A mobile ad hoc network (MANET) is an infrastructure-less network where mobile nodes can share information through wireless links without dedicated hardware that handles the network routing. MANETs’ nodes create on-the-fly connections with each other to share information, and they frequently join and leave MANET during run time. Therefore, flexibility in MANETs is needed to be able to handle variations in the number of existing network nodes. An effective routing protocol should be used to be able to route data packets within this dynamic network. Lacking centralized infrastructure in MANETs makes it harder to secure communication between network nodes, and this lack of infrastructure makes network nodes vulnerable to harmful attacks. Testbeds might be used to test MANETs under specific conditions, but researchers prefer to use simulators to obtain more flexibility and less cost during MANETs’ environment setup and testing. A MANET’s environment is dependent on the required scenario, and an appropriate choice of the used simulator that fulfills the researcher’s needs is important. Furthermore, researchers need to define the simulation parameters and the other parameters required by the routing protocol used. In addition, if the MANET’s environment handles some conditions where malicious nodes perform network attacks, the parameters affecting the MANET from the attack perspective need to be understood.
- MANET attacks
- MANET configuration parameters
- MANET evaluation
- MANET simulation
- aodv
1. Introduction
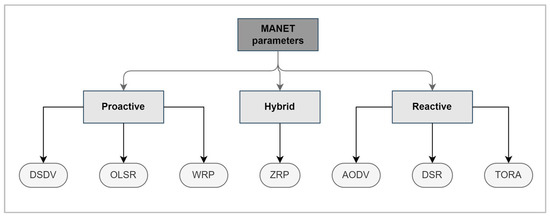
2. Routing in MANETs
-
Proactive routing protocols: For example, OLSR, each node maintains its routing table by periodically updating its information [6]; this increases network overhead. On the other hand, routes will always be available with a minimum delay. Proactive protocols provide better performance than reactive protocols as each node continuously updates its awareness of network changes. When a request is received, the packet forwarding procedure is directly handled.
-
Reactive routing protocols: For example, AODV and DSR, when a source node tries to perform a packet transmission, it initiates a route discovery mechanism to know how to reach the destination. After the route is determined and updated in the routing table, the packet is forwarded [7]. Reactive protocols have minimal network overhead, but there is a delay time consumed in the route discovery.
-
Hybrid routing protocols: For example, ZRP, the close local neighbors to a node are periodically updated, and the global nodes that are not direct neighbors will be updated on demand such as in reactive routing protocols [8].
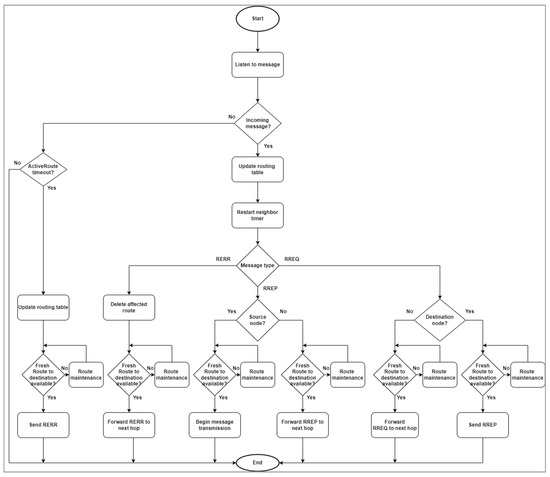
2.1. AODV Routing Protocol
-
Destination node address;
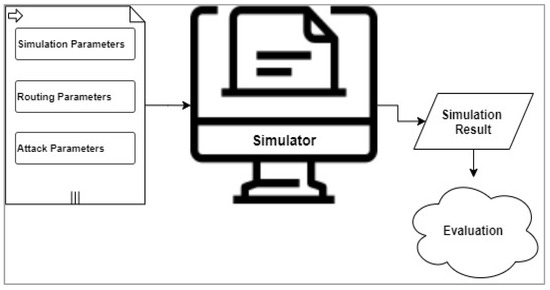
3. Simulation in MANETs
3.0. Simulation in MANETs
MANET technology is rapidly changing, and new protocols and mechanisms are continuously proposed by researchers. Evaluating a network’s performance under different attacks is important to be able to propose protection mechanisms. Therefore, a cost-effective method that empowers researchers to set up and test MANETs plays an important role in research.MANET technology is rapidly changing, and new protocols and mechanisms are continuously proposed by researchers. Evaluating a network’s performance under different attacks is important to be able to propose protection mechanisms. Therefore, a cost-effective method that empowers researchers to set up and test MANETs plays a key role in research.
3.1. MANETs Simulators
Simulators are software tools used to create a virtual environment that supports researchers to set up and test a network’s performance under different conditions. Simulators are GUI-driven tools used to set up a network environment and then perform different attacks on the defined network, or make comparisons between a standard routing protocol and a newly proposed protocol. Using the defined evaluation metrics, a simulator is also capable of collecting the network’s results and evaluating the overall performance [19].Simulators are software tools used to create a virtual environment that supports researchers to set up and test a network’s performance under different conditions. Simulators are GUI-driven tools used to set up a network environment and then perform different attacks on the defined network or make comparisons between a standard routing protocol and a newly proposed protocol. Using the defined evaluation metrics, a simulator is also capable of collecting the network’s results and evaluating the overall performance [30].
There is another method for developers to define and test MANETs using testbeds. Testbeds are experimentation in-lab networks that researchers can set up using dedicated hardware sets for this purpose. Testbeds lack the flexibility to define a MANET network, as MANETs are dynamic networks where nodes continuously join and leave the network. Additionally, the cost is much higher than software simulations to define a MANET using testbeds.
To be able to select a suitable simulator, the researchers need to know the simulator’s key features [20]. Table 2 is a comparison between the widely used simulators in MANETs.To be able to select a suitable simulator, the researchers need to know the simulator’s key features [31]. Table 2 is a comparison between the widely used simulators in MANETs.
-
THPT: Throughput is the rate of successfully delivered packets that reached the receiver node per time slot [30][43]. Throughput is affected by topology changes, noise on communication links, the power of transmission from the source node, and the existence of malicious nodes affecting the throughput ratio.
- Number of hop counts to reach the destination;
-
Intermediate nodes address;
-
Route entry expiry time;
-
Destination node sequence number.
-
Network diameter: The network diameter value sets the maximum number of hop counts between two nodes in MANETs. The network diameter default value is up to thirty-five hops at most as per RFC 3561 standard.
| Simulator Name | Languages Supported | Platform Support | License | Advantages | Disadvantages |
|---|
-
Node transversal time: The node transversal time is the estimation of packet transversal time between two neighbor nodes; this estimation should consider the network, processing, and transfer delay time. The default configuration time is 40 ms.
[32]. This malicious node would then block the data packets from being forwarded to the destination node. Such malicious activity leads to increasing the loss of important data packets, and it is reducing the network’s overall throughput.
MANETs suffer from malicious activities where malicious nodes tend to impact the routing protocol mechanism. The direct impact of the attacks on routing protocols is to degrade the MANET’s performance. To disrupt the MANET routing protocol, attackers tend to use several techniques such as follows:
-
Routing table overflow attack: In this attack, the attacking node tends to crowd the network by advertising several non-existing nodes to overflow the routing table [22]. This prevents legitimate nodes from being aware of network nodes and routing their packets normally.
| OPNET | C, C++ | Windows, Sun Solaris, RedHat Linux | Commercial, Free Educational License |
|
- Network transversal time: The network transversal time is the expected time between sending the RREQ packet and the reception of the RREP packet as per the equation
| ||
|
-
Route request retry: If a route reply is not received by the source node within the maximum network transversal time, the source node can retry to request the route discovery again for a maximum route request retry times. If the route discovery exceeds the route request retry times, the destination node should be considered unreachable. The default value for the route request retry parameter is equal to 2 retries.
-
Blacklist timeout: When the RREP transmission from node A to node B fails, node A records node B in its blacklist buffer. During this blocking time, node A discards any RREQ from neighbor node B until the blacklist timeout is reached. After the blacklist timeout expires, node B is removed from the blacklist [14].
| AODV Parameter | Default Value | ||||||
|---|---|---|---|---|---|---|---|
| NetworkDiameter | 35 hops | ||||||
|
|
|
NodeTransversalTime | 40 ms | |||
| OMNeT++ | C++, NED | Windows, MacOS, and any Unix-like systems | Open source |
|
|
NetworkTransversalTime | 1400 ms |
| NS-2 | C++, OTCL | Windows, MacOS, Ubuntu, Sun Solaris, Fedora Linux, and any Unix-like systems | Open source |
|
|
RouteRequestRetry | 2 retries |
|
|
|
|||||
| NS-3 | C++, Python | MacOS, FreeBSD, Linux | Open source |
|
BlackListTimeout | 2800 ms | |
| RouteRequestRateLimits | 10 packets/s | ||||||
| ActiveRouteTimeout | 3000 ms | ||||||
|
|
| |||||
| GloMoSim | C, PERSEC | Windows XP/7, FreeBSD, Sun Solaris, Fedora Linux | Free |
|
|
||
| QualNet and EXATA/cyber | JAVA | Windows NT/2000/XP/Professional, macOS, Sun Solaris, and most Unix-like systems | Commercial |
-
Flooding attack: In a flooding attack, malicious nodes tend to waste network resources such as memory, bandwidth, and battery by flooding the network with bogus packets [23]. For example, flooding RREQ packets prevents the MANET from functioning normally.
| |||||||
| |||||||
|
|
|
|
||||
| JIST/SWANS | JAVA, Tcl | Windows, macOS, Sun Solaris Linux | Commercial |
|
|
HelloInterval | 1000 ms |
| J-SIM | JAVA | Windows, Sun Solaris Linux | Open source |
|
|
AllowedHelloLoss | 2 times |
| Delete Period Constant | 5 s |
Comparison between simulation tools in MANETs.
3.2. Attacks on MANETs’ Routing Protocols
- DDoS attack: In a DDoS attack, attackers tend to keep the targeted legitimate node busy by continuously requesting RREQ messages from collaborative attackers at the same time without respecting the TTL time
-
False removal of working route: In this attack, the malicious node advertises a false state of the link with the destination node as if the link is broken. This enforces the source node to re-initiate route discovery protocol to find another path to reach the destination. Additionally, it slows down packet transmission. False removal of working route attack could be used with another collaborative attack to isolate the targeted legitimate node from MANET.
- PDR: Packet delivery ratio is the ratio of packets that are received by the destination across the overall transmitted packets from the source node
- Node isolation attack: Attackers isolate an innocent node by blocking routing information about this targeted node from the entire network
- [
- ]
- . This leads to an ignorance of the presence of this innocent node.
- ROR: Routing overhead ratio is the size of control and header packets needed by the protocol for route discovery and maintenance over the total data packets received by the destination node
- [
- Routing table poisoning: In this attack, the attacker sends false RREQ packets with a higher sequence number to force all nodes to delete the old genuine route to a destination and update this route with a corrupted one.
- NRL: Normalized routing load is the ratio between the total number of control packets sent by a source node over the total number of data packets received by a destination node
- [
- ][48]. An increase in normalized routing load metric indicates the efficiency of the used routing protocol.
- Blackhole attack: The attacker tends to change the routing protocol packets to be the best route known for a targeted destination, and when it is requested to forward data packets to the destination node, it starts discarding the received packets to slow down the network performance
- [
- ]
- .
- NL: The network load is the average amount of data packets that are being carried by the entire network over time
- [
- ]
- [
- 49]. Increasing the network load ratio increases the possibility of data collision in the wireless medium.
- Grayhole attack: Grayhole attack is an instance of a blackhole attack where an attacker selectively drops some data packets and normally forwards others
- [
- ]
- , or drops all packets but only at a certain time. This makes the attack difficult to detect.
- Wormhole attack: In a wormhole attack, two attacking nodes cooperate where one attacker at a specific location encapsulates some packets and tunnels them to the second attacker, bypassing all intermediate nodes to introduce itself as the fastest route to a destination and then drop the data packets later [28]. It can also be used to replay the received data packets in the other side of the network to disrupt the routing protocol.
-
Rushing attack: In a rushing attack, the malicious node sends RREQ messages with high-power transmission to introduce itself as the shortest path to any destination with only one hop count [29], this manipulates all network nodes to use this routing path. The rushing attack is most likely used alongside another attack such as dropping the network packets that need forwarding.
|
Simulator Name |
Languages Supported |
Platform Support |
License |
Advantages |
Disadvantages |
|
OPNET |
C, C++ |
Windows, Sun Solaris, RedHat Linux |
Commercial, Free Educational License |
-User-friendly and easy to use. -Provides additional supportive tools. |
-Limited wireless mobility. -Not open source and supported protocols are limited. -Expensive. -Lack of energy model. |
|
OMNeT++ |
C++, NED |
Windows, MacOS, and any Unix-like systems |
Open source |
-Used by a wide number of users. -Extensive GUI interface. -Intelligence support. -Rich C++ libraries. -Parallelly distributed simulation is supported. |
-Documentation is poor. -Performance measures are weak. -Does not cover all protocols. |
|
NS-2 |
C++, OTCL |
Windows, MacOS, Ubuntu, Sun Solaris, Fedora Linux, and any Unix-like systems |
Open source |
-The most used simulator for research. -Good with complex systems’ evaluation. -Provides energy model. -Supports wired and wireless networks. |
-Documentation is poor. -Simulation is not real-time. -Lack of supporting tools. -Not suitable for large systems. -Difficult to use and poor GUI. -High computational overhead and memory usage. |
|
NS-3 |
C++, Python |
MacOS, FreeBSD, Linux |
Open source |
-Very fast simulator where parallel simulation is supported with real-time scheduling. -Supports emulation. -Provides debugging traces. -Organized source code with low-level abstraction. -Good documentation. |
-Lacks backward compatibility with NS-2. -Virtualization support is limited. -Difficult to use. |
|
GloMoSim |
C, PERSEC |
Windows XP/7, FreeBSD, Sun Solaris, Fedora Linux |
Free |
-Scalable and can handle very large systems with thousands of nodes. -Parallel simulation environment. -Scalable simulation library. |
-Documentation is poor. -The simulator is outdated. -Does not support end devices such as simulators.
|
|
QualNet and EXATA/cyber |
JAVA |
Windows NT/2000/XP/Professional, macOS, Sun Solaris, and most Unix-like systems |
Commercial |
-Provides animation tools. -Scalable and can handle very large systems with thousands of nodes. -Support wired and wireless networks. - Realtime simulator
|
-Slow interfaces. -Difficult to install. -Expensive. |
|
JIST/SWANS |
JAVA, Tcl |
Windows, macOS, Sun Solaris Linux |
Commercial |
-Powerful simulator and suitable for simulating real-world systems. -Less memory usage. |
-Features not competing with other simulators. |
|
J-SIM |
JAVA |
Windows, Sun Solaris Linux |
Open source |
-Supports wired and wireless networks. -Reusable models with good flexibility. |
-Worst execution time. |
-
Route request rate limits: The route request rate limit is the maximum number of RREQ packets for the source node to originate per second. The route request rate limit’s default value is ten packets per second.
-
Active route timeout: The neighbor node is recorded in the routing table and considered an active node when the active route timeout is not exceeded. When a neighbor node is active, the recorded route to this neighbor should be used [
3.2. Attacks on MANETs’ Routing Protocols
MANETs suffer from malicious activities where malicious nodes tend to impact the routing protocol mechanism. The direct impact of the attacks on routing protocols is to degrade the MANET’s performance. To disrupt the MANET routing protocol, attackers tend to use several techniques such as follows:The MANET’s environment is dynamic, and nodes continuously join and leave. An attacker could easily take a critical location in the network to block data packets from being delivered to the destination node. Moreover, a malicious node might produce a high-power signal that covers a wide range of network nodes to introduce itself as the best routing path to forward the packet between the source node and the destination node
- Routing table overflow attack: In this attack, the attacking node tends to crowd the network by advertising several non-existing nodes to overflow the routing table
- . This prevents legitimate nodes from being aware of network nodes and routing their packets normally.
- Flooding attack: In a flooding attack, malicious nodes tend to waste network resources such as memory, bandwidth, and battery by flooding the network with bogus packets [34]. For example, flooding RREQ packets prevents the MANET from functioning normally.
- DDoS attack: In a DDoS attack, attackers tend to keep the targeted legitimate node busy by continuously requesting RREQ messages from collaborative attackers at the same time without respecting the TTL time [35].
- False removal of working route: In this attack, the malicious node advertises a false state of the link with the destination node as if the link is broken. This enforces the source node to re-initiate route discovery protocol to find another path to reach the destination. Additionally, it slows down packet transmission. False removal of working route attack could be used with another collaborative attack to isolate the targeted legitimate node from MANET.
- Node isolation attack: Attackers isolate an innocent node by blocking routing information about this targeted node from the entire network [36]. This leads to an ignorance of the presence of this innocent node.
- Routing table poisoning: In this attack, the attacker sends false RREQ packets with a higher sequence number to force all nodes to delete the old genuine route to a destination and update this route with a corrupted one.
- Blackhole attack: The attacker tends to change the routing protocol packets to be the best route known for a targeted destination, and when it is requested to forward data packets to the destination node, it starts discarding the received packets to slow down the network performance [37].
- Grayhole attack: Grayhole attack is an instance of a blackhole attack where an attacker selectively drops some data packets and normally forwards others [38], or drops all packets but only at a certain time. This makes the attack difficult to detect.
- Wormhole attack: In a wormhole attack, two attacking nodes cooperate where one attacker at a specific location encapsulates some packets and tunnels them to the second attacker, bypassing all intermediate nodes to introduce itself as the fastest route to a destination and then drop the data packets later [39]. It can also be used to replay the received data packets in the other side of the network to disrupt the routing protocol.
- Rushing attack: In a rushing attack, the malicious node sends RREQ messages with high-power transmission to introduce itself as the shortest path to any destination with only one hop count [40], this manipulates all network nodes to use this routing path. The rushing attack is most likely used alongside another attack such as dropping the network packets that need forwarding.
- ]. The active route timeout default value is 3000 ms.
-
Hello interval: All MANET nodes should reveal their existence in the network within a hello interval time [16]. If a node does not contribute to the routing activities for a hello interval time, it should broadcast a hello message with TTL = 1. Hello interval default value is set to be 1000 ms.
-
Allowed hello loss: If a node does not receive any contribution to routing activities from its direct neighbor node for more than (HelloInterval × AllowedHelloLoss), the node should assume a link failure to this neighbor [17]. The allowed hello loss default value is two link failures.
-
DPC: After the delete period constant time is expired, the expired route will be deleted from the routing table [18]. The default value for DPC is 5 s.
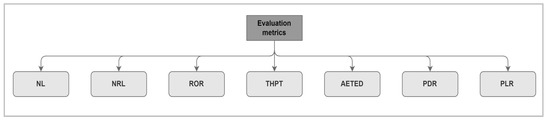
4. Evaluation Metrics and Performance Analysis in MANETs
Different evaluation metrics are used to define the characteristics of the MANET performance under certain conditions. After researchers set up the simulation environment and define the parameters needed to control the MANET environment, the results of the simulation tool need to be evaluated. To analyze the network performance, some metrics are used as follows: Figure 45 is a conclusion of the evaluation metric terms used in MANETs.