Your browser does not fully support modern features. Please upgrade for a smoother experience.
Please note this is a comparison between Version 1 by Lamia Alhoraibi and Version 2 by Lindsay Dong.
The physical layer security of wireless networks is becoming increasingly important because of the rapid development of wireless communications and the increasing security threats. In addition, because of the open nature of the wireless channel, authentication is a critical issue in wireless communications. Physical layer authentication (PLA) is based on distinctive features to provide information-theory security and low complexity.
- physical layer authentication
- physical layer security
- wireless networks
1. Wireless Network
A network’s architecture defines the protocols and components required to meet application needs. The open systems interconnection (OSI) Model practically represents a wireless network’s different standards and compatibility. The OSI model is a conceptual framework that outlines how data are exchanged within a computer network from one device to another. The OSI model describes a complete set of network services within each network component organized into layers, illustrated in Figure 1. Each layer consists of a collection of conventional communication protocols and customized components to accomplish specific functions.
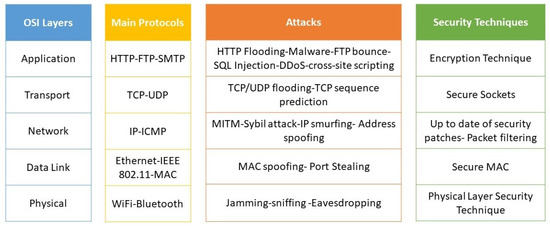
Figure 1. A generic wireless OSI Model information consisting of the layers, main protocols, main attacks, security techniques.
1.1. Physical Layer
The physical layer is the only layer in the OSI model interacts with actual hardware, transmission, and signaling mechanisms. The physical layer transmits raw bits over a physical data link connecting network nodes by converting them to electrical pulses, representing the binary data. The electric pulses are then converted to electromagnetic waves to be transmitted wirelessly. On the other hand, the physical layer specifies the data transmission mechanism and how data can move between devices.
1.2. Wireless Physical Layer Protocols
A generic wireless OSI Model information consisting of the layers, main protocols, main attacks, security techniques.
.1. Physical Layer
The physical layer is the only layer in the OSI model interacts with actual hardware, transmission, and signaling mechanisms. The physical layer transmits raw bits over a physical data link connecting network nodes by converting them to electrical pulses, representing the binary data. The electric pulses are then converted to electromagnetic waves to be transmitted wirelessly. On the other hand, the physical layer specifies the data transmission mechanism and how data can move between devices.
1.2. Wireless Physical Layer Protocols
Recently, massive of advanced wireless technologies and dozens of different wireless protocols meet the needs, each with its performance characteristics and optimized for a specific task and context. However, various wireless protocols exist, such as WiFi, Bluetooth, ZigBee, NFC, WiMAX, LoRa, 5G, satellite services, and more. Therefore, it is necessary to be aware of the system’s constraints and performance requirements when choosing protocols. Power, data rate, reliability, and range are essential metrics for distinguishing between protocols [1][27].1.3. Wireless Networks Physical Layer Threats
The openness of wireless networks produces communication more vulnerable to attacks, which poses severe challenges for network security. Wireless networks have security vulnerabilities, such as [1][2][3][4][4,6,27,32]: Eavesdropping: Unauthorized and unannounced interception of communications between devices. Through eavesdropping, the intercepted messages can be exploited for future illegal purposes. Eavesdropping attackers can be categorized as active eavesdroppers and silent eavesdroppers. The distinction is that active eavesdroppers acting as communication parties unintentionally send signals to transmitters, which channel state information (CSI)CSIs can extract through estimation. On the other hand, silent eavesdroppers snoop on messages while being silent, where their CSIs are not available for transmitters. Therefore, this kind of threat can be divided into two types based on the manner of the attacker: interception and traffic analysis.-
Interception: Eavesdropping is the most common attack on wireless devices’ privacy. The attacker could find legitimate communication by snooping in the nearby wireless environment when the traffic transmits control information about the sensor network configuration.
-
Traffic Analysis: The ability to track communication patterns to facilitate various types of attacks.
-
Proactive Jamming: Proactive jamming attackers spread interfering signals whether the legitimate signal communication is there or not. To save energy and toggle between the sleep and jamming phases, attackers sporadically spread random bits or normal packets into networks. Attackers sporadically broadcast either random bits or conventional packets into networks to preserve energy and rotation between the sleep and jamming phases.
-
Reactive Jamming: Attackers that use reactive jamming can monitor the legitimate channel’s activity. If there is an activity, the attacker transmits a random signal to interfere with the existing signal on the channel.
2. Physical Layer Security
The world has become increasingly online and connected via wireless networks recently. Additionally, wireless devices are increasingly employed in a variety of sectors. For example, smart things, mobile communication, unmanned platforms, drone control, autonomous driving, etc. Unlike wired networks, the openness of the wireless network allows nearly all wireless receiving devices within their range to receive signals [5][6][33,34]. This feature gives legal and illegal users the same access to the communication channel. However, protecting the integrity, confidentiality, and availability is challenging in wireless networks [5][33]. Information security mainly depends on cryptographic techniques to achieve communication security requirements, including authenticity, confidentiality, integrity, and availability [2][7][8][2,4,35]. Authenticity verifies communicating entities. Data integrity validates that transmitted data are not changed. Data confidentiality assures that transmitted data did not expose to unauthorized entities. Finally, data availability prevents adversaries from interrupting access to data. Using encryption-based security technologies at application layers has enhanced wireless security. Still, their inherent vulnerabilities are heavy computation and key management, resulting in high complexity and resource consumption [7][8][9][2,35,36]. Cryptographic techniques have efficiently protected modern communication and computer networks. However, it is not entirely suited to the future of ubiquitous computing, which will be elaborated on in the following. Traditional cryptographic approaches are computationally secure because the attacker cannot decipher the protection within a specific time. However, it may be compromised due to the progress in quantum computing advances. However, because of advances in quantum computing, it may be compromised. For example, the quantum search algorithms such as Grover’s and Shor’s algorithms exploited the discrete logarithm problem that current cryptographic mechanisms heavily rely on [10][37]. Traditional authentication techniques are based on the IP or media access control (MAC) addresses as the identity, which can be easily tampered with by malware attackers [11][12][38,39]. In addition, cryptographic algorithms rely heavily on computational complexity and secret keys [13][14][5,28]. As a result, these algorithms perform effectively on devices with high processing capabilities, like smartphones. In comparison, many IoT devices are low cost and small, equipped with limited storage memory, and powered with batteries, making it impractical to implement complicated cryptography-based security protocols. Shannon first considered the confidentiality of physical layer security (PLS) was assumed in 1949 and proposed the first application of information theory to cryptology, also known as Shannon’s information-theoretic secrecy [15][40]. Then, approximately three decades later, one of the most targeted studies the physical layer confidentiality is to maximize the secret information rate received by the legitimate user in the wiretap channel, which is defined as the secrecy capacity by Wyner [16][41]. Wyner’s work set the basis and inspired PLS research, with scholars proposing various PLS techniques for different purposes. Wireless network security was previously thought to be a high-layer problem that could be handled with cryptographic approaches [17][42]. The situation changed in the first decade of the 21st century when wireless networks started to spread around [10][37]. Therefore, physical layer security based on information theory has appeared as a promising approach to protecting wireless communications to achieve information-theoretic security against eavesdropping attacks, for instance. Compared to cryptographic techniques executed at upper layers, physical layer security offers two significant advantages:-
First, physical layer security techniques do not rely on computational complexity compared to cryptography techniques [2][11][18][19][20][3,4,26,38,43]. As a result, the achieved level of security will not be compromised; even if the unauthorized devices in the wireless network are provided with powerful computational capabilities, secure and safe communications can still be performed.
3. Physical Layer Authentication
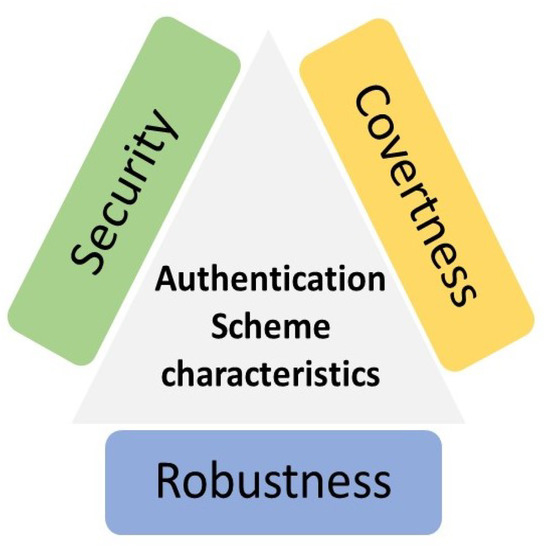
The inherent broadcast nature of wireless communications raises security and privacy issues where adversaries can launch different types of attacks. Accordingly, authentication is an important issue in wireless communications [21][29]. Device identity authentication requires safeguarding wireless networks to validate whether the users are legitimate and allowing them to access the network while preventing malicious users [12][39]. Most existing wireless communication systems perform authentication through upper-layer authentication techniques that are typically implemented using cryptography-based authentication algorithms [12][39]. However, traditional authentication approaches depend on software addresses such as IP and MAC addresses, which can be tampered with or forged [22][44]. Once adversaries obtain the security credentials, they can pretend as legitimate users to reach private data and launch severe attacks on the wireless devices [22][23][44,45]. However, upper-layer authentication mechanisms based on traditional cryptography-based algorithms are unsuitable for advanced wireless communication systems [21][29]. For example, cognitive radio networks, Internet of Things (IoT)T, internet of vehicles (IoV), smart grids networks, and unmanned aerial vehicles (UAV) because of the following issues [3][12][21][24][6,29,39,46]: With the advancement in computational power and cryptanalysis algorithms, the time it takes to crack a cryptography key has been drastically reduced. However, because the upper layer signaling is not altered, the replayed signal can successfully spoof the legitimate receiver. Therefore, the complicated cryptography techniques in upper-layer operations, e.g., encryption, decryption, and frequent authentication handovers, are unsuitable with limited capability for wireless devices. Furthermore, the process of key sharing and management introduces overhead concerns in massive ubiquitous computing scenarios, such as the amount of storing excessive keys or defending against the eavesdropping attacks of frequent exchanging keys. Wireless physical layer authentication is a method of validating a wireless transmitter by checking the physical layer characteristics of the communication [24][46]. A good authentication scheme should generally have three characteristics: covertness, robustness, and security [14][28], as demonstrated in Figure 2.
Figure 2.
Authentication Scheme Characteristics.
-
The covertness means that any authentication schemes should not significantly affect the performance of the standard data transmission, do not occupy too much communication overheads or extra computational resources, and do not harm the existing conventional higher-layer cryptographic-based techniques.
-
Robustness requires that the PLA framework is robust enough to mitigate channel fading and noise interference.
-
Security is the kernel of PLA systems, representing the ability to prevent the authentication procedure from being interrupted or invaded by eavesdroppers.
-
The PLA allows a legitimate receiver to easily distinguish between a legitimate and adversary transmitter without upper-layer processing, decreasing computational complexity and processing delay.
-
There is no key distribution and management need with PLA compared to conventional secret key-based authentication schemes. Instead, some existing physical layer authentication approaches rely on analog channel information and device-specific characteristics caused by manufacturing variability.
-
In a heterogeneous coexistence system, incompatible devices may not be able to decode each other’s upper-layer signaling, but they should be able to decode the physical layer bit-streams.
-
The PLA presents information-theoretic security, where the physical layer puts adversaries in a state of uncertainty.
