IoT security requirements are crucial for ensuring the safe and secure operation of interconnected devices and the data they produce. Strong authentication and access control mechanisms to prevent unauthorized access and defend against cyberattacks are essential IoT security requirements. These mechanisms need to be capable of identifying and authenticating users and devices, controlling access to sensitive data, and providing granular permissions to ensure that only authorized entities can access the system. Moreover, data generated by IoT devices should be encrypted and protected to ensure privacy and confidentiality. Additionally, the data should be protected from tampering to ensure its integrity and authenticity. Network and device security is another vital aspect of IoT security. IoT devices and systems need to be protected from network-based assaults. Physical assaults, such as destruction, larceny, and tampering, should also be prevented by IoT devices’ inbuilt security mechanisms.
The IoT combines the physical and Internet-connected worlds to provide intelligent collaboration between physical entities and their surrounding environments. Typically, IoT devices work in a variety of environments to accomplish a variety of goals. Nonetheless, their business needs to adhere to stringent cybersecurity and physical security standards [
43,
44]. The participation of interdisciplinary components, networks, computations, and so on contributes to the composite character of IoT settings. This broadens the attack areas of IoT-based systems and makes meeting security restrictions more difficult. To meet the expected IoT security requirements, a solution with all-inclusive factors is required. Nonetheless, IoT devices are typically used in congested and open settings. As a result, attackers/intruders can directly reach IoT devices. IoT devices are usually linked across wireless communication networks, where attackers/intruders can impersonate eavesdropping to extract sensitive information from the communication. Because of their limited resources, IoT devices cannot support complex security solutions [
45]. As a result, preserving the privacy or security of IoT-based devices is a multifaceted and difficult job that has sparked considerable interest in both scholarly and industrial areas. Given that the primary goal of an IoT-based system is to provide simple access to anyone, anywhere, and at any time, attack surfaces become more vulnerable to different attacks [
46].
IoT devices generate vast quantities of data, which are transmitted over networks, making them susceptible to cyber threats. Consequently, securing the network and data in IoT is essential for the safety and security of the entire system. Network security measures provide the foundation for securing data in transit, whereas data security measures safeguard data in transit and at rest. To ensure the secure and safe operation of IoT devices and systems, it is necessary to employ a comprehensive security strategy that includes both network and data security measures.
2.4. Security of Data
Information assurance is a broad category of security standards or goals that only pertain to particular digital information systems. Because of this, this section goes into great detail about the goals and/or requirements of IoT security. The reasons why these requirements are challenging to meet about Industry 4.0 applications are also addressed, giving readers helpful insights into why the contentious security requirements are challenging to meet using conventional techniques. The requirements for an IoT-based device’s security can be summed up as follows.
The digital world will now document data security as an essential security element, and the introduction of IoT will make data security an indispensable aspect of the creation of safe IoT systems. Several works [
47,
48,
49] deemed data secrecy to be a security requirement for IoT data. Nonetheless, data consistency and data access are considered more beneficial than secrecy, particularly in industrial environments [
50,
51], because they have a measurable business impact. This is an unsuitable point of view in the context of a networked device world, with businesses quickly shifting their offline platforms to be internet-connected frameworks. According to company-based survey studies [
52], it was found and proven that data protection is an important motivator for businesses to migrate to Industry 4.0 [
49]. Furthermore, it was stated that businesses were hesitant to adopt data-sharing-based methods (such as cloud sharing, prevention, flaw detection, and so on) due to the lack of proof about the security or safety of these methods during the protection of intellectual property. As a result, this highlighted the need for a consistent strategy to safeguard the rational estate of the presence of data-sharing processes. In the early phases, there is widespread agreement that businesses are hesitant to rely on cloud servers for keeping and exchanging IoT data [
53]. Nonetheless, the majority of IoT data violations are noticed within businesses rather than at cloud providers. Then, cloud-based storage was developed to reduce the surface of assaults on both the business and cloud sides. However, data loss mitigation has emerged as an additional requirement, identifying four critical processes required for creating an effective solution. Identification, prevention, recording, and notification are among these variables.
The difficulties in this area are linked with three interfering factors: To begin, due to the resource-constrained nature and mobility of IoT systems, data security methods need to operate in a manner that allows for very limited resource consumption. Second, numerous IoT facilities are supported by data sharing; however, in data-sensitive settings, secrecy is of utmost importance, which frequently presents numerous problems. Third, the need for data security increases dramatically, particularly in the case of sensitive IoT services or apps.
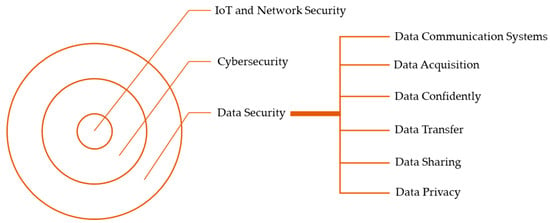
IoT security is a protection tactic and defense mechanism that guards against attacks that particularly target physically connected IoT devices. Network security protects the network and the data it contains from intrusions, assaults, and other threats. This is a wide and inclusive term that covers both software and hardware solutions as well as procedures, guidelines, and configurations for network use, accessibility, and threat avoidance in general. Encryption methods are just one aspect of the topic of data protection. Numerous benefits result from the combination of IoT and the Industry 4.0 paradigm, including better IoT data exploitation. This covers information sharing and other data-dependent operations that might take place anywhere in the system, even outside the organization’s borders. While encryption methods enable preferential data exchange, this part elaborates on other strategies for maintaining the confidentiality of IoT data (Figure 2). Significant connections exist between the IoT and network security, cybersecurity, and data security. Protecting IoT devices and networks is vital for preventing cyberattacks. Network security protects the networks that link IoT devices. Cybersecurity requires defending the whole IoT ecosystem from cyber assaults, including devices, networks, and apps.
Figure 2. IoT info security: how important is it?
Data security is the safeguarding of data gathered and communicated by the IoT devices. This involves encrypting the data during transmission and storing it securely. In addition, access restrictions and authentication systems are crucial for preventing unwanted access to sensitive data. These data security measures are essential for protecting the data collected and transmitted by IoT devices [
32]. IoT devices are susceptible to cyber threats, and protecting them entails installing network security, cybersecurity, and data protection safeguards.
2.5. Summary
IoT software platforms are described as pieces of software that make it easier for IoT devices connected to a network to share data and services. A platform’s characteristics [57] include data gathering, integration and storing, tracking, security, event processing, application enablement, processor analysis and visualization, device management, and connectivity and network management. The sanctity of data while in transmission, safe data storage, recognizing devices seeking a link and transmitting data, and permission of users or organizations are the four categories into which security solutions for a network can be broken down. The two types of IoT software platforms are cloud-based platforms and open-source platforms.
A network is created when gadgets are interconnected to carry out specific duties. Both conventional and cellular networks are possible. People can benefit from useful knowledge that is shared or distributed through the network. Utilizing the network is essential for data to be transmitted more quickly. Information security refers to an organization’s desire to protect information while it is being transmitted over a network. The confidentiality of data, data veracity, and data exposure to the appropriate individual are the three goals of information security [
58].
Data security in the IoT or the cloud is a more recent area of computer security study that can benefit from the established findings in the more established field of data flow management for security [
59]. Logrippo [
59] approached the issue from a basic standpoint. They demonstrated that, under the assumptions of transitivity and reflexivity, any network of communicating entities can be viewed as a partial order of equivalence classes of entities. This generalized and simplified the current theory, which is based on the lattice concept and generates lattices through labeling. There are many methods to build networks of interacting entities, including routing, access control rules (which may involve naming), etc. For data security, their inherent partial orders were adequate and essential, and in any such network, entities will have varying levels of secrecy or integrity depending on where they are in the partial order. It was demonstrated how labeling systems—which can convey various security requirements—can be built to place things in the proper places within network partial orders. Examples were used to present well-established data security concepts such as disputes, conglomeration, and consolidation. The addition, deletion, or relocation of entities in partial orders as a consequence of occurrences such as user or managerial action was then demonstrated. The preservation of security needs through such transformations was explained using a label-based approach.
Many security-related problems with the current communication technologies need to be resolved to provide safe end-to-end connectivity among services. Additionally, the majority of common security methods that are currently thought to be safe may soon be in danger due to the recent, rapid development of quantum technologies. As a result, for contemporary security systems to withstand various possible quantum computer attacks, quantum technologies need to also be powerful. Quantum walks (QW) are regarded as a global quantum computation model and a top-notch key generator due to their unique properties [
60]. In this respect, a novel, lightweight picture encryption method based on QW is suggested in the article by El-Latif et al. [
60] for safe data transmission in IoT systems and wireless networking with edge computing. The newly proposed method builds permutation boxes using the power of QW’s nonlinear dynamic behavior and creates pseudo-random numbers to encrypt the plain picture after splitting it into blocks. The outcomes of the performed modeling and numerical studies demonstrate the viability of the proposed encryption method. Because of the randomness of the encrypted pictures, it is impossible to decipher them by looking at the connection between neighboring pixels. Additionally, the entropy value is close to 8, the percentage of pixels that change is higher than 99.61 percent, and the key parameters are highly sensitive with a big key area to withstand different assaults. The article by Li et al. [
61] developed a data security monitoring method based on narrow-band IoT to address the issues of bad data categorization accuracy and efficacy of conventional data monitoring methods. To begin collecting data for the intranet, a model of network data collection and the best setup for a sensor node were created. Dynamic intranet data analysis indexes were created from three perspectives based on the analysis of data characteristics: creating a security event quantity index, establishing an address entropy index, and data diversion. The security indicator of the IoT was computed by the narrow-band data aggregation rate previously stated to achieve the security of monitoring data. The testing findings demonstrated that, regardless of whether a network assault is present or not, the technique consistently accomplishes its design objectives in terms of accuracy rate (more than 90%), classification time (less than 4 s), and energy usage (less than 150 J).
IoT frequently offers the data gathering, administration, and device and data protection services needed for application development. IoT things or gadgets interact and compute to improve the comfort and security of our lives. IoT can be used for inventory automation, real-time item monitoring, and the administration of things’ information and state. The vast quantity of data that moves between the devices in the network necessitates the creation of a security structure that guarantees the integrity, secrecy, authentication, and permission of data [
62]. The sections that follow cover a few data protection solutions.
Authentication
In addition to its inherent limitations such as processing power, storage capacity, and energy resources, the proliferation of IoT devices is raising security vulnerabilities throughout the business. IoT security is becoming a bigger task for security experts to fight attack susceptibility. Given various security flaws, mobile IoT devices require a data routing mechanism to transmit the collected data [
63]. The enormous rise in IoT usage has changed daily life in many countries, affecting the entire globe. IoT-based networks require protection just like any other program does because the data they generate contain sensitive data. The security methods currently used in these networks do not consider all security goals. The data need to be protected from different kinds of attacks as soon as they are sensed from the IoT world. Additionally, it needs to be possible to accomplish data integrity, access control, secrecy, and authentication of all concerned parties [
64].
Wireless Networks
Wireless sensing networks are a key component of the IoT and have found widespread application in all facets of people’s lives. In wireless sensor networks, identity verification ensures users’ access to real-time data from sensor nodes without risk [
72]. Many tiny devices are used in an IoT-based wireless sensor network (WSN) to gather data and transmit them to central archives. These battery-powered, resource-constrained sensors spend the majority of their energy detecting, gathering, and transmitting data. Security is a major worry in these networks when exchanging data because they are vulnerable to numerous threats, the bloodiest of which is the wormhole assault. These attacks are initiated without obtaining crucial network information, and they seriously jeopardize the network’s efficiency, security, and communication. The limited resource availability in the sensing devices makes its prevention more difficult in an IoT-based network context [
73]. The ESWI method was created by Shahid et al. [
73] to enhance efficiency and security while detecting wormhole attacks. To reduce overhead and energy consumption during operation, this method has been intended to be straightforward and less complex. Their method’s simulation findings demonstrated comparable detection rates and packet transport ratios. Additionally, it resulted in significantly reduced energy usage, a decreased end-to-end delay, and improved output.
Use Cases
In network engineering, today’s Industrial IoT (IIoT) is very sophisticated, and networks experience annual data leaks. To improve IIoT security defense under privacy regulations, an anti-intrusion monitoring device has been developed. High standards need to be met by the IoT’s structural system and security performance parameters are required in an unfriendly network. The network system should employ a technique with a very low rate of data loss and high levels of stability [
80]. Teng [
80] adopted the first deep-learning network technology after evaluating numerous network designs. The LeNet-5 network was upgraded and optimized by the Convolutional Neural Network technology, and a new LeNet-7 was created. An IIoT anti-intrusion monitoring system was built by combining three network technologies. The system’s effectiveness was evaluated and confirmed. The algorithm had a high detection rate, a low false-positive rate, and high data precision. To achieve the highest performance, the model’s generality on high-performance data was verified and contrasted with privacy-aware task offloading techniques. As a result, the technology can be used to safeguard IIoT data privacy under the legislation.
Challenges and Prospects
The digital planet can be controlled and monitored thanks to the IoT. The most recent technology to monitor the necessary data is the IoT. IoT is the answer to lowering intricacy and improving system efficiency in transportation, healthcare, and cyber systems. Pervasive computing enables the IoT to handle data and present the necessary graphical user interface. Information can be accessed through a computer system called cloud computing anywhere and anytime on the globe [
58].