The cyberspace depicts an increasing number of difficulties related to security, especially in healthcare. This is evident from how vulnerable critical infrastructures are to cyberattacks and are unprotected against cybercrime. Users, ideally, should maintain a good level of cyber hygiene, via regular software updates and the development of unique passwords, as an effective way to become resilient to cyberattacks. Cyber security breaches are a top priority, and most users are aware that their behaviours may put them at risk; however, they are not educated to follow best practices, such as protecting their passwords. Mass cyber education may serve as a means to offset poor cyber security behaviours; however, mandatory education becomes a questionable point if the content is not focused on human factors, using human-centric approaches and taking into account end users’ behaviours, which is currently the case. The nature of the present p Paper is largely exploratory, and the purpose is two-fold: To present and explore the cyber hygiene definition, context and habits of end users in order to strengthen our understanding of users. Our paper reports the best prs report the best practices that should be used by healthcare organisations and healthcare professionals to maintain good cyber hygiene and how these can be applied via a healthcare use case scenario to increase awareness related to data privacy and cybersecurity. This is an issue of great importance and urgency considering the rapid increase of cyberattacks in healthcare organisations, mainly due to human errors. Further to that, based on human-centric approaches, ourthe long-term vision and future work involves facilitating the development of efficient practices and education associated with cybersecurity hygiene via a flexible, adaptable and practical framework.
- cyber hygiene
- cyberattacks
- healthcare
- human factors
1. Introduction
2. Cyber Hygiene in the Cyberspace
Cyber hygiene originates from the concept of personal hygiene in the public health domain. In an extensive report exploring cyber hygiene practices across various nations, the European Union Agency for Network and Information Security (ENISA) [6] introduced that “cyber hygiene should be viewed in the same manner as personal hygiene and, once properly integrated into an organisation will be simple daily routines, good behaviours and occasional check-ups to make sure the organisations online health is in optimum condition”. Research in social sciences on cyber security has been focused on the security behaviours and risk factors of the end–end users, while there is limited research on developing measurements of cyber hygiene. In particular, according to previous approaches that assume that the end users are aware of cyber safety behaviours, they, therefore, focus on measuring the frequency of enactment of these behaviours [7]. It is of high importance to understand the role of how end users are processing information and their interpretation within a cybersecurity framework in an organisation. For instance, researchers have empirically demonstrated that individuals who systematically process information are less likely to get victimised during a spear phishing attack [8]. Therefore, plenty of cybersecurity awareness programs aim to enhance the ability of the users to process better information. The lack of cyber hygiene leads to a number of cyber threats and cyberattacks. The recent WannaCry Ransomware cyberattack [9], which targeted, on a large scale, the Microsoft Windows operating system, had a severe impact on the systems. This occurred due to the organisations and individuals not having updated their software security versions as of the month of March, even though the more recent version had been released in 2014. This is why unlicensed Windows software and systems with outdated software versions became vulnerable and easy to exploit in this attack. The healthcare ecosystem was particularly affected by CT and MRI scanners being exploited in hospitals, among banking, business and corporate sectors worldwide. Around 300,000 computer systems in 150 countries were affected.3. Human Behaviours: The Weakest Link in Cyberattacks
A significant number of cyberattacks are directed towards the users through distorted means, such as malicious emails and masqueraded applications. Though cyberattacks are aiming to exploit either the technical vulnerabilities of networks and systems, or the errors due to human behaviour, it is the latter that remains as the weakest link in these cyberattacks [10][11]. Attackers most often employ methods exploiting weak cyber behaviours, defined as social engineering. Studies historically confirm that social engineering approaches account for the majority of total cyber security attacks. Bowen et al. [12] showed that 28% of the total attacks were due to social engineering, and in 2016, 97% of malware attacks targeted human behaviour. A more recent report estimated that 95% of cyberattacks were again attributed to human errors and risky behaviour [13]. Looking in the literature at the types of risky behaviours and human errors, one can identify the most common, including the use of infected memory disks, sharing of passwords, reusing the same passwords for different platforms, not updating software, unauthorised disclosure of personal information, accessing fake emails and installing software from unverified sources [14][15][16][17][18].4. Cyber Threats and Countermeasures in Healthcare 4.0
There are several attacks that occur daily within healthcare 4.0. However, as found in the literature, there are six main types of cyber threats that can be identified in the cyberspace, and are directly applied in healthcare 4.0, accompanied by appropriate countermeasures [4], which are presented in detail in Table 1.| Cyber Threat | Description |
|---|---|
| ] | |
| . These types of attacks can be tackled by carrying out countermeasures, as for example, software isolation; “secured boot”, meaning that when any malicious activities are carried out in the system, after rebooting the system, it then does not turn on and all the available data in the system becomes resilient to the attacker; and/or software update, which maintains the software and its system updated with the latest version available on the market. | |
| Security Misconfiguration | |
| This type of attack is being performed due to inattentiveness or carelessness. The moment when it has been observed to occur is when handling the security changes of the software, as the security changes become misconfigured and provide the attackers with the right opportunity to attack the devices and extract the available data from them. Hence, the most significant countermeasure is that the security changes ought to be carried out with extreme care and with proper decryption encryption techniques as well | [21]. |
5. Towards a Human-Centric Approach to Security
Human behaviour is the weakest link in cybersecurity; it is the employees of any organisation that should be involved and engaged within cybersecurity awareness and the development of mitigation approaches.
Furthermore, as a result of the global COVID-19 pandemic, new working trends have been introduced, where employees working flexibly use their own devices or are using work devices outside the office, resulting in blurred lines between personal and business limits, exacerbating the risky behaviours. As a result, any measures to mitigate the cyber risks need to go beyond the software updating and hardware maintenance to a more human-centric approach. Human-centric cyber security is still a new domain, which is an intangible concept and is challenging to define and to be understood, not only by the lay end user, but also by specialists in cyberspace. The reason is that it sits at the intersection of human behaviour, computing and security systems. Grobler et al. (2021) [24] defined human-centric cyber security as involving all aspects of cyber security, with a particular focus on the human involvement in the system and processes. They propose for the design, implementation and assessment of holistic human centric cyber security systems, three components of what they define as the 3U’s, User, Usage and Usability, with each one of them including further subsections, as seen in Table 2.| Component | Description | ||
|---|---|---|---|
| Attacks on Hosted Components | These types of attacks include destructive software injection to a targeted system, for example, cross-site scripting, SQL injection and related techniques, which threaten the access and/or authentication controls. This may occur in cloud-based control systems handling big volumes of sensitive data. Here, the countermeasures include mainly role-based approaches, creating awareness in order to protect towards impersonation at the cloud level and API authentication. | ||
| User |
|
||
| Social Engineering | It refers to the attacks performed on the “weakest link” in the security supply chain. This is achieved by psychologically manipulating individuals to perform malicious actions or share confidential information. Common techniques used for this manipulation are shoulder surfing, diversion theft, “dumpster diving”, impersonation of help desk calls, phishing and/or personal blackmailing [19][20]. Social engineering is one of the major reasons why even security-aware and well-equipped companies fall victims to cyberattacks. Hackers identify the weakest link in the security supply chain in which they can insert the malicious software or the virus into the targeted system. Therefore, it is of great importance to identify and further secure the weakest link in the security chain. Some of the initial countermeasures, which can be adopted to prevent upcoming attacks, include block Wi-Fi connections to unsecured networks, block network connections related to malicious content, stop using non-secure web pages and websites and performing actions on them. Further approaches, which can be taken to reduce the high level of cyberattacks, include mitigating known threats in the systems and applications, regularly patching vulnerable systems and/or keeping the company’s devices up-to-date with the latest version. | ||
| Usage |
|
Physical Attack | |
| Usability | Physical attacks are mostly carried out in fields involving several Internet of Things (IoT) applications since they are connected to a number of components and hardware devices. These are easily located by hackers since they cannot be monitored at a single location and are kept far away from each other [21] |
|
|
|
Network Compromise | These attacks are known as ‘middle way attacks’ where the hackers use a number of techniques, for example, altering or blocking communications between hardware devices and their cloud-based controller session and/or hijacking to enter and disrupt a network. The countermeasures that can be offered here include performing regular updates on the software and use of proper file decryption and encryption techniques while sending and receiving sensitive data between the end-to-end users. | |
| Hacked Device Software | In these attacks, the hacker accesses the software at the device level and then it carries out several fraudulent activities and techniques. Such activities and techniques target to take control of the data in the system and include elevation of privileges, denial of service, malware injection and/or false identification [23 |
6. Best Practices and Education of Cybersecurity Hygiene for Healthcare Professionals
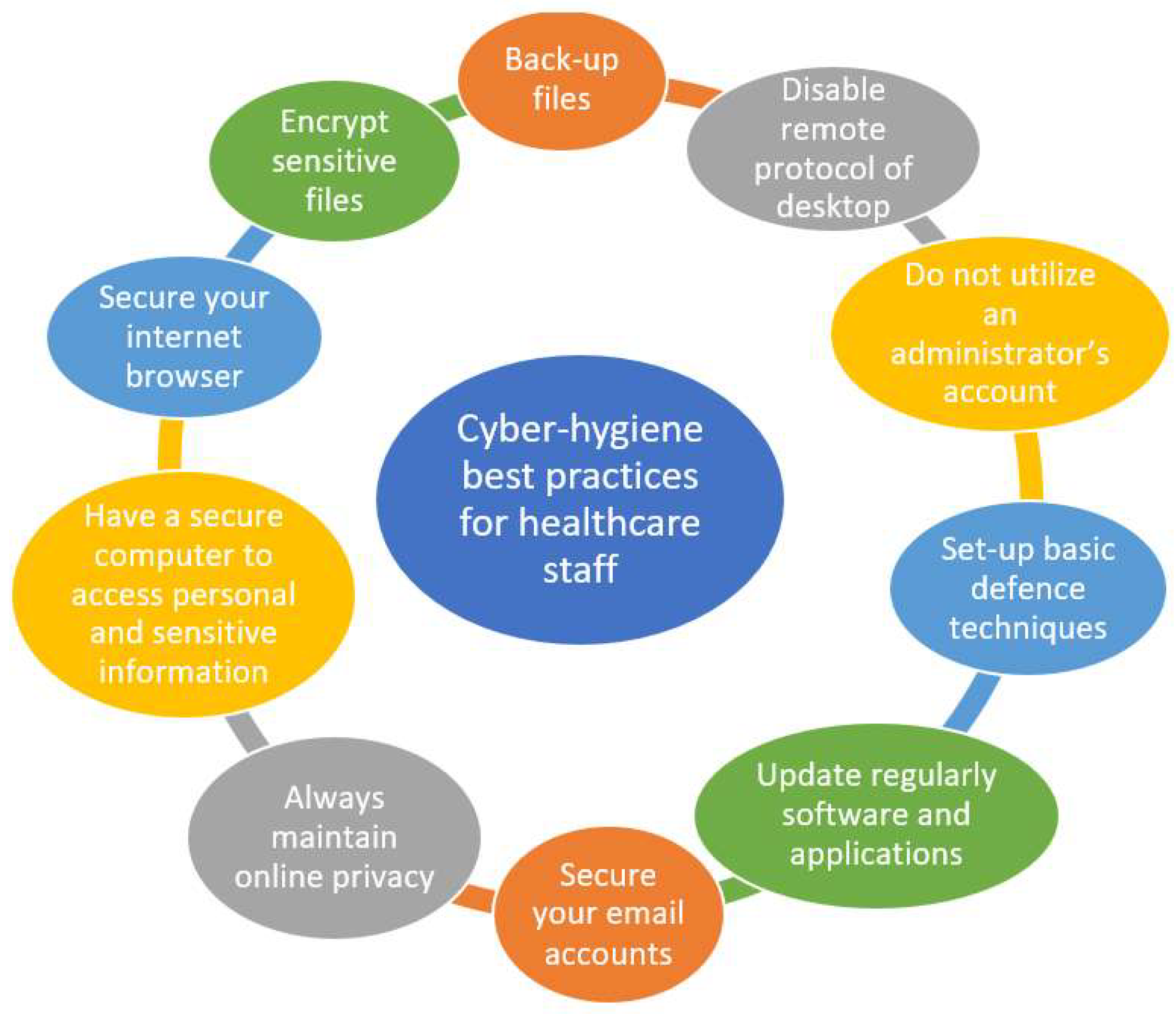
Cyber threats are rapidly increasing across various business sectors and the incidents in data privacy and cybersecurity breaches are also rising alongside them, particularly in the healthcare domain. In response to the rising threats and incidents, healthcare organisations adopt technical measures, such as the use of firewalls, antivirus and software/firmware patches, aiming to preserve and protect the business continuity of healthcare services. Regardless of such efforts, cybersecurity threats are rising, and the adopted measures have been proven insufficient to respond to cyberattacks. This is often because the important role that the personnel play in this supply chain, related to cyber defence, is not being considered. In practice, healthcare organisations are encouraged to adopt general data privacy and cybersecurity guidelines that have, as a focal point, the human factor. Nevertheless, there is limited research within the literature on collective practical cyber hygiene guidelines and best practices, which can help healthcare organisations to apply specific interventions, such as training programs and awareness activities, which at the same time are measurable to the healthcare professionals. With that being said, structured best practices that would assist the higher management to choose the optimal number of security controls that will be most efficient for healthcare organisations and professionals are yet not available and, at the same time, are highly desirable. Cybersecurity hygiene best practices and education are linked to individual differences aiming to improve cybersecurity. Even though Internet security guidelines for users are widely available, it is doubtful how many consumers understand and apply these reports and if the available security guidelines are written in a lay language for both tech laggards and tech savvy users [25]. One feasible solution in order to overcome the educational gap in cybersecurity would be to establish best practices and mandatory cyber hygiene education for users, including both non-cyber and cyber professionals [26][27]. Best practices and mass cyber education may contribute to discourage poor cybersecurity behaviours; however, to achieve the most optimal results, the content should shift its focus to human factors and use behaviours. It is evident that most available courses and/or training do not address explicitly human cognition and behaviours. The baseline cyber hygiene involves several basic steps that are required for cyber defence. The baseline practices are mostly rooted in frameworks, such as, for example, the NIST cybersecurity framework. It helps organisations, including the healthcare supply chain, to have a detailed and clear set of best practices to show and modify how cybersecurity is being performed and measured regularly [28]. While there are not standardised best practices for healthcare, a basic set of methods to maintain cyber hygiene in business has been presented in the literature [29][30]. All organisations and cyber users need to take responsibility for their browsing in both their personal and professional space. Individuals must take ownership of maintaining sufficient cyber hygiene and safeguarding, by using best practices, against cyberattacks [4]. Best practices, as collected from the literature, are presented in Figure 1.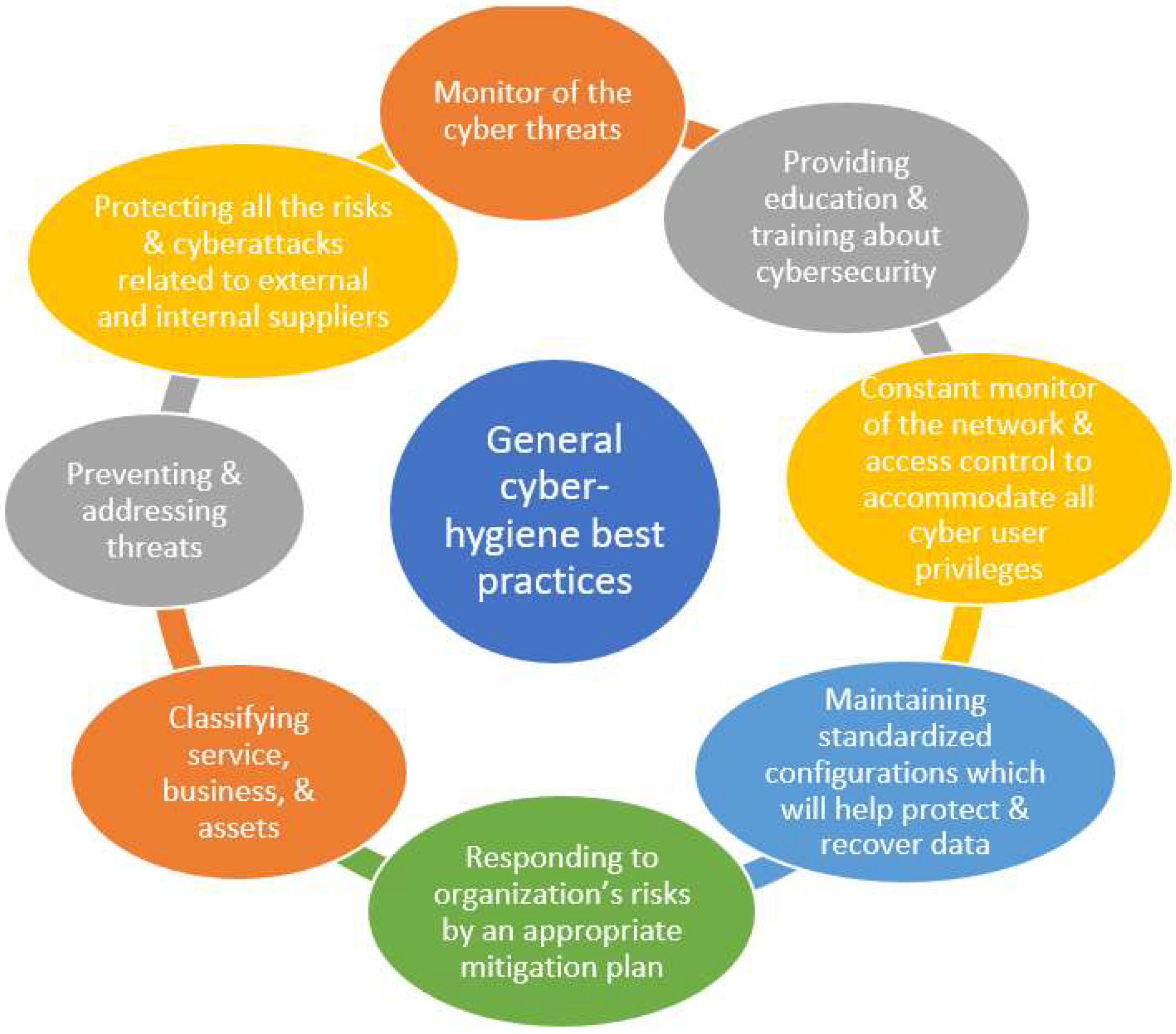
References
- Liaropoulos, A. A Human-Centric Approach to Cybersecurity: Securing the Human in the Era of Cyberphobia. J. Inf. Warf. 2015, 14, 15–24.
- Javid, T.; Faris, M.; Beenish, H.; Fahad, M. Cybersecurity and data privacy in the cloudlet for preliminary healthcare big data analytics. In Proceedings of the 2020 International Conference on Computing and Information Technology, Tabuk, Saudi Arabia, 9–10 September 2020; pp. 1–4.
- Thuemmler, C.; Bai, C. Health 4.0: Application of industry 4.0 design principles in future asthma management. In Health 4.0: How Virtualization and Big Data Are Revolutionizing Healthcare; Springer: Berlin/Heidelberg, Germany, 2017; pp. 23–37.
- Singh, D.; Mohanty, N.; Swagatika, S.; Kumar, S. Cyber-hygiene: The key Concept for Cyber Security in Cyberspace. Test Eng. Manag. 2020, 83, 8145–8152.
- Cain, A.; Edwards, M.; Still, J. An exploratory study of cyber hygiene behaviors and knowledge. J. Inf. Secur. Appl. 2018, 42, 36–45.
- European Union Agency for Network and Information Security (ENISA). Review of Cyber Hygiene Practices. 2016. Available online: https://www.enisa.europa.eu/publications/cyber-hygiene (accessed on 30 November 2022).
- Trevors, M. Mapping Cyber Hygiene to the NIST Cybersecurity Framework. 2019. Available online: https://insights.sei.cmu.edu/insider-threat/2019/10/mapping-cyber-hygiene-to-the-nist-cybersecurity-framework.html (accessed on 3 January 2023).
- Vishwanath, A.; Neo, L.S.; Goh, P.; Lee, S.; Khader, M.; Ong, G.; Chin, J. Cyber hygiene: The concept, its measure, and its initial tests. Decis. Support Syst. 2020, 128, 113–160.
- Ehrenfeld, J.M. Wannacry, cybersecurity and health information technology: A time to act. J. Med. Syst. 2017, 41, 104.
- Kelly, R. Almost 90% of Cyber Attacks Are Caused by Human Error or Behaviour. 2017. Available online: https://chiefexecutive.net/almost-90-cyber-attacks-caused-human-error-behavior/ (accessed on 5 December 2022).
- Annarelli, A.; Nonino, F.; Palombi, G. Understanding the management of cyber-resilient systems. Comput. Ind. Eng. 2020, 149, 43–59.
- Bowen, B.; Devarajan, R.; Stolfo, S. Measuring the human factor of cyber security. In Proceedings of the 2011 IEEE International Conference on Technologies for Homeland Security (HST), Waltham, MA, USA, 13–16 November 2011; Volume 1, pp. 198–207.
- Nobles, C. Botching human factors in cybersecurity in business organizations. Holistica 2018, 9, 71–88.
- Dragana, C.; Pattinson, M.R.; Parsons, K.; Butavicius, M.A.; McCormac, A. Naïve and Accidental Behaviours that Compromise Information Security: What the Experts Think. In Proceedings of the 10th International Symposium of Human Aspects of Information Security and Assurance, Frankfurt, Germany, 19–21 July 2016; Volume 1, pp. 32–52.
- Baillon, A.; Bruin, J.; Emirmahmutoglu, A.; Veer, E.; Dijk, B. Informing, simulating experience, or both: A field experiment on phishing risks. PLoS ONE 2019, 14, e0224216.
- Hakim, Z.; Ebner, N.; Oliveira, D.; Getz, S.; Levin, B.E.; Lin, T.; Wilson, R.C. The phishing email suspicion test (PEST) a lab-based task for evaluating the cognitive mechanisms of phishing detection. Behav. Res. Methods 2021, 53, 1342–1352.
- Kobis, P. Human factor aspects in information security management in the traditional IT and cloud computing models. Oper. Res. Decis. 2021, 31, 61–76.
- Richardson, M.D.; Lemoine, P.A.; Stephens, W.E.; Waller, R.E. Planning for Cyber Security in Schools: The Human Factor. Educ. Plan. 2020, 27, 23–39.
- Moustafa, A.A.; Bello, A.; Maurushat, A. The Role of User Behaviour in Improving Cyber Security Management. Front. Psychol. 2021, 12, 224–231.
- Moustafa, A.A.; Morris, A.N.; Elhaj, M. A review on future episodic thinking in mood and anxiety disorders. Rev. Neurosci. 2018, 30, 85–94.
- Chen, H.; Zhongchuan, F.; Dongyan, Z. Security and trust research in M2M system. In Proceedings of the 2011 IEEE International Conference on Vehicular Electronics and Safety, Beijing, China, 10–12 July 2011; Volume 1, pp. 286–290.
- Sung-Ming, Y.; Kim, S.; Lim, S.; Moon, S. A countermeasure against one physical cryptanalysis may benefit another attack. In Proceedings of the International Conference on Information Security and Cryptology, Seoul, Republic of Korea, 6–7 December 2001; pp. 414–427.
- Gregory, R.G.; Fitzgerald, J.; Hunsperger, N.; Lavine, J.; Nguyen, V.; Tellado, J. Service Processor Configurations for Enhancing or Augmenting System Software of a Mobile Communications Device. U.S. Patent Application 14/083,324, 3 March 2014.
- Grobler, M.; Gaire, R.; Nepal, S. Usage and Usability: Redefining Human Centric Cyber Security. Front. Big Data 2021, 4, 344–452.
- Symantec, C.D. Internet Security Threat Report: 2011 Trends. Symantec Corp. 2012, 17, 977–999.
- Dupuis, M.J. Cyber security for everyone: An introductory course for nontechnical majors. J. Cybersecur. Educ. Res. Pract. 2017, 3, 1–17.
- Sobiesk, E.; Blair, J.R.; Conti, G.; Lanham, M.; Taylor, H. Cyber education: A multilevel, multi-discipline approach. In Proceedings of the 16th Annual Conference on Information Technology Education, London, UK, 4–8 September 2015; Volume 1, pp. 43–47.
- Molinara, M.; Cancelliere, R.; Di Tinno, A.; Ferrigno, L. A Deep Learning Approach to Organic Pollutants Classification Using Voltammetry. Sensors 2022, 22, 8032.
- Ncubukezi, T.; Mwansa, L. Best practices used by businesses to maintain good cyber hygiene during COVID-19 pandemic. J. Internet Technol. Secur. Trans. 2021, 9, 714–721.
- Trevors, M.; Wallen, C.M. Cyber Hygiene: A Baseline Set of Practices; Software Engineering Institute, Carnegie Mellon University: Pittsburgh, PA, USA, 2017; pp. 1–17.
- Cyber Essentials. 2020. Available online: https://www.gov.uk/gov (accessed on 26 January 2023).
- Such, J.M.; Cholas, P.; Rashid, A.; Vidler, J.; Seabrook, T. Basic cyber hygiene: Does it work? Computer 2019, 52, 21–31.
- NIST Special Publication 800–181. 2017. Available online: https://www.nist.gov/itl/applied-cybersecurity/nice/nice-framework-resource-center (accessed on 3 October 2022).
- Mehravari, N. Resilience management through the use of CERT-RMM and associated success stories. In Proceedings of the IEEE, International Conference on Technologies for Homeland Security (HST), Vienna, Austria, 17–20 October 2013; Volume 1, pp. 119–125.
- Martin, R.A. Non-Malicious Taint: Bad Hygiene Is as Dangerous to the Mission as Malicious Intent. 2014; Volume 1, pp. 19–30. Available online: https://apps.dtic.mil/sti/pdfs/AD1107757.pdf (accessed on 4 November 2022).
