visibility of transactions and data to authorized participants.
Figure 2 presents an extensive blockchain architecture standardization that can be applied to several novel industrial applications [4].
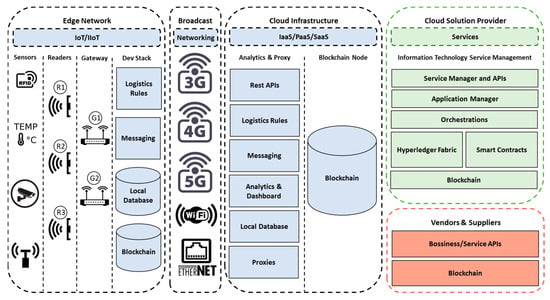
Figure 2. Blockchain scalable architecture for industrial ecosystems [4].
Here are a few examples of how blockchain technology has been applied in various scenarios to enhance privacy:
-
Healthcare Data Sharing: Blockchain can be used to improve the privacy and security of healthcare data sharing. By storing medical records and sensitive patient information on a blockchain, access can be controlled, and data integrity can be ensured. Patients have control over their own data and can grant access to healthcare providers as needed, reducing the risk of unauthorized access or data breaches. One example is MedRec, a blockchain-based system that allows patients to securely share their medical records with healthcare providers while maintaining privacy and data ownership.
-
Supply Chain Management: Blockchain technology has found applications in enhancing privacy and transparency in supply chain management. By recording transactions and tracking products on a blockchain, stakeholders can verify the authenticity and provenance of goods without revealing sensitive business information. This helps prevent counterfeit products and provides transparency for consumers. IBM’s Food Trust is a notable example that utilizes blockchain to track and trace food products, ensuring the integrity of the supply chain and providing consumers with information about the origin and handling of their food.
-
Identity Management: Blockchain offers potential solutions for secure and privacy-preserving identity management systems. By using blockchain, individuals can maintain control over their personal data and selectively disclose information to third parties, reducing the risk of identity theft and unauthorized data access. Self-sovereign identity (SSI) solutions, such as uPort and Sovrin, leverage blockchain to enable individuals to manage and control their digital identities, providing privacy-enhancing features and reducing reliance on centralized identity providers.
-
Financial Transactions and Privacy: Blockchain technology can improve privacy in financial transactions by reducing the need for trusted intermediaries and providing pseudonymity. Cryptocurrencies like Bitcoin and privacy-focused cryptocurrencies like Monero utilize blockchain to facilitate secure, decentralized, and pseudonymous transactions. While blockchain transactions are public, privacy-focused techniques such as ring signatures, stealth addresses, and zero-knowledge proofs are employed to obfuscate transaction details and enhance privacy.
It is worth noting that while blockchain technology can enhance privacy in these scenarios, its implementation requires careful consideration of the specific use case, including factors such as regulatory compliance, scalability, and user adoption.
Federated learning is also a privacy-preserving architecture that enables collaborative machine learning on decentralized data. It allows multiple parties, such as individual devices or edge servers, to train a shared machine learning model without directly sharing their raw data with a central server or each other. Here are some key aspects of federated learning that contribute to its privacy-preserving nature [43,44]:
-
Local Training: In federated learning, the training of the machine learning model takes place locally on individual devices or edge servers. This means that data remains on the devices, and only model updates (such as gradients) are shared with the central server or aggregator.
-
Differential Privacy: Differential privacy techniques can be employed in federated learning to further protect privacy. By adding controlled noise or perturbation to the local model updates before sharing them, the individual data points and patterns are obfuscated, preventing the reconstruction of sensitive information.
-
Encryption: Encryption techniques can be applied to protect the confidentiality of the model updates during transmission. Secure multi-party computation (MPC) protocols, homomorphic encryption, or secure enclaves (such as Trusted Execution Environments) can be utilized to ensure that the model updates remain private.
-
Aggregation with Privacy Preservation: The central server or aggregator collects the encrypted or differentially private model updates from the participants and performs the aggregation to update the shared model. Aggregation techniques can be designed in a way that preserves privacy, such as using secure aggregation protocols that do not reveal individual contributions.
-
On-Device Personalization: Federated learning can also support on-device personalization, where the shared model is further fine-tuned or customized on individual devices using locally available data. This approach ensures that sensitive data remains on the user’s device, enhancing privacy.
-
Secure Communication: Secure communication protocols, such as encrypted channels and secure socket layers (SSL/TLS), should be employed during data transmission between the participants and the central server to protect against eavesdropping and data tampering.
Federated learning allows organizations or individuals to leverage the collective intelligence of decentralized data while minimizing the risks associated with data sharing. This architecture promotes privacy by keeping sensitive data localized, incorporating privacy-preserving algorithms, and utilizing encryption and secure communication protocols. Figure 3 presents the Federated Auto-Meta-Ensemble Learning (FAMEL) architecture in the new IT/OT industrial environment [45].
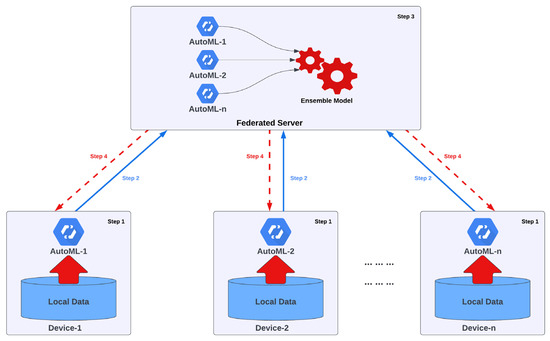
Figure 3. Basic security reference architecture in the industrial environment [45].
It is a holistic system that automates selects and uses the most appropriate algorithmic hyperparameters to optimally solve a problem under consideration, approaching it as a model for finding algorithmic solutions where it is solved via mapping between the input and output data. The proposed framework uses meta-learning to identify similar knowledge accumulated in the past to speed up the process. This knowledge is combined using heuristic techniques, implementing a single, constantly updated intelligent framework. The data remains in the local environment of the operators, and only the parameters of the models are exchanged through secure processes, thus making it harder for potential adversaries to intervene with the system.
Here are a few examples of how federated learning technology has been applied in different scenarios to enhance privacy:
-
Healthcare [46]: Federated learning can be applied in healthcare settings to enable collaborative model training while preserving patient privacy. Hospitals or medical institutions can train machine learning models using local patient data without sharing sensitive patient information. The models are then aggregated or updated in a privacy-preserving manner, allowing healthcare providers to benefit from shared insights without compromising patient confidentiality. This approach can be useful for applications such as disease diagnosis, medical image analysis, or predictive analytics.
-
Smart Devices and the Internet of Things (IoT) [47]: Federated learning is well-suited for scenarios involving edge devices or IoT devices. These devices often have limited computational resources, making it challenging to send large amounts of data to a centralized server for model training. With federated learning, edge devices can collaboratively train machine learning models using locally collected data while keeping the data on the device. Only model updates or aggregated information is sent to a central server, ensuring privacy while benefiting from shared knowledge. This is useful in applications such as personalized recommendations, activity recognition, or anomaly detection in smart homes or industrial IoT settings.
-
Financial Services [48]: Federated learning can enhance privacy in financial services by enabling collaborative model training while keeping sensitive customer data on local servers or devices. Banks or financial institutions can train machine learning models for tasks like fraud detection or credit scoring using locally held customer data. The models’ updates or aggregated information are exchanged in a privacy-preserving manner, ensuring the privacy of individual customer transactions and sensitive financial information.
-
Natural Language Processing (NLP) [49]: Federated learning can be applied in NLP tasks to protect user privacy while improving language models. Instead of centralizing user data on a single server, federated learning allows individual devices or servers to train language models using local data. The models’ updates or aggregated information, which preserve the privacy of individual texts, are shared across devices or servers. This approach enhances privacy while enabling the improvement of language models for applications such as voice assistants, chatbots, or sentiment analysis.
These examples illustrate how federated learning can be leveraged in various domains to enable collaborative model training while maintaining privacy and data confidentiality. By keeping the data decentralized and only exchanging model updates or aggregated information, federated learning offers a privacy-enhancing approach for machine learning in scenarios where data privacy is crucial.
A discussion and comparison of these two approaches (Blockchain and Federated Learning) are presented in the Table 2.
Table 2. Blockchain vs. Federated Learning.
| Technology | Description | Privacy Benefits | Challenges | Comparison |
|---|---|---|---|---|
| Blockchain | Blockchain technology is a decentralized and distributed ledger system that offers enhanced security and privacy features. It ensures the integrity and immutability of data by storing transactions in a chain of blocks, making it difficult for malicious actors to alter or tamper with the data. | Data Transparency: Blockchain allows participants in the network to have access to a transparent and auditable history of transactions without revealing specific identifying information. | Scalability: Blockchain networks can face challenges in terms of scalability due to the consensus mechanisms and the need to replicate data across multiple nodes, resulting in slower transaction speeds. | Data Handling: Blockchain technology stores data directly on the ledger. |
| Data Integrity: The decentralized nature of blockchain ensures that data stored on the ledger is tamper-resistant, making it difficult for unauthorized parties to modify or manipulate information. | Energy Consumption: Some blockchain networks, particularly those utilizing proof-of-work consensus, require significant computational power, leading to high-energy consumption. | Data Privacy: Blockchain provides transparency and integrity but may not provide strong privacy for data contents. | ||
| Secure Transactions: Blockchain employs cryptographic techniques, such as digital signatures and encryption, to secure data transfers and ensure authenticity. | Data Privacy: While blockchain technology ensures data integrity and immutability, it does not inherently provide strong privacy protection for the contents of the data. The transparency of blockchain can potentially reveal sensitive information about transactions. | Trust Model: Blockchain is based on a decentralized trust model. | ||
| Federated Learning | Federated learning is an approach where machine learning models are trained across multiple decentralized edge devices or servers without sharing the raw data. Instead, only model updates or aggregated information is exchanged between the devices and a central server, ensuring data privacy. | Data Localization: Federated learning allows data to remain on local devices or servers, reducing the risk of data breaches or unauthorized access. | Model Heterogeneity: Federated learning can be challenging when dealing with a diverse range of edge devices or servers with different computational capabilities, data distributions, or data quality. | Data Handling: Federated learning keeps the data locally and only exchanges model updates or aggregated information. |
| Privacy-Preserving Model Training: The model updates or aggregated information shared during federated learning are typically anonymized and encrypted, preserving the privacy of individual data points. | Central Server Trust: While federated learning aims to preserve privacy, it still requires trust in the central server that aggregates model updates. A compromised or malicious server could potentially extract sensitive information from the updates. | Data Privacy: Federated learning focuses on preserving the privacy of individual data points during model training. | ||
| Reduced Data Transmission: Federated learning minimizes the need to transfer large amounts of raw data to a central server, which can be beneficial in bandwidth-constrained environments or when dealing with sensitive data. | Model Interpretability and Debugging: Federated learning can make it challenging to interpret and debug models trained across multiple devices or edge nodes. Understanding the reasons behind model performance issues, identifying erroneous contributions, or diagnosing the root causes of failures may require specialized techniques and tools. | Trust Model: Federated learning relies on trust in the central server and the integrity of participants. |
It is important to note that these solutions are not mutually exclusive, and their applicability depends on the specific requirements and constraints of the IIoT ecosystem. Organizations may choose to combine these approaches or utilize other privacy-enhancing technologies to achieve the desired level of privacy and security.
This entry is adapted from the peer-reviewed paper 10.3390/a16080378
This entry is offline, you can click here to edit this entry!
 Encyclopedia
Encyclopedia
