In the 6G network, with blockchain and unmanned aerial vehicles (UAVs) authentication, the network decentralization and resource sharing would minimize resource under-utilization thereby facilitating PG targets. Furthermore, through an appropriate selection of blockchain type and consensus algorithms, the SG’s needs of UAV authentication in 6G network applications can also be readily addressed.
- 6G
- unmanned aerial vehicles
- UAVs
- : 6G
1. Introduction
2. UAV Communication
Unmanned aerial vehicles (UAVs) have enormous potential in the universal domains including civil, defense, media and public domains [8]. They have unprecedented and useful applications where human lives can otherwise be in danger. In addition to this, multi UAV systems are jointly mission capable and can accomplish the same but better economy, precision and efficiency compared with solo UAV systems. However, there are many concerns that are required to be resolved before the effective use of unmanned aerial vehicles for the provision of reliable, assured and context-focused networks. In view of the distinctive characteristics of the UAV networks and the need to address related issues, considerable work is yet to be carried out in this area. Current progress in the domain of mobile adhoc networks (MANETs) and vehicular adhoc networks (VANETS) is not sufficient to address the peculiar nature of UAV networks. UAV networks may vary from slow dynamic to dynamic as some have intermittent links and topology that is relatively fluid.
2.1. Characterizing the UAV Network
2.1.1. Multi UAV Network
The utilization of a single large UAV for a mission was common in the early days of UAV use. As a result, in these systems, the UAV-based communication network only had one aerial node and one or more terrestrial nodes. The UAVs in a multi UAV system are smaller and less expensive and they have the ability to work together. multi UAV systems may now be used to carry out most public and civic applications more efficiently [9]. The communication network, which ensures communication between UAVs and between UAVs and ground nodes, constitutes a key component in most multi UAV systems. These UAVs can be designed to cooperate together to provide services and function as relays to extend network coverage. The mobility of UAVs is determined by the application. For example, in order to provide communication in an earthquake-stricken area [10], UAVs would hover over the operation area and the linkages would be slow and dynamic. The fact that the UAVs may go out of service due to failure or battery drain demonstrates the dynamic nature of the network setup and connectivity. Agricultural and forest monitoring applications, on the other hand, demand UAVs to move across a vast region, with links breaking and reestablishing often. This is also true for UAVs that must hover over an area for extended periods of time. To take their place, new unmanned aerial vehicles must be launched. Some of the UAVs may be pulled out of operation to save power until a more appropriate time comes. As a result, it would be a requirement that the linkages immediately reconfigure themselves in all such circumstances. Multi UAV systems, while beneficial in many ways, complicate the UAV communication network. Reliability and survivability through redundancy are two significant advantages of multi UAV systems. When a single UAV fails in a multi UAV system, the network must reorganize and retain communication through other nodes. In a single UAV system, this would be impossible. However, in order to gain the full benefits of numerous UAVs operating together in a multi UAV topology, the protocols in place must address concerns such as power limits, mobility and changing topology [11]. Figure 2 illustrates the multi UAV system; each UAV struggles to address mobility and varying link’ quality dividends in an ever changing topology during the flying role. As per interference requirements, the UAV link selection and topology should be dynamically optimized. The phenomenon is a governing element in terms of authentication protocol implementation in a multi UAV network. A single UAV system would have to maintain communication linkages with the control station(s), servers and base stations as well as provide access for functionality. The limited battery power and bandwidth are severely hampered as a result.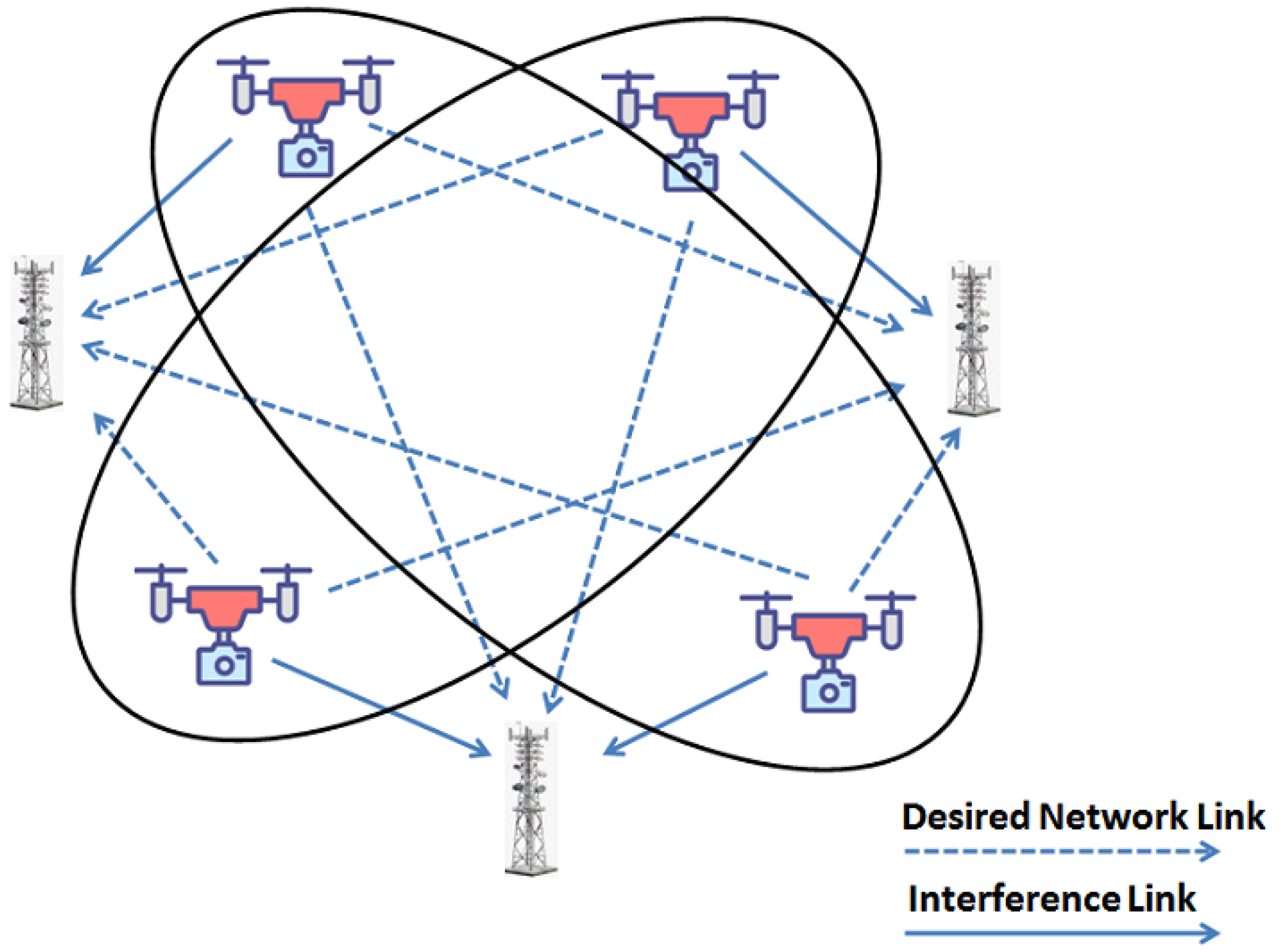
2.1.2. Infrastructure-Based or Adhoc UAV Networks
2.1.3. Server or Client?
Whether the node is in the role of server or client is another distinction. In vehicular networks, the nodes are usually servers and in adhoc networks, the nodes usually act as clients [13]. UAV nodes usually act as servers and perform relaying functions of sensor data and packet forwarding [14]. They are also utilized for provision of data forwarding to other UAV clients. Figure 3 is a depiction of a widely used server–client implementation of UAV network is surveillance mode.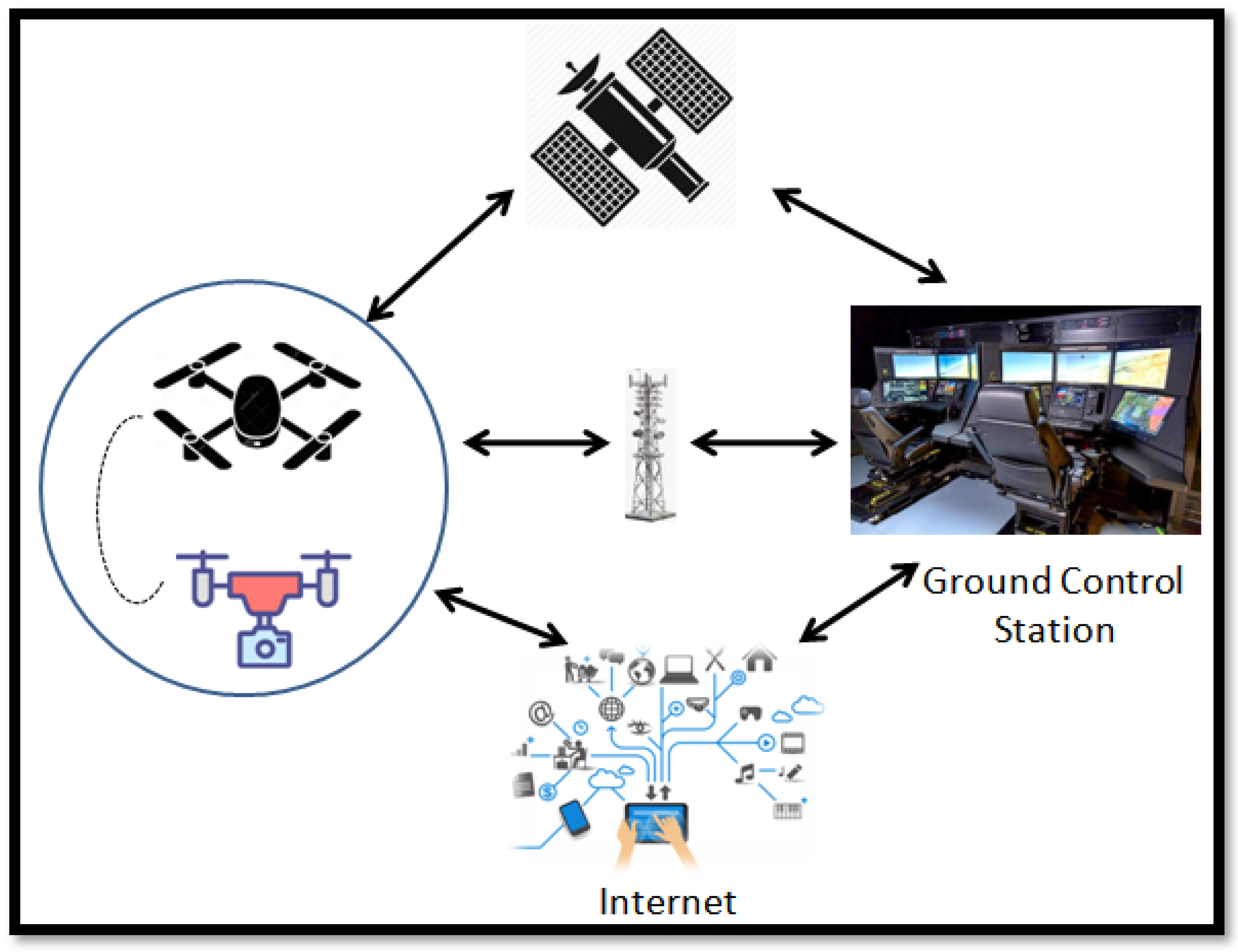
2.1.4. Star or Mesh?
2.2. Security in UAV Communication
Internet of Things (IoT) acts as an interface between the physical world and computing systems; IoTs perform this role by transfer of information regarding the physical atmosphere after sensing and necessary analysis. Internet of Drones (IoD) is a classic mobile IoT system [15][16]. In the latest years, unmanned aerial vehicles and drones have become a popular application in several fields due to its inherent characteristics including reach, exploratory abilities, flexibility, speed, life safety in case of difficult missions and coverage, etc. Keeping in mind advancements in this domain, the public’s demand has invariably increased. Moreover, there is increased demand against consumer grade drones across the globe as engagement of UAVs in different applications and roles is becoming widespread. The employment of UAVs in various fields has increased manifold, including in shooting movies, drone selfies, agriculture businesses, and security objectives; all are utilizing these aerial devices. Growth in UAV commerce is expected to accelerate upwards at a rate of at least 29.9% per annum in upcoming years. Moreover, the industry volume is expected to rise to approximately 4.9 billion dollars at the end of the coming three years [17]. Two critical properties of UAVs as a smart IoT apparatus are resource limitations and the varying environment. Moreover, UAV network connection conditions including AP servers are subject to constantly changing position and environments. Consequently, the identity of every element of the UAV network must be periodically authenticated in multiple cycles. Moreover, due to the mobility of these smart devices, which are embedded with smart features, they face noteworthy limitations such as power constraints and processing power. Furthermore, the endurance of these devices and other abilities will be adversely affected if an excessively recurrent and sophisticated authentication scheme is defined for them [18].3. UAV 6G Networks
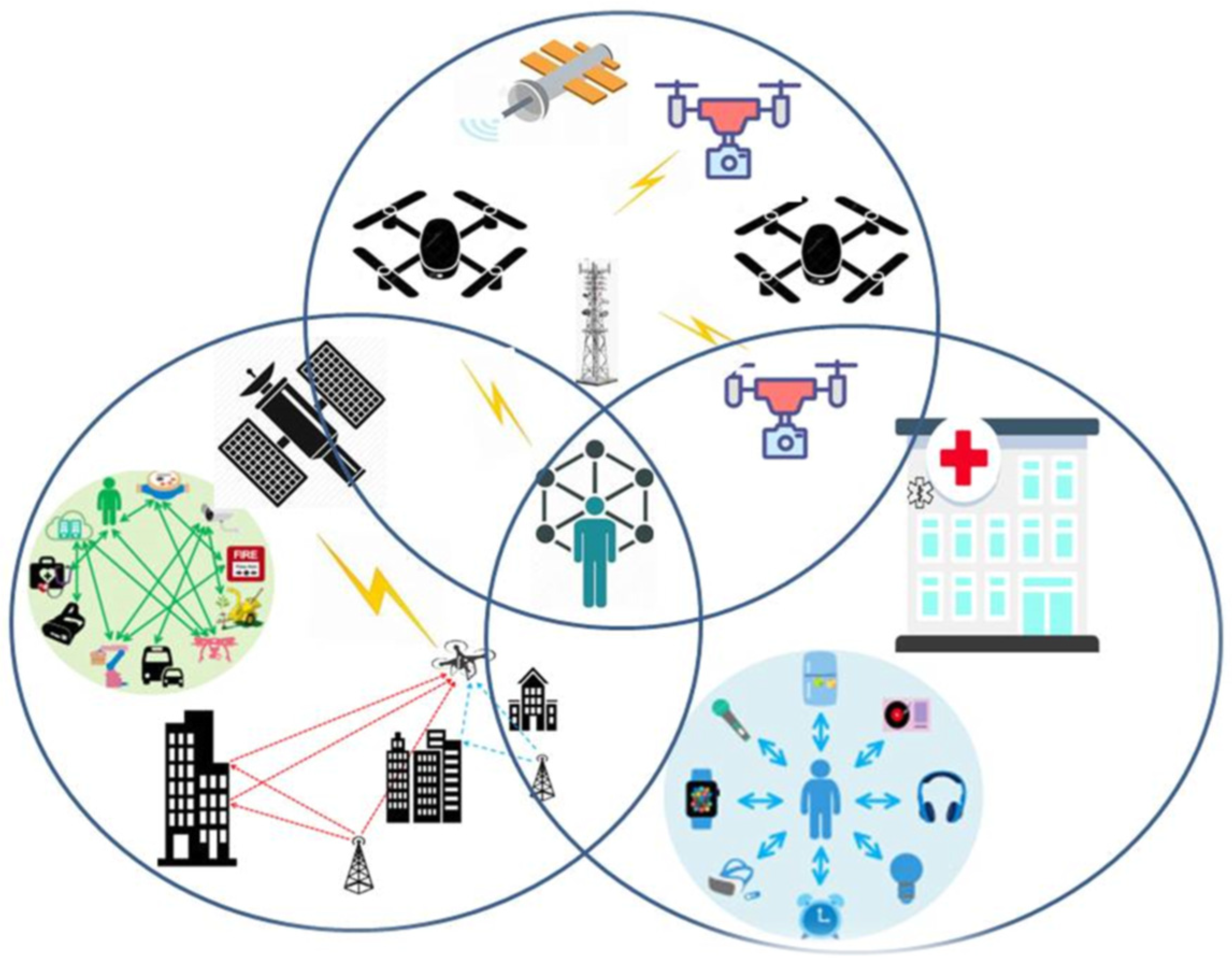
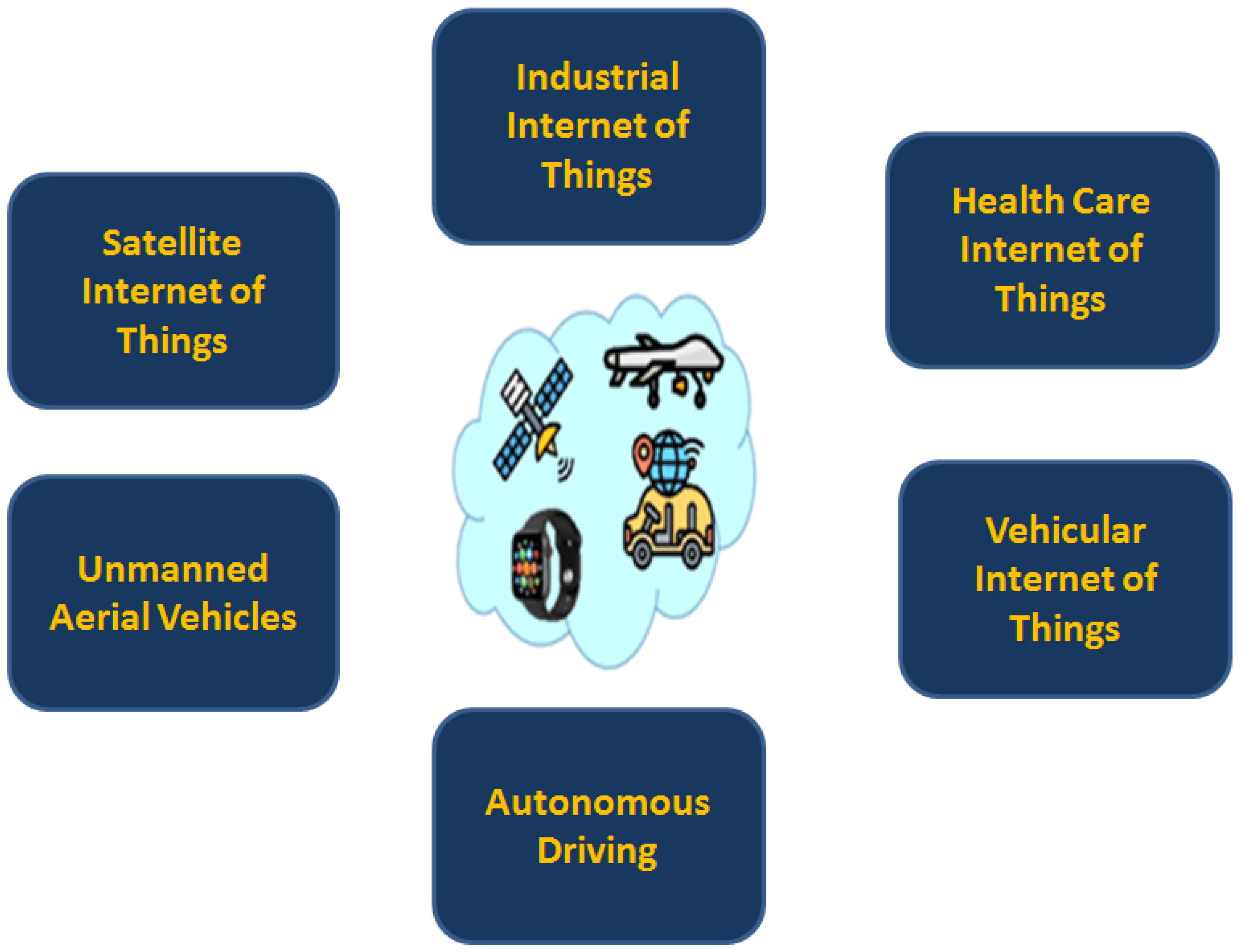
Figure 4 depicts future advanced applications that will work hand in glove with UAVs in 6G and beyond networks. Moreover, mandatory requirements in connection with the subject are also discussed. It is pertinent to mention that UAVs will be an integral part of such future applications in connection with several aspects of application needs. Most importantly, in many future scenarios, drones will act as Aerial base stations for the provision of wide area coverage of 6G networks.
3.1. 6G Applications
3.2. 6G Application Requirements
With the goal of making blockchain utility more understandable, 6G applications are separated into two major groups. Ultra-reliability, low latency, increased data speeds and huge connection are among the typical criteria. I view of the pertinent factor in almost entire wireless communication generations, these needs are made part of the first category. These are referred as Qualification Group-I (QG-I). QG-I standards necessitate considerable improvement for potential 6G applications. The prime features for any reliable and secure network include non-reputability, confidentiality, defined level of secrecy, data integrity and auditability. These features are catered in second group named Qualification Group-II (QG-II).
3.2.1. High-Precision Positioning and Seamless Coverage
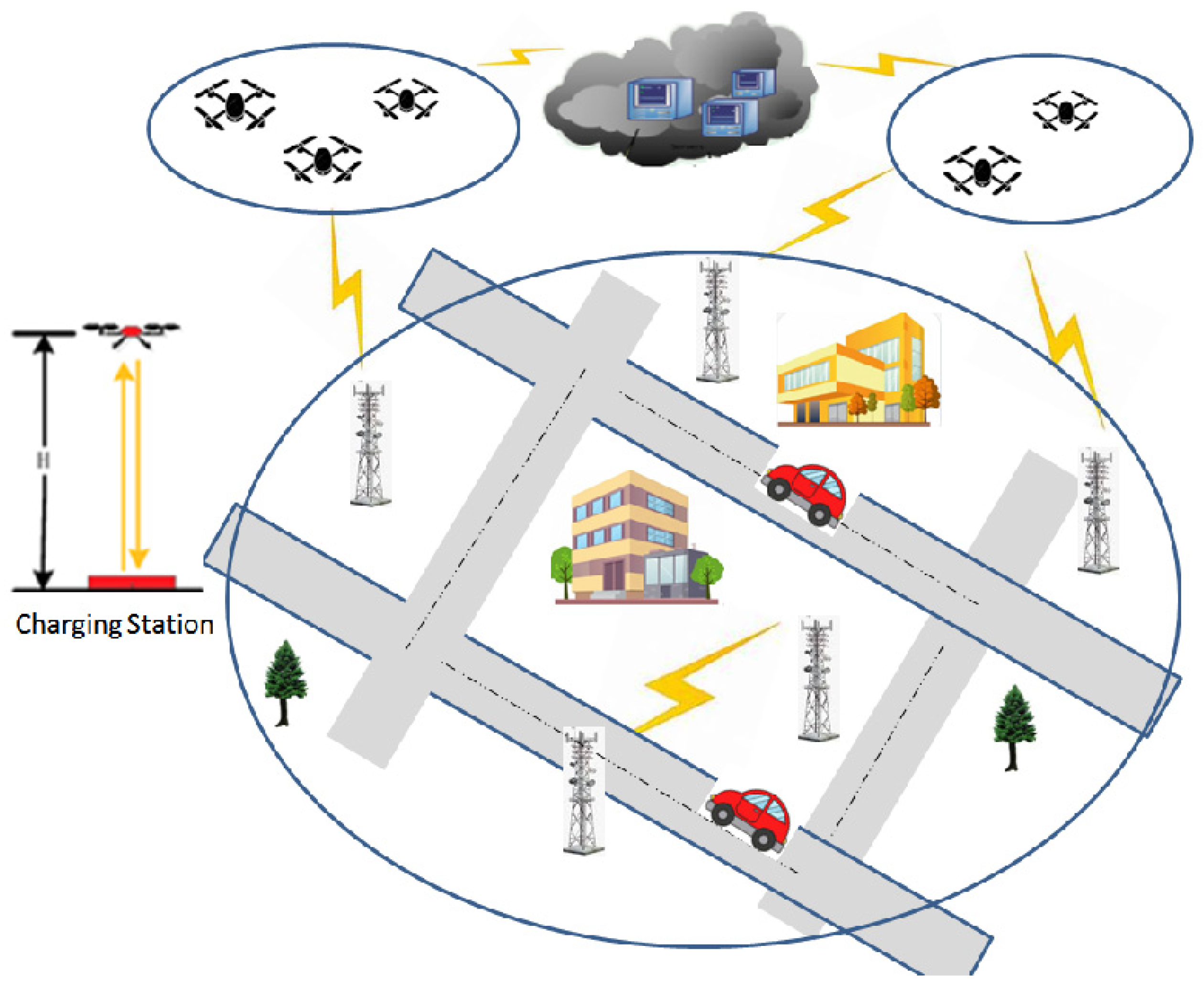
3.2.2. Remote and Real-Time Control (RRC)
3.2.3. Multimedia Transmission
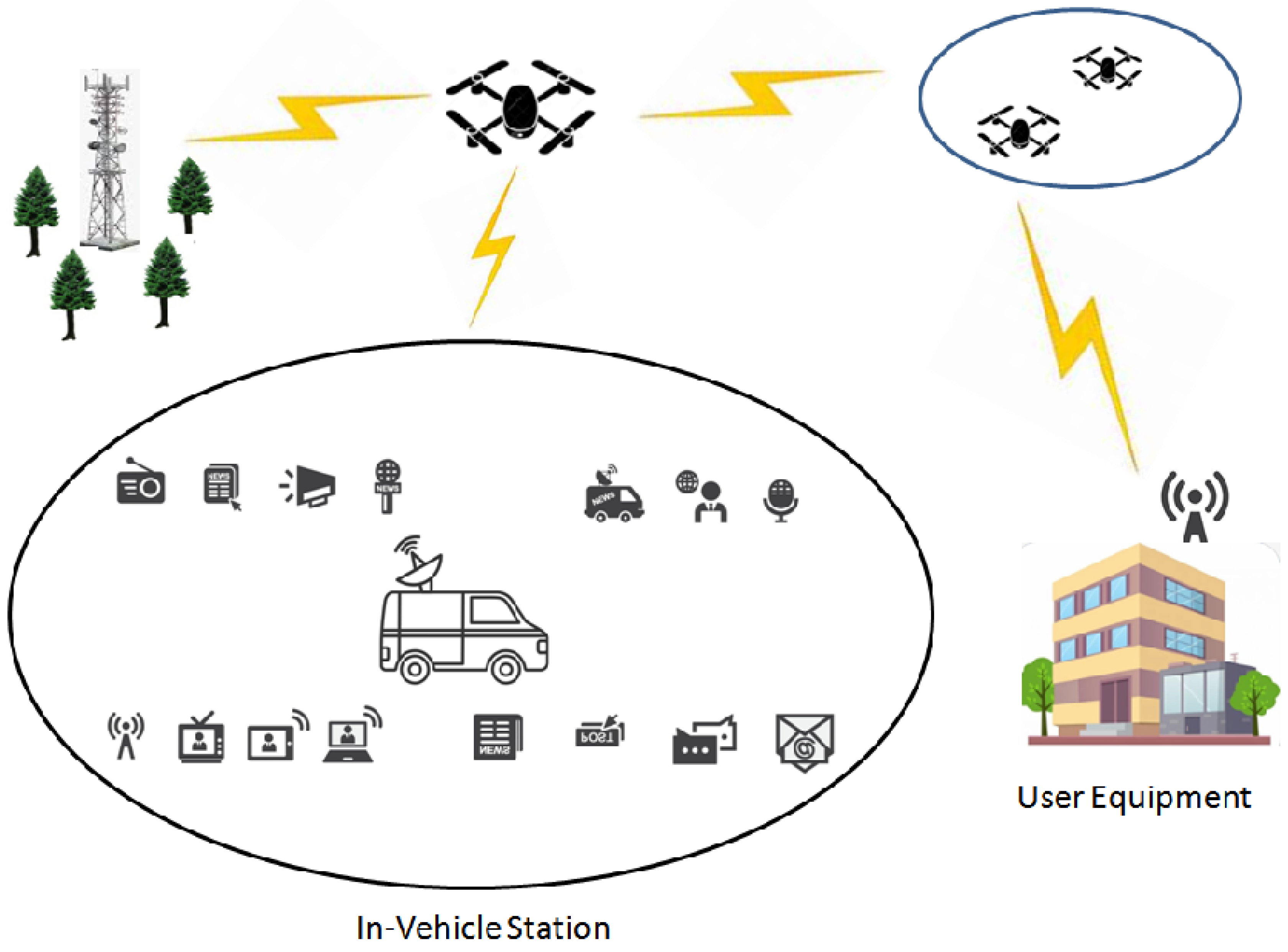
3.2.4. Aircraft Identification and Regulation
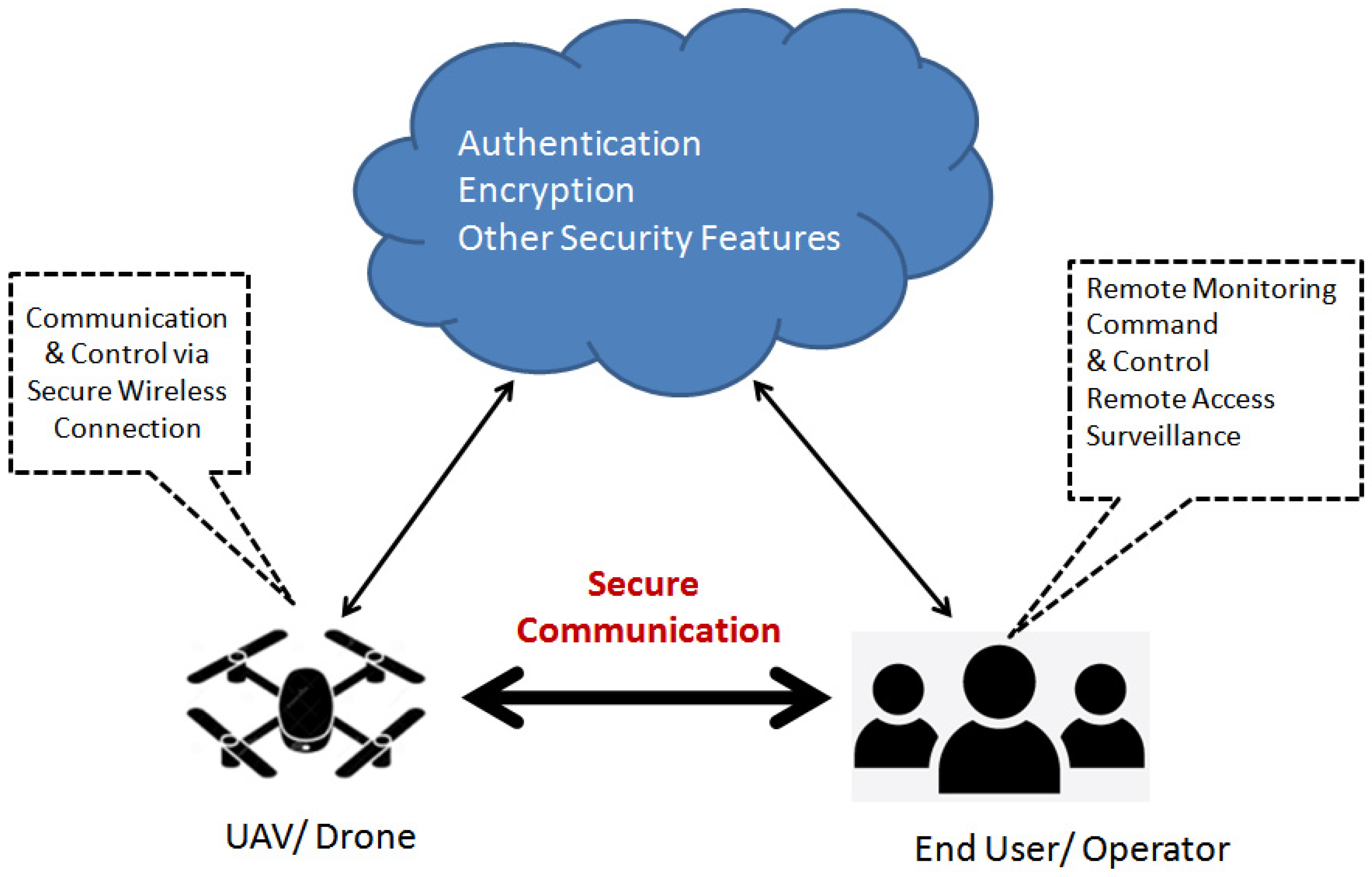
4. Authentication in UAV Networks
4.1. Light Weight Authentication Protocols
The use of WiFi has significantly increased over the years both at individual and commercial levels. Due to no complexity involved in installation and operational use of WiFi technology, the popularity of this wireless communication system is ever-increasing [38]. Moreover, it is a cost-effective solution in comparison to typical cable network. wireless sensor nodes are exploding in popularity, with applications as diverse as in any possible fields for the future [39]. These sensors are expected to be a ground-breaking addition in the consumer and business world. For example, the information collected by these sensors in a market place, in a particular section of a store, can turned into meaningful data for targeted advertisement, thus engaging visitors through tapped data by these small sensors for attracting customers and providing better services in consumer field [40].4.2. 6G Enabled Light Weight Authentication Protocols
References
- Popovski, P.; Chiariotti, F.; Huang, K.; Kalør, A.; Kountouris, M.; Pappas, N.; Soret, B. A perspective on time toward wireless 6G. Proc. IEEE 2022, 110, 1116–1146.
- Khan, A.; Javed, Y.; Abdullah, J.; Nazim, J.; Khan, N. Security issues in 5G device to device communication. Int. J. Comput. Sci. Netw. Secur. 2017, 17, 366.
- Premkumar, R.; Priya, S.S. Blockchain and Internet of Things: Applications and practices. In Proceedings of the 2021 International Conference on Artificial Intelligence and Smart Systems (ICAIS), Pichanur, India, 25–27 March 2021; pp. 1376–1380.
- Gupta, R.; Nair, A.; Tanwar, S.; Kumar, N. Blockchain-assisted secure UAV communication in 6G environment: Architecture, opportunities, and challenges. IET Commun. 2021, 15, 1352–1367.
- Moşteanu, N.; Faccia, A. Digital Systems and New Challenges of Financial Management–FinTech, XBRL, Blockchain and Cryptocurrencies. Qual.-Access Success J. 2020, 21, 159–166.
- Khan, A.S.; Balan, K.; Javed, Y.; Tarmizi, S.; Abdullah, J. Secure trust-based blockchain architecture to prevent attacks in VANET. Sensors 2019, 19, 4954.
- Safdar, H.; Fisal, N.; Ullah, R.; Maqbool, W.; Asraf, F.; Khalid, Z.; Khan, A. Resource allocation for uplink M2M communication: A game theory approach. In Proceedings of the 2013 IEEE Symposium on Wireless Technology & Applications (ISWTA), Kuching, Malaysia, 22–25 September 2013; pp. 48–52.
- Kazmi, S.H.A.; Masood, A.; Nisar, K. Design and Analysis of Multi Efficiency Motors Based High Endurance Multi Rotor with Central Thrust. In Proceedings of the 2021 IEEE 15th International Conference on Application of Information and Communication Technologies (AICT), Baku, Azerbaijan, 13–15 October 2021; pp. 1–4.
- Raja, G.; Anbalagan, S.; Ganapathisubramaniyan, A.; Selvakumar, M.S.; Bashir, A.K.; Mumtaz, S. Efficient and secured swarm pattern multi-UAV communication. IEEE Trans. Veh. Technol. 2021, 70, 7050–7058.
- Li, T.; Hu, H. Development of the Use of Unmanned Aerial Vehicles (UAVs) in Emergency Rescue in China. Risk Manag. Healthc. Policy 2021, 14, 4293.
- Zhu, K.; Han, B.; Zhang, T. Multi-UAV Distributed Collaborative Coverage for Target Search Using Heuristic Strategy. Guid. Navig. Control 2021, 1, 2150002.
- Khan, I.U.; Shah, S.B.H.; Wang, L.; Aziz, M.A.; Stephan, T.; Kumar, N. Routing protocols & unmanned aerial vehicles autonomous localization in flying networks. Int. J. Commun. Syst. 2021, e4885.
- Nagpal, S.; Aggarwal, A.; Gaba, S. Privacy and Security Issues in Vehicular Ad Hoc Networks with Preventive Mechanisms. In Proceedings of the International Conference on Intelligent Cyber-Physical Systems; Springer: Singapore, 2022; pp. 317–329.
- El Haber, E.; Alameddine, H.A.; Assi, C.; Sharafeddine, S. UAV-aided ultra-reliable low-latency computation offloading in future IoT networks. IEEE Trans. Commun. 2021, 69, 6838–6851.
- Yahuza, M.; Idris, M.Y.I.; Ahmedy, I.B.; Wahab, A.W.A.; Nandy, T.; Noor, N.M.; Bala, A. Internet of drones security and privacy issues: Taxonomy and open challenges. IEEE Access 2021, 9, 57243–57270.
- Jan, S.U.; Abbasi, I.A.; Algarni, F.; Khan, A.S. Corrections to “A Verifiably Secure ECC Based Authentication Scheme for Securing IoD Using FANET”. IEEE Access 2022, 10, 105496.
- Lei, Y.; Zeng, L.; Li, Y.-X.; Wang, M.-X.; Qin, H. A lightweight authentication protocol for UAV networks based on security and computational resource optimization. IEEE Access 2021, 9, 53769–53785.
- Oteafy, S.M. Resource augmentation in Heterogeneous Internet of Things via UAVs. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021.
- Gandra, C.; Hansson, J. Application of Value Proposition Design to a High-Tech Business Market Product; Lund University: Lund, Sweden, 2021.
- Baltaci, A.; Dinc, E.; Ozger, M.; Alabbasi, A.; Cavdar, C.; Schupke, D. A Survey of Wireless Networks for Future Aerial Communications (FACOM). IEEE Commun. Surv. Tutor. 2021, 23, 2833–2884.
- Zhang, T.; Wang, Z.; Liu, Y.; Xu, W.; Nallanathan, A. Joint Resource, Deployment, and Caching Optimization for AR Applications in Dynamic UAV NOMA Networks. IEEE Trans. Wirel. Commun. 2021, 21, 3409–3422.
- Kaiser, M.S.; Zenia, N.; Tabassum, F.; Mamun, S.A.; Rahman, M.A.; Islam, M.; Mahmud, M. 6G access network for intelligent internet of healthcare things: Opportunity, challenges, and research directions. In Proceedings of the International Conference on Trends in Computational and Cognitive Engineering; Springer: Singapore, 2021; pp. 317–328.
- Hamza, B.J.; Saad, W.K.; Shayea, I.; Ahmad, N.; Mohamed, N.; Nandi, D.; Gholampour, G. Performance enhancement of SCM/WDM-RoF-XGPON system for bidirectional transmission with square root module. IEEE Access 2021, 9, 49487–49503.
- Mitkas, D.Z.; Lovell, D.J.; Venkatesh, S.; Young, S. Activity Identification using ADS-B data at General Aviation Airports. In Proceedings of the AIAA AVIATION 2021 FORUM, Virtual Event, 2–6 August 2021.
- Ahmad, Z.; Shahid Khan, A.; Wai Shiang, C.; Abdullah, J.; Ahmad, F. Network intrusion detection system: A systematic study of machine learning and deep learning approaches. Trans. Emerg. Telecommun. Technol. 2021, 32, e4150.
- Munusamy, R.; Kumre, J.; Chaturvedi, S.; Bandhu, D. Design and Development of Portable UAV Ground Control and Communication Station Integrated with Antenna Tracking Mechanism. In Intelligent Infrastructure in Transportation and Management; Springer: Singapore, 2022; pp. 193–212.
- Adnan, W.H.; Khamis, M.F. Drone use in military and civilian application: Risk to national security. J. Media Inf. Warf. 2022, 15, 60–70.
- Mohammed, I.; Collings, I.B.; Hanly, S.V. Line of sight probability prediction for UAV communication. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6.
- Tang, S.; Zhou, W.; Chen, L.; Lai, L.; Xia, J.; Fan, L. Battery-constrained federated edge learning in UAV-enabled IoT for B5G/6G networks. Phys. Commun. 2021, 47, 101381.
- Sehrawat, H.; Siwach, V. Security vulnerabilities in Wireless Sensor Networks. J. Inf. Assur. Secur. 2010, 5, 31–44.
- Javed, Y.; Khan, A.S.; Qahar, A.; Abdullah, J. Preventing DoS attacks in IoT using AES. J. Telecommun. Electron. Comput. Eng. (JTEC) 2017, 9, 55–60.
- Nazir, M.; Sabah, A.; Sarwar, S.; Yaseen, A.; Jurcut, A. Power and resource allocation in wireless communication network. Wirel. Pers. Commun. 2021, 119, 3529–3552.
- Ly, B.; Ly, R. Cybersecurity in unmanned aerial vehicles (UAVs). J. Cyber Secur. Technol. 2021, 5, 120–137.
- Chierici, A.; Malizia, A.; Di Giovanni, D.; Ciolini, R.; d’Errico, F. A High-Performance Gamma Spectrometer for Unmanned Systems Based on Off-the-Shelf Components. Sensors 2022, 22, 1078.
- Maikol, S.O.; Khan, A.S.; Javed, Y.; Bunsu, A.L.A.; Petrus, C.; George, H.; Jau, S. A novel authentication and key agreement scheme for countering MITM and impersonation attack in medical facilities. Int. J. Integr. Eng. 2021, 13, 127–135.
- Balan, K.; Abdulrazak, L.; Khan, A.; Julaihi, A.; Tarmizi, S.; Pillay, K.; Sallehudin, H. RSSI and public key infrastructure based secure communication in autonomous vehicular networks. Int. J. Adv. Comput. Sci. Appl. 2018, 9, 298–304.
- Mahmood Saqib, R.; Shahid Khan, A.; Javed, Y.; Ahmad, S.; Nisar, K.; Abbasi, I.A.; Haque, M.R.; Ahmadi Julaihi, A. Analysis and intellectual structure of the multi-factor authentication in information security. Intell. Autom. Soft Comput. 2022, 32, 1633–1647.
- Memon, S.K.; Nisar, K.; Hijazi, M.H.A.; Chowdhry, B.; Sodhro, A.H.; Pirbhulal, S.; Rodrigues, J.J. A survey on 802.11 MAC industrial standards, architecture, security & supporting emergency traffic: Future directions. J. Ind. Inf. Integr. 2021, 24, 100225.
- Uribe-Leitz, T.; Matsas, B.; Dalton, M.K.; Lutgendorf, M.A.; Moberg, E.; Schoenfeld, A.J.; Goralnick, E.; Weissman, J.S.; Hamlin, L.; Cooper, Z. Geospatial analysis of access to emergency cesarean delivery for military and civilian populations in the US. JAMA Netw. Open 2022, 5, e2142835.
- Talpur, M.R.H.; Talpur, M.S.H.; Talpur, F.; Haseeb, A.; Kehar, A.; Fatima, S. A Model for Secure Inter-Institutional Communication Based on Artificial Intelligence (AI) and Blockchain. Int. J. Comput. Intell. Control 2021, 13, 145–154.
- Javed, Y.; Khan, A.S.; Qahar, A.; Abdullah, J. EEoP: A lightweight security scheme over PKI in D2D cellular networks. J. Telecommun. Electron. Comput. Eng. (JTEC) 2017, 9, 99–105.
- Deebak, B.D.; Fadi, A.-T. Lightweight authentication for IoT/Cloud-based forensics in intelligent data computing. Future Gener. Comput. Syst. 2021, 116, 406–425.
- Lafta, S.A.; Abdulkareem, M.M.; Ibrahim, R.K.; Kareem, M.M.; Ali, A.H. Quality of service performances of video and voice transmission in universal mobile telecommunications system network based on OPNET. Bull. Electr. Eng. Inform. 2021, 10, 3202–3210.
- Chaudhry, S.A.; Irshad, A.; Khan, M.A.; Khan, S.A.; Nosheen, S.; AlZubi, A.A.; Zikria, Y.B. A Lightweight Authentication Scheme for 6G-IoT Enabled Maritime Transport System. IEEE Trans. Intell. Transp. Syst. 2021.
- Pothumarti, R.; Jain, K.; Krishnan, P. A lightweight authentication scheme for 5G mobile communications: A dynamic key approach. J. Ambient Intell. Humaniz. Comput. 2021, 1–19.
