Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Sun Rongbo and Version 2 by Catherine Yang.
Represented by reactive security defense mechanisms, cyber defense possesses a static, reactive, and deterministic nature, with overwhelmingly high costs to defend against ever-changing attackers. To change this situation, researchers have proposed moving target defense (MTD), which introduces the concept of an attack surface to define cyber defense in a brand-new manner, aiming to provide a dynamic, continuous, and proactive defense mechanism. With the increasing use of machine learning in networking, researchers have discovered that MTD techniques based on machine learning can provide omni-bearing defense capabilities and reduce defense costs at multiple levels.
- moving target defense
- cyber security
- affordable defense
- self-adaptive defense
1. Background
To have the principles of MTD thoroughly comprehended, it is essential to understand its background. The concept of MTD was first proposed in 2009 as a response to the shortcomings of reactive security defense mechanisms, which were primarily based on techniques such as authentication, access control, information encryption, intrusion detection, vulnerability scanning, and virus prevention. While these measures offered a degree of security, they proved inadequate due to the increasing automation and diversification of attacks. Furthermore, the complexity of modern networking environments places an overwhelming burden on network administrators, who may overlook even minor issues that could lead to serious security risks. In general, the following are key features that differentiate traditional cyber defense mechanisms from MTD:
-
Traditional defenses often focus on monitoring, detecting, preventing, and remediating attacks on static infrastructure. MTD emphasizes faster and more comprehensive attack detection and timely responses to mitigate potential damages.
-
Traditional defenses rely on known attack patterns for defense and may be limited in addressing emerging or novel threats. MTD seeks to proactively address such unpredictable attacks through its dynamic nature.
-
Unlike traditional defense mechanisms, which operate in a fixed dimension, MTD adapts and changes constantly to protect against attacks on ever-changing systems. This approach significantly limits attackers’ research time and ability to penetrate compromised systems.
While general defense mechanisms aim to improve system stability, their rigid nature makes it challenging to ensure long-term fortification against the rapidly evolving techniques employed by attackers. In contrast, MTD prioritizes affordable, service-oriented defense [1][3] to meet three core development points:
-
Minimizing defense costs (e.g., system deployment overhead)
-
Maximizing service availability for users
-
Maintaining the required defense security levels
Although MTD is built on the architecture of general defense, it aims to minimize deployment overhead by adopting existing security mechanisms as its base. Introducing new security measures requires intensive analysis and patching efforts quintessentially, which can be time-consuming and impractical. MTD aims to preserve affordability in individual system deployments while maintaining its fundamental principle of providing cost-effective defense, i.e., affordable defense.
2. Design and Classification
The basic design principle of MTD centers around three key points.
2.1. What to Move
By dynamically shifting attack surfaces, MTD techniques confuse attackers who rely on fixed system configurations to execute an attack. As a collection of resource attributes (shown in Table 12) in a system that could be used by an attacker to execute an attack, the attack surface can be exploited to confuse the attacker by dynamically changing these configurations. To facilitate the enumeration of joint attack surfaces, they can be classified hierarchically based on their level of existence. This classification leads to the first way of classifying MTD techniques, which includes the network layer, platform layer, runtime environment layer, software layer, and data layer [1][3].
Table 12.
Attack surfaces most often utilized.
| The Attack Surfaces Often Utilized in Recent Years (Since ′18) | ||
|---|---|---|
| Network L. | ❏IP address/Port [2]11[3][4][5][6][7][8][9][10][11][,1212,13],14[13,15][14][,16,17,18,19,20,21,22,23] | ❏Route/Network topology [15][16][[19][2417][18],25,26,27,28] |
| Platform L. | ❏Virtual Machines [20][21][22][23][24][29,30,31,32,33] | ❏Proxies [25][34] |
| Rt. Env. L. | ❏Operation Systems [26][27][28][35,36,37] | |
| Software L. | ❏Software [29]38[30][,3931][,4032][33][,41,42] | |
| Data L. | ❏Instruction sets [34][35][43,44] | ❏Codes [36][37][45,46] |
Various MTD techniques can disrupt the attacker’s resource reconnaissance and vulnerability detection. By continuously shifting the attack surface, MTD techniques hinder an attackers’ ability to locate and access target hosts, forcing them to continuously chase the target. This not only increases the attacker’s cost but also eliminates their temporal advantage and information asymmetry advantage over defenders. The result is a more resilient defense mechanism that can adapt to ever-evolving threats.
Research on MTD has primarily focused on the network layer for several key reasons. Firstly, designing defense mechanisms at the network layer is more in line with MTD’s pursuit of affordable defense due to its small size, low resource consumption, and ease of operation. Secondly, narrowing the focus to a specific layer, such as the network layer, allows for more targeted study and development.
Nevertheless, it is important to note that MTD has been in development for over a decade, and thus, the current top-heavy research situation does not fully represent the breadth and depth of MTD as a cyber defense mechanism.
2.2. How to Move
By seeking ways to shift attack surfaces to increase unpredictability and uncertainty, MTD techniques can lead to information failure for attackers. Cho et al. [38][9] classified the shifting of attack surfaces into shuffling, diversity, and redundancy (SDR), as well as hybrid techniques based on a mixture of these two or three, as shown in Figure 14.
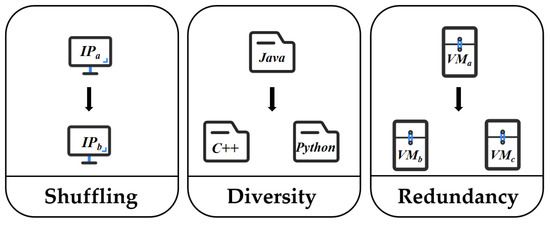
Figure 14.
SDR examples.
-
Shuffling
Shuffling involves randomizing or rearranging system configurations. IP hopping [2][11] is a common shuffling method that constantly changes the host’s IP address to evade scanning by attackers. Shuffling does not require building new security techniques. Instead, it builds on existing ones, and is, therefore, less burdensome in terms of development costs and resource consumption, is easy to operate, and is highly compatible. However, because shuffling relies on the quality of existing techniques, its effectiveness may be limited if those techniques are not sufficiently robust against attacks.
-
Diversity
Diversity means alternating between different components that can achieve the same system functionality. For example, if a program is programmed in Python, the same functionality can be achieved in C++. Diversity builds on existing defense techniques and has similar advantages and disadvantages to shuffling. However, it also incurs additional defense costs due to the need to prepare extra systems or components.
-
Redundancy
Redundancy refers to the preparation of multiple copies of a system or network component to ensure that the new copy can be replaced at any time if the original system or component is attacked, disabling the original attack process. It is worth noting that redundancy requires higher service availability for users than the previous two techniques. Therefore, quality measurement of redundancy is usually accomplished by evaluating the system’s Quality of Service (QoS). In addition, if redundancy is not performed correctly, it provides a more significant opportunity for an attacker to execute an attack on a larger attack surface (e.g., another server to attack or another path to the target) than a system that does not use redundancy.
-
Hybrid
Hybrid combines two or three of the above methods. While enhancing security, the benefits of each of the three methods can be taken into account, such as improving QoS while keeping the overhead low, but what cannot be overlooked is that hybrid presents a larger attack surface than individual methods and requires an additional overhead when combining multiple methods into a single solution.
2.3. When to Move
MTD techniques need to determine when to update the current state of the MTD system to maximize the invalidation of the relevant resource information obtained by an attacker. The conditions for triggering updates can be divided into fixed-time triggering [39][6] and ad hoc event triggering.
-
Fixed-time triggering: MTD techniques periodically shift the attack surface at fixed intervals. Setting the triggering interval requires a technique-specific analysis, but for each technique, researchers need to find the right triggering point. If the interval is too long, attackers have enough time to penetrate the system and launch an attack. If it is too short, the MTD mechanism is triggered frequently, leading to wasted resources and degraded performance. Additionally, frequent triggering of MTD can significantly degrade the QoS and users’ experience.
As a result, self-adaptive MTD techniques based on ad hoc event triggering are becoming increasingly favored. These techniques can effectively avoid the problems associated with selecting fixed intervals. By adapting to changes in the system or network environment, self-adaptive MTD techniques can ensure optimal defense mechanisms that minimize the likelihood of successful attacks while maintaining high QoS and user usage satisfaction.
-
Ad hoc event triggering: MTD shifts the attack surface when the system detects an attacker’s access or a precursor to an attack. Self-adaptive MTD adopts this approach, and its main challenge is accurately predicting attacks that can trigger MTD effectively.
Machine learning can be a helpful tool in addressing this challenge by assisting in the achievement of the self-adaptive triggering of MTD. By analyzing patterns in system behavior, machine learning algorithms can identify potential threats and predict future attacks more accurately than traditional rule-based systems.
3. Development Trends and Challenges for Existing MTD Techniques
3.1. Systematic Development
As mentioned above, MTD techniques are classified into two categories based on what to move and how to move, but these techniques are generally independently proposed by different researchers and have not yet formed a complete system. Therefore, it is urgent and significant in the future that work is conducted to analyze the system or network attributes affected by various MTD techniques, evaluate whether different MTD techniques can be utilized integrally, and establish a complete and available MTD system.
3.2. Integration with Existing Security Defense Mechanisms
MTD defends attackers by shifting the attack surface, but by its nature, this defense mechanism cannot cover the vulnerability of the system itself. For instance, software randomization [29][30][31][38,39,40] (classified as Shuffling/Software layer), a common MTD technique, does not eliminate the existence of vulnerabilities in software. Attackers are still capable of performing vulnerability attacks on specific targets through exploiting mining, buffer overflow, and other methods.
Another example is instruction set randomization [34][35][43,44] (classified as Shuffling/Data layer). Although it can prevent attackers from inserting binary instructions into the target program to execute an attack successfully, the vulnerability of the target program is also not eliminated, and well-designed worms and viruses can still break through the defense of instruction set randomization.
Existing network security defenses such as firewalls, intrusion detection systems, and anti-virus systems have been deployed in the network with network topology and a configuration that is relatively fixed, while introducing MTD into them changes the existing network configuration, thus potentially leading to increased resource consumption, reduced network availability, and possible mutual interference with existing network security defense techniques.
MTD must be implemented appropriately without affecting existing network operations and must adapt to existing network infrastructure, network services, and network protocols. The development trend of MTD needs to integrate better with existing network security protection technology and be embedded better into the existing network.
3.3. Combination with New Techniques
How to maintain the vitality of MTD is our concern, and we believe that as a defense framework concept rather than a defense mechanism that needs to be built from scratch, MTD can be very compatible with emerging techniques.
Undoubtedly, the future of MTD is not just about machine learning. MTD has been combined with many other types of emerging techniques to achieve better active defense effects, such as:
-
SDN-based MTD
MTD tends to change the existing network configuration and, therefore, usually causes the degradation of network service availability. For example, while IP address hopping can interfere with attackers’ scanning and intrusion to some extent, it may cause the failure of the entire network communication, whereas a software-defined network (SDN) can fundamentally change the network structure, giving the central controller the ability to regulate the entire network globally [40][49]. Therefore, IP address hopping in SDN [41][50] could minimize the impact of moving target defense techniques on the entire network.
-
MTD-applied cloud computing
Cloud computing has been widely adopted to process massive traffic data. Many large data centers have utilized cloud computing to provide convenient services due to highly centralized data and services, which is precisely the reason why cloud services are in demand of high-level defense mechanisms to protect these highly centralized data and services. Favorably, the combination of MTD with cloud computing outstandingly improves the proactive defense capability of cloud servers [42][51] and ensures the security of cloud services [43][52].
3.4. Challenges for Existing MTD Techniques
Several issues that require improvement in some existing MTD techniques, including:
-
Large resource consumption and high defense costs.
-
For example, in the face of the attacker’s scanning, the existing MTD’s countermeasure is to perform IP hopping when scanning behavior is detected, and their representative techniques include but are not limited to OF-RHM [2][11], SEHT [3][12], DDS [4][13], and NATD [5][14]. Their common problem is a lack of accuracy and efficiency in identifying attack manners, the waste of resources caused by untargeted hops, and a lack of integration with the affordable defense pursued by MTD.
-
They have an incapability of balancing multi-constraints (e.g., costs, security performance, and service availability).
-
For instance, routing randomization has been proven to be an effective method against eavesdropping attacks. Currently, representative routing randomization techniques include but are not limited to: RRM [44][53], AE-RRM [41][50], AT-RRM [45][54], and SSO-RM [46][55]. However, RRM and AE-RRM implement random transformations only on the routes of data transmission between nodes, without considering different attack behaviors and protecting network QoS under such circumstances. As for AT-RRM and SSO-RM, they can dynamically adjust transformation strategies to some extent, but their protection effectiveness for QoS is still unsatisfactory, and they fail to consider the varying demands of different applications for latency and bandwidth. Besides, all of their packets’ granularity is too coarse, making it easy for attackers to intercept continuous data packets and render the defense ineffective.
-
Relatively fixed defense strategies (easy to be reconnoitered and recognized by attackers).
An example is the ASLR [47][56] deployed in Unix systems. It performs well in defending against buffer overflow vulnerabilities by randomly selecting the base address of the stack at runtime. This means that the location of each variable in memory is uncertain, making it difficult for attackers to exploit these vulnerabilities. However, ASLR is vulnerable to BROP attacks [48][57], which can exploit the fact that the parent process retains the same address space layout when forking a child’s process. This example illustrates that fixed defense strategies are vulnerable to countermeasures applied by attackers. Therefore, there is no easy way for MTD to achieve long-term defense success.
Although MTD is confronted with many challenges, its idea that transitioning from passiveness to activeness and affordable defense is the future trend of cyber security means it has broad application prospects in many fields. With the help of machine learning, MTD research has met a brave new world.
