1. Introduction
Microgrids, the new-age form of power grid architecture, are gaining increasing attention from researchers and industries. The possibility of integrating renewable generations, electric vehicles (EV), energy storage, and distributed energy resources into the power grid and coupling them with effective communication links presents an opportunity to improve the efficiency of the power grid [
1]. Additionally, microgrids are capable of powering localized loads by operating in an isolated mode [
2].
With the aim of reducing carbon emissions, renewable energy generation is encouraged in the power sector, and the transportation sector is moving towards the electrification of vehicles. To achieve sustainable development goals, by 2030, there exists a target to integrate 8000 GW of renewables (compared to the 2800 GW integrated at present). By 2025, at least 100 countries will aim to transition to 100% renewable generation. At present, Norway has achieved the most renewable power integration, with 99%; New Zealand (81%), Brazil (79%), Colombia (74%), Canada (68%), Sweden (67%), and Portugal (65.5%) follow. Saudi Arabia has achieved the least integration (0.1%).
The renewable energy share globally increased from 26.30% to 28.1% from 2020 to 2021. It has been observed that 17% of global CO
2 emissions are due to the transport sector; the global EV market has received huge support, which has led to over 16.5 million EVs on the road. By 2030, 2% of global electrical demand is expected to be due to EVs. Microgrids are the best alternative to conventional grids in terms of grid integration with RES and EVs [
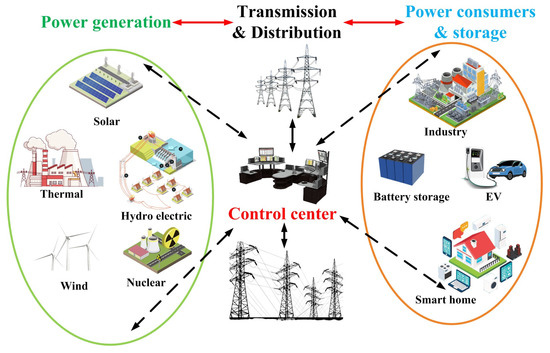
3]; the variety of sources and loads that can be integrated into a microgrid is shown in
Figure 1.
Figure 1. Overview of a microgrid.
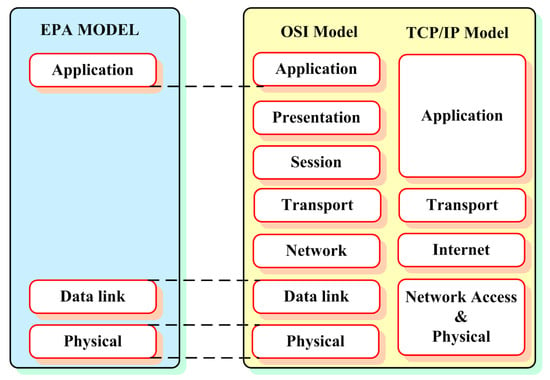
With the variety of intermittent distributed energy resources that exists, information regarding load availability and demand on the grid should be continuously monitored and communicated to the controller for effective operation and control. The communication network is established based on the open system interconnection (OSI) model, transfer control protocol/internet protocol (TCP/IP) model, extensible authentication protocol (EAP), and microgrid communication [
4,
5].
Figure 2 denotes the different protocol structures. The development of Internet of Things (IoT) devices and architectures makes it viable to utilize the services of smart meters, smart health, smart transport, and smart grid [
6]. IoT architecture is preferred on the demand side, whereas the EAP model is implemented on the supply side. The battlegrounds between countries have constantly been shifting. Intruding upon a country’s cyberspace and attacking the communication channels of the enemy, thereby interrupting their information transfer, is the war strategy likely to be followed in the near future. This kind of war strategy is termed cyber warfare [
7], and even the strongest and most developed countries are vulnerable to it. To overcome this, countries are focusing on building cyber security and creating cyber awareness [
8,
9,
10]. According to the crunch base cyber security report [
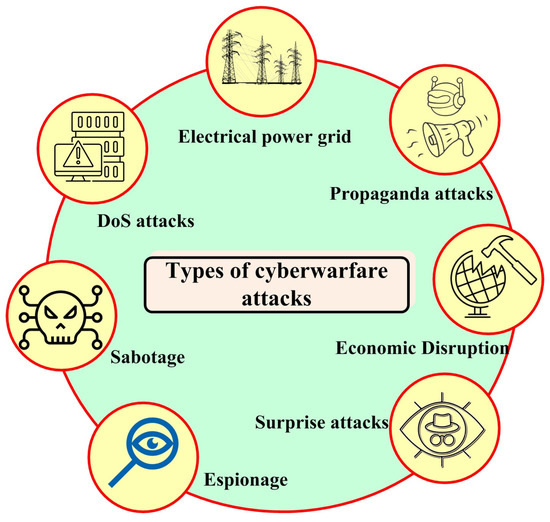
11], over the last decade, there has been an almost 700% increase in cyber security funding. The USA holds the greatest share (76%) of global cyber security funding, and Israel and the UK stand next with 13% and 3%, respectively; all the other countries account for 8%. There are seven different types of attacks, as shown in
Figure 3, through which an attacker can create havoc in a country.
Figure 2. Communication models for microgrid communication.
Figure 3. Different attack methodologies used for cyber warfare.
Espionage is a form of gentle cyber attack, where an attacking country tries to monitor and steal sensitive information by phishing attacks or botnets [
12]. Sabotage attacks or cyber sabotage deliberately destroy critical infrastructure by introducing a malfunction into the system [
13]. These attacks are frequently observed in the introduction of a software update bug. Flooding the communication channel with multiple requests, causing the channel to be irresponsive to legitimate users, is defined as a denial of service attack [
14]. This attack is dangerous, and causes communication delays or interruptions, thereby affecting military bodies and research bodies. Cyber attacks on power grids are the most dangerous and impactful phenomenon. They can cause interruptions in information sharing, disruption to critical services, and huge economic losses [
15].
Propaganda attacks are largely used to influence the audience and their perspective by spreading false news that makes people lose faith and creates agitations in a country; these kinds of attacks look simple, but are effective [
16]. Economic disruption attacks target the economic pillars of the country; these attacks try to take down financial systems such as the stock market and the banking sector by stealing money or blocking people’s access available funds [
17]. Surprise attacks are performed to create a massive impact in less time, thereby weakening the country’s defense systems.
2. Role of AI in Microgrid Control and Safety
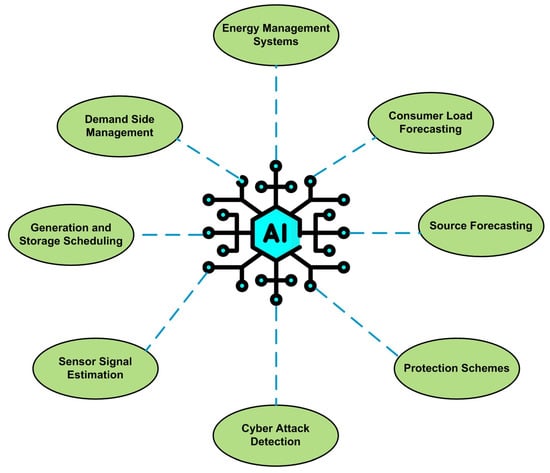
Microgrid systems, considered the application of cyber-physical systems, are more complex and critical in their operation compared to the classical CPS. The characteristics of microgrids include energy management, demand-side management, generation, load scheduling, and interoperability. To achieve these characteristics, industrial IoT is implemented, and network frameworks such as GOOSE, DNP3, and IEC 61850 are used. The applications of artificial intelligence in DC microgrid systems are shown in
Figure 4. The energy management system is important in DC microgrid systems’ control and operation. Due to the presence of multiple distributed generations and a variety of loads on the microgrid system, energy management becomes crucial to attaining optimized power consumption. As the level of importance is high for EMS, it becomes the target of adversaries, who attempt to disrupt its operation. EMS basically collects the data from the variable sensors and gives them to various meta-heuristic methods, math heuristic methods, and state estimation for optimization. State estimation is considered one of the most effective energy management strategies of microgrid systems. The estimated state variables are used to monitor and control various aspects of the microgrid, such as load forecasting, stability analysis, contingency analysis, bad data detection, and optimal power dispatch [
141,
142]. Voltage control is one of the objectives of the microgrid system; in microgrids, voltage control is performed through the distribution generators controlled by power electronic devices. In such cases, the attackers try to breach the control layers and modify the sensor variables, causing a change in the reference voltage levels of the microgrid [
143,
144]. Additionally, the cyber attacks target the microgrid frequency control [
145,
146] and the protection systems [
147]. Several attack mitigation strategies for cyber attacks on microgrid energy systems are proposed in the literature, based on the analysis of measured data. Detection schemes are classified into static and dynamic detection. Detection mechanisms used for attack detection in the steady state are known as static detection methods; meanwhile, dynamic detection schemes utilize systems dynamics for attack detection. The Bayesian detection method [
148], discrete wavelet transform method with DNN [
149], Kulback–Leibler distance method [
150], and transmission line variations techniques [
151] are used to detect FDIA within state estimation methods. Detection of cyber attacks on the load frequency control of power systems is discussed in [
152,
153], in which dynamic detection methods are used. An image-processing method based on parameter variations is used for FDIA detection in [
154].
Figure 4. Applications of AI in DC microgrid systems.
Traditionally implemented model-based methods require complete domain expertise to design energy management systems (EMS). Moreover, the unpredictability and uncertainty in the microgrid often leads to the redesigning of EMS, leading to high design costs and maintenance costs. To overcome this, a model-free-based methodology is proposed, using AI to design EMS. In [
155,
156] GAN is used to model the uncertainties in the output power of RES in a DC microgrid, and to achieve optimal energy management. Load and source forecasting has become the most important part of DC microgrid control. Due to the integration of various RES in DC microgrid systems and dynamic loading scenarios, source forecasting and load forecasting is performed. Based on the time window of forecasting, it is differentiated into short-term, mid-term, and long-term forecasting methods. [
157,
158] explain the load forecasting and source forecasting methods; SVM, ANN, and self-organizing maps are also discussed. Fault detection in microgrids differs from distributed systems because of RES. In [
159], fault detection is performed using machine learning techniques such as SVM, Naïve Bayes, KNN and decision trees. Demand-side management is one of the characteristics of a smart grid. Demand-side management (DSM) is implemented mainly in areas wherein there is a time-based pricing mechanism; depending on the time of the day, the tariff is varied by the utility. In such scenarios, to achieve cost optimization, the DSM mechanism is used, which schedules the operation of loads in order to reduce the overall cost of the end user. Ref. [
160] demonstrates the DSM using ANN in smart grid environments.
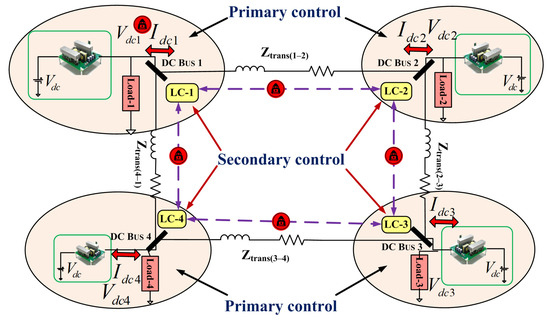
Figure 5 shows the control architecture of the distributed control DC microgrid [
161,
162]. This architecture consists of four nodes, which communicate with neighboring nodes. There are two control layers: the primary control layer and the secondary control layer. The sensor value information from the neighboring converters is transferred to the particular converter through the secondary control layer. The received information is processed and passed through the control algorithm, and the control outputs are sent to the plant; the control outputs are sent to the plant through the primary layer communication. Given the presence of multiple source and loads in the microgrid systems, the control and optimization plays a crucial role. Different control and optimization techniques of microgrids are proposed in the literature. In [
163], the optimization and analysis of microgrid operation are performed using distributed algorithms; the initialization-free algorithm focuses on generation cost optimization in economic dispatch problems. To develop a safe consensus algorithm for the distributed control of microgrids, a differential privacy-based consensus algorithm is designed in [
164]. This research shows that the privacy policy directly correlates to the number of neighbors; thus, each node decides its privacy level.
Figure 5. Control architecture of a distributed DC microgrid.
The present literature consists of different model-dependent control and optimization mechanisms. The inclusion of AI in microgrid control can improve the system’s efficiency. The estimating ability and adaptive capability of the AI and DL methods should be utilized as much as possible.
Microgrid Cyber Security Using AI
Cyber attacks in microgrid systems not only cause issues with data integrity and confidentiality, but cause huge economic losses. Communication of sensor and operational data between each node is essential to attain the efficient operation of microgrid systems. Therefore, monitoring and analyzing the data continuously plays a major role in attaining data integrity. This becomes challenging when the attack is made at the device level rather than the network level. In this scenario, the basic network-level security used in the classical CPS fails to identify the attacks. Therefore, there is a need to develop a cyber security algorithm that is capable of detecting and mitigating device-level and network-level cyber attacks.
The secondary and primary layers, which carry critical sensor information, are prone to cyber attacks. The attack on the communication layers leads to the disruption in the control technique, and causes the maloperation of the DC microgrid. As discussed in the above sections, AI can detect and mitigate cyber attacks. In [
165] an ANN-based FDI attack mitigation mechanism is proposed; an FDI attack is performed on the bus voltage sensors. Reference value estimation is performed using ANN, and compared with the bus voltage. The error from the comparison results in a correction factor when passed through a proportional-integral (PI) controller. This correction factor is added to the bus voltage value before passing to the secondary control to nullify the attack. In [
166], model predictive control (MPC) along with an artificial neural network (ANN) was used to generate the attack mitigation factor when there is an FDI attack on the bus voltage sensor. An ANN with a PI controller is used in [
167] to detect and mitigate the FDI attack on the voltage sensors. A non-linear autoregressive network with an exogenous inputs (NARX) network is used in [
168] to train the actual data and the attack data of the voltage sensors; when there is a difference between the NARX model output and the actual output, an FDI attack is detected.
In all the above articles studied, the attacker created a virtual attack layer just before the secondary layer. This attack layer manipulates the sensor values by injecting false data. Therefore, mitigation is also proposed before the secondary layer. In the whole process, the actual control algorithm is not disturbed. However, the proposed control algorithms, along with the mitigation mechanism, combine model-dependent and model-free parameters. Model-dependent parameters such as PI controllers should be integrated with model-free techniques such as the ANN model. This combination often results in high design complexity and increased computational burden. Additionally, the reduction in the efficiency of the PI controllers during parametric change affects the operation of the detection and mitigation mechanism. Therefore, a unified AI-based mechanism is needed to achieve microgrid control and mitigate cyber attacks.
This entry is adapted from the peer-reviewed paper 10.3390/en16124573